Abstract
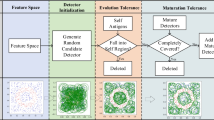
The negative selection algorithm (NSA), inspired by human immunity, has the advantages of being adaptable and not requiring prior knowledge, so it is increasingly used across various industries. To address issues related to security detection, intrusion detection, anomaly detection, fault detection, and other industry-related problems, various improvements have been made; however, the false positive (FP) problem remains unresolved. The NSA comprises the detector generation stage and the detection stage. Thus far, improvements have concentrated on the first stage to create a flawless detector set, yet no researcher has considered enhancing the second linear detection stage, which leads to the FP. This paper re-examines the current advancements in biological immunology, utilizes the multilayer immune tolerance mechanism to improve the NSA, and proposes the multilayer immune tolerance (MIT) method based on the NSA to decrease FP. This method is divided into three layers. The first layer generates the detector set through the NSA. The second layer tolerates or filters out escaped and unfunctional detectors by simulating the ignorance mechanism and the co-stimulation mechanism, thereby producing the activated detectors. Specifically, the activating set derived from the testing set is clustered using the k-means method, and the generated detectors and the clusters are utilized to obtain pre-activated detectors through the concentration-checking based on MIT (CC-MIT) algorithm, with activated detectors being determined by the co-stimulation based on MIT (CS-MIT) algorithm. In the third layer, these activated detectors are evaluated using the positive selection algorithm. Those within the activated range of detectors are classified as abnormal, while others are considered normal. This method significantly reduces the occurrence of unfunctional or escaped detectors, thereby greatly decreasing FP and enhancing detection precision. The effectiveness of the proposed MIT method and the selection of the related parameters is validated through experiments comparing it with the NSA algorithm. Furthermore, the progress of this method is illustrated through comparisons with well-regarded algorithms known for their efficacy in anomaly detection, especially in apparently improving precision.















Similar content being viewed by others
Data availability
No datasets were generated or analysed during the current study.
References
Zhou W, Liang Y, Dong H, Tan C, Xiao Z, Liu W (2017) A numerical differentiation based dendritic cell model. In: 2017 IEEE 29th International Conference on Tools with Artificial Intelligence (ICTAI), pp. 1092–1098. IEEE
Saurabh P, Verma B (2023) Negative selection in anomaly detection-a survey. Comput Sci Rev 48:100557
Althalji A, Khawatmi S, Khatib M (2023) Improving the security of aodv protocol using v-detector algorithm. Int J Comput Appl 975:8887
Ren Y, Wang X, Zhang C (2020) A novel fault diagnosis method based on improved negative selection algorithm. IEEE Trans Instrum Meas 70:1–8
Wen C, Changzhi W (2022) Combine labeled and unlabeled data for immune detector training with label propagation. Knowl-Based Syst 236:107661
Gu M, Li D, Liu J, Shan W, Liu S (2024) A negative selection algorithm with hypercube interface detectors for anomaly detection. Appl Soft Comput 154:111339
Singh K, Kaur L, Maini R (2022) A survey of intrusion detection techniques based on negative selection algorithm. Int J Syst Assur Eng Manag 1–11
Duru C, Ladeji–Osias J, Wandji K, Otily T, Kone R (2022) A review of human immune inspired algorithms for intrusion detection systems. In: 2022 IEEE World AI IoT Congress (AIIoT). IEEE, pp 364–371
Peng L, Liang Y, Yang H (2024) Improved v-detector algorithm based on bagging for earthquake prediction with faults. J Supercomput 80(16):24605–24637
Forrest S, Perelson AS, Allen L, Cherukuri R (1994) Self-nonself discrimination in a computer. In: Proceedings of 1994 IEEE Computer Society Symposium on Research in Security and Privacy. IEEE, pp 202–212
Kodati S, Sreekanth N, Sarma K, Reddy PCS, Saxena A, Narasaiah BP (2023) Ensemble framework of artificial immune system based on network intrusion detection system for network security sustainability. In: E3S Web of Conferences, vol 430. EDP Sciences, p 01070
Ma M, Yang G, He J, Fang W (2024) An adaptive detection framework based on artificial immune for iot intrusion detection system. Appl Soft Comput 166:112152
Chen J, He J, Li W, Fang W, Lan X, Ma W, Li T (2024) A hierarchical unmanned aerial vehicle network intrusion detection and response approach based on immune vaccine distribution. IEEE Internet Things J
Yang G, Wang L, Yu R, He J, Zeng B, Wu T (2023) A modified gray wolf optimizer-based negative selection algorithm for network anomaly detection. Int J Intell Syst 2023(1):8980876
Huang H, Liu N, Chen D, Yang Q, Huang X (2022) Research on the intrusion detection model of underwater sensor networks. J Sensors 2022(1):2323747
Li B, Chang Y, Huang H, Li W, Li T, Chen W (2023) Artificial immunity based distributed and fast anomaly detection for industrial internet of things. Futur Gener Comput Syst 148:367–379
Gupta KD, Dasgupta D (2021) Using negative detectors for identifying adversarial data manipulation in machine learning. In: 2021 International Joint Conference on Neural Networks (IJCNN). IEEE, pp 1–8
Sompayrac LM (2022) How the immune system works. Wiley, Hoboken
Yatim KM, Lakkis FG (2015) A brief journey through the immune system. Clin J Am Soc Nephrol 10(7):1274–1281
Waldmann H (2016) Mechanisms of immunological tolerance. Clin Biochem 49(4–5):324–328
Mills CD, Ley K, Buchmann K, Canton J (2015) Sequential immune responses: the weapons of immunity. J Innate Immun 7(5):443–449
Aarthy R, Muthupriya V, Balaji G (2024) Detection of bone cancer based on a four-phase framework generative deep belief neural network in deep learning. Alex Eng J 109:394–407
Owen RD (1945) Immunogenetic consequences of vascular anastomoses between bovine twins. Science 102(2651):400–401
Schwartz RH (2012) Historical overview of immunological tolerance. Cold Spring Harb Perspect Biol 4(4):006908
Gammon JM, Jewell CM (2019) Engineering immune tolerance with biomaterials. Adv Healthc Mater 8(4):1801419
Yang L, Jin R, Lu D, Ge Q (2020) T cell tolerance in early life. Front Immunol 11:576261
Suhrkamp I, Scheffold A, Heine G (2023) T-cell subsets in allergy and tolerance induction. Eur J Immunol 53(10):2249983
Bluestone JA, McKenzie BS, Beilke J, Ramsdell F (2023) Opportunities for treg cell therapy for the treatment of human disease. Front Immunol 14:1166135
Cho E, Han S, Eom HS, Lee S-J, Han C, Singh R, Kim S-H, Park B-M, Kim B-G, Kim YH (2023) Cross-activation of regulatory t cells by self antigens limits self-reactive and activated cd8+ t cell responses. Int J Mol Sci 24(18):13672
Brown CC, Rudensky AY (2023) Spatiotemporal regulation of peripheral t cell tolerance. Science 380(6644):472–478
Wortel IM, Keşmir C, Boer RJ, Mandl JN, Textor J (2020) Is t cell negative selection a learning algorithm? Cells 9(3):690
Saxena V, Li L, Paluskievicz C, Kasinath V, Bean A, Abdi R, Jewell CM, Bromberg JS (2019) Role of lymph node stroma and microenvironment in t cell tolerance. Immunol Rev 292(1):9–23
Hofmeyr S (2004) The implications of immunology for secure systems design. Comput Secur 23(6):453–455
Li Z, Li T (2022) Using known nonself samples to improve negative selection algorithm. Appl Intell 52(1):482–500
Zhou C, Paffenroth RC (2017) Anomaly detection with robust deep autoencoders. In: Proceedings of the 23rd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp 665–674
Chen Z, Yeo CK, Lee BS, Lau CT (2018) Autoencoder-based network anomaly detection. In: 2018 Wireless Telecommunications Symposium (WTS). IEEE, pp 1–5
Acknowledgements
The authors want to thank the National Natural Science Foundation of China-http://www.nsfc.gov.cn for the support through Grants Number 62202147.
Author information
Authors and Affiliations
Contributions
Lu Peng and Wen Zhou wrote the main manuscript, while Yiwen Liang and He Yang supervised the project, edited the review, and acquired funding. Fan Yang prepared Figures 6-12. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Peng, L., Liang, Y., Zhou, W. et al. A preliminary exploration of the T cells multilayer immune tolerance model. J Supercomput 81, 565 (2025). https://doi.org/10.1007/s11227-025-07059-3
Accepted:
Published:
DOI: https://doi.org/10.1007/s11227-025-07059-3