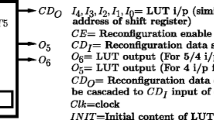
Abstract
The present era has witnessed deployment of reconfigurable hardware or field-programmable gate arrays (FPGAs) in diverse domains like automation and avionics, which are cyber physical in nature. Such cyber physical systems are associated with strict power budgets. Efficient real-time task-scheduling strategies exist that ensure execution of maximum number of tasks within the power budget. However, these do not consider hardware threats into account. Recent literature has exposed the existence of hardware trojan horses (HTHs). HTHs are malicious circuitry that remain dormant during testing and evade detection, but get activated at runtime to jeopardize operations. HTHs can be etched into the FPGA fabric by adversaries in the untrustworthy foundries, during fabrication of the FPGAs. Even vendors selling reconfigurable intellectual properties or bitstreams that configure the FPGA fabric for task operation may insert HTHs during writing the bitstream codes. HTHs may cause a variety of attacks which may affect the basic security primitives of the system like its integrity, confidentiality or availability. In this work, we explore how power draining ability of HTHs may reduce lifetime of the system. A self-aware approach is also proposed which detects the affected resources of the system and eradicates their use in future to facilitate system reliability. An offline–online scheduling strategy is proposed for periodic tasks which can ensure reliability of their operations till the expected lifetime of the system. Accommodating non-periodic tasks in the periodic task schedule based on available power is also focused. For experimentation, we consider tasks associated with EPFL benchmarks and demonstrate results based on the metric task success rate for periodic tasks and metric task rejection rate for non-periodic tasks.














Similar content being viewed by others
Abbreviations
- FPGA:
-
Field-programmable gate array
- IP:
-
Intellectual property
- 3PIP:
-
Third party IP vendor
- HTH:
-
Hardware trojan horse
- HDL:
-
Hardware description language
- DPR:
-
Dynamic partial reconfiguration
- DCM:
-
Dynamic clock management
- PTI:
-
Periodic task interface
- NPTI:
-
Non-periodic task interface
- CU:
-
Control unit
- TIA:
-
Task information analyzer
- EDF:
-
Earliest deadline first
- TSR:
-
Task success rate
- TRR:
-
Task rejection rate
- NPB:
-
Normalized power budget
- NToA:
-
Normalized time of attack
- NTRD:
-
Normalized task relative deadline
- VLSI:
-
Very large scale integration
- fn :
-
Total number of FPGAs
- vn :
-
Total number of 3PIP vendors
- v :
-
Variable which indexes the number of vendors
- b :
-
Total number of bitstreams procured
- t :
-
Time instant
- f :
-
Default operational frequency
- i :
-
Variable used for indexing tasks
- \(T_{i}\) :
-
Task i
- \(\rho _{i}\) :
-
Reconfiguration time of \(T_i\)
- \(\epsilon _{i}\) :
-
Execution time of \(T_i\)
- \(\alpha _{i}\) :
-
Arrival time of \(T_i\)
- \(\delta _{i}\) :
-
Deadline of \(T_i\)
- \(\pi _{i}\) :
-
Periodicity of \(T_i\)
- \(\sigma\) :
-
Total time units in a schedule period
- \(\chi\) :
-
Number of time units required by the control unit to operate
- \(\mu\) :
-
Multiple factor of f
- \(T_{ij}\) :
-
Task \(T_i\) operating on \({{FPGA}}_j\)
- x :
-
Counting index for HTH trigger
- y :
-
Value set by adversary for HTH trigger
- sp :
-
Schedule period
- \(P_{sp}\) :
-
Power dissipation in each schedule period
- n :
-
Total number of schedule periods
- q :
-
Number of FPGAs
- p :
-
Order of unscheduled and available tasks at time t
- \(\zeta\) :
-
Total number of unscheduled and available tasks at time t
- \(\phi\) :
-
Operational frequency of an FPGA
- k :
-
Number of schedules
- S(k):
-
Schedule k
- max(FPGA):
-
Maximum number of FPGAs required for execution of periodic tasks
- min(FPGA):
-
Minimum number of FPGAs required for execution of periodic tasks
- \(COUNT_{FPGA(q)}\) :
-
Number of malicious task executions associated with FPGA(q)
- \(COUNT_{Vendor(v)}\) :
-
Number of malicious task executions associated with bitstreams from Vendor(v)
- s :
-
Number of safe FPGAs
- iqn :
-
Total number of tasks in a schedule to be executed on an FPGA
- iq :
-
Variable which indexes tasks in a schedule to be executed on an FPGA
- \(P_{reference}T_iq\) :
-
Reference power for executing task \(T_{iq}\)
- \(P_{observed}T_iq\) :
-
Observed power for executing task \(T_{iq}\)
- CHECK(q):
-
Variable for fault diagnosis
- npn :
-
Total number of non-periodic tasks
- np :
-
Variable for indexing non-periodic tasks
- Start(AP):
-
Start time of available period for non-periodic task execution
- End(AP):
-
End time of available period for non-periodic task execution
References
Hayashi T, Kojima A, Miyazaki T, Oda N (2014) Application of FPGA to nuclear power plant I&C systems. In: Progress of nuclear safety for symbiosis and sustainability, pp 41–47
Sedcole P, Blodget B, Becker T, Anderson J, Lysaght P (2006) Modular dynamic reconfiguration in Virtex FPGAs. IEE Proc Comput Digit Tech 153(3):157–164
Koc H, Madupu PP (2018) Optimizing energy consumption in cyber physical systems using multiple operating modes. In: IEEE 8th Annual Computing and Communication Workshop and Conference (CCWC), pp 520–525
Sheikh SZ, Pasha MA (2019) Energy-efficient multicore scheduling for hard real-time systems: a survey. ACM Trans Embedded Comput Syst 17(6):1–26
Bambagini M, Marinoni M, Aydin H, Buttazzo G (2016) Energy-aware scheduling for real-time systems: a survey. ACM Trans Embedded Comput Syst 15(1):1–34
Tosun S (2012) Energy and reliability aware task scheduling onto heterogeneous MPSoC architectures. J Supercomput 62:265289
Moghaddas V, Fazeli M, Patooghy A (2016) Reliability-oriented scheduling for static-priority real-time tasks in standby-sparing systems. Microprocess Microsyst 45(Part A):208–215
Bhunia S, Hsiao MS, Banga M, Narasimhan S (2014) Hardware trojan attacks: threat analysis and countermeasures. Proc IEEE 102(8):1229–1247
Liu C, Rajendran J, Yang C, Karri R (2015) Shielding heterogeneous MPSoCs from untrustworthy 3PIPs through security driven task scheduling. IEEE Trans Emerg Top Comput 2(4):461–472
Xiao K, Forte D, Tehranipoor M (2014) A novel built-in self-authentication technique to prevent inserting hardware trojans. IEEE Trans Comput-Aided Des Integr Circuits Syst 33(12):1778–1791
Skorobogatov S (2012) Hardware assurance and its importance to national security. https://www.cl.cam.ac.uk/sps32/secnews.html. Accessed 3 Feb 2020
U.S. Department of Commerce (2010) Defense industrial base assessment: Counterfeit electronics. https://www.bis.doc.gov/index.php/documents/technology-evaluation/37-defense-industrial-base-assessment-of-counterfeit-electronics-2010/file. Accessed 3 Feb 2020
United States Senate: Inquiry into counterfeit electronic parts in the department of defense supply chain. Senate Report of the Committee on Armed Services. https://www.armedservices.senate.gov/imo/media/doc/Counterfeit-Electronic-Parts.pdf, 112 (2012). Accessed 3 Feb 2020
Sarkar SM, Karam R, Krishna A, Bhunia S (2016) Design and validation for FPGA trust under hardware trojan attacks. IEEE Trans Multi-Scale Comput Syst 2(3):186–198
Liu C, Jou J (2001) Efficient coverage analysis metric for HDL design validation. IEE Proc Comput Digit Tech 148(1):1–6
McIntyre D, Wolf F, Papachristou C, Bhunia S, Weyer D (2009) Dynamic evaluation of hardware trust. In: IEEE international workshop on hardware oriented security and trust 2009 (HOST’09), pp 108–111
Guha K, Saha D, Chakrabarti A (2017) Real-time SoC security against passive threats using crypsis behavior of Geckos. ACM J Emerg Technol Comput Syst 13(3):1–26
Guha K, Saha D, Chakrabarti A (2019) Stigmergy-based security for SoC operations from runtime performance degradation of SoC components. ACM Trans Embed Comput Syst 18(2):1–26
Guha K, Saha D, Chakrabarti A (2017) Self aware SoC security to counteract delay inducing hardware trojans at runtime. In: 30th International Conference on VLSI Design, pp 417–422
Chakraborty RS, Wolff F, Paul S, Papachristou C, Bhunia S (2009) MERO: a statistical approach for hardware trojan detection. In: Clavier C, Gaj K (eds) Cryptographic hardware and embedded systems—CHES 2009. Lecture notes in computer Science, vol 5747 (2009)
Narasimhan S, Du D, Chakraborty RS, Paul S, Wolff FG, Papachristou CA, Roy K, Bhunia S (2013) Hardware trojan detection by multiple-parameter side-channel analysis. IEEE Trans Comput 62(11):2183–2195
Love E, Jin Y, Markis Y (2012) Proof-carrying hardware intellectual property: a pathway to trusted module acquisition. IEEE Trans Inf Forensics Secur 7(1):25–40
Xu T, Potkonjak M (2014) Robust and flexible FPGA-based digital PUF. In: 24th International Conference on Field Programmable Logic and Applications, pp 1–6
Amin HAM, Alkabani Y (2014) Selim: system-level protection and hardware trojan detection using weighted voting. J Adv Res 5:499–505
Guha K, Saha D, Chakrabarti A (2015) RTNA: securing SOC architectures from confidentiality attacks at runtime using ART1 neural networks. In: 19th international symposium on VLSI design and test, pp 1–6
Sarma S, Dutt N, Gupta P, Venkatasubramanian N, Nicolau A (2015) Cyber physical system on chip: a self aware MPSoC paradigm with cross-layer virtual sensing and actuation. In: Proceedings of Design, Automation and Test in Europe Conference and Exhibition (DATE), pp 625–628
Guha K., Saha D., Chakrabarti A.: SARP: self aware runtime protection against integrity attacks of hardware trojans. VLSI design and test. In: VDAT 2018. Springer Communications in Computer and Information Science, vol 892, pp 198–209 (2019)
Defense Science Board: Task Force on High Performance Microchip Supply. http://www.acq.osd.mil/dsb/reports/ADA435563.pdf.Feb.2005. Accessed 31 Dec 2019
Saha D, Sur-Kolay S (2016) Embedding of signatures in reconfigurable scan architecture for authentication of intellectual properties in system-on-chip. IET Comput Digit Tech 10(3):110–118
Ramakrishna V, Bhargava L, Sahula V (2018) Novel variability aware path selection for self-referencing based hardware trojan detection. In: 31st International Conference on VLSI Design (VLSID), pp 79–84
Moulik S, Devaraj R, Sarkar A (2019) HEALERS: a heterogeneous energy-aware low-overhead real-time scheduler. IET Comput Digit Tech 13(6):470–480
Baital K, Chakrabarti A (2019) Dynamic scheduling of tasks for multi-core real-time systems based on optimum energy and throughput. IET Comput Digit Tech 13(2):93–100
Bolchini C, Miele A (2013) Reliability-driven system-level synthesis for mixed-critical embedded systems. IEEE Trans Comput 62(12):2489–2502
Mohd BJ, Yousef KMA, AlMajali A, Hayajneh T (2019) Power-aware adaptive encryption. In: IEEE Jordan International Joint Conference on Electrical Engineering and Information Technology (JEEIT), pp 711–716
Guha K, Majumder A, Saha D, Chakrabarti A (2018) Reliability driven mixed critical tasks processing on FPGAs against hardware trojan attacks. In: 2018 21st Euromicro Conference on Digital System Design (DSD), pp 537–544
Guha K, Saha S, Chakrabarti A (2018) SHIRT (self healing intelligent real-time) scheduling for secure embedded task processing. In: 2018 31st International Conference on VLSI Design (VLSID), pp 463–464
Guha K, Majumder A, Saha D, Chakrabarti A (2019) Criticality based reliability against hardware trojan attacks for processing of tasks on reconfigurable hardware. Microprocess Microsyst 71:102865
Rajendran JV, Sinanoglu O, Karri R (2016) Building trustworthy systems using untrusted components: a high-level synthesis approach. IEEE Trans VLSI Syst 24(9):2946–2959
Amar L, Gaillardon PE, De Micheli G (2015) The EPFL combinational benchmark suite. In: 24th international workshop on logic & synthesis (IWLS)
Acknowledgements
This work is supported by the Department of Science and Technology, Government of India, INSPIRE Fellowship No. IF150916 and Intel Final Year Research Fellowship Award 2019 by Intel Corporations, India.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Guha, K., Majumder, A., Saha, D. et al. Dynamic power-aware scheduling of real-time tasks for FPGA-based cyber physical systems against power draining hardware trojan attacks. J Supercomput 76, 8972–9009 (2020). https://doi.org/10.1007/s11227-020-03184-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-020-03184-3