Abstract
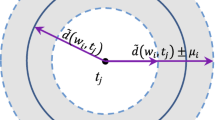
Spatial crowdsourcing is a promising architecture for collecting various types of data online with the aid of participants’ powerful mobile devices. However, it is also associated with certain privacy and security issues, which can reduce the quality of the crowdsourcing service. Some crowd tasks require the collection of connected data points. When a location-anonymous method is employed to ensure the privacy of location data points, the location trajectory data may become meaningless. To solve the privacy problem for trajectory data in large-scale crowdsourcing systems, we proposed a spatial task management method for privacy-preserving trajectory-based crowdsourcing, using a 3DES encryption and compressive-sensing-based trajectory data decryption method which is called DES-TraVec (3DES-based trajectory vector) cryptography algorithm. To provide a real-time crowdsourcing service, we proposed the use of an extended TPR*-Tree to bulk load the crowdsourcing results and manage the benders service requests so that the proposed method could support participants’ privacy and ensure quick answers for crowdsourcing services. The experimental results demonstrated that the proposed method is efficient in preserving trajectory-based crowdsourcing data and is faster than the current method.




Similar content being viewed by others
References
Han Y-H, Lim H-K, Gil J-M (2017) Hierarchical location caching scheme for mobile object tracking in the internet of things. J Inf Process Syst 13(5):1410–1429
Kim J-J (2017) Spatio-temporal sensor data processing techniques. J Inf Process Syst 13(5):1259–1276
To H, Asghari M, Deng D, Shahabi C (2016) SCAWG: a toolbox for generating synthetic workload for spatial crowdsourcing. In: Proceedings of International Workshop on Benchmarks for Ubiquitous Crowdsourcing: Metrics, Methodologies, and Datasets
Vanus J et al (2017) Monitoring of the daily living activities in smart home care. Hum Centric Comput Inf Sci 7(1):30
Xiao F et al (2018) An information-aware visualization for privacy-preserving accelerometer data sharing. Hum Centric Comput Inf Sci 8(1):13
Tao Y, Papadias D, Sun J (2003) The TPR*-tree: an optimized spatio-temporal access method for predictive queries. In: International Conference on Very Large Data Bases. VLDB Endowment, pp 790–801
Perez AJ, Zeadally S, Jabeur N (2018) Security and privacy in ubiquitous sensor networks. J Inf Process Syst 14(2):268–308
Kazemi L, Shahabi C (2012) Geocrowd: enabling query answering with spatial crowdsourcing. In: Proceedings of the 20th International Conference on Advances in Geographic Information Systems. ACM
Van BN, Lee S, Kwon K (2017) Selective encryption algorithm using hybrid transform for GIS vector map. J Inf Process Syst 13(1):68–82
Kong L, He L, Liu X Y et al (2015) Privacy-preserving compressive sensing for crowdsensing based trajectory recovery IEEE. In: International Conference on Distributed Computing Systems. IEEE, pp 31–40
Donoho DL (2006) Compressed sensing. IEEE Trans Inf Theory 52(4):1289–1306
Hao F, Park D-S, Pei Z (2018) When social computing meets soft computing: opportunities and insights. Hum Centric Comput Inf Sci 8(8):1–18
Arthur J, Azadegan S (2005) Spring framework for rapid open source J2EE web application development: a case study. In: Sixth International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, and First ACIS International Workshop on Self-Assembling Wireless Networks, SNPD/SAWN 2005. IEEE
Jain N, Mangal P, Mehta D (2015) AngularJS: a modern MVC framework in JavaScript. J Glob Res Comput Sci 5(12):17–23
To H, Ghinita G, Shahabi C (2014) A framework for protecting worker location privacy in spatial crowdsourcing. Proc VLDB Endow 7(10):919–930
Li Y, Yiu ML, Xu W (2015) Oriented online route recommendation for spatial crowdsourcing task workers. LNCS 9239:137–156
Lee C, Lee S, Li Y, Shin B-S (2016) Design and Implementation of spatial crowdsourcing platform for geospatial knowledge acquisition and dissemination. J Korean Inst Next Gen Comput 12(3):61–74
Pournajaf L et al (2014) Spatial task assignment for crowd sensing with cloaked locations. In: IEEE 15th International Conference on Mobile Data Management (MDM), vol 1. IEEE
Manly BFJ (2006) Randomization, bootstrap and Monte Carlo methods in biology, vol 70. CRC Press, Boca Raton
Santiago A (2015) The book of OpenLayers 3. Theory and practice. Leanpub, Victoria, BC Google Scholar
Huang KL, Kanhere SS, Wen H (2009) Towards privacy-sensitive participatory sensing. In: IEEE International Conference on Pervasive Computing and Communications, PerCom 2009. IEEE, pp 1–6
Liu B et al (2017) Protecting location privacy in spatial crowdsourcing using encrypted data. In: EDBT
To H, Ghinita G, Shahabi C (2015) PrivGeoCrowd: a toolbox for studying private spatial crowdsourcing. In: IEEE 31st International Conference on Data Engineering, pp 1404–1407
Yang K et al (2015) Security and privacy in mobile crowdsourcing networks: challenges and opportunities. IEEE Commun Mag 53(8):75–81
To H, Shahabi C (2015) A server assigned spatial crowdsourcing framework. ACM Trans Spat Algorithms Syst 1(1):2
Wernke M et al (2014) A classification of location privacy attacks and approaches. Pers Ubiquit Comput 18(1):163–175
Wang H et al (2010) Index-based selective audio encryption for wireless multimedia sensor networks. IEEE Trans Multimed 12(3):215–223
Guha S, Jain M, Padmanabhan VN (2012) Koi: a location-privacy platform for smartphone apps. In: Proceedings of the 9th USENIX Conference on Networked Systems Design and Implementation. USENIX Association
Chen C et al (2012) Fused matrix factorization with geographical and social influence in location-based social networks. In: Aaai, vol 12
Candes EJ, Plan Y (2010) Matrix completion with noise. Proc IEEE 98(6):925–936
Roy JA et al (2009) CRISP: congestion reduction by iterated spreading during placement. In: Proceedings of the 2009 International Conference on Computer-Aided Design. ACM
Singh G (2013) A study of encryption algorithms (RSA, DES, 3DES and AES) for information security. Int J Comput Appl 67(19):33–38
Acknowledgements
This research was supported by Research Program To Solve Social Issues of the National Research Foundation of Korea(NRF) funded by the Ministry of Science and ICT (No. NRF-2017M3C8A8091768).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Li, Y., Shin, BS. Privacy-aware task data management using TPR*-Tree for trajectory-based crowdsourcing. J Supercomput 74, 6976–6987 (2018). https://doi.org/10.1007/s11227-018-2486-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-018-2486-3