Abstract
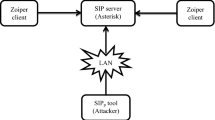
As Voice over IP (VoIP) applications become increasingly popular, they are more and more facing security challenges that have not been present in the traditional Public Switched Telephone Network (PSTN). One of the reasons is that VoIP applications rely heavily on external Internet-based infrastructures (e.g., DNS server, web server), so that vulnerabilities of these external infrastructures have an impact on the security of VoIP systems as well. This article presents a Denial of Service (DoS) attack on VoIP systems by exploiting long response times of external infrastructures. This attack can lead the whole VoIP system in a blocked state thus reducing the availability of its provided signalling services. The results of our experiments prove the feasibility of blocking attacks. Finally, we also discuss several defending methods and present an improved protection mechanism against blocking attacks.
Similar content being viewed by others
References
Voice over IP Security Alliance (VOIPSA). http://www.voipsa.org/. Accessed at 16 September 2008.
Geneiatakis, D., Dagiuklas, T., Kambourakis, G., Lambrinoudakis, C., Gritzalis, S., Ehlert, S., & Sisalem, D. (2006). Survey of security vulnerabilities in session initiation protocol. IEEE Communications Surveys & Tutorials, 8(3), 68–81.
Rosenberg, J., Schulzrinne, H., Camarillo, G., Johnston, A., Peterson, J., Sparks, R., Handley, M., & Schooler, E. (2002). SIP: Session initiation protocol. RFC 3261.
Zhang, G., Ehlert, S., Magedanz, T., & Sisalem, D. (2007). Denial of service attack and prevention on SIP VoIP infrastructures using DNS flooding. In IPTComm ’07: Proceedings of the 1st international conference on principles, systems and applications of IP telecommunications (pp. 57–66). New York, NY, USA, July 2007. ACM.
Fielding, R., Gettys, J., Mogul, J., Frystyk, H., Masinter, L., Leach, P., & Berners-Lee, T. (1999). Hypertext transfer protocol—HTTP/1.1. RFC 2616.
Handley, M., & Jacobson, V. (1998). SDP: Session description protocol. RFC 2327.
Sisalem, D., Kuthan, J., & Ehlert, S. (2006). Denial of service attacks targeting a SIP VoIP infrastructure: attack scenarios and prevention mechanisms. IEEE Network, 20(5), 26–31.
Sengar, H., Wijesekera, D., Wang, H., & Jajodia, S. (2006). Fast detection of denial of service attacks on IP telephone. In 14th IEEE international workshop on quality of service, New Haven, USA, June 2006. IEEE.
Chen, E. Y. (2006). Detecting DoS attacks on SIP system. In 1st IEEE workshop on VoIP management and security, Vancouver, Canada, April 2006. IEEE.
Sengar, H., Wijesekera, D., Wang, H., & Jajodia, S. (2006). VoIP intrusion detection through interacting protocol state machines. In DSN ’06: the international conference on dependable systems and networks, June.
Ehlert, S., Wang, C., Magedanz, T., & Sisalem, D. (2008). Specification-based denial-of-service detection for SIP voice-over-IP networks. In 3rd international conference on Internet monitoring and protection, Bucharest, Hungary, July 2008. IEEE.
Conner, W., & Nahrstedt, K. (2008). Protecting SIP proxy servers from ringing-based denial-of-service attacks. In The tenth IEEE international symposium on multimedia (ISM), Berkeley, USA, December 2008. IEEE.
Geneiatakis, D., Kambourakis, G., Lambrinoudakis, C., Dagiuklas, T., & Gritzalis, S. (2007). A framework for protecting a SIP-based infrastructure against malformed message attacks. Computer Networks, 51(10), 2580–2593.
Fei, A., Pei, G., Liu, R., & Zhang, L. (1998). Measurements on delay and hop-count of the Internet. In IEEE GLOBECOM’98—Internet mini-conference, Sydney, Australia, November 1998. IEEE.
Mockapetris, P. V. (1987). Domain names—implementation and specification. RFC 1035.
Berners-Lee, T., Fielding, R., & Masinter, L. (2005). Uniform resource identifier (URI): Generic syntax. RFC 3986.
Faltstrom, P., & Mealling, M. (2004). The e.164 to uniform resource identifiers (URI) dynamic delegation discovery system (DDDS) application (ENUM). RFC 3761.
Rosenberg, J., & Schulzrinne, H. (2002). Session initiation protocol (SIP): locating SIP servers. RFC 3263.
Nassar, M., State, R., & Festor, O. (2007). VoIP honeypot architecture. In IEEE international symposium on integrated network management, Munich, Germany, May 2007. IEEE.
Peterson, J., & Jennings, C. (2006). Enhancements for authenticated identity management in the session initiation protocol (SIP). RFC 4474.
Berners-Lee, T., Masinter, L., & McCahill, M. (1994). Uniform resource locators (URL). RFC 1738.
Rosenberg, J., & Jennings, C. (2008). The session initiation protocol (SIP) and spam. RFC 5039.
The MIT “king” dataset: http://pdos.csail.mit.edu/p2psim/kingdata/. Accessed 16 January 2009.
Gummadi, K. P., Saroiu, S., & Gribble, S. D. (2002). King: estimating latency between arbitrary Internet end hosts. In IMW’02: proceedings of the 2nd ACM SIGCOMM workshop on Internet measurement (pp. 5–18). New York, NY, USA. ACM.
SIPp: http://sipp.sourceforge.net/. Accessed 16 September 2008.
Express Router, S. I. P. (SER): http://www.iptel.org. Accessed 16 September 2008.
Minihttpd: http://www.acme.com/software/mini_httpd/. Accessed 16 September 2008.
Dnsmasq: http://www.thekelleys.org.uk/dnsmasq/doc.html. Accessed 16 September 2008.
Stewart, J. (2003). DNS cache poisoning—the next generation (Technical report). http://www.lurhq.com/dnscache.pdf. Accessed 4 November 2008.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhang, G., Fischer-Hübner, S. & Ehlert, S. Blocking attacks on SIP VoIP proxies caused by external processing. Telecommun Syst 45, 61–76 (2010). https://doi.org/10.1007/s11235-009-9234-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-009-9234-1