Abstract
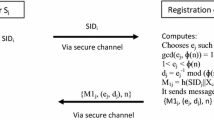
In recent papers (J Supercomput 66(2):973–988, 2013; J Supercomput 69(1):395–411, 2014), the authors presented two efficient identity-based authenticated key agreement schemes for mobile client–server networks, respectively. In this letter, we show that there is a serious security flaw in the user registration phase of the two schemes: any authorized user can impersonate the server to generate an effective private key of any other user. We then present a suggestion to overcome the problem without losing any good features of the original schemes.
Similar content being viewed by others
References
Chou CH, Tsai KY, Lu CF (2013) Two ID-based authenticated schemes with key agreement for mobile environments. J Supercomput 66(2):973–988
Farash MS, Attari MA (2014) A secure and efficient identity-based authenticated key exchange protocol for mobile client–server networks. J Supercomput 69(1):395–411
Acknowledgments
This work was supported by National Natural Science Foundation of China (61173187, 61173188 and 11301002), the Ministry of Education institution of higher learning doctor discipline and scientific research fund (20133401110004), Natural Science Foundation of Anhui Province (1408085QF107), and the 211 Project of Anhui University (33190187 and 17110099).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Shi, Rh., Zhong, H. & Zhang, S. Comments on two schemes of identity-based user authentication and key agreement for mobile client–server networks. J Supercomput 71, 4015–4018 (2015). https://doi.org/10.1007/s11227-015-1496-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-015-1496-7