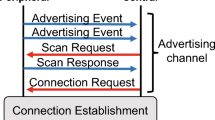
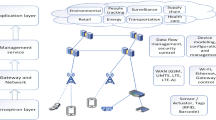
Abstract
Several dynamic frame-slotted ALOHA (DFSA) methods are suggested to resolve the collision problem in radio frequency identification systems. This paper proposes a rapid DFSA-based algorithm for tags identification. The above-stated algorithm is based on adaptive class parting technique to select the optimal frames length. The selection of the best frame length is a major research factor to be used for dynamic frame slotted ALOHA algorithm. To get the best frame length in DFSA protocol, we classified the tags into the some groups. Each group of tags is determined by same prefixes. The main objectives of the new algorithm are to improve the tags identification time and to increase the reader energy efficiency. The ideal frame size has to be fixed to 2 times of the total of tags bit length if the ratio among collision-slot and empty-slot is 5. Observing the results clarifies that the algorithm in this paper offers a reading rapidity of up to 400 tags/s and can achieve time-saving identification up to 15–20% in comparison to the traditional DFSA. The rapid DFSA anti-collision algorithm has a number of merits such as compatibility with ISO 18000-6, better system performance and ease of implementation.










Similar content being viewed by others
References
Khadka, G., & Hwang, S.-S. (2017). Tag-to-tag interference suppression technique based on time division for RFID. Sensors, 17(1), 78. https://doi.org/10.3390/s17010078.
Chen, C.-L., Huang, Y.-C., & Jiang, J.-R. (2013). A secure ownership transfer protocol using EPCglobal Gen-2 RFID. Telecommunication Systems, 53(4), 387–399. https://doi.org/10.1007/s11235-013-9711-4.
Zhang, H. P., Li, J. J., Chen, Z. L., & Wang, B. (2015). A rapid anti-collision method for RFID tag identification. Applied Mechanics and Materials, 738–739, 1123–1128. https://doi.org/10.4028/www.scientific.net/AMM.738-739.1123.
Kim, C. S., Jang, B. I., & Jung, H. K. (2014). Performance analysis of anti-collision algorithm for tag identification time improvement. International Journal of Software Engineering and Its Applications, 8(3), 1–10. https://doi.org/10.14257/ijseia.2014.8.3.01.
Chen, Y. C., Lo, N. W., Kuo, R. Z., Winata, E., & Yeh, K. H. (2017). A fast collision arbitration algorithm for RFID tag identifcation in supply chain environment. Journal of Internet Technology, 18(1), 125–134. https://doi.org/10.6138/JIT.2017.18.1.20120311.
Zhang, D., Huang, H., & Jo, M. (2015). Future RFID technology and applications: Visions and challenges. Telecommunication Systems, 58(3), 193–194. https://doi.org/10.1007/s11235-014-9865-8.
Bang, O. B. O., Kim, S. K. S., & Lee, H. L. H. (2009). Identification of RFID tags in dynamic framed slotted Aloha. In 2009 11th international conference on advanced communication technology (Vol. 1, pp. 354–357). Phoenix Park, South Korea: IEEE. Retrieved from http://ieeexplore.ieee.org/document/4809969/.
Vogt, H. (2002). Efficient object identification with passive RFID tags (pp. 98–113). https://doi.org/10.1007/3-540-45866-2_9.
Schoute, F. (1983). Dynamic frame length ALOHA. IEEE Transactions on Communications, 31(4), 565–568. https://doi.org/10.1109/TCOM.1983.1095854.
Wang, Z., Wen, G., & Yang, Y. (2013). A novel tag number estimation method for RFID systems. In 2013 IEEE 4th international conference on software engineering and service science (pp. 442–446). IEEE. https://doi.org/10.1109/icsess.2013.6615344.
Chen, W.-T. (2014). A feasible and easy-to-implement anticollision algorithm for the EPCglobal UHF Class-1 generation-2 RFID protocol. IEEE Transactions on Automation Science and Engineering, 11(2), 485–491. https://doi.org/10.1109/TASE.2013.2257756.
Klair, D. K., Chin, K.-W., & Raad, R. (2007). On the accuracy of RFID tag estimation functions. In 2007 international symposium on communications and information technologies (pp. 1401–1406). IEEE. https://doi.org/10.1109/iscit.2007.4392235.
Knerr, B., Holzer, M., Angerer, C., & Rupp, M. (2010). Slot-wise maximum likelihood estimation of the tag population size in FSA protocols. IEEE Transactions on Communications, 58(2), 578–585. https://doi.org/10.1109/TCOMM.2010.02.080571.
Klair, D. K., Chin, K.-W., & Raad, R. (2010). A survey and tutorial of RFID anti-collision protocols. IEEE Communications Surveys & Tutorials, 12(3), 400–421. https://doi.org/10.1109/SURV.2010.031810.00037.
Jakkhupan, W., Arch-int, S., & Li, Y. (2015). An RFID-based traceability system. Telecommunication Systems, 58(3), 243–258. https://doi.org/10.1007/s11235-014-9866-7.
Chen, W.-T. (2016). Optimal frame length analysis and an efficient anti-collision algorithm with early adjustment of frame length for RFID systems. IEEE Transactions on Vehicular Technology, 65(5), 3342–3348. https://doi.org/10.1109/TVT.2015.2441052.
La Porta, T. F., Maselli, G., & Petrioli, C. (2011). Anticollision protocols for single-reader RFID systems: Temporal analysis and optimization. IEEE Transactions on Mobile Computing, 10(2), 267–279. https://doi.org/10.1109/TMC.2010.58.
Chen, W.-T. (2014). A fast anticollision algorithm for the EPCglobal UHF Class-1 generation-2 RFID standard. IEEE Communications Letters, 18(9), 1519–1522. https://doi.org/10.1109/LCOMM.2014.2334317.
Zhang, D., Li, G., Pan, Z., & Liang, Y. (2013). A new anti-collision algorithm for RFID tag. International Journal of Communication Systems. https://doi.org/10.1002/dac.2543.
Wu, H., Zeng, Y., Feng, J., & Gu, Y. (2013). Binary tree slotted ALOHA for passive RFID tag anticollision. IEEE Transactions on Parallel and Distributed Systems, 24(1), 19–31. https://doi.org/10.1109/TPDS.2012.120.
Gandino, F., Montrucchio, B., & Rebaudengo, M. (2017). A security protocol for RFID traceability. International Journal of Communication Systems, 30(6), e3109. https://doi.org/10.1002/dac.3109.
Jia, X., Feng, Q., & Ma, C. (2010). An efficient anti-collision protocol for RFID tag identification. IEEE Communications Letters, 14(11), 1014–1016. https://doi.org/10.1109/LCOMM.2010.091710.100793.
Bagheri, N., Alenaby, P., & Safkhani, M. (2017). A new anti-collision protocol based on information of collided tags in RFID systems. International Journal of Communication Systems, 30(3), e2975. https://doi.org/10.1002/dac.2975.
Oner, M., Ustundag, A., & Budak, A. (2017). An RFID-based tracking system for denim production processes. The International Journal of Advanced Manufacturing Technology, 90(1–4), 591–604. https://doi.org/10.1007/s00170-016-9385-7.
Yan, X.-Q., Liu, Y., Li, B., & Liu, X.-M. (2015). A memoryless binary query tree based successive scheme for passive RFID tag collision resolution. Information Fusion, 22, 26–38. https://doi.org/10.1016/j.inffus.2013.08.006.
Ullah, N., Sanaullah Chowdhury, M., Khan, P., Ullah, S., & Kwak, K. S. (2012). Throughput and delay limits of chirp spread spectrum-based IEEE 802.15.4a. International Journal of Communication Systems, 25(1), 1–15. https://doi.org/10.1002/dac.1283.
Sanchez, L., Ramos, V., & Ledesma, O. (2016). Efficient detection of missing tags for passive RFID systems. International Journal of Communication Systems, 29(9), 1545–1567. https://doi.org/10.1002/dac.3127.
Del-Valle-Soto, C., Mex-Perera, C., Orozco-Lugo, A., Lara, M., Galván-Tejada, G., & Olmedo, O. (2014). On the MAC/network/energy performance evaluation of wireless sensor networks: Contrasting MPH, AODV, DSR and ZTR routing protocols. Sensors, 14(12), 22811–22847. https://doi.org/10.3390/s141222811.
Seol, J.-M., & Kim, S.-W. (2007). Collision-resilient multi-state query tree protocol for fast RFID tag identification (pp. 733–742). https://doi.org/10.1007/978-3-540-74377-4_76.
Junjie, Z., Li, Z. Z., Xiantao, Z., Lei, Z. C., & Mei, Z. X. (2010). Anti-collision algorithm based on the regressive-style RFID of BIBD (4,2,1). In 2010 3rd international conference on advanced computer theory and engineering (ICACTE) (pp. V4-352–V4-355). IEEE. https://doi.org/10.1109/icacte.2010.5579479.
Ullah, S., Alsalih, W., Alsehaim, A., & Alsadhan, N. (2012). A review of tags anti-collision and localization protocols in rfid networks. Journal of Medical Systems, 36(6), 4037–4050. https://doi.org/10.1007/s10916-012-9876-5.
Zhang, D., Qian, Y., Wan, J., & Zhao, S. (2015). An efficient RFID search protocol based on clouds. Mobile Networks and Applications, 20(3), 356–362. https://doi.org/10.1007/s11036-015-0597-0.
Shariat, Z., Movaghar, A., & Hoseinzadeh, M. (2017). A learning automata and clustering-based routing protocol for named data networking. Telecommunication Systems, 65(1), 9–29. https://doi.org/10.1007/s11235-016-0209-8.
Yang, J., Wang, Y., Cai, Q., & Zhan, Y. (2015). A novel hybrid anticollision algorithm for RFID system based on grouped dynamic framed recognition and binary tree recursive process. International Journal of Distributed Sensor Networks, 11(8), 641327. https://doi.org/10.1155/2015/641327.
Hu, L., Ong, D. M., Zhu, X., Liu, Q., & Song, E. (2015). Enabling RFID technology for healthcare: application, architecture, and challenges. Telecommunication Systems, 58(3), 259–271. https://doi.org/10.1007/s11235-014-9871-x.
Chen, Y., Zhou, J., & Guo, M. (2016). A context-aware search system for Internet of Things based on hierarchical context model. Telecommunication Systems, 62(1), 77–91. https://doi.org/10.1007/s11235-015-9984-x.
Park, J., Chung, M., & Lee, T. (2007). Identification of RFID tags in framed-slotted ALOHA with robust estimation and binary selection. IEEE Communications Letters, 11(5), 452–454. https://doi.org/10.1109/LCOMM.2007.061581.
Yin, Y., Xie, L., Lu, S., & Chen, D. (2014). Check out the rules: Towards time-efficient rule checking over RFID tags. Mobile Networks and Applications, 19(4), 524–533. https://doi.org/10.1007/s11036-014-0524-9.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chekin, M., Hossienzadeh, M. & Khademzadeh, A. A rapid anti-collision algorithm with class parting and optimal frames length in RFID systems. Telecommun Syst 71, 141–154 (2019). https://doi.org/10.1007/s11235-018-0492-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-018-0492-7