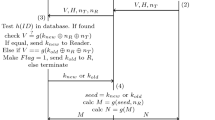
Abstract
RFID systems usually involve passive tags (with limited computing and storage capacity) to secure data exchange via wireless communication. This paper builds an effective lightweight privacy protection authentication protocol, over the XCro, rotation and XOR functions, to handle the privacy and security problems in RFID systems. We employ both BAN Logic and ProVerif to prove that the new protocol is secure, its writing logic is correct, the query results are true and the protocol is free of all common attacks. We also conduct the OPNET simulation to evaluate the performance of our protocol and the existing lightweight protocol of Fan, in terms of authentication time, throughput, bandwidth consumption rate and queuing delay. The obtained results show that our protocol is more secure and effective—because we can resist all of the mentioned common attacks by a more efficient authentication process which involves less calculations, communications and transmissions.
















Similar content being viewed by others
References
Fan K, Jiang W, Li H, Yang Y (2018) Lightweight RFID protocol for medical privacy protection in IoT. IEEE Trans Ind Informat 14(4):1656–1665
Damghani H, Hosseinian H, Damghani L (2019) Investigating attacks to improve security and privacy in RFID systems using the security bit method. In: Proceedings of 2019 5th Conference on Knowledge Based Engineering and Innovation, 2019, pp 833–838
Huang H, Yu P, Liu K (2014) A privacy and authentication protocol for mobile RFID system. In: Proceedings of 2014 IEEE Int’l Symposium on Independent Computing, 2014, pp 1–6
Bernardi P, Gandino F, Lamberti F, Montrucchio B, Rebaudengo M, Sanchez ER (2008) An anti-counterfeit mechanism for the application layer in low-cost RFID devices. In: Proceedings of 2008 4th European Conference on Circuits and Systems for Communications, 2008, pp 227–231
EPC™ Radio-Frequency Identity Protocols Generation-2 UHF RFID Standard (2018) Specification for RFID air interface protocol for communications at 860 MHz–960 MHz, 2018 GS1 AISBL, Release 2.1, Ratified, Jul 2018
Maarof A, Labbi Z, Senhadji M, Belkasmi M (2016) A novel mutual authentication scheme for low-cost RFID systems. In: Proceedings of 2016 Int’l Conference on Wireless Networks and Mobile Communications, Feb 2016, pp 240–245
Noor NM et al (2016) A study of authentication protocols for security of mobile RFID (M-RFID) system. In: Proceedings of 2016 Int’l Conference on Advances in Electrical, Electronic and Systems Engineering, 2016, pp 339–343
Gódor G, Imre S (2011) Elliptic curve cryptography based authentication protocol for low-cost RFID tags. In: Proceedings of 2011 IEEE Int’l Conference on RFID-Technologies and Applications, 2011, pp 386–393
Khan S, AggarwalRK (2019) Efficient mutual authentication mechanism to secure Internet of Things (IoT). In: Proceedings of 2019 Int’l Conference on Machine Learning, Big Data, Cloud and Parallel Computing, 2019, pp 409–412
Xie W, Xie L, Zhang C, Zhang Q, Tang C (2013) Cloud-based RFID authentication. In: Proceedings of 2013 IEEE Int’l Conference on RFID, 2013, pp 168–175
Yu W, Jiang Y (2017) Mobile RFID mutual authentication protocol based on hash function. In: Proceedings of 2017 Int’l Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery, 2017, pp 358–361
He F, Fang Z, Wang D, Wang Q, Hao Y, Wang X (2020) Improved secure lightweight RFID authentication protocol. In: Proceedings of 3rd Int’l Conference on Machine Learning and Machine Intelligence, Sept 2020, pp 127–132
Wu F, Xu L, Kumari S, Li X, Das AK, Shen J (2018) A lightweight and anonymous RFID tag authentication protocol with cloud assistance for e-healthcare applications. J Ambient Intell Humaniz Comput 9(4):919–930
Gabsi S, Beroulle V, Bilgacem H, Machhout M (2019) Architectural choices for implementing a secure ECC-based lightweight RFID tag. In: Proceedinsg of 2019 IEEE Int’l Conference on Design & Test of Integrated Micro & Nano-systems, 2019, pp 1–5
Huang Y, Jiang J (2012) An ultralightweight mutual authentication protocol for EPC C1G2 RFID tags. In: Proceedings of 2012 5th Int’l Symposium on Parallel Architectures, Algorithms and Programming, 2012, pp 133–140
Baghery K, Abdolmaleki B, Akhbari B, Aref MR (2015) Untraceable RFID authentication protocols for EPC compliant tags. In: Proceedings of 2015 23rd Iranian Conference on Electrical Engineering, 2015, pp 426–431
Shi Z, Chen J, Chen S, Ren S (2017) A lightweight RFID authentication protocol with confidentiality and anonymity. In: Proceedings of 2017 IEEE 2nd Advanced Information Technology, Electronic and Automation Control Conference, 2017, pp 1631–1634
Azad S, Ray B (2019) A lightweight protocol for RFID authentication. In: Proceedings of 2019 IEEE Asia-Pacific Conference on Computer Science and Data Engineering, 2019, pp 1–6
Tewari A, Gupta BB (2017) Cryptanalysis of a novel ultra-lightweight mutual authentication protocol for IoT devices using RFID tags. J Supercomput 73(3):1085–1102
Wang K, Chen C, Fang W, Wu T (2018) On the security of a new ultra-lightweight authentication protocol in IoT environment for RFID tags. J Supercomput 74(1):65–70
Burrows M, Abadi M, Needham R (1990) A logic of authentication. ACM Trans Comput Syst 8(1):18–36
[online] Available: https://en.wikipedia.org/wiki/Burrows-Abadi-Needham_logic
[online] Available: https://prosecco.gforge.inria.fr/personal/bblanche/proverif/
Marino F, Massei G, Paura L (2013) Modeling and performance simulation of EPC Gen2 RFID on OPNET. In: Proceedings of 2013 IEEE Int’l Workshop on Measurements & Networking, 2013, pp 83–88
Keil Embeded Development Tool. https://www.keil.com
Zhang X, Hu Y (2015) RFID mutual-authentication protocol with synchronous updated-keys based on Hash function. J China Univ Posts Telecommun 22(6):27–35
Dolev D, Yao A (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208
[online] Available: https://proverif16.paris.inria.fr/index.php
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Chuang, PJ., Tu, YF. Constructing effective lightweight privacy protection in RFID-based systems. J Supercomput 77, 9658–9688 (2021). https://doi.org/10.1007/s11227-021-03656-0
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-021-03656-0