Abstract
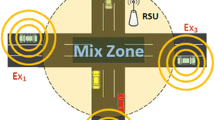
Preserving privacy of vehicle movement is an important challenge in road networks; as trajectory data with spatiotemporal information may reveal much individual information. One of the main threats is revealing history location of vehicle trajectories while it stops and again moves toward the destination. Generally, vehicles stop at mostly two places; the first one is traffic light (signal system)/traffic jam and second is at parking locations such as office, shopping mall, home, hospital etc. While existing works only consider social spots. To cope with this issue, we present a new multiple mix zones de-correlation privacy model in which the degree of de-correlation between parking locations and traffic light/traffic jam places. Further, we consider multiple mix zones method to replace parking locations and traffic light/traffic jam places by de-correlation mix zone region. This paper presents an improved privacy traffic monitoring system for road network applications via a proposed security scheme. Specifically, the proposed model analyzes the monitored scene and deployed mix zones parking location and traffic light/traffic jam places. Our method achieved a high privacy level and anonymity solution for trajectory model; moreover, it also balances the service quality and privacy protection. Finally, we performed experiments on real-world data and showed the effectiveness of our method in comparison to existing methods.





















Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Memon, I., & Arain, Q. A. (2017). Dynamic path privacy protection framework for continuous query service over road networks. World Wide Web, 20(4), 639–672.
Memon, I., Chen, L., Arain, Q. A., Memon, H., & Chen, G. (2017). Pseudonym changing strategy with multiple mix zones for trajectory privacy protection in road networks. International Journal of Communication Systems. https://doi.org/10.1002/dac.3437.
Horng, G. J. (2015). The adaptive recommendation mechanism for distributed parking service in smart city. Wireless Personal Communications, 80(1), 395–413.
Keler, A., Krisp, J. M., & Ding, L. (2017). Visualization of traffic bottlenecks: Combining traffic congestion with complicated crossings. In International cartographic conference (pp. 493–505). Cham: Springer.
Memon, I., Ali, Q., Zubedi, A., & Mangi, F. A. (2017). DPMM: Dynamic pseudonym-based multiple mix-zones generation for mobile traveler. Multimedia Tools and Applications, 76(22), 24359–24388.
Huang, X., Zhao, D., & Peng, H. (2017). Empirical study of DSRC performance based on safety pilot model deployment data. IEEE Transactions on Intelligent Transportation Systems, 18(10), 2619–2628.
Memon, M. H., Li, J.-P., Memon, I., & Arain, Q. A. (2017). GEO matching regions: Multiple regions of interests using content based image retrieval based on relative locations. Multimedia Tools and Applications, 76(14), 15377–15411.
Arain, Q. A., Deng, Z., Memon, I., Zubedi, A., Jiao, J., Ashraf, A., et al. (2017). Privacy protection with dynamic pseudonym-based multiple mix-zones over road networks. China Communications, 14(4), 89–100.
Pan, Y., & Li, J. (2013). Cooperative pseudonym change scheme based on the number of neighbors in VANETs. Journal of Network and Computer Applications, 36, 1599–1609.
Shen, X. S. (2017). Cloud-based privacy-preserving parking navigation through vehicular communications. In Proceedings of the security and privacy in communication networks: 12th international conference, SecureComm 2016, Guangzhou, China, October 10–12, 2016 (Vol. 198, p. 85). Berlin: Springer.
Sun, G., Liao, D., Li, H., Yu, H., Chang, V., Sun, G., et al. (2017). L2P2: A location-label based approach for privacy preserving in LBS. Future Generation Computer Systems, 74, 375–384.
Memon, I., Hussain, I., Akhtar, R., & Chen, G. (2015). Enhanced privacy and authentication: An efficient and secure anonymous communication for location based service using asymmetric cryptography scheme. Wireless Personal Communications, 84(2), 1487–1508.
Lu, R., Lin, X., Luan, T. H., Liang, X., & Shen, X. S. (2012). Pseudonym changing at social spots: an effective strategy for location privacy in vanets. IEEE Transactions on Vehicular Technology, 61(1), 86–96.
Memon, I., & Memon, H. (2017). An effective and secure user authenticated protocol for location based services in road networks. arXiv preprint arXiv:1706.02646.
Arain, Q. A., Memon, H., Memon, I., Memon, M. H., Shaikh, R. A., & Mangi, F. A. (2017). Intelligent travel information platform based on location base services to predict user travel behavior from user-generated GPS traces. International Journal of Computers and Applications, 39(3), 155–168.
Bali, R. S., Kumar, N., & Rodrigues, J. J. (2017). An efficient energy-aware predictive clustering approach for vehicular ad hoc networks. International Journal of Communication Systems, 30(2), e2924.
Sun, W., Liu, J., & Zhang, H. (2017). When smart wearables meet intelligent vehicles: challenges and future directions. IEEE Wireless Communications, 24(3), 58–65.
Tomandl, A., Scheuer, F., & Federrath, H. (2012). Simulation-based evaluation of techniques for privacy protection in VANETs. In 2012 IEEE 8th international conference on wireless and mobile computing, networking and communications (WiMob) (pp. 165–172). IEEE.
Yu, R., Kang, J., Huang, X., Xie, S., Zhang, Y., Gjessing, S., et al. (2016). Mixgroup: Accumulative pseudonym exchanging for location privacy enhancement in vehicular social networks. IEEE Transactions on Dependable and Secure Computing, 13(1), 93–105.
Sui, P., Li, X., & Bai, Y. (2017). A study of enhancing privacy for intelligent transportation systems: k-correlation privacy model against moving preference attacks for location trajectory data. IEEE Access, 5, 24555–24567.
Hoh, B., Gruteser, M., Xiong, H., & Alrabady, A. (2006). Enhancing security and privacy in traffic-monitoring systems. IEEE Pervasive Computing, 5(4), 38–46.
Abul, O., Bonchi, F., & Nanni, M. (2008). Never walk alone: Uncertainty for anonymity in moving objects databases. In Proceedings of the 24th international conference on data engineering (pp. 376–385).
Yarovoy, R., Bonchi, F., Lakshmanan, L., et al. (2009). Anonymizing moving objects: How to hide a MOB in a crowd? In Proceedings of the 12th international conference on extending database technology, Saint Petersburg, Russia (pp. 72–83).
Memon, I., & Arain, Q. A. (2017). Dynamic distributed mobility management system based on multiple mix-zones over road networks. arXiv preprint arXiv:1706.02252.
Emara, K., Woerndl, W., & Schlichter, J. (2015). Caps: Context-aware privacy scheme for vanet safety applications. In Proceedings of the 8th ACM conference on security & privacy in wireless and mobile networks (p. 21). ACM.
Buttyán, L., Holczer, T., Weimerskirch, A., & Whyte, W. (2009). Slow: A practical pseudonym changing scheme for location privacy in vanets. In IEEE vehicular networking conference (pp. 1–8).
Memon, I., & Arain, Q. A. (2017). Optimal placement of mix zones in road networks. arXiv preprint arXiv:1705.11104.
Wiedersheim, B., Ma, Z., Kargl, F., Papadimitratos, P. Wiedersheim B, Ma Z, et al. (2010). Privacy in inter-vehicular networks: Why simple pseudonym change is not enough. In 2010 Seventh international conference on wireless on-demand network systems and services (WONS) (pp. 176–183). IEEE.
Raya, M., & Hubaux, J. P. (2007). Securing vehicular ad hoc networks. Journal of Computer Security, 15(1), 39–68.
Song, J. H., Wong, V. W., & Leung, V. C. (2010). Wireless location privacy protection in vehicular ad-hoc networks. Mobile Networks and Applications, 15(1), 160–171.
Memon, I., Mangi, F. A., & Jamro, D. A. (2013). Collision avoidance of intelligent service robot for industrial security system. IJCSI International Journal of Computer Science Issues, 10(2), 3.
Hubaux, J. P., Capkun, S., & Luo, J. (2004). The security and privacy of smart vehicles. IEEE Security and Privacy Magazine, 2(3), 49–55.
Feiri, M., Petit, J., & Kargl, F. (2013). Efficient and secure storage of private keys for pseudonymous vehicular communication. In Proceedings of the 2013 ACM workshop on security, privacy & dependability for cyber vehicles (pp. 9–18). New York, NY: ACM.
Xie, Y., Wu, L. B., Shen, J., et al. (2017). EIAS-CP: New efficient identity-based authentication scheme with conditional privacy-preserving for VANETs. Telecommunications Systems, 65(2), 229–240.
Ferrag, M. A., Maglaras, L., & Ahmim, A. (2017). Privacy-preserving schemes for ad hoc social networks: A survey. IEEE Communications Surveys & Tutorials, 19(4), 3015–3045.
Akhtar, R., Amin, N. U., Memon, I., & Shah, M. (2012). Implementation of secure AODV in MANET. In 2012 International conference on graphic andimage processing (pp. 876803–876803-5).
Artail, H., & Abbani, N. (2016). A pseudonym management system to achieve anonymity in vehicular Ad hoc networks. IEEE Transactions on Dependable and Secure Computing, 13(1), 106–119.
Boualouache, A., & Moussaoui, S. (2017). TAPCS: Traffic-aware pseudonym changing strategy for VANETs. Peer-to-Peer Networking and Applications, 10(4), 1008–1020.
Memon, I., Chen, L., Majid, A., Lv, M., Hussain, I., & Chen, G. (2015). Travel recommendation using geo-tagged photos in social media for tourist. Wireless Personal Communications, 80, 1347–1362. https://doi.org/10.1007/s11277-014-2082-7.
Akhtar, R., Leng, S., Memon, I., Ali, M., & Zhang, L. (2015). Architecture of hybrid mobile social networks for efficient content delivery. Wireless Personal Communications, 80(1), 85–96.
Memon, I. (2015). Authentication user’s privacy: An integrating location privacy protection algorithm for secure moving objects in location based services. Wireless Personal Communications, 82(3), 1585–1600.
Memon, I. (2015). A secure and efficient communication scheme with authenticated key establishment protocol for road networks. Wireless Personal Communications, 85(3), 1167–1191.
Kamenyi, D. M., Wang, Y., Zhang, F., Memon, I., & Gustav, Y. H. (2014). Authenticated privacy preserving for continuous query in location based services. Journal of Computer Information Systems, 9(24), 9857–9864.
Domenic, M. K., Wang, Y., Zhang, F., Memon, I., & Gustav, Y. H. (2013). Preserving users’ privacy for continuous query services in road networks. In 2013 6th International conference on information management, innovation management and industrial engineering (ICIII) (Vo. 1, pp. 352–355). IEEE.
Memon, I., Mohammed, M. R., Akhtar, R., Memon, H., Memon, M. H., & Shaikh, R. A. (2014). Design and implementation to authentication over a GSM system using certificate-less public key cryptography(CL-PKC). Wireless Personal Communications, 79(1), 661–686.
Freudiger, J., Manshaei, M. H., Le Boudec, J. Y., & Hubaux, J. P. (2010). On the age of pseudonyms in mobile ad hoc networks. In INFOCOM, Proceedings IEEE (pp. 1–9). IEEE.
Gao, S., Ma, J., Shi, W., Zhan, G., & Sun, C. (2013). TrPF: A trajectory privacy-preserving framework for participatory sensing. IEEE Transactions on Information Forensics and Security, 8(6), 874–887.
Hwang, R. H., Hsueh, Y. L., & Chung, H. W. (2014). A novel time-obfuscated algorithm for trajectory privacy protection. IEEE Transactions on Services Computing, 7(2), 126–139.
Gao, S., Ma, J., Sun, C., & Li, X. (2014). Balancing trajectory privacy and data utility using a personalized anonymization model. Journal of Network and Computer Applications, 38, 125–134.
Sui, P., & Yang, X. (2018). A privacy-preserving compression storage method for large trajectory data in road network. Journal of Grid Computing, 16, 229–245.
Memon, I., Arain, Q. A., Memon, M. H., Mangi, F. A., & Akhtar, R. (2017). Search me if you can: Multiple mix zones with location privacy protection for mapping services. International Journal of Communication Systems. https://doi.org/10.1002/dac.3312.
Arain, Q. A., Memon, I., Deng, Z., Memon, M. H., Mangi, F. A., & Zubedi, A. (2018). Location monitoring approach: Multiple mix-zones with location privacy protection based on traffic flow over road networks. Multimedia Tools and Applications, 77(5), 5563–5607.
Arain, Q. A., Zhongliang, D., Memon, I., Arain, S., Shaikh, F. K., Zubedi, A., et al. (2017). Privacy preserving dynamic pseudonym-based multiple mix-zones authentication protocol over road networks. Wireless Personal Communications, 95(2), 505–521.
Arain, Q. A., Uqaili, M. A., Deng, Z., Memon, I., Jiao, J., Shaikh, M. A., et al. (2017). Clustering based energy efficient and communication protocol for multiple mix-zones over road networks. Wireless Personal Communications, 95(2), 411–428.
Boualouache, Abdelwahab., & Moussaoui, Samira. (2017). Urban pseudonym changing strategy for location privacy in VANETs. International Journal of Ad Hoc and Ubiquitous Computing, 24(1-2), 49–64.
Boualouache, Abdelwahab., Senouci, Sidi.-Mohammed., & Moussaoui, Samira. (2016). Vlpz: The vehicular location privacy zone. Procedia Computer Science, 83, 369–376.
Memon, I. (2018). Distance and clustering-based energy-efficient pseudonyms changing strategy over road network. International Journal of Communication Systems, 31(11), e3704.
Memon, I., & Mirza, H. T. (2018). MADPTM: Mix zones and dynamic pseudonym trust management system for location privacy. International Journal of Communication Systems, 31(17), e3795.
Mohammed, N., Fung, B., & Debbabi, M. (2009). Walking in the crowd: Anonymizing trajectory data for pattern analysis. In Proceedings of the 18th international conference on information and knowledge management (pp. 1441–1444). ACM.
Chen, R., Xiao, Q., Zhang, Y., et al. (2015). Differentially private high-dimensional data publication via sampling-based inference. In Proceedings of the 21st international conference on knowledge discovery and data mining (pp. 129–138). ACM.
Monreale, A., Trasarti, R., Pedreschi, D., et al. (2011). C-safety: A framework for the anonymization of semantic trajectories. Transactions on Data Privacy, 4(2), 73–101.
Yigitoglu, E., Damiani, M. L., Abul, O., et al. (2012). Privacy-preserving sharing of sensitive semantic locations under road-network constraints. In Proceedings of the 13th international conference on mobile data management (pp. 186–195). IEEE.
Castro, P. S., Zhang, D., & Li, S. (2012). Urban traffic modelling and prediction using large scale taxi GPS traces, pervasive computing (pp. 57–72). Berlin: Springer.
Zheng, Y., Zhang, L., Xie, X., et al. (2009). Mining interesting locations and travel sequences from GPS trajectories. In Proceedings of the 18th international conference on World Wide Web (pp. 791–800). ACM.
Cicek, A. E., Nergiz, M. E., & Saygin, Y. (2014). Ensuring location diversity in privacy-preserving spatio-temporal data publishing. The International Journal on Very Large Data Bases, 23(4), 609–625.
Zang, H., & Bolot, J. (2011). Anonymization of location data does not work: A large-scale measurement study. In Proceedings of the 18th international conference on mobile computing and networking (pp. 145–156). ACM.
Gambs, S., Killijian, M. O., & del Prado Cortez, M. N. (2014). De-anonymization attack on geolocated data. Journal of Computer and System Sciences, 80(8), 1597–1614.
Ma, C. Y. T., Yau, D. K. Y., Yip, N. K., et al. (2013). Privacy vulnerability of published anonymous mobility traces. Networking, 21(3), 720–733.
Memon, I., Arain, Q. A., Memon, H., & Mangi, F. A. (2017). Efficient user based authentication protocol for location based services discovery over road networks. Wireless Personal Communications, 95(4), 3713–3732.
Adu-Gyamfi, D., Wang, Y., Zhang, F., Domenic, M. K., Memon, I., & Gustav, Y. H. (2013). Modeling the spreading behavior of passive worms in mobile social networks. In 2013 6th International conference on information management, innovation management and industrial engineering (ICIII) (Vol. 1, pp. 380–383). IEEE.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Memon, I., Mirza, H.T., Arain, Q.A. et al. Multiple mix zones de-correlation trajectory privacy model for road network. Telecommun Syst 70, 557–582 (2019). https://doi.org/10.1007/s11235-019-00551-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-019-00551-1