Abstract
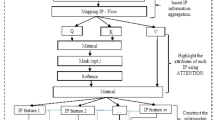
Network security situation assessment (NSSA) has become increasingly critical due to the growing frequency and sophistication of network attacks. NSSA involves analyzing network threats and security incidents to support network administrators in decision-making and the implementation of protective strategies. To address the challenges of low assessment accuracy in current NSSA methods, we propose a novel model that integrates an enhanced black-winged kite algorithm (BKA) with a cross dual-channel framework. First, we develop a cross dual-channel architecture that combines a convolutional neural network with a bidirectional long short-term memory network. This structure effectively integrates temporal and spatial features; while, an attention mechanism highlights key information, thereby improving the accuracy of traffic classification. Second, the improved BKA is employed to optimize network parameters, further enhancing the model’s overall performance. Finally, the situation value is derived from the classification results and mapped to corresponding network security situation levels, completing the NSSA process. Experimental results on the NSL-KDD dataset demonstrate that the proposed model achieves notable improvements, with an accuracy of 83.66%, a recall of 80.04%, and an F1-score of 83.13%. Moreover, the proposed assessment method offers a more robust and comprehensive evaluation of the network’s overall security status, highlighting its potential for practical application.














Similar content being viewed by others
Data availability
No datasets were generated or analysed during the current study.
References
Zhang Z, Ning H, Shi F et al (2022) Artificial intelligence in cyber security: research advances, challenges, and opportunities. Artif Intell Rev 55:1–25
Rathore S, Sharma PK, Loia V et al (2017) Social network security: Issues, challenges, threats, and solutions. Inf Sci 421:43–69
Zhao D, Liu J (2018) Study on network security situation awareness based on particle swarm optimization algorithm. Comput Ind Eng 125:764–775
Bass T (1999) Multisensor data fusion for next generation distributed intrusion detection systems. In: Proceedings of the IRIS National Symposium on Sensor and Data Fusion. Citeseer, 24(28), pp 24–27
Cheng X, Lang S (2012) Research on network security situation assessment and prediction. In: 2012 4th International Conference on Computational and Information Sciences. IEEE, pp 864–867
Abasi A (2014) A network security situational awareness model based on information fusion. Adv Mater Res 846:1632–1635
Liu X, Yu J, Wang ML (2009) Network security situation generation and evaluation based on heterogeneous sensor fusion. In: 2009 5th International Conference on Wireless Communications, Networking and Mobile Computing. IEEE, pp 1–4
Zhang Q, Ma D (2021) Research on network security analysis based on big data technology application. J Phys Conf Ser IOP Publ 1744(3):032199
Ding X, Tian Y, Yu Y (2015) A real-time big data gathering algorithm based on indoor wireless sensor networks for risk analysis of industrial operations. IEEE Trans Ind Inf 12(3):1232–1242
He Y, Yu FR, Zhao N et al (2016) Big data analytics in mobile cellular networks. IEEE access 4:1985–1996
Chopade P, Zhan J, Bikdash M (2015) Node attributes and edge structure for large-scale big data network analytics and community detection. In: 2015 IEEE international symposium on technologies for homeland security (HST). IEEE, pp 1–8
Leau YB, Manickam S, Chong YW (2015) Network security situation assessment: a review and discussion. In: Kim K (ed) Information science and applications. lecture notes in electrical engineering, vol 339. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-662-46578-3_48
Saaty TL (2004) Decision making—the analytic hierarchy and network processes (AHP/ANP). J Syst Sci Syst Eng 13:1–35
Stach W, Kurgan L, Pedrycz W (2005) A survey of fuzzy cognitive map learning methods[J]. Issues in soft computing: theory and applications, 2005:71–84
Wang H, Chen Z, Feng X et al (2018) Research on network security situation assessment and quantification method based on analytic hierarchy process. Wireless Pers Commun 102:1401–1420
Fan Z, Tan C, Li X (2021) A hierarchical method for assessing cyber security situation based on ontology and fuzzy cognitive maps. Int J Inf Comput Secur 14(3–4):242–262
Zhao X, Zhang Y, Xue J et al (2020) Research on network risk evaluation method based on a differential manifold. IEEE Access 8:66315–66326
Lin ZG, Xu LZ, Yan XJ et al (2006) A decision-making method on DS evidence fusion information based on distance measure. J Comput Res Dev 43(1):169–175
Xu G, Cao Y, Ren Y et al (2017) Network security situation awareness based on semantic ontology and user-defined rules for Internet of Things. IEEE Access 5:21046–21056
Liao Y, Zhao G, Wang J et al (2020) Network security situation assessment model based on extended hidden Markov. Math Probl Eng 2020:1–13
Fava DS, Byers SR, Yang SJ (2008) Projecting cyberattacks through variable-length markov models. IEEE Trans Inf Forensics Secur 3(3):359–369
De Vel O, Liu N, Caelli T, et al. (2006) An embedded Bayesian network hidden Markov model for digital forensics. In: Intelligence and security informatics: IEEE International Conference on Intelligence and Security Informatics, ISI 2006, San Diego, CA, USA, May 23–24, 2006. Proceedings 4. Springer Berlin Heidelberg, pp 459–465
Lee D, Kim D, Jung J (2008) Multi-stage intrusion detection system using hidden Markov model algorithm. In: 2008 International Conference on Information Science and Security (ICISS 2008). IEEE, pp 72–77
Farhadi H, AmirHaeri M, Khansari M (2011) Alert correlation and prediction using data mining and HMM. ISeCure 3(2)
Lin P, Chen Y (2018) Dynamic network security situation prediction based on bayesian attack graph and big data. In: 2018 IEEE 4th Information Technology and Mechatronics Engineering Conference (ITOEC). IEEE, pp 992–998
Qu ZY, Li YY (2010) A network security situation evaluation method based on DS evidence theory. In: 2010 the 2nd Conference on Environmental Science and Information Application Technology. vol 2. IEEE, pp 496–499
Boyer S, Dain O, Cunningham R. Stellar (2005) A fusion system for scenario construction and security risk assessment. In: 3rd IEEE international workshop on information assurance (IWIA’05). IEEE, pp 105–116
Li Y, Yao S, Zhang R et al (2021) Analyzing host security using D-S evidence theory and multisource information fusion. Int J Intell Syst 36(2):1053–1068
Ren H, Stakhanova N, Ghorbani AA (2010) An online adaptive approach to alert correlation. In: Detection of intrusions and malware, and vulnerability assessment: 7th International Conference, DIMVA 2010, Bonn, Germany, Proceedings 7. Springer Berlin Heidelberg, pp 153–172
Marchetti M, Colajanni M, Manganiello F (2011) Identification of correlated network intrusion alerts. In: 2011 3rd International Workshop on Cyberspace Safety and Security (CSS). IEEE, pp 15–20
Ramaki AA, Khosravi-Farmad M, Bafghi AG (2015) Real time alert correlation and prediction using Bayesian networks. In: 2015 12th International Iranian Society of Cryptology Conference on Information Security and Cryptology (ISCISC). IEEE, pp 98–103
Ramaki AA, Amini M, Atani RE (2015) RTECA: real time episode correlation algorithm for multi-step attack scenarios detection. Comput Secur 49:206–219
Soleimani M, Ghorbani AA (2012) Multi-layer episode filtering for the multi-step attack detection. Comput Commun 35(11):1368–1379
Dong G, Li W, Wang S, et al (2020) The assessment method of network security situation based on improved BP neural network. In: The 8th International Conference on Computer Engineering and Networks (CENet2018). Springer International Publishing, pp 67–76
Kalyani S, Swarup KS (2010) Classification and assessment of power system security using multiclass SVM. IEEE Trans Syst Man Cybern Part C (Appl Rev) 41(5):753–758
Li S, Bi F, Chen W et al (2018) An improved information security risk assessments method for cyber-physical-social computing and networking. IEEE Access 6:10311–10319
Zhang H, Kang C, Xiao Y (2021) Research on network security situation awareness based on the LSTM-DT model. Sensors 21(14):4788
Zhao D, Ji G, Zeng S (2022) A network security situation assessment method based on multi-attention mechanism and HHO-ResNeXt. In: International symposium on security and privacy in social networks and big data. Springer Nature Singapore, Singapore, pp 199–211
Yang H, Zeng R, Xu G et al (2021) A network security situation assessment method based on adversarial deep learning. Appl Soft Comput 102:107096
Zhang H, Huang Q, Li F et al (2016) A network security situation prediction model based on wavelet neural network with optimized parameters. Digit Commun Netw 2(3):139–144
Dong Z, Su X, Sun L et al (2021) Network security situation prediction method based on strengthened LSTM neural network. J Phys Conf Ser IOP Publ 1856(1):012056
Li Z, Zhao D, Li X et al (2021) Network security situation prediction based on feature separation and dual attention mechanism. EURASIP J Wirel Commun Netw 2021:1–19
Yao C, Yang Y, Yang J et al (2022) A network security situation prediction method through the use of improved TCN and BiDLSTM. Math Probl Eng 2022:1–15
Cao B, Li C, Song Y et al (2022) Network intrusion detection model based on CNN and GRU. Appl Sci 12(9):4184
Zhang R, Liu M, Pan Z et al (2022) Network security situation assessment based on improved WOA-SVM. IEEE Access 10:96273–96283
Wang J, Wang WC, Hu XX, Qiu L, Zang HF (2024) Black-winged kite algorithm: a nature-inspired meta-heuristic for solving benchmark functions and engineering problems. Artif Intell Rev 57(4):1–53
Krizhevsky A, Sutskever I, Hinton GE (2012) Imagenet classification with deep convolutional neural networks. Adv Neural Inform Process Syst. https://doi.org/10.1145/3065386
Min L, Qiang C, Shuicheng Y (2014) Network in network. In Proceedings of the IEEE International Conference on Learning Representations
Zheng S, Ristovski K, Farahat A, et al (2017) Long short-term memory network for remaining useful life estimation. In: 2017 IEEE International Conference on Prognostics and Health Management (ICPHM). IEEE, pp 88–95
Mell P, Scarfone K, Romanosky S (2007) A complete guide to the common vulnerability scoring system version 2.0. In: Published by FIRST-forum of incident response and security teams. vol 1. p 23
C. Team, Common vulnerability scoring system v3. 0: Specification document, [EB/OL], 2015, https://www.first.org/cvss/v3.0/specification-document/ Accessed 9 Sept 2023
Zhang S, Fu Q, An D, He Z, Liu Z (2023) A novel network security situation assessment model based on multiple strategies whale optimization algorithm and bidirectional GRU. Peer J Comput Sci 9:e1729
Doynikova E, Chechulin A, Kotenko I (2017) Analytical attack modeling and security assessment based on the common vulnerability scoring system. In: 2017 20th Conference of Open Innovations Association (FRUCT). IEEE, pp 53–61
Tang TA, Mhamdi L, McLernon D et al (2016) Deep learning approach for network intrusion detection in software defined networking. In: 2016 International Conference on Wireless Networks and Mobile Communications (WINCOM). IEEE, pp 258–263
Funding
This work was supported by Innovation Foundation Project of Gansu Provincial Department of Education (Grant Nos. 2022CYZC-57, 2025B-134), and funded by University-level Innovative Research Team of Gansu University of Political Science and Law.
Author information
Authors and Affiliations
Contributions
Shengcai Zhang: Funding acquisition, methodology, software, resources, data curation, writing—original draft, writing—review & editing. Zhiying Fu: Conceptualization, software, validation, investigation, data curation, writing—original draft, writing—review & editing, visualization. Dezhi An: Methodology, validation, resources, writing—review &editing, project administration. Huiju Yi: Validation, writing—review & editing.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no competing interests.
Ethical approval
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhang, S., Fu, Z., An, D. et al. Network security situation assessment based on BKA and cross dual-channel. J Supercomput 81, 461 (2025). https://doi.org/10.1007/s11227-025-06932-5
Accepted:
Published:
DOI: https://doi.org/10.1007/s11227-025-06932-5