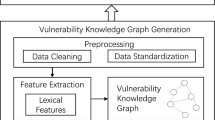
Abstract
Advanced persistent threat (APT) attacks cause significant damage to both enterprises and individuals, and timely and accurate identification of APT groups is of critical importance. However, APT groups are highly covert, making it difficult to obtain accurate data samples for classification. To improve the classification of APT groups, this paper proposes an organization classification model based on Graph Attention Networks. By enriching the dataset with additional samples of APT groups, this study extracts various types of knowledge related to APT groups and explores the relationships among these knowledge pieces to construct a security entity model. Furthermore, a network security knowledge graph is built to store these security entity models. To enhance the stability of the graph attention network, multi-head attention is introduced. The improved graph attention network is then used to group similar security entity models into one category, completing the classification of APT groups.














Similar content being viewed by others
Data availability
References
Lee S, Kim C, Park H (2024) Practical apt group hash unit profiling framework using ttps. IEICE Trans Inform Syst E107(12):1533–1537. https://doi.org/10.1587/transinf.2024EDL8046
Li T, Jiang Y, Lin C, Obaidat MSS, Shen Y, Ma J (2023) Deepag: attack graph construction and threats prediction with bi-directional deep learning. IEEE Trans Depend Secure Comput 20(1):740–757. https://doi.org/10.1109/TDSC.2022.3143551
Sharma A, Gupta BB, Singh AK, Saraswat V (2023) Advanced persistent threats (apt): evolution, anatomy, attribution and countermeasures. J Ambient Intell Humaniz Comput 14(7):9355–9381
Li T, Liu X, Qiao W, Zhu X, Shen Y, Ma J (2023) T-trace: constructing the apts provenance graphs through multiple syslogs correlation. IEEE Trans Depend Secure Comput 21:1179–1195
Yadav S (2024) Social automation and apt attributions in national cybersecurity. J Cyber Secur Technol 8:1–26
Yuan Y, Adhatarao SS, Lin M, Yuan Y, Liu Z, Fu X (2020) Ada: adaptive deep log anomaly detector. In IEEE INFOCOM 2020-IEEE Conference on Computer Communications, pp 2449–2458. IEEE
Muhammad Z, Anwar Z, Javed AR, Saleem B, Abbas S, Gadekallu TR (2023) Smartphone security and privacy: a survey on apts, sensor-based attacks, side-channel attacks, google play attacks, and defenses. Technologies 11(3):76
Chen Z-S, Vaitheeshwari R, Wu EH-K, Lin Y-D, Hwang R-H, Lin P-C, Lai Y-C, Ali A (2024) Clustering apt groups through cyber threat intelligence by weighted similarity measurement. IEEE Access 12:141851–141865
Lee K, Lee J, Yim K (2023) Classification and analysis of malicious code detection techniques based on the apt attack. Appl Sci 13(5):2894
Bahrami PN, Dehghantanha A, Dargahi T, Parizi RM, Choo K-KR, Javadi HH (2019) Cyber kill chain-based taxonomy of advanced persistent threat actors: Analogy of tactics, techniques, and procedures. J Inform Process Syst 15(4):865–889
Li J, Liu J, Zhang R (2024) Advanced persistent threat group correlation analysis via attack behavior patterns and rough sets. Electronics 13(6):1106
Moran N, Bennett JT (2013) Supply chain analysis: from quartermaster to Sunshop, vol 11. FireEye, Milpitas, CA
Pandazhengzheng (2024) Analysis and defense strategies of APT attacks. Accessed: Dec 21, 2024. https://blog.csdn.net/pandazhengzheng/article/details/136267327
Burita L, Le DT (2021) Cyber security and apt groups. In 2021 Communication and Information Technologies (KIT), pp 1–7. IEEE
Lee J-S, Fan Y-Y, Cheng C-H, Chew C-J, Kuo C-W (2025) Ml-based intrusion detection system for precise apt cyber-clustering. Comput Secur 149:104209
Ren W, Song X, Hong Y, Lei Y, Yao J, Du Y, Li W (2023) Apt attack detection based on graph convolutional neural networks. Int J Comput Intell Syst. https://doi.org/10.1007/s44196-023-00369-5
Xu L, Zhao Z, Zhao D, Li X, Lu X, Yan D (2024) Ajsage: a intrusion detection scheme based on jump-knowledge connection to graphsage. Comput Secur 150:104263
Duan G, Lv H, Wang H, Feng G (2023) Application of a dynamic line graph neural network for intrusion detection with semisupervised learning. IEEE Trans Inform For Secur 18:699–714. https://doi.org/10.1109/TIFS.2022.3228493
Tang G, Yang L, Zhang L, Cao W, Meng L, He H, Kuang H, Yang F, Wang H (2023) An attention-based automatic vulnerability detection approach with ggnn. Int J Mach Learn Cyber 14(9):3113–3127. https://doi.org/10.1007/s13042-023-01824-7
Cai Y, Gu Z, Wang L, Li S, Han W (2020) An apt group knowledge model based on mdata. In Proceedings of the 2020 International Conference on Cyberspace Innovation of Advanced Technologies, pp 374–378
Lyu Y, Wang Z, Yang X, Song W, Peng G (2023) A novel apt malware classification method based on feature function code. J Zhengzhou Univ (Natur Sci Ed) 55(2):10–18. https://doi.org/10.13705/j.issn.1671-6841.20221417
Liu J, Liu Y, Li J, Sun W, Cheng J, Zhang R, Huang X, Pang J (2022) Two statistical traffic features for certain apt group identification. J Inform Secur Appl. https://doi.org/10.1016/j.jisa.2022.103207
Saha A, Blasco J, Cavallaro L, Lindorfer M (2024) Adapt it! automating apt campaign and group attribution by leveraging and linking heterogeneous files. In Proceedings of the 27th International Symposium on Research in Attacks, Intrusions and Defenses, pp 114–129
Krishnapriya S, Singh S (2024) A comprehensive survey on advanced persistent threat (apt) detection techniques. CMC-Comput Mater Contin 80(2):2675–2719. https://doi.org/10.32604/cmc.2024.052447
Fahad M, Kumar A, Arif H, Hussain HK (2023) Mastering apt defense: strategies, technologies, and collaboration. BIN: Bull Inform 1(2):84–94
Cybersecurity and Infrastructure Security Agency (CISA) (2023) CISA cybersecurity advisory: AA23-108A - APT actors exploiting CVE-2023-23397 and other vulnerabilities. Accessed: 2025-02-01. https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-108
Kaspersky (2023) Lazarus Group’s new malware: a detailed analysis. Accessed: 2025-02-01. https://securelist.com/lazarus-new-malware/115059/
Mancuso J (2023) Motives and tactics, techniques, and procedures: making sense of the activities of Russian advanced persistent threat groups. Utica University, Utica, NY
Abbas-Escribano M, Debar H (2023) An improved honeypot model for attack detection and analysis. In Proceedings of the 18th International Conference on Availability, Reliability and Security, pp 1–10
La Z, Qian Y, Leng H, Gu T, Gong W, Chen J (2024) Mc-gat: multi-channel graph attention networks for capturing diverse information in complex graphs. Cogn Comput 16(2):595–607
Ling Y, Li X, Bin D, Yang C, Han S, Lu J, Ming S, Li J (2024) Graph attention mechanism-based method for tracing apt attacks in power systems. In 2024 IEEE 4th International Conference on Power, Electronics and Computer Applications (ICPECA), pp 23–27. IEEE
Zhao X, Jiang R, Han Y, Li A, Peng Z (2024) A survey on cybersecurity knowledge graph construction. Comput Secur 136:103524
Sikos LF (2023) Cybersecurity knowledge graphs. Knowl Inf Syst 65(9):3511–3531
Mandiant (2021) APT28: A window into Russia’s cyber espionage group. Accessed: 2024-12-27. https://www.mandiant.com/sites/default/files/2021-09/APT28-Center-of-Storm-2017.pdf
FreeBuf (2019) Analysis and attribution of the first APT attack using the "Double Kill" 0day vulnerability (CVE-2018-8174) by APT-C-06. Accessed: 2024-12-27. https://www.freebuf.com/articles/paper/171254.html
Microsoft (2024) Analyzing forest Blizzard’s custom post-compromise tool for exploiting CVE-2022-38028 to obtain credentials. Accessed: 2024-12-27. https://www.microsoft.com/en-us/security/blog/2024/04/22/analyzing-forest-blizzards-custom-post-compromise-tool-for-exploiting-cve-2022-38028-to-obtain-credentials
Acknowledgements
This research is funded by Jilin Science and Technology Development Plan Project of China(20230201074GX).
Author information
Authors and Affiliations
Contributions
Yazhou Du was involved in validation, methodology, formal analysis, writing-original draft, and writing-review & editing. Weiwu Ren was involved in project administration, funding acquisition, validation, writing-review & editing. Xintong Song was involved in Data curation, Writing - review & editing. Wenjuan Li was involved in data curation, writing-review & and editing.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no Conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Du, Y., Ren, W., Song, X. et al. Research on APT group classification method based on graph attention networks. J Supercomput 81, 563 (2025). https://doi.org/10.1007/s11227-025-07051-x
Accepted:
Published:
DOI: https://doi.org/10.1007/s11227-025-07051-x