Abstract
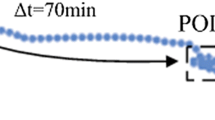
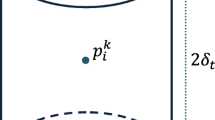
Since Osman Abul et al. first proposed the k-anonymity-based privacy protection for trajectory data, researchers have proposed a variety of trajectory privacy-preserving methods. These methods mainly adopt a static anonymity algorithm, which only focusing on the trajectories in a specific time span, directly anonymizes data and publishes them without considering dynamic nature of trajectory data as the new time slice arriving. Furthermore, due to its correlation with time and position, the trajectory data is produced in large scale and many sensitive attributes; the traditional k-anonymity-based privacy-preserving models need to recalculate the last released trajectory data, which will increase the computing cost and reduce the availability of the released trajectories, are not fit for privacy protection in large-scale trajectory data. Therefore, this paper presents a method to dynamically publish the large-scale vehicle trajectory data with privacy protection under \((k,\delta )\) security constraints. According to the spatial and temporal characteristics of vehicle trajectory data, this paper first proposes a method to partition the trajectory data for storage and computation. We choose the sample point \((x_{i},y_{i})\) at time \(t_{i}\) as partition points and store the partitions of the trajectory data according to the time sequence and location of the running vehicle. This results in the efficient trajectory scanning, clustering and privacy protection. We use \((x_{i},y_{i},t_{m}-t_{n})\) to represent the identifier of trajectory data to publish, use the generalize function to cluster trajectory data under the \((k,\delta )\) security constraints. Through this way, we can effectively process the trajectory in every data partition as time goes on and need not to recalculate the released trajectories, effectively reduce the computing cost. Through experiments on real trajectory data and Oldenburg trajectory data, confirming the data partitioning method in privacy-preserving large-scale trajectory data publishing under the security constraint of \((k,\delta )\), and the l-diversity. By the experimental comparison, our method maintains a least level of computing cost and higher data availability.














Similar content being viewed by others
References
Abul O, Bonchi F, Nanni M (2008) Never walk alone: Uncertainty for anonymity in moving objects databases. In: IEEE International Conference on Data Engineering, pp 376–385
Bayardo RJ, Agrawal R (2005) Data privacy through optimal k anonymization. In: Proceedings of International Conference on Data Engineering, 2005, ICDE 2005, pp 217–228
Beresford AR, Stajano F (2004) Mix zones: User privacy in location aware services. In: Proceedings of the Second IEEE Conference on Pervasive Computing and Communications Workshops, pp 127–131
Bonchi F, Lakshmanan LVS, Wang H (2011) Trajectory anonymity in publishing personal mobility data. ACM Sigkdd Explor Newsl 13(1):30–42
Chen TS, Lee WB, Chen J, Kao YH, Hou PW (2013) Reversible privacy preserving data mining: a combination of difference expansion and privacy preserving. J Supercomput 66(2):907–917
Guangdong communications and transportation department. http://www.gddata.gov.cn (2018)
Finkel JR, Grenager T, Manning C (2005) Incorporating non-local information into information extraction systems by GIBBS sampling. In: Meeting on Association for Computational Linguistics, pp 363–370
Gao S, Ma J, Sun C, Li X (2014) Balancing trajectory privacy and data utility using a personalized anonymization model. J Netw Comput Appl 38(1):125–134
Ghorbel A, Ghorbel M, Jmaiel M (2017) Privacy in cloud computing environments: a survey and research challenges. J Supercomput 73(6):2763–2800
Han H, Park S (2017) Traffic information service model considering personal driving trajectories. J Inf Process Syst 13(4)
Kumari V, Chakravarthy S (2016) Cooperative privacy game: a novel strategy for preserving privacy in data publishing. Hum Centric Comput Inf Sci 6(1):12
Li F, Gao F, Yao L, Pan Y (2016) Privacy preserving in the publication of large scale trajectory databases. Springer, New York
Liberti L, Lavor C, Maculan N, Mucherino A (2014) Euclidean distance geometry and applications. Quant Biol 56(1):3–69
Liu P, Li Y, Sang Y, Zhang J (2016) Anonymity based privacy preserving network data publication. In: Trustcom BigDatase ISPA, pp 823–828
Machanavajjhala A, Gehrke J, Kifer D, Venkitasubramaniam M (2006) L diversity: privacy beyond k anonymity. In: International Conference on Data Engineering, pp 24–24
Mano K, Minami K, Maruyama H (2013) Privacy preserving publishing of pseudonym based trajectory location data set. In: Eighth International Conference on Availability, Reliability and Security, pp 615–624
Perez AJ, Zeadally S, Jabeur N (2018) Security and privacy in ubiquitous sensor networks. J Inf Process Syst 14(2):286–308
Pingley A, Zhang Nan, Fu Xinwen, Choi HA (2013) Protection of query privacy for continuous location based services. In: 2011 Proceedings IEEE INFOCOM, pp 1710–1718
Poulis G, Skiadopoulos S, Loukides G, Gkoulalas-Divanis A (2013) Distance based km anonymization of trajectory data. In: IEEE International Conference on Mobile Data Management, pp 57–62
Samarati P (2001) Protecting respondents identities in microdata release. IEEE Trans Knowl Data Eng 13(6):1010–1027
Sang Y, Shen H, Tian H, Zhang Z (2016) Achieving probabilistic anonymity in a linear and hybrid randomization model. IEEE Trans Inf Forensics Secur 11(10):2187–2202
Shin H, Vaidya J, Atluri V, Choi S (2010) Ensuring privacy and security for lbs through trajectory partitioning. In: Eleventh International Conference on Mobile Data Management, pp 224–226
Suryani V, Sulistyo S, Widyawan W (2017) Internet of things (iot) framework for granting trust among objects. J Inf Process Syst 13(6):1613–1627
Sweeney L (2002) k-anonymity a model for protecting privacy. Int J Uncertain Fuzziness Knowl Based Syst 10(05):557–570
Brinkhoff T (2003) Generating traffic data. IEEE Data Eng Bull 23(2):19–25
Thimmarayappa S, Megha V (2014) Big data privacy and management. Int J Comput Appl 107(6):13–16
Tramp S, Frischmuth P, Arndt N, Ermilov T, Auer S (2011) Weaving a distributed, semantic social network for mobile users. Springer, Berlin
Wang L, Zhang Y, Feng J (2005) On the Euclidean distance of images. IEEE Trans Pattern Anal Mach Intell 27(8):1334–1339
Wang Y, Jiang Y-C (2008) Detection and parameter estimation of multicomponent lfm signal based on the cubic phase function. EURASIP J Adv Sig Process 2008(1):1–7
Yingjie W, Tang Q, Ni W, Sun Z, Liao S (2013) A clustering hybrid based algorithm for privacy preserving trajectory data publishing. J Comput Res Dev 50(3):578–593
Xin Y, Xie ZQ, Yang J (2017) The privacy preserving method for dynamic trajectory releasing based on adaptive clustering. Inf Sci 378:131–143
Xu J, Wang W, Pei J, Wang X, Shi B, Fu WC (2006) Utility based anonymization using local recoding. In: ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp 785–790
Zhou L, Ding L, Finin T (2011) How is the semantic web evolving, a dynamic social network perspective. Comput Hum Behav 27(4):1294–1302
Acknowledgements
This work was supported by the National Key R & D Program of China Project under Grant 2017YFB0203201 and the Australian Research Council Discovery Projects under Grant DP150104871. The corresponding author is Hong Shen. The authors would like to thank the anonymous reviewers for their suggestions and comments.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Li, S., Shen, H., Sang, Y. et al. An efficient method for privacy-preserving trajectory data publishing based on data partitioning. J Supercomput 76, 5276–5300 (2020). https://doi.org/10.1007/s11227-019-02906-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-019-02906-6