Abstract
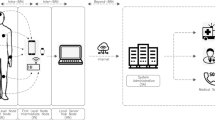
Health-care is one of the major concerns for every individual; however, it is not always possible to physically visit the health-care center in emergency situations. In such situations, remote health-care monitoring is beneficial, which can be provided by remote health-care monitoring applications based on wireless body area networks (WBANs). Since the communication in WBANs is carried over a public channel, their security becomes a paramount concern. Many schemes aimed to achieve secure and efficient communication in WBANs, but their own flaws impaired them. In this paper, we cryptanalyze Fotouhi et al.’s scheme and find that it is vulnerable to various attacks, namely privileged insider attack, sensor node capture attack, denial-of-service, desynchronization attack, replay attack, and stolen-verifier attack. It also lacks confidentiality and anonymity. Hence, we propose a new four-factor mutual authentication scheme for health-care based on WBANs that overcomes these issues and has better performance as it uses lightweight cryptographic primitives. The robustness of this scheme is verified formally using the Real-Or-Random model and Burrows–Abadi–Needham logic and informally through the state-of-the-art security analysis. Additionally, we verify the system’s security using the automated validation of Internet security protocols and applications tool-based automated simulation. Finally, we provide a comparative study of security and performance to show its efficacy in real-life applications.










Similar content being viewed by others
References
Kira Alex R (2013) The factors affecting gross domestic product (gdp) in developing countries: The case of Tanzania
Vani Rajasekar J, Sathya Premalatha K, Muzafer S (2021) Secure remote user authentication scheme on health care, iot and cloud applications: a multilayer systematic survey. Acta Polytechnica Hungarica 18(3):87–106
Chang L, Qing Z, Holroyd Kenneth A, Seng Elizabeth K (2011) Status and trends of mobile-health applications for ios devices: a developer’s perspective. J Syst Softw 84(11):2022–2033
Pardeep K, Sang-Gon L, Hoon-Jae L (2012) E-sap: efficient-strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors 12(2):1625–1647
Debiao H, Neeraj K, Jianhua C, Cheng-Chi L, Naveen C, Seng-Soo Y (2015) Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multim Syst 21(1):49–60
Qi J, Jianfeng M, Xiang L, Youliang T (2014) Robust chaotic map-based authentication and key agreement scheme with strong anonymity for telecare medicine information systems. J Med Syst 38(2):1–8
Jun Z, Zhenfu C, Xiaolei D, Naixue X, Vasilakos Athanasios V (2015) 4s: A secure and privacy-preserving key management scheme for cloud-assisted wireless body area network in m-healthcare social networks. Inform Sci 314:255–276
Limin MY, Yuesheng Z (2014) Tinyzkp: a lightweight authentication scheme based on zero-knowledge proof for wireless body area networks. Wireless Personal Commun 77(2):1077–1090
Jingwei L, Qian L, Rui Y, Sun R (2015) Efficient authenticated key exchange protocols for wireless body area networks. EURASIP J Wireless Commun Netw 1:1–11
Hamada Ibrahim M, Saru K, Kumar Das A, Mohammad W, Vanga O (2016) Secure anonymous mutual authentication for star two-tier wireless body area networks. Computer Methods Programs Biomed 135:37–50
Gaimei G, Xinguang P, Ye T, Zefeng Q (2016) A chaotic maps-based authentication scheme for wireless body area networks. Int J Distrib Sensor Netw 12(7):2174720
Kumar Das Ashok, Kumar Sutrala Anil, Vanga Odelu, Adrijit Goswami (2017) A secure smartcard-based anonymous user authentication scheme for healthcare applications using wireless medical sensor networks. Wireless Personal Commun 94(3):1899–1933
Fan W, Lili X, Saru K, Xiong L (2017) An improved and anonymous two-factor authentication protocol for health-care applications with wireless medical sensor networks. Multim Syst 23(2):195–205
Jangirala S, Dheerendra M, Sourav M (2017) A mutual authentication framework for wireless medical sensor networks. J Med Syst 41(5):80
Ruhul A, Hafizul Islam SK, Biswas GP, Khurram Khan M, Neeraj K (2018) A robust and anonymous patient monitoring system using wireless medical sensor networks. Fut Gener Computer Syst 80:483–495
Xu Y, Wang H, Li Z, Chen S, Hu B, Zou S (2017) A survey on secure wireless body area networks. Secur Commun Netw 1–9:2017
Peyman D, Hossein Jahangir A (2018) A biometric security scheme for wireless body area networks. J Inf Secur Appl 41:62–74
Mohammad W, Kumar Das A, Vasilakos Athanasios V (2018) Authenticated key management protocol for cloud-assisted body area sensor networks. J Netw Computer Appl 123:112–126
Fan W, Xiong L, Kumar Sangaiah A, Lili X, Kumari Saru W, Liuxi Shen J (2018) A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Fut Gener Computer Syst 82:727–737
Mahdi F, Majid B, Kumar Das A, Nasib Far Hossein A, Morteza Pournaghi S, Doostari MA (2020) A lightweight and secure two-factor authentication scheme for wireless body area networks in health-care iot. Computer Netw 177:107333
Canetti R, Krawczyk H (2001) Analysis of key-exchange protocols and their use for building secure channels. In International Conference on the Theory and Applications of Cryptographic Techniques, pages 453–474. Springer
Danny D, Andrew Y (1983) On the security of public key protocols. IEEE Trans Inf Theor 29(2):198–208
Al-Hussain Arwa, Al-Rassan Iehab (2010) A biometric-based authentication system for web services mobile user. In Proceedings of the 8th International Conference on Advances in Mobile Computing and Multimedia, pages 447–452,
Ohood A, Mznah A-R, Abdullah A-D (2013) An efficient biometric authentication protocol for wireless sensor networks. Int J Distrib Sensor Netw 9(5):407971
Wei-Chi K, Shen-Tien C (2005) Impersonation attack on a dynamic id-based remote user authentication scheme using smart cards. IEICE Trans Commun 88(5):2165–2167
Wu Zhizheng, Gao Sheng, Cling Eng Siong, Li Haizhou (2014) A study on replay attack and anti-spoofing for text-dependent speaker verification. In Signal and Information Processing Association Annual Summit and Conference (APSIPA), 2014 Asia-Pacific, pages 1–5. IEEE
Vinod K, Rajendra K, Pandey SK (2020) Polynomial based non-interactive session key computation protocol for secure communication in dynamic groups. Int J Inf Technol 12(1):283–288
Sarvabhatla Mrudula, Reddy M Chandra Mouli, Vorugunti Chandra Sekhar (2015) A robust remote user authentication scheme resistant to known session specific temporary information attack. In 2015 Applications and Innovations in Mobile Computing (AIMoC), pages 164–169. IEEE
Alsalhi Israa N, Albermany Salah A Authentication of crns by using ban logic
Mohammad W, Kumar Das A, Neeraj K, Vasilakos Athanasios V (2019) Design of secure key management and user authentication scheme for fog computing services. Fut Gener Computer Syst 91:475–492
Abdalla Michel, Chevassut Olivier, Fouque Pierre-Alain, Pointcheval David (2005) A simple threshold authenticated key exchange from short secrets. In International Conference on the Theory and Application of Cryptology and Information Security, pages 566–584. Springer
Armando Alessandro, Basin David, Boichut Yohan, Chevalier Yannick, Compagna Luca, Cuéllar Jorge, Drielsma P Hankes, Héam Pierre-Cyrille, Kouchnarenko Olga, Mantovani Jacopo, et al. (2005) The avispa tool for the automated validation of internet security protocols and applications. In International Conference on Computer Aided Verification, pages 281–285. Springer
Fan W, Lili X, Saru K, Xiong L (2015) A novel and provably secure biometrics-based three-factor remote authentication scheme for mobile client-server networks. Computers Elect Eng 45:274–285
Lili X, Fan W (2015) Cryptanalysis and improvement of a user authentication scheme preserving uniqueness and anonymity for connected health care. J Med Syst 39(2):1–9
Kumar Das A, Kumar Sutrala A, Saru K, Vanga O, Mohammad W, Xiong L (2016) An efficient multi-gateway-based three-factor user authentication and key agreement scheme in hierarchical wireless sensor networks. Secur Commun Netw 9(13):2070–2092
Shnayder Victor, Hempstead Mark, Chen Bor-rong, Allen Geoff Werner, Welsh Matt (2004) Simulating the power consumption of large-scale sensor network applications. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, pages 188–200
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Rangwani, D., Om, H. Four-factor mutual authentication scheme for health-care based on wireless body area network. J Supercomput 78, 5744–5778 (2022). https://doi.org/10.1007/s11227-021-04099-3
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-021-04099-3