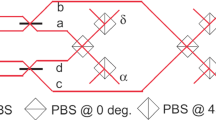
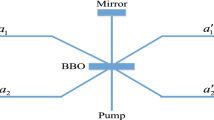
Abstract
Despite the proven security in theory and its potential to achieve high secret key rates, eavesdroppers may crack two-way quantum key distribution (TWQKD) systems by exploiting imperfections of the detection devices that most loopholes exist in, in actual implementations. Lu et al. (Phys. Rev. A 88(4):0443021–044302, 2013) have proved that TWQKD is measurement-device-independent (MDI) security on Bob’s side while assuming ideal detectors on Alice’s side. However, the MDI security proof on Alice’s side is still missing. In this paper, we focus on proving that the TWQKD protocol, secure deterministic communication without entanglement, proposed by Lucamarini and Mancini in 2005 (LM05), is MDI security on both sides of Alice and Bob (fully MDI scenario). First, using a relatively simple method, we give a qubit-based analytical proof that the LM05 is fully MDI security in a depolarizing quantum channel. Then, based on the analytical proof, we derive the expected lower bound of the security formula for it with the reasonable model of finite single-photon sources based on recent experiment progress. Moreover, with the parameters of the current technology, simulation results of the lower bound are presented. It shows that TWQKD can achieve good performances in the fully MDI scenario.




Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Data availability
The authors declare that the data supporting the findings of this study are available within the article.
References
Bennett, C.H., Brassard, G.: Withdrawn: quantum cryptography: public key distribution and coin tossing. Theor. Comput. Sci. 560, 175–179 (1984). https://doi.org/10.1016/j.tcs.2011.08.039
Lo, H.-K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283(5410), 2050–2056 (1999)
Mayers, D.: Quantum key distribution and string oblivious transfer in noisy channels. In: Koblitz, N. (ed.) Advances in Cryptology—CRYPTO ’96, pp. 343–357. Springer, Heidelberg (1996)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441–444 (2000). https://doi.org/10.1103/PhysRevLett.85.441
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.G.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145–200 (2002). https://doi.org/10.1103/RevModPhys.74.145
Boaron, A., Boso, G., Rusca, D., Vulliez, C., Autebert, C., Caloz, M., Perrenoud, M., Gras, G., Bussières, F., Li, M.-J., Nolan, D., Martin, A., Zbinden, H.: Secure quantum key distribution over 421 km of optical fiber. Phys. Rev. Lett. 121(19), 9–13 (2018). https://doi.org/10.1103/PhysRevLett.121.190502
Liao, S.-K., Cai, W.-Q., Liu, W.-Y., Zhang, L., Li, Y., Ren, J.-G., Yin, J., Shen, Q., Cao, Y., Li, Z.-P., Li, F.-Z., Chen, X.-W., Sun, L.-H., Jia, J.-J., Wu, J.-C., Jiang, X.-J., Wang, J.-F., Huang, Y.-M., Wang, Q., Zhou, Y.-L., Deng, L., Xi, T., Ma, L., Hu, T., Zhang, Q., Chen, Y.-A., Liu, N.-L., Wang, X.-B., Zhu, Z.-C., Lu, C.-Y., Shu, R., Peng, C.-Z., Wang, J.-Y., Pan, J.-W.: Satellite-to-ground quantum key distribution. Nature 549(7670), 43–47 (2017)
Zhao, Y., Fred Fung, C.-H., Qi, B., Chen, C., Lo, H.-K.: Quantum hacking: experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys. Rev. A 78(4), 042333 (2008). https://doi.org/10.1103/PhysRevA.78.042333
Xu, F.H., Qi, B., Lo, H.-K.: Experimental demonstration of phase-remapping attack in a practical quantum key distribution system. New J. Phys. 12(11), 113026 (2010). https://doi.org/10.1088/1367-2630/12/11/113026
Lydersen, L., Wiechers, C., Wittmann, C., Elser, D., Skaar, J., Makarov, V.: Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photonics 4(10), 686–689 (2010)
Gaidash, A., Kozubov, A., Miroshnichenko, G.: Countermeasures for advanced unambiguous state discrimination attack on quantum key distribution protocol based on weak coherent states. Phys. Scr. 94(12), 125102 (2019). https://doi.org/10.1088/1402-4896/ab3277
Lo, H.-K., Curty, M., Qi, B.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108(13), 130503 (2012). https://doi.org/10.1103/PhysRevLett.108.130503
Rubenok, A., Slater, J.A., Chan, P., Lucio-Martinez, I., Tittel, W.: A quantum key distribution system immune to detector attacks (2012). https://doi.org/10.48550/arXiv.1204.0738
Ferreira da Silva, T., Vitoreti, D., Xavier, G.B., do Amaral, G.C., Temporão, G.P. and von der Weid, J.P.: Proof-of-principle demonstration of measurement-device-independent quantum key distribution using polarization qubits. Phys. Rev. A 88(5), 052303–052309 (2013). https://doi.org/10.1103/PhysRevA.88.052303
Liu, Y., Chen, T.-Y., Wang, L.-J., Liang, H., Shen, Tu., G.-L., Wang, J., Cui, K., Yin, H.-L., Liu, N.-L., Li, L., Ma, X.-F., Pelc, J.S., Fejer, M.M., Peng, C.-Z., Zhang, Q., Pan, J.-W.: Experimental measurement-device-independent quantum key distribution. Phys. Rev. Lett. 111(13), 130502–130505 (2013). https://doi.org/10.1103/PhysRevLett.111.130502
Tang, Z.-Y., Liao, Z.-F., Xu, F.-H., Qi, B., Qian, L., Lo, H.-K.: Experimental demonstration of polarization encoding measurement-device-independent quantum key distribution. Phys. Rev. Lett. 112(19), 190503–190506 (2014). https://doi.org/10.1103/PhysRevLett.112.190503
Yin, H.-L., Chen, T.-Y., Yu, Z.-W., Liu, H., You, L.-X., Zhou, Y.-H., Chen, S.-J., Mao, Y.Q., Huang, M.-Q., Zhang, W.-J., Chen, H., Li, M.-J., Nolan, D., Zhou, F., Jiang, X., Wang, Z., Zhang, Q., Wang, X.-B., Pan, J.-W.: Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett. 117(19), 190501–190515 (2016)
Ma, X.-F., Zeng, P., Zhou, H.-Y.: Phase-matching quantum key distribution. Phys. Rev. X 8(3), 0310431 (2018). https://doi.org/10.1103/PhysRevX.8.031043
Lucamarini, M., Yuan, Z.L., Dynes, J.F., Shields, A.J.: Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 557, 400–403 (2018)
Fang, X.-T., Zeng, P., Liu, H., Zou, M., Wu, W.-J., Tang, Y.-L., Sheng, Y.-J., Xiang, Y., Zhang, W.-J., Li, H., Wang, Z., You, L.-X., Li, M.-J., Chen, H., Chen, Y.-A., Zhang, Q., Peng, C.-Z., Ma, X.-F., Chen, T.-Y., Pan, J.-W.: Implementation of quantum key distribution surpassing the linear rate-transmittance bound. Nat. Photonics 14, 422–425 (2020). https://doi.org/10.1038/s41566-020-0599-8
Chen, J.-P., Zhang, C., Liu, Y., Jiang, C., Zhang, W.-J., Hu, X.- L., Guan, J.-Y., Yu, Z.-W., Xu, H., Lin, J., Li, M.-J., Chen, H., Li, H., You, L.-X., Wang, Z., Wang, X.-B., Zhang, Q., Pan, J.-W.: Sending-or-not-sending with independent lasers: secure twin-field quantum key distribution over 509 km. Phys. Rev. Lett. 124(7), 070501 (2020). https://doi.org/10.1103/PhysRevLett.124.070501
Boström, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89(18), 187902 (2002). https://doi.org/10.1103/PhysRevLett.89.187902
Lucamarini, M., Mancini, S.: Secure deterministic communication without entanglement. Phys. Rev. Lett. 94(14), 140501 (2005). https://doi.org/10.1103/PhysRevLett.94.140501
Cai, Q.-Y.: The ping-pong protocol can be attacked without eavesdropping. Phys. Rev. Lett. 91, 109801 (2003). https://doi.org/10.1103/PhysRevLett.91.109801
Wójcik, A.: Eavesdropping on the “ping-pong’’ quantum communication protocol. Phys. Rev. Lett. 90(15), 157901 (2003). https://doi.org/10.1103/PhysRevLett.90.157901
Beaudry, N.J., Lucamarini, M., Mancini, S., Renner, R.: Security of two-way quantum key distribution. Phys. Rev. A 88(6), 062302 (2013). https://doi.org/10.1103/PhysRevA.88.062302
Lu, H., Fred Fung, C.-H., Ma, X.-F., Cai, Q.-Y.: Unconditional security proof of a deterministic quantum key distribution with a two-way quantum channel. Phys. Rev. A 84(4), 042344 (2011). https://doi.org/10.1103/PhysRevA.84.042344
Fred Fung, C.-H., Ma, X.-F., Chau, H.F., Cai, Q.-Y.: Quantum key distribution with delayed privacy amplification and its application to the security proof of a two-way deterministic protocol. Phys. Rev. A 85(3), 032308 (2012). https://doi.org/10.1103/PhysRevA.85.032308
Kang, G.-D., Zhou, Q.-P., Fang, M.-F.: Two-way quantum key distribution in a uniformly distributed quantum space via a special mapping and its analytical security proofs. Int. J. Quant. Inf. 17(1), 1950010 (2019). https://doi.org/10.1142/S0219749919500102
Lucamarini, M., Cere’, A., Di Giuseppe, G., Mancini, S., Vitali, D., Tombesi, P.: Two-way protocol for quantum cryptography with imperfect devices. Open. Syst. Inf. Dyn. 14, 169–178 (2007)
Lu, H., Fred Fung, C.-H., Cai, Q.-Y.: Two-way deterministic quantum key distribution against detector-side-channel attacks. Phys. Rev. A 88(4), 0443021–044302 (2013)
Jozsa, R., Schlienz, J.: Distinguishability of states and von Neumann entropy. Phys. Rev. A (2000). https://doi.org/10.1103/PhysRevA.62.012301
Senellart, P., Solomon, G., White, A.: High-performance semiconductor quantum-dot single-photon sources. Nat. Nanotechnol. 12(11), 1026–1039 (2017)
Jie, Zeng Zhi, H., Phan Ngyuen, M.A., Ai, X.-Y., Bennet, A., Solnstev, A., Laucht, A., Al-Juboori, A., Toth, M., Mildren, R., Malaney, R. and Aharonovich, I.: Integrated room temperature single-photon source for quantum key distribution. Opt. Lett. 47(7), 1673–1676 (2022)
Lütkenhaus, N.: Security against individual attacks for realistic quantum key distribution. Phys. Rev. A 61(5), 052304–052314 (2000)
Ma, X.-F., Qi, B., Zhao, Y., Lo, H.-K.: Practical decoy state for quantum key distribution. Phys. Rev. A 72, 012326 (2005). https://doi.org/10.1103/PhysRevA.72.012326
El Gamal, A., Kim, Y.H.: Network Information Theory. Cambridge University Press, Cambridge (2011). https://doi.org/10.1017/CBO9781139030687
Li, H.-W., Zhao, Y.-B., Yin, Z.-Q., Wang, S., Han, Z.-F., Bao, W.-S., Guo, G.-C.: Security of decoy states QKD with finite resources against collective attacks. Opt. Commun. 282(20), 4162–4166 (2009)
Christandl, M., Koenig, R., Renner, R.: Post-selection technique for quantum channels with applications to quantum cryptography. Phys. Rev. Lett. 102(2), 020504 (2008). https://doi.org/10.1103/PhysRevLett.102.020504
Gobby, C., Yuan, Z.L., Shields, A.J.: Quantum key distribution over 122 km of standard telecom fiber. Appl. Phys. Lett. 84(19), 3762–3764 (2004). https://doi.org/10.1063/1.1738173
Gu, Y.-B., Bao, W.-S., Wang, Y., Zhou, C.: Security of the decoy state two-way quantum key distribution with finite resources. Chin. Phys. Lett. 33(4), 040301 (2016). https://doi.org/10.1088/0256-307X/33/4/040301
Zhou, Z.-R., Sheng, Y.-B., Niu, P.-H., Yin, L.-G., Long, G.-L.: Measurement-device-independent quantum secure direct communication. Sci. China Phys. Mech. 63(3), 1–6 (2020). https://doi.org/10.1007/s11433-019-1450-8
Acknowledgements
This work was supported by the National Natural Science Foundation of China under Grant Nos. (12604012,11464015), the Natural Science Foundation of Hunan Province under Grant No. 2020JJ4496 and the Science Research Foundation of Education Department of Hunan Province under Grant No.20A0585
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: Against zero error attacks
For TWQKD protocols, these creative ideas of zero error attacks [24, 25] are fatal and should be dealt with carefully. Here, we analyze the effects of zero error attacks for this fully MDI protocol.
Eve intercepts and stores all of Bob’s qubits \( \arrowvert \psi _{Bob}\rangle =\mathop {\otimes }\limits _{i=1}^{N}\arrowvert \phi _{i}\rangle \) on the QFC, and then emits the faked states \( \arrowvert \psi _{Eve}\rangle =\mathop {\otimes }\limits _{i=1}^{N}\arrowvert \phi _{i}^{'}\rangle \) to Alice, with the i-th photon \( \arrowvert \phi _{i}^{'}\rangle \) randomly chosen from the four states \( \left\{ Z:\arrowvert 0\rangle ,\arrowvert 1\rangle ;X:\arrowvert +\rangle ,\arrowvert -\rangle \right\} \). After passing \( \arrowvert \psi _{Eve}\rangle \) through the CM(EM) performed by Alice, the faked states \(\arrowvert \psi _{Eve}\rangle \) are transformed to \( \arrowvert \psi _{Eve}^{'}\rangle \), and Eve tries to extract Alice’s encoding bits \( l^{'}_{k} \) by measuring each qubit in \( \arrowvert \psi _{Eve}^{'}\rangle \) with the preparation bases of \(\arrowvert \psi _{Eve}\rangle \). And then, without changing the position index i, each bit of \( l^{'}_{k} \) will be encoded in each of the intercepted qubits \(\arrowvert \psi _{Bob}\rangle \). Then \(\arrowvert \psi _{Bob}\rangle \) is transformed to \( \arrowvert \psi _{Eve}^{''}\rangle \). Finally, with Bob’s bases, Eve measures each qubit of \(\arrowvert \psi _{Eve}^{''}\rangle \) and reports the measurement results(classical bits) to Bob. Obviously, via the above attacks, on the one hand, Eve can get all of Alice’s key bits, and on the other hand, Eve will inevitably introduce errors due to the CM. The analysis is simple and presented below. From Tables 1 and 2 in Sect. 2, it is easy to figure out that, in each round, Eve chooses the wrong basis with probability 1/2 when conducting the zero error attacks and sending the faked state \( \arrowvert \phi _{i}^{'}\rangle \) to Alice, where she gets a flipped bit 1 with probability 1/2. This strategy will be detected by Alice and Bob after Alice’s announcement in the step.(6) mentioned in Sect. 2, while the measurement result with bit 0 causes zero error. So, considering the fully MDI scenario, before reporting all of the final results to Bob, Eve may, with probability \( P_{t} \), tamper with the flipped bit 1, regarded as the result of basis mismatching in the CM, to be 0. However, this strategy causes error in the case that the flipped bit 1 is Alice’s encoding bit since Eve cannot distinguish between the CM and the EM. Hence, the error rates introduced by Eve in the CM and the EM are, respectively, given by
where \( 0\le P_{t}\le 1 \). Obviously, if Eve does not tamper with any of the flipped bits, the error rate is \( Q_{f} =0.0625\). Otherwise, the error rate is \( Q_{f-b}=0.375 \) if Eve tries to escape completely from being detected by the CM. Hence, Eve should control her strategy to balance \( Q_{f} \) and \( Q_{f-b} \), while Alice and Bob can set the security threshold bound tightly with \( Q_{f-b}=Q_{f}=Q_{(max)}\approx 0.053 \), which is true in asymptotic cases in a depolarizing quantum channel to forbid Eve’s zero error attacks.
Appendix B: General collective attacks
In this paper, we consider the case of general collective attacks and classical post-processing implemented with direct reconciliation. The most general attack that Eve can perform on the QFC consists of a joint interaction between the sent qubit and some auxiliary ancillas. It can be represented as
where \( \widehat{U} \)(Eve’s attacks operation) is a unitary operation acting on the joint Hilbert space of the ancilla and the qubit \( \rho ^{B} \), The set \( \left\{ \arrowvert i\rangle _{\textbf{k}}\right\} =\left\{ \arrowvert 0\rangle _{\textbf{k}},\arrowvert 1\rangle _{\textbf{k}} \right\} \) represent the eigenstates of the Pauli operator with \( \textbf{k}=\left\{ Z,X \right\} \) Bob’s preparation direction. Without loss of generality, we assume that ancilla states fulfill the following conditions(neglecting the preparation direction symbol \( \textbf{k} \))
Equation(B.2) guarantees the unitarity of \( \widehat{U} \). Considering the QFC and QBC are depolarizing channels, the nature noise \( Q_{f-b} \) is independent of the bases of the qubit \( \rho ^{B} \). Thus, the specific form of Eve’s attacks can further be written as follows
where \( Q_{f-b} \) also represents the upper bound of noise that Eve can introduce in her attacks without being detected. According to the Gram matrix defined in Ref. [32] and Eve’s collective attacks \( \widehat{U} \) in Eq. (B.1), the sets of the \(G\left\{ |\varphi _{1}\rangle ,|\varphi _{2}\rangle ,|\varphi _{3}\rangle ,|\varphi _{4}\rangle \right\} \) can be written as
Then, using the specific form of Eve’s attacks in Eq. (B.3), the Gram matrix of \(\rho ^{ABE}\) is explicitly given by
The eigenvalues of \( G(\rho ^{ABE}) \) and the von Neumann entropy \( S(\rho ^{ABE}) \) are, respectively, given by
where the factor 2 in Eq. (B.7) is due to the multiple roots of the eigenvalues of \( G(\rho ^{ABE}) \). From Eqs.(B.6), (B.7) and note that \( S(\rho ^{ABE}) \) takes its maximum S(max) at \(\langle \varepsilon _{00}\arrowvert \varepsilon _{10}\rangle =0\), we can get the maximum value of von Neumann entropy \( S(\rho ^{ABE}) \)
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kang, GD., Liu, J., Zhang, T. et al. Fully measurement-device-independent two-way quantum key distribution with finite single-photon sources. Quantum Inf Process 23, 211 (2024). https://doi.org/10.1007/s11128-024-04419-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-024-04419-5