Abstract
Due to tremendous growth in the network, security is a major concern and it is gaining a high level of attention in the system. In the Industrial control systems such as SCADA wind turbines, intruders target to corrupt information by making traffic. A Novel method known as Mesh Intruder detachment scheme has proposed to overcome such influential attacks. Enhanced intrusion detection based traffic optimization and deep learning based neural network algorithm are used to detect delay and passage caused by the intruders. The proposed scheme acts in two phases. In the first phase, redundant information such as unwanted distortions, frequency specification changes was removed and selected features were extracted for optimization. In the second phase, an Interruption attack has been detected and labeled which causes damage to the growth of production.






Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Abbreviations
- EID-TO:
-
Enhanced intrusion detection based traffic optimization
- DL-NN:
-
Deep learning based neural network algorithm
- SCADA:
-
Supervisory control and data acquisition
- IDS:
-
Intrusion detection system
- FDR:
-
Flight data recorder
- PPV:
-
Prediction of peak velocity
- FDR:
-
False detection rate
- NPV:
-
Net present value
- STO:
-
Surplus training optimization
- GA:
-
Graphical artificial intelligence
- TP:
-
True positive
- TN:
-
True negative
- FP:
-
False positive
- FP:
-
False negative
References
Wei, H., Chen, H., Guo, Y., Jing, G., & Tao, J. (2016). A survey of network anomaly detection techniques. Journal of Network and Computer Applications,60, 19–31.
Yang, Y., McLaughlin, K., Sezer, S., Littler, T., Im, E. G., Pranggono, B., et al. (2016). A concise model to evaluate the security of SCADA systems based on security standards. International Journal of Computer Applications,111(14), 1–9.
Sezer, S., Pranggono, B., & Wang, H. F. (2017). Host-based intrusion detection systems adapted from agent-based artificial immune systems. Neurocomputing Journal,88, 78–86.
Suthaharan, S., Alzahrani, M., Rajasegarar, S., Leckie, C., & Palaniswami, M. (2016). Building an intrusion detection system using a filter-based feature selection algorithm. IEEE Transactions on Computers,99, 1–13.
Sanyal, S., Das, N., & Sarkar, T. A. (2016). Accurate modeling of Modbus/TCP for intrusion detection in SCADA systems. International Journal of Critical Infrastructure Protection,6(2), 63–75.
Das, N., & Sarkar, T. (2016). Intrusion detection system: A comprehensive review. Journal of Network and Computer Applications,36(1), 16–24.
Shahzad, A., Xiong, N. N., Irfan, M., Lee, M., Hussain, S., & Khaltar, B. (2015). A SCADA intermediate simulation platform to enhance the system security. In 2015 17th International conference on advanced communication technology (ICACT) (pp. 368–373). IEEE.
Liu, A. X., & Torng, E. (2016). Overlay automata and algorithms for fast and scalable regular expression matching. IEEE/ACM Transactions on Networking, 24(4), 2400–2415.
Qiu, Y., Feny, Y., Sun, J., & Infield, D. (2016). Applying thermophysics for wind turbine drivetrain fault diagnosis using SCADA data. Institute of Engineering and Technology Journal,10(5), 661–668.
Mazidi, P., Du, M., Tjernberg, L. B., & Bobi, M. A. S. (2016). A performance and maintenance evaluation framework for wind turbines. International Journal on Probabilistic Methods Applied to Power Systems. https://doi.org/10.1109/pmaps.2016.7763931.
Tautz-Weinert, J., & Watson, S. J. (2017). Using SCADA data for wind turbine condition monitoring—A review. Institution of Engineering and Technology Journal,11, 382–394.
Straczkiewicz, M., & Barszcz, T. (2016). Application of artificial neural network for damage detection in the planetary gearbox of wind turbine. Stock and Vibration Journal. https://doi.org/10.1155/2016/4086324.
Marugan, A. P., & Marquez, F. P. G. (2017). SCADA and artificial neural networks for maintenance management. In International conference on management science and engineering management (pp. 912–919). Springer. https://doi.org/10.1007/978-3-319-59280-0_75
Fahad, A., & Mouftah, H. T. (2016). A network intrusion detection system based on a hidden Naïve Bayes multiclass classifier. Expert Systems with Applications,39(18), 13492–13500.
Almalawi, A., Yu, X., Tari, Z., Fahad, A., & Khalil, I. (2014). An unsupervised anomaly-based detection approach for integrity attacks on SCADA systems. Computers and Security,46, 94–110.
Sayegh, N., Elhajj, I. H., Kayssi, A. I., & Chehab, A. (2014). SCADA intrusion detection system based on the temporal behavior of frequent patterns. In MELECON 2014—17th IEEE mediterranean electrotechnical conference (pp. 432–448). IEEE.
Samdarshi, R., Sinha, N., & Tripathi, P. (2015). A triple layer intrusion detection system for SCADA security of electric utility. In 2015 Annual IEEE India conference (INDICON) (pp. 1–5).
Almalawi, A., Fahad, A., Tari, Z., Alamri, A., AlGhamdi, R., & Zomaya, A.Y. (2016). An efficient data-driven clustering technique to detect attacks in SCADA systems. IEEE Transactions on Information Forensics and Security,11, 893–906.
Acknowledgment
This research work has been confidentially acknowledged by Anna University recognized research center lab at V V College of Engineering, Tisaiyanvilai, India.
Funding
The data needed for the research work is taken from Gamesa Wind turbines. Since in Wind Turbines traffic based attacks and time delay based interruption attacks cause huge damage which leads to the growth in production, Real-time data stored in SCADA are taken and analyzed.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
R B. Benisha and Dr. S. Raja Ratna declare that they have no Competing interests.
Human and Animal Rights
This article does not contain any studies with animal subjects performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
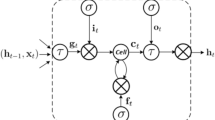
Mesh Intruder detachment scheme workflow in SCADA
Mesh Intruder detachment scheme workflow in SCADA

Rights and permissions
About this article
Cite this article
Benisha, R.B., Raja Ratna, S. Detection of interruption attack in the wireless networked closed loop industrial control systems. Telecommun Syst 73, 359–370 (2020). https://doi.org/10.1007/s11235-019-00614-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-019-00614-3