Abstract
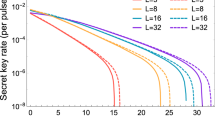
Phase-matching quantum key distribution (PM-QKD) is a promising protocol that can surpass the linear key-rate bound. Generally, inserting an advantage distillation (AD) step into PM-QKD can improve the secure key rate and transmission distance significantly in the asymptotic case. Here, we investigate the performance of practical PM-QKD systems with AD in the non-asymptotic case. Simulation results show that AD can dramatically improve the performance of practical PM-QKD systems. Moreover, we propose to estimate the information leakage using three mutually unbiased bases, namely X, Y and Z, to further enhance its performance, which demonstrates that using the error rates in X, Y and Z bases to estimate the information leakage can improve the secure key rate at high channel losses and misalignment errors.






Similar content being viewed by others
Data availability
Data underlying the results presented in this paper are not publicly available at this time but may be obtained from the authors upon reasonable request.
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, pp 175–179 (1984)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67(6), 661 (1991). https://doi.org/10.1103/PhysRevLett.67.661
Boaron, A., Boso, G., Rusca, D., Vulliez, C., Autebert, C., Caloz, M., Perrenoud, M., Gras, G., Bussières, F., Li, M.-J.: Secure quantum key distribution over 421 km of optical fiber. Phys. Rev. Lett. 121(19), 190502 (2018). https://doi.org/10.1103/PhysRevLett.121.190502
Lo, H.-K., Curty, M., Qi, B.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108(13), 130503 (2012). https://doi.org/10.1103/PhysRevLett.108.130503
Ma, X., Razavi, M.: Alternative schemes for measurement-device-independent quantum key distribution. Phys. Rev. A 86(6), 062319 (2012). https://doi.org/10.1103/PhysRevA.86.062319
Wang, S., Chen, W., Guo, J.-F., Yin, Z.-Q., Li, H.-W., Zhou, Z., Guo, G.-C., Han, Z.-F.: 2 GHz clock quantum key distribution over 260 km of standard telecom fiber. Opt. Lett. 37(6), 1008–1010 (2012). https://doi.org/10.1364/OL.37.001008
Yin, H.-L., Chen, T.-Y., Yu, Z.-W., Liu, H., You, L.-X., Zhou, Y.-H., Chen, S.-J., Mao, Y., Huang, M.-Q., Zhang, W.-J.: Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett. 117(19), 190501 (2016). https://doi.org/10.1103/PhysRevLett.117.190501
Pirandola, S., Ottaviani, C., Spedalieri, G., Weedbrook, C., Braunstein, S.L., Lloyd, S., Gehring, T., Jacobsen, C.S., Andersen, U.L.: High-rate measurement-device-independent quantum cryptography. Nat. Photonics 9(6), 397–402 (2015). https://doi.org/10.1038/nphoton.2015.83
Pirandola, S., Laurenza, R., Ottaviani, C., Banchi, L.: Fundamental limits of repeaterless quantum communications. Nat. Commun. 8(1), 15043 (2017). https://doi.org/10.1038/ncomms15043
Takeoka, M., Guha, S., Wilde, M.M.: Fundamental rate-loss tradeoff for optical quantum key distribution. Nat. Commun. 5(1), 5235 (2014). https://doi.org/10.1038/ncomms6235
Lucamarini, M., Yuan, Z.L., Dynes, J.F., Shields, A.J.: Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 557(7705), 400–403 (2018). https://doi.org/10.1038/s41586-018-0066-6
Tamaki, K., Lo, H.-K., Wang, W., Lucamarini, M.: Information theoretic security of quantum key distribution overcoming the repeaterless secret key capacity bound. arXiv:1805.05511; https://doi.org/10.48550/arXiv.1805.05511 (2018)
Ma, X., Zeng, P., Zhou, H.: Phase-matching quantum key distribution. Phys. Rev. X 8(3), 031043 (2018). https://doi.org/10.1103/PhysRevX.8.031043
Wang, X.-B., Yu, Z.-W., Hu, X.-L.: Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 98(6), 062323 (2018). https://doi.org/10.1103/PhysRevA.98.062323
Cui, C., Yin, Z.-Q., Wang, R., Chen, W., Wang, S., Guo, G.-C., Han, Z.-F.: Twin-field quantum key distribution without phase postselection. Phys. Rev. Appl. 11(3), 034053 (2019). https://doi.org/10.1103/PhysRevApplied.11.034053
Curty, M., Azuma, K., Lo, H.-K.: Simple security proof of twin-field type quantum key distribution protocol. npj Quantum Inf. 5(1), 64 (2019). https://doi.org/10.1038/s41534-019-0175-6
Lin, J., Lütkenhaus, N.: Simple security analysis of phase-matching measurement-device-independent quantum key distribution. Phys. Rev. A 98(4), 042332 (2018). https://doi.org/10.1103/PhysRevA.98.042332
Yin, H.-L., Fu, Y.: Measurement-device-independent twin-field quantum key distribution. Sci. Rep. 9(1), 3045 (2019). https://doi.org/10.1038/s41598-019-39454-1
Wang, R., Yin, Z.-Q., Lu, F.-Y., Wang, S., Chen, W., Zhang, C.-M., Huang, W., Xu, B.-J., Guo, G.-C., Han, Z.-F.: Optimized protocol for twin-field quantum key distribution. Commun. Phys. 3(1), 149 (2020). https://doi.org/10.1038/s42005-020-00415-0
Xie, Y.-M., Lu, Y.-S., Weng, C.-X., Cao, X.-Y., Jia, Z.-Y., Bao, Y., Wang, Y., Fu, Y., Yin, H.-L., Chen, Z.-B.: Breaking the rate-loss bound of quantum key distribution with asynchronous two-photon interference. PRX Quantum 3(2), 020315 (2022). https://doi.org/10.1103/PRXQuantum.3.020315
Zeng, P., Zhou, H., Wu, W., Ma, X.: Mode-pairing quantum key distribution. Nat. Commun. 13(1), 3903 (2022). https://doi.org/10.1038/s41467-022-31534-7
Zhong, X., Wang, W., Qian, L., Lo, H.-K.: Proof-of-principle experimental demonstration of twin-field quantum key distribution over optical channels with asymmetric losses. npj Quantum Inf. 7(1), 8 (2021). https://doi.org/10.1038/s41534-020-00343-5
Chen, J.-P., Zhang, C., Liu, Y., Jiang, C., Zhang, W., Hu, X.-L., Guan, J.-Y., Yu, Z.-W., Xu, H., Lin, J.: Sending-or-not-sending with independent lasers: secure twin-field quantum key distribution over 509 km. Phys. Rev. Lett. 124(7), 070501 (2020). https://doi.org/10.1103/PhysRevLett.124.070501
Wang, S., Yin, Z.-Q., He, D.-Y., Chen, W., Wang, R.-Q., Ye, P., Zhou, Y., Fan-Yuan, G.-J., Wang, F.-X., Chen, W.: Twin-field quantum key distribution over 830-km fibre. Nat. Photonics 16(2), 154–161 (2022). https://doi.org/10.1038/s41566-021-00928-2
Liu, Y., Zhang, W.-J., Jiang, C., Chen, J.-P., Zhang, C., Pan, W.-X., Ma, D., Dong, H., Xiong, J.-M., Zhang, C.-J.: Experimental twin-field quantum key distribution over 1000 km fiber distance. Phys. Rev. Lett. 130(21), 210801 (2023). https://doi.org/10.1103/PhysRevLett.130.210801
Zhou, L., Lin, J., Jing, Y., Yuan, Z.: Twin-field quantum key distribution without optical frequency dissemination. Nat. Commun. 14(1), 928 (2023). https://doi.org/10.1038/s41467-023-36573-2
Zhou, L., Lin, J., Xie, Y.-M., Lu, Y.-S., Jing, Y., Yin, H.-L., Yuan, Z.: Experimental quantum communication overcomes the rate-loss limit without global phase tracking. Phys. Rev. Lett. 130(25), 250801 (2023). https://doi.org/10.1103/PhysRevLett.130.250801
Zhu, H.-T., Huang, Y., Liu, H., Zeng, P., Zou, M., Dai, Y., Tang, S., Li, H., You, L., Wang, Z.: Experimental mode-pairing measurement-device-independent quantum key distribution without global phase locking. Phys. Rev. Lett. 130(3), 030801 (2023). https://doi.org/10.1103/PhysRevLett.130.030801
Zeng, P., Wu, W., Ma, X.: Symmetry-protected privacy: beating the rate-distance linear bound over a noisy channel. Phys. Rev. Appl. 13(6), 064013 (2020). https://doi.org/10.1103/PhysRevApplied.13.064013
Fang, X.-T., Zeng, P., Liu, H., Zou, M., Wu, W., Tang, Y.-L., Sheng, Y.-J., Xiang, Y., Zhang, W., Li, H.: Implementation of quantum key distribution surpassing the linear rate-transmittance bound. Nat. Photonics 14(7), 422–425 (2020). https://doi.org/10.1038/s41566-020-0599-8
Wang, R.-Q., Zhang, C.-M., Yin, Z.-Q., Li, H.-W., Wang, S., Chen, W., Guo, G.-C., Han, Z.-F.: Phase-matching quantum key distribution with advantage distillation. New J. Phys. 24(7), 073049 (2022). https://doi.org/10.1088/1367-2630/ac8115
Renner, R.: Security of quantum key distribution. Int. J. Quantum Inf. 6(01), 1–127 (2008). https://doi.org/10.1142/S0219749908003256
Bae, J., Acín, A.: Key distillation from quantum channels using two-way communication protocols. Phys. Rev. A 75(1), 012334 (2007). https://doi.org/10.1103/PhysRevA.75.012334
Murta, G., Rozpędek, F., Ribeiro, J., Elkouss, D., Wehner, S.: Key rates for quantum key distribution protocols with asymmetric noise. Phys. Rev. A 101(6), 062321 (2020). https://doi.org/10.1103/PhysRevA.101.062321
Tan, E.Y.-Z., Lim, C.C.-W., Renner, R.: Advantage distillation for device-independent quantum key distribution. Phys. Rev. Lett. 124(2), 020502 (2020). https://doi.org/10.1103/PhysRevLett.124.020502
Li, H.-W., Zhang, C.-M., Jiang, M.-S., Cai, Q.-Y.: Improving the performance of practical decoy-state quantum key distribution with advantage distillation technology. Commun. Phys. 5(1), 53 (2022). https://doi.org/10.1038/s42005-022-00831-4
Liu, X., Luo, D., Zhang, Z., Wei, K.: Mode-pairing quantum key distribution with advantage distillation. Phys. Rev. A 107(6), 062613 (2023). https://doi.org/10.1103/PhysRevA.107.062613
Li, H.-W., Wang, R.-Q., Zhang, C.-M., Cai, Q.-Y.: Improving the performance of twin-field quantum key distribution with advantage distillation technology. Quantum 7, 1201 (2023). https://doi.org/10.22331/q-2023-12-06-1201
Zhou, Y., Wang, R.-Q., Zhang, C.-M., Yin, Z.-Q., Wang, Z.-H., Wang, S., Chen, W., Guo, G.-C., Han, Z.-F.: Sending-or-not-sending twin-field quantum key distribution with advantage distillation. Phys. Rev. Appl. 21(1), 014036 (2024). https://doi.org/10.1103/PhysRevApplied.21.014036
Zhu, J.-R., Zhang, C.-M., Wang, R., Li, H.-W.: Reference-frame-independent quantum key distribution with advantage distillation. Opt. Lett. 48(3), 542–545 (2023). https://doi.org/10.1364/OL.480427
Wang, X.-B.: Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94(23), 230503 (2005). https://doi.org/10.1103/PhysRevLett.94.230503
Lo, H.-K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94, 230504 (2005). https://doi.org/10.1103/PhysRevLett.94.230504
Ma, X., Qi, B., Zhao, Y., Lo, H.-K.: Practical decoy state for quantum key distribution. Phys. Rev. A 72(1), 012326 (2005). https://doi.org/10.1103/PhysRevA.72.012326
Zhou, Y., Yin, Z.-Q., Wang, S., Chen, W., Guo, G.-C., Han, Z.-F.: Twin-field quantum key distribution with three mutually unbiased bases. Phys. Rev. A 107(3), 032621 (2023). https://doi.org/10.1103/PhysRevA.107.032621
Fung, C.-H.F., Ma, X., Chau, H.: Practical issues in quantum-key-distribution postprocessing. Phys. Rev. A 81(1), 012318 (2010). https://doi.org/10.1103/PhysRevA.81.012318
Acknowledgements
This work is supported by National Natural Science Foundation of China (62371244), NSAF (U2130205), China Postdoctoral Science Foundation (2019T120446, 2018M642281), Jiangsu Planned Projects for Postdoctoral Research Funds (2018K185C).
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Conflict of interest
All authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
In general, the prepare-and-measure QKD is equivalent to an entanglement-based scheme, where Alice prepares the quantum state \(\frac{1}{\sqrt{2} } \left( \mid {00} \rangle + \mid {11} \rangle \right) \), she keeps the first particle and sends the other to Bob through the quantum channel. After that, Alice and Bob take inputs from \({H_A} \otimes {H_B}\), where both \({H_A}\) and \({H_B}\) are two-dimensional Hilbert spaces, to apply the measurements of the Z, X and Y bases (the Z basis consists of \(\mid {0} \rangle \) and \(\mid {1} \rangle \), the X basis consists of \(\mid + \rangle = \frac{1}{{\sqrt{2} }}\left( {\mid 0 \rangle + \mid 1 \rangle } \right) \) and \(\mid - \rangle = \frac{1}{{\sqrt{2} }}\left( {\mid 0 \rangle - \mid 1 \rangle } \right) \), and the Y basis consists of \(\mid +i \rangle = \frac{1}{{\sqrt{2} }}\left( {\mid 0 \rangle + i\mid 1 \rangle } \right) \) and \(\mid -i \rangle = \frac{1}{{\sqrt{2} }}\left( {\mid 0 \rangle - i\mid 1 \rangle } \right) \)). Because the quantum channel can be completely controlled by the eavesdropper Eve, Alice and Bob finally share the quantum state \({\sigma _{AB}} = \sum \nolimits _{i = 0}^3 {{\lambda _i}} \mid {{\Phi _i}} \rangle \langle {{\Phi _i}}\mid \), where \({\lambda _i}\) is the diagonal value of \(\sigma _{AB}\) in the Bell basis and \(\sum \nolimits _{i = 0}^3 {{\lambda _i}} = 1\). Note that, the Bell basis has the form \(\mid {{\Phi _0}} \rangle = \frac{1}{{\sqrt{2} }}\left( {\mid { 0 0 } \rangle + \mid { 1 1 } \rangle } \right) \), \(\mid {{\Phi _1}} \rangle = \frac{1}{{\sqrt{2} }}\left( {\mid { 0 0 } \rangle - \mid { 1 1 } \rangle } \right) \), \(\mid {{\Phi _2}} \rangle = \frac{1}{{\sqrt{2} }}\left( {\mid { 0 1 } \rangle + \mid { 1 0 } \rangle } \right) \), and \(\mid {{\Phi _3}} \rangle = \frac{1}{{\sqrt{2} }}\left( {\mid { 0 1 } \rangle - \mid { 1 0 } \rangle } \right) \). It is clear that the error rates in the Z, X and Y bases satisfy \(\lambda _{2} + \lambda _{3} = E^{Z}\), \(\lambda _{1} + \lambda _{3} = E^{X}\) and \(\lambda _{1} + \lambda _{2} = E^{Y}\), respectively. Note that, Eve can choose the optimal \(\lambda _{i}\) freely to eavesdrop if \(\lambda _{i}\) is constrained by these error rates. And the final secret key rate between Alice and Bob can be expressed as [32]
where \(H(x)=-x{\log _2}x-(1-x){\log _2}(1-x)\) is the binary Shannon entropy function.
To improve the performance of QKD, Ref. [32] proposed the AD method, which can increase the correlations of raw keys between Alice and Bob. The procedure of AD is given as follows:
Step 1 Alice (Bob) splits her (his) raw key bits into blocks of size b, denoted by \(\{ x_{1}, x_{2}, \ldots , x_{b} \} (\{ y_{1}, y_{2}, \ldots , y_{b} \})\).
Step 2 Alice chooses a bit \(r\in \{ 0, 1 \}\) randomly, then sends the message \(c = \{ c_{1}, c_{2}, \ldots , c_{b} \} = \{ x_{1}\oplus r, x_{2}\oplus r, \ldots , x_{b}\oplus r \}\) to Bob through an authenticated classical channel.
Step 3 Bob calculates the result of \(\{ d_{1}, d_{2}, \ldots , d_{b}\} = \{ c_{1}\oplus y_{1}, c_{2}\oplus y_{2}, \ldots , c_{b}\oplus y_{b} \}\) to Alice. If the block \(\{ d_{1}, d_{2}, \ldots , d_{b} \}\) is \(\{ 0, 0, \ldots , 0 \}\) or \(\{ 1, 1, \ldots , 1 \}\), they continue to step 4. Otherwise, the procedure of AD ends.
Step 4 Alice and Bob keep the first bit of their initial block (specially, \(x_{1}\) and \(y_{1}\)) as their raw keys.
It is apparent that the successful probability of the AD method on the block of size b is \(p_\textrm{succ} = (\lambda _{0} + \lambda _{1})^{b} + (\lambda _{2} + \lambda _{3})^{b}\), and the final quantum state shared between Alice and Bob is \({\tilde{\sigma }_{AB}} = \sum \nolimits _{i = 0}^3 {{\tilde{\lambda }_i}} \mid {{\Phi _i}} \rangle \langle {{\Phi _i}}\mid \), where \({{{\tilde{\lambda }}_0}=\frac{{{{({\lambda _0}+{\lambda _1})}^b}+{{({\lambda _0}-{\lambda _1})}^b}}}{2p_\textrm{succ}},}\) \({{{\tilde{\lambda }}_1}=\frac{{{{({\lambda _0}+{\lambda _1})}^b}-{{({\lambda _0}-{\lambda _1})}^b}}}{2p_\textrm{succ}},}\) \({{{\tilde{\lambda }}_2}=\frac{{{{({\lambda _2}+{\lambda _3})}^b}+{{({\lambda _2}-{\lambda _3})}^b}}}{2p_\textrm{succ}},}\) and \({{{\tilde{\lambda }}_3}=\frac{{{{({\lambda _2}+{\lambda _3})}^b}-{{({\lambda _2}-{\lambda _3})}^b}}}{2p_\textrm{succ}}.}\) Consequently, the final secret key rate of QKD with AD is [32]
From the procedure of AD and Eq. A2, it is clear that Alice and Bob can choose the optimal value b to maximize the final secret key rate.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Wang, Z., Zhang, CM. & Li, HW. Improving the performance of practical phase-matching quantum key distribution with advantage distillation. Quantum Inf Process 23, 128 (2024). https://doi.org/10.1007/s11128-024-04337-6
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-024-04337-6