Abstract
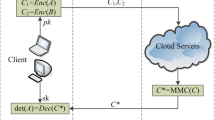
Fully homomorphic encryption (FHE) is capable of handling sensitive encrypted data in untrusted computing environments. The efficient application of FHE schemes in secure outsourced computation can effectively address security and privacy concerns. This paper presents a novel fully homomorphic encryption scheme called GMS, based on the n-secret learning with errors (LWE) assumption. By utilizing block matrix and decomposition technology, GMS achieves shorter encryption and decryption times and smaller ciphertext sizes compared to existing FHE schemes. For secure outsourced matrix multiplication \({\textbf {A}}_{m\times n}\cdot {\textbf {B}}_{n\times l}\) with arbitrary dimensions, GMS only requires \(O(\max \{m,n,l\})\) rotations and one homomorphic multiplication. Compared to the state-of-the-art methods, our approach stands out by achieving a significant reduction in the number of rotations by a factor of \(O(\log \max \{n, l\})\), along with a decrease in the number of homomorphic multiplications by a factor of n and \(O(\min \{m, n, l\})\). The experimental results demonstrate that GMS shows superior performance for secure outsourced matrix multiplication of any dimension. For example, when encrypting a \(64\times 64\)-dimensional matrix, the size of the ciphertext is only 1.27 MB. The encryption and decryption process takes approximately 0.2 s. For matrix multiplication \({\textbf {A}}_{64\times 64}\cdot {\textbf {B}}_{64\times 64}\), the runtime of our method is 39.98 s, achieving a speedup of up to 5X and 2X.



Similar content being viewed by others
Data availability
The data is available upon request.
References
Zhang P, Huang T, Sun X et al (2023) Privacy-preserving and outsourced multi-party k-means clustering based on multi-key fully homomorphic encryption. IEEE Trans Dependable Secure Comput 20(3):2348–2359. https://doi.org/10.1109/tdsc.2022.3181667
Zhao L, Chen L (2018) Sparse matrix masking-based non-interactive verifiable (outsourced) computation, revisited. IEEE Trans Dependable Secure Comput 17(6):1188–1206. https://doi.org/10.1109/tdsc.2018.2861699
Duong DH, Mishra PK, Yasuda M (2016) Efficient secure matrix multiplication over lwe-based homomorphic encryption. Tatra Mt Math Publ 67(1):69–83. https://doi.org/10.1515/tmmp-2016-0031
Huang H, Zong H (2023) Secure matrix multiplication based on fully homomorphic encryption. J Supercomput 79(5):5064–5085. https://doi.org/10.1007/s11227-022-04850-4
Zhu L, Hua Q, Chen Y, et al (2023) Secure outsourced matrix multiplication with fully homomorphic encryption. In: European Symposium on Research in Computer Security, Springer, pp 249–269, https://doi.org/10.1007/978-3-031-50594-2_13
Hiromasa R, Abe M, Okamoto T (2016) Packing messages and optimizing bootstrapping in gsw-fhe. IEICE Trans Fundam Electron Commun Comput Sci 99(1):73–82. https://doi.org/10.1587/transfun.e99.a.73
Van DM, Gentry C, Halevi S, et al (2010) Fully homomorphic encryption over the integers. In: Advances in Cryptology—EUROCRYPT 2010: 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, May 30–June 3, 2010. Proceedings 29, Springer, pp 24–43
Regev O (2009) On lattices, learning with errors, random linear codes, and cryptography. J ACM (JACM) 56(6):1–40. https://doi.org/10.1145/1568318.1568324
L\(\acute{o}\)pez-Alt A, Tromer E, Vaikuntanathan V, (2012) On-the-fly multiparty computation on the cloud via multikey fully homomorphic encryption. IACR Cryptol ePrint Arch 2013:94. https://doi.org/10.1145/2213977.2214086
Regev O (2010) The learning with errors problem. Invit Surv CCC 7(30):11. https://doi.org/10.1109/ccc.2010.26
Brakerski Z, Gentry C, Vaikuntanathan V (2014) (leveled) fully homomorphic encryption without bootstrapping. ACM Trans Comput Theory (TOCT) 6(3):1–36. https://doi.org/10.1145/2633600
Gentry C, Sahai A, Waters B (2013) Homomorphic encryption from learning with errors: Conceptually-simpler, asymptotically-faster, attribute-based. In: Advances in Cryptology–CRYPTO 2013: 33rd Annual Cryptology Conference, Santa Barbara, CA, USA, August 18–22, 2013. Proceedings, Part I, Springer, pp 75–92, https://doi.org/10.1007/978-3-642-40041-4_5
Cheon JH, Kim A, Kim M, et al (2017) Homomorphic encryption for arithmetic of approximate numbers. In: Advances in Cryptology—ASIACRYPT 2017: 23rd International Conference on the Theory and Applications of Cryptology and Information Security, Hong Kong, China, December 3–7, 2017, Proceedings, Part I 23, Springer, pp 409–437, https://doi.org/10.1007/978-3-319-70694-8_15
Chillotti I, Gama N, Georgieva M et al (2020) Tfhe: fast fully homomorphic encryption over the torus. J Cryptol 33(1):34–91. https://doi.org/10.1007/s00145-019-09319-x
Benarroch D, Brakerski Z, Lepoint T (2017) Fhe over the integers: decomposed and batched in the post-quantum regime. In: IACR International Workshop on Public Key Cryptography, Springer, pp 271–301, https://doi.org/10.1007/978-3-662-54388-7_10
Canteaut A, Carpov S, Fontaine C et al (2018) Stream ciphers: a practical solution for efficient homomorphic-ciphertext compression. J Cryptol 31(3):885–916. https://doi.org/10.1007/s00145-017-9273-9
Genise N, Gentry C, Halevi S, et al (2019) Homomorphic encryption for finite automata. In: Advances in Cryptology—ASIACRYPT 2019: 25th International Conference on the Theory and Application of Cryptology and Information Security, Kobe, Japan, December 8–12, 2019, Proceedings, Part II 25, Springer, pp 473–502
Pereira HVL (2020) Efficient agcd-based homomorphic encryption for matrix and vector arithmetic. In: International Conference on Applied Cryptography and Network Security, Springer, pp 110–129, https://doi.org/10.1007/978-3-030-57808-4_6
Atallah MJ, Pantazopoulos KN, Rice JR, et al (2002) Secure outsourcing of scientific computations. In: Advances in Computers, vol 54. Elsevier, pp 215–272
Lei X, Liao X, Huang T et al (2014) Achieving security, robust cheating resistance, and high-efficiency for outsourcing large matrix multiplication computation to a malicious cloud. Inf Sci 280:205–217. https://doi.org/10.1016/j.ins.2014.05.014
Fu S, Yu Y, Xu M (2017) A secure algorithm for outsourcing matrix multiplication computation in the cloud. In: Proceedings of the Fifth ACM international workshop on security in cloud computing, pp 27–33, https://doi.org/10.1145/3055259.3055263
Halevi S, Shoup V (2014) Algorithms in helib. In: Advances in Cryptology—CRYPTO 2014: 34th Annual Cryptology Conference, Santa Barbara, CA, USA, August 17–21, 2014, Proceedings, Part I 34, Springer, pp 554–571, https://doi.org/10.1007/978-3-662-44371-2_31
Lu W, Kawasaki S, Sakuma J (2017) Using fully homomorphic encryption for statistical analysis of categorical, ordinal and numerical data. In: Proceedings 2017 Network and Distributed System Security Symposium, Internet Society, https://doi.org/10.14722/ndss.2017.23119
Wang S, Huang H (2019) Secure outsourced computation of multiple matrix multiplication based on fully homomorphic encryption. KSII Trans Internet Inf Syst (TIIS) 13(11):5616–5630. https://doi.org/10.3837/tiis.2019.11.019
Lu W, Sakuma J (2018) More practical privacy-preserving machine learning as a service via efficient secure matrix multiplication. In: Proceedings of the 6th Workshop on Encrypted Computing and Applied Homomorphic Cryptography, pp 25–36, https://doi.org/10.1145/3267973.3267976
Jiang X, Kim M, Lauter K, et al (2018) Secure outsourced matrix computation and application to neural networks. In: Proceedings of the 2018 ACM SIGSAC conference on computer and communications security, pp 1209–1222, https://doi.org/10.1145/3243734.3243837
Micciancio D, Walter M (2017) Gaussian sampling over the integers: Efficient, generic, constant-time. In: Advances in Cryptology—CRYPTO 2017: 37th Annual International Cryptology Conference, Santa Barbara, CA, USA, August 20–24, 2017, Proceedings, Part II 37, Springer, pp 455–485, https://doi.org/10.1007/978-3-319-63715-0_16
Genise N, Micciancio D, Polyakov Y (2019) Building an efficient lattice gadget toolkit: Subgaussian sampling and more. In: Advances in Cryptology—EUROCRYPT 2019: 38th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Darmstadt, Germany, May 19–23, 2019, Proceedings, Part II 38, Springer, pp 655–684, https://doi.org/10.1007/978-3-030-17656-3_23
Katz J, Lindell Y (2020) Introduction to modern cryptography, 3rd edn. Chapman and Hall CRC, London. https://doi.org/10.1201/9781351133036
Author information
Authors and Affiliations
Contributions
Jianxin Gao wrote the main manuscript text, performed the main simulation experiment and prepared the figures and tables. Ying Gao reviewed and edited the manuscript, provided supervision and guidance on the research topics and provided funding and project support. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Gao, J., Gao, Y. GMS: an efficient fully homomorphic encryption scheme for secure outsourced matrix multiplication. J Supercomput 80, 26435–26461 (2024). https://doi.org/10.1007/s11227-024-06449-3
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-024-06449-3