Abstract
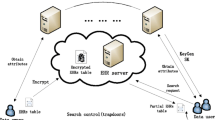
In the Attribute-Based Encryption (ABE) scheme, patients encrypt their electronic health record (EHR), attach the appropriate attributes with it, and outsource them over the cloud. Doctors get the encrypted EHR corresponding to their area of interest (attributes) from the cloud. To decrypt the received encrypted EHR, doctors get the secret keys from the key generation center (KGC). Since the KGC knows the secret keys of all the encrypted EHRs, it may decrypt patients’ records. A decentralized ABE scheme overcomes this issue but requires high computation and communication costs. Moreover, in this scheme, any unauthorized doctor can access the patients’ EHR. Besides, the KGC’s secret keys privacy and the doctor’s attribute privacy are also serious concerns. In this paper, we have proposed a comprehensive privacy-preserving e-health (CP2EH) scheme over the cloud that overcomes the problems of both unauthorized access of patient records by a doctor and a doctor’s attribute privacy in an ABE scheme. In the CP2EH scheme, we have incorporated oblivious transfer (OT) and zero-knowledge proof (ZKP) protocols into the centralized ABE scheme. The OT protocol preserves KGC’s secret keys privacy and the doctor’s attribute privacy. The ZKP protocol preserves the patient’s EHR privacy from unauthorized doctors. Results show that the CP2EH scheme is able to meet all the privacy requirements of e-health applications over the cloud at a lower computation and communication cost as compared to the existing ABE schemes.




Similar content being viewed by others
References
Agrawal R, Kiernan J, Srikant R, Xu Y (2004) Order preserving encryption for numeric data. In: Proceedings of the 2004 ACM SIGMOD International Conference on Management of Data, pp 563–574
BEIMEL A (1996) Secure schemes for secret sharing and key distribution. PhD thesis, Israel Institute of Technology, Technion
Bethencourt J, Sahai A, Waters B (2007) Ciphertext-policy attribute-based encryption. In: 2007 IEEE Symposium on Security and Privacy (SP’07), IEEE, pp 321–334
Boldyreva A, Chenette N, Lee Y, O’neill A (2009) Order-preserving symmetric encryption. In: Annual International Conference on the Theory and Applications of Cryptographic Techniques, Springer, pp 224–241
Boldyreva A, Chenette N, O’Neill A (2011) Order-preserving encryption revisited: improved security analysis and alternative solutions. In: Annual Cryptology Conference, Springer, pp 578–595. Springer
Boneh D, Franklin M (2001) Identity-based encryption from the weil pairing. In: Annual International Cryptology Conference, Springer, pp 213–229
Boneh D, Lewi K, Raykova M, Sahai A, Zhandry M, Zimmerman J (2015) Semantically secure order-revealing encryption: multi-input functional encryption without obfuscation. In: Annual International Conference on the Theory and Applications of Cryptographic Techniques, Springer, pp 563–594
Camenisch J, Shoup V (2003) Practical verifiable encryption and decryption of discrete logarithms. In: Annual International Cryptology Conference, Springer, pp 126–144
Cheng N, Lyu F, Chen J, Xu W, Zhou H, Zhang S, Shen XS (2018) Big data driven vehicular networks. IEEE Netw 32(6):160–167
Du M, Wang Q, He M, Weng J (2018) Privacy-preserving indexing and query processing for secure dynamic cloud storage. IEEE Tran Inf Forensic Secur 13(9):2320–2332
Hazay C, Lindell Y (2010) Efficient secure two-party protocols: techniques and constructions. Springer
Hoffstein J, Pipher J, Silverman JH, Silverman JH (2008) An introduction to mathematical cryptography, vol 1. Springer
Huang C, Lu R, Lin X, Shen X (2018) Secure automated valet parking: a privacy-preserving reservation scheme for autonomous vehicles. IEEE Trans Vehic Technol 67(11):11169–11180
Huang C, Lu R, Zhu H, Shao J, Lin X (2016) Fssr: fine-grained ehrs sharing via similarity-based recommendation in cloud-assisted ehealthcare system. In: Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, pp 95–106
Kerschbaum F (2015) Frequency-hiding order-preserving encryption. In: Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, pp 656–667
Kerschbaum F, Schröpfer A (2014) Optimal average-complexity ideal-security order-preserving encryption. In: Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, pp 275–286
Lewi K, Wu DJ (2016) Order-revealing encryption: new constructions, applications, and lower bounds. In: Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, pp 1167–1178
Li J, Zhang Y, Ning J, Huang X, Poh GS, Wang D (2020) Attribute based encryption with privacy protection and accountability for cloudiot. IEEE Trans Cloud Comput 01:1–1
Liang J, Qin Z, Xiao S, Ou L, Lin X (2019) Efficient and secure decision tree classification for cloud-assisted online diagnosis services. IEEE Trans Depend Secur Comput 01:1–1
Liang J, Qin Z, Xiao S, Zhang J, Yin H, Li K (2020) Privacy-preserving range query over multi-source electronic health records in public clouds. J Parallel Distrib Comput 135:127–139
Liang P, Zhang L, Kang L, Ren J (2019) Privacy-preserving decentralized abe for secure sharing of personal health records in cloud storage. J Inf Secur Appl 47:258–266
Liu Q, Wang G, Li F, Yang S, Wu J (2016) Preserving privacy with probabilistic indistinguishability in weighted social networks. IEEE Trans Parallel Distrib Syst 28(5):1417–1429
Liu X, Liu Q, Peng T, Wu J (2017) Dynamic access policy in cloud-based personal health record (phr) systems. Inf Sci 379:62–81
Lyu F, Zhu H, Cheng N, Zhou H, Xu W, Li M, Shen X (2019) Characterizing urban vehicle-to-vehicle communications for reliable safety applications. IEEE Trans Intel Transp Syst 21(6):2586–2602
Noor TH, Zeadally S, Alfazi A, Sheng QZ (2018) Mobile cloud computing: challenges and future research directions. J Netw Comput Appl 115:70–85
Ou L, Qin Z, Liao S, Hong Y, Jia X (2018) Releasing correlated trajectories: towards high utility and optimal differential privacy. IEEE Trans Depend Secur Comput 17(5):1109–1123
Popa RA, Li FH, Zeldovich N (2013) An ideal-security protocol for order-preserving encoding. In: 2013 IEEE Symposium on Security and Privacy, IEEE, pp 463–477
Popa RA, Redfield CM, Zeldovich N, Balakrishnan H (2011) Cryptdb: protecting confidentiality with encrypted query processing. In: Proceedings of the Twenty-Third ACM Symposium on Operating Systems Principles, pp 85–100
Pournaghi SM, Bayat M, Farjami Y (2020) Medsba: a novel and secure scheme to share medical data based on blockchain technology and attribute-based encryption. J Amb Intel Hum Comput 1–29
Rahulamathavan Y, Veluru S, Han J, Li F, Rajarajan M, Lu R (2016) User collusion avoidance scheme for privacy-preserving decentralized key-policy attribute-based encryption. IEEE Trans Comput 65(9):2939–2946
Rivest RL, Shamir A, Adleman LM (1983) Cryptographic communications system and method, US Patent 4,405,829
Roche DS, Apon D, Choi SG, Yerukhimovich A (2016) Pope: Partial order preserving encoding. In: Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, pp 1131–1142
Schnorr CP (1989) Efficient identification and signatures for smart cards. In: Conference on the Theory and Application of Cryptology, Springer, pp 239–252
Sun PJ (2020) Security and privacy protection in cloud computing: discussions and challenges. J Netw Comput Appl 102642
Wang Q, Du M, Chen X, Chen Y, Zhou P, Chen X, Huang X (2018) Privacy-preserving collaborative model learning: the case of word vector training. IEEE Trans Knowl Data Eng 30(12):2381–2393
Wang Q, He M, Du M, Chow SS, Lai RW, Zou Q (2016) Searchable encryption over feature-rich data. IEEE Trans Depend Secur Comput 15(3):496–510
Waters B (2011) Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In: International Workshop on Public Key Cryptography, Springer, pp 53–70
Xiao L, Yen IL, Huynh DT (2012) Extending order preserving encryption for multi-user systems. IACR Cryptol ePrint Arch 2012:192
Yang A, Xu J, Weng J, Zhou J, Wong DS (2018) Lightweight and privacy-preserving delegatable proofs of storage with data dynamics in cloud storage. IEEE Trans Cloud Comput 01:1–1
Yao X, Lin Y, Liu Q, Long S (2015) Efficient and privacy-preserving search in multi-source personal health record clouds. In: 2015 IEEE Symposium on Computers and Communication (ISCC), IEEE, pp 803–808
Yao X, Lin Y, Liu Q, Zhang J (2018) Privacy-preserving search over encrypted personal health record in multi-source cloud. IEEE Access 6:3809–3823
Yin H, Qin Z, Zhang J, Ou L, Li K (2017) Achieving secure, universal, and fine-grained query results verification for secure search scheme over encrypted cloud data. IEEE Trans Cloud comput 01:1–1
Zhang L, Liang P, Mu Y (2018) Improving privacy-preserving and security for decentralized key-policy attributed-based encryption. IEEE Access 6:12736–12745
Zhang Y, Xu C, Lin X, Shen XS (2019) Blockchain-based public integrity verification for cloud storage against procrastinating auditors. IEEE Trans Cloud Comput 01:1–1
Zhong H, Zhu W, Xu Y, Cui J (2018) Multi-authority attribute-based encryption access control scheme with policy hidden for cloud storage. Soft Comput 22(1):243–251
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yadav, V.K., Yadav, R.K., Verma, S. et al. CP2EH: a comprehensive privacy-preserving e-health scheme over cloud. J Supercomput 78, 2386–2416 (2022). https://doi.org/10.1007/s11227-021-03967-2
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-021-03967-2