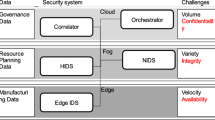
Abstract
Owing to the fourth industrial revolution, collaborations between companies and various technologies have become indispensable, particularly in the manufacturing industry. However, technology leakage is likely to occur among cooperative partners where the ratio of small- and medium-sized enterprises is relatively high because of low-security resources. To address this security management problem, we analyzed existing literature and designed a reference model and questions to evaluate security levels reflecting partners’ characteristics to be managed by the manufacturing parent company. We conducted an expert survey to verify the designed model and calculated the weight of each evaluation area. Consequently, we designed a reference model to effectively evaluate, from the perspective of the parent company, partners in manufacturing. We anticipate that the results of this study will assist a parent company in securely sharing data and technologies with partners and being used as a self-diagnosis tool by partners to evaluate its security levels.






Similar content being viewed by others
References
Vimal S, Jesuva AS, Bharathiraja S, Guru S, Jackins V (2021) Reducing latency in smart manufacturing service system using edge computing. J Platform Technol 9(1):15–22
Gul MJ, Rehman A, Paul A, Rho S, Riaz R, Kim J (2020) Blockchain expansion to secure assets with fog node on special duty. Soft Comput 24(20):15209–15221. https://doi.org/10.1007/s00500-020-04857-0
Smith R, Barry R (2019) America’s Electric grid has a vulnerable back door – and russia walked through it. Wall Street J. https://www.wsj.com/articles/americas-electric-grid-has-a-vulnerable-back-doorand-russia-walked-through-it-11547137112?mod=article_inline, Accessed 2022/06/02.
Deloitte, MAPI (2016) cyber risk in advanced manufacturing. United States of America
WIPO https://www.wipo.int/tradesecrets/en/. last accessed 2022.06.04.
Yu HR, Chang HB (2020) A meta-analysis of industrial security research for sustainable organizational growth. Sustainability 12(22):9526. https://doi.org/10.3390/su12229526
Gul MJ, Rabia R, Jararweh Y, Rathore MM, and Paul A. (2019). Security flaws of operating system against live device attacks: a case study on live linux distribution device. In: 2019 Sixth International Conference on Software Defined Systems (SDS), IEEE, pp 154–159
Khalil MI, Kim R, Seo CY (2020) Challenges and opportunities of big data. J Plat Tech 8(2):3–9
Lee JM (2013) Internal control management methodology designed for the industrial technology protection and leakage prevention: case studies on the improved security management system of the manufacturer's suppliers. Dissertation, Korea University
Kim IH, Lee KH (2017) Evaluation model of the contracting company’s security management using the DEA model. J Korea Inst Inf Security Cryptol 27(3):687–704. https://doi.org/10.13089/JKIISC.2017.27.3.687
Kim JW, Lee CW, Chang HB (2020) The development of a security evaluation model focused on information leakage protection for sustainable growth. Sustainability 12(24):10639. https://doi.org/10.3390/su122410639
Noh SY, Lim JI (2017) A study for enterprise type realtime information security management system. J Korea Inst Inf Security Cryptol 27.3:617–636. https://doi.org/10.13089/JKIISC.2017.27.3.617
Ahn BG, Yu HR, Chang HB (2020) A research on activating factor for cultivating a proactive organizational security culture. Converg Security J 20(2):3–13. https://doi.org/10.33778/kcsa.2020.20.2.003
Bae ST, Kim JH (2013) A study on development of the evaluation model about level of security in national R&D program. J Korean Assoc Comput Educ 16(1):73–80
Wei YC, Wu WC, Chu YC (2018) Performance evaluation of the recommendation mechanism of information security risk identification. Neurocomputing 279:48–53. https://doi.org/10.1016/j.neucom.2017.05.106
Ministry of Trade, Industry and Energy, Korean Association for Industrial Technology Security (2017) Industrial technology protection guidelines and manuals. Korea.
Small and Medium Business Administration of Korea (SMBA), Large & Small Business Cooperation Foundation Korea, Rural Affairs (2016) SME technology protection guidelines. Korea.
Ministry of Science and ICT (2014). National R & D Business Security Management Standard Manual. Korea
Korea Industrial Technology Association, Small and Medium Business Administration (SMBA), Korea Technology and Information Promotion Agency for SMEs (2007). Manual to respond to technology leakage for SMEs. Korea.
Mullet V, Sondi P, Ramat E (2021) A review of cybersecurity guidelines for manufacturing factories in industry 4.0. IEEE Access 9:23235–23263. https://doi.org/10.1109/ACCESS.2021.3056650
Johansson K, Paulsson T, Bergström E, Seigerroth U (2022) Improving Cybersecurity Awareness Among SMEs in the Manufacturing Industry. In: SPS2022. IOS Press, Amsterdam, pp 209–220. https://doi.org/10.3233/ATDE220140
Corallo A, Lazoi M, Lezzi M, Pontrandolfo P (2021) Cybersecurity Challenges for Manufacturing Systems 4.0: Assessment of the Business Impact Level. IEEE Trans Eng Manage. 1109/TEM.2021.3084687
Saaty TL, Vargas LG (2012) The seven pillars of the analytic hierarchy process. In: Models, methods, concepts and applications of the analytic hierarchy process. Springer, Boston, MA, pp 23–40
Korea Development Institute (2008) Study on Modification and improvement of general guidelines to perform preliminary feasibility study, the 5th edn. Korea
Kim DG, Park YW, Lee SM (2007) Assessment of tourism resource development by the analytic hierarchy process: focusing on the planning process. Int J Tour Hosp Res 21:5–18
Saaty TL (2008). Relative measurement and its generalization in decision making why pairwise comparisons are central in mathematics for the measurement of intangible factors in the analytic hierarchy/network process. RACSAM-Revista de la Real Academia de Ciencias Exactas, Fisicas y Naturales. Serie A. Matematicas, 102(2):251–318. https://doi.org/10.1007/BF03191825
Chen X, Chen R, Yang C (2022) Research to key success factors of intelligent logistics based on IoT technology. J Supercomput 78(3):3905–3939. https://doi.org/10.1007/s11227-021-04009-7
Acknowledgements
This paper was supported by Korea Institute for Advancement of Technology (KIAT) grant funded by the Korea Government (MOTIE) (P0008703, The Competency Development Program for Industry Specialist).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declared that they have no conflicts of interest to this work.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Choi, Y., Chang, H. Design of evaluation items of the security levels for suppliers in the manufacturing industry. J Supercomput 79, 11707–11742 (2023). https://doi.org/10.1007/s11227-023-05101-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-023-05101-w