Abstract
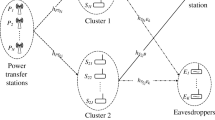
In this paper, wireless sensor network (WSN) security issue in the presence of an eavesdropper is analysed. The sensor-sink as well as sensor-eavesdropper channels are assumed to be subjected to generalized-K fading. According to the physical layer security framework, we employ round-robin, optimal sensor and cumulative distribution function-based scheduling scheme to enhance secure connection between sensor nodes and to attain low probability of intercept. Novel analytical results are given in a form of easy-to-compute analytical expressions for the intercept probability. Additionally, asymptotic closed-form expressions are derived and diversity orders of scheduling schemes are determined. Numerical results demonstrate important impacts of fading and shadowing parameters of main and wiretap links, network size and selected scheme on WSN security. Presented results are validated by independent Monte Carlo simulations.





Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Yetgin, H., Cheung, K. T. K., El-Hajjar, M., & Hanzo, L. H. (2017). A survey of network lifetime maximization techniques in wireless sensor networks. IEEE Communications Surveys & Tutorials, 19(2), 828–854.
Gungor, V. C., Lu, B., & Hancke, G. P. (2010). Opportunities and challenges of wireless sensor networks in smart grid. IEEE Transactions on Industrial Electronics, 57(10), 3557–3564.
Zou, Y., Zhu, J., Wang, X., & Hanzo, L. (2016). A survey on wireless security: Technical challenges, recent advances, and future trends. Proceedings of the IEEE, 104(9), 1727–1765.
Gandino, F., Montrucchio, B., & Rebaudengo, M. (2013). Key management for static wireless sensor networks with node adding. IEEE Transactions on Industrial Informatics, 10(2), 1133–1143.
Liu, R., & Trappe, W. (2010). Securing wireless communications at the physical layer (Vol. 7). Berlin: Springer.
Wu, Y., Khisti, A., Xiao, C., Caire, G., Wong, K.-K., & Gao, X. (2018). A survey of physical layer security techniques for 5G wireless networks and challenges ahead. IEEE Journal on Selected Areas in Communications, 36(4), 679–695.
Lei, H., Ansari, I. S., Pan, G., Alomair, B., & Alouini, M.-S. (2017). Secrecy capacity analysis over \(\alpha -\mu \) fading channels. IEEE Communications Letters, 21(6), 1445–1448.
Lei, H., Ansari, I. S., Gao, C., Guo, Y., Pan, G., & Qaraqe, K. A. (2016). Physical-layer security over generalised-K fading channels. IET Communications, 10(16), 2233–2237.
Lei, H., Zhang, H., Ansari, I. S., Gao, C., Guo, Y., Pan, G., et al. (2015). Performance analysis of physical layer security over generalized-\( k \) fading channels using a mixture Gamma distribution. IEEE Communications Letters, 20(2), 408–411.
Wu, L., Yang, L., Chen, J., & Alouini, M.-S. (2018). Physical layer security for cooperative relaying over generalized-\( k \) fading channels. IEEE Wireless Communications Letters, 7(4), 606–609.
Goel, S., & Negi, R. (2008). Guaranteeing secrecy using artificial noise. IEEE Transactions on Wireless Communications, 7(6), 2180–2189.
Zou, Y., Wang, X., & Shen, W. (2013). Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE Journal on Selected Areas in Communications, 31(10), 2099–2111.
Zou, Y., Zhu, J., Wang, X., & Leung, V. C. (2015). Improving physical-layer security in wireless communications using diversity techniques. IEEE Network, 29, 42–48.
Zou, Y., & Wang, G. (2015). Intercept behavior analysis of industrial wireless sensor networks in the presence of eavesdropping attack. IEEE Transactions on Industrial Informatics, 12(2), 780–787.
Ge, X., Wu, P., Jin, H., & Leung, V. C. (2015). Secrecy analysis of multiuser downlink wiretap networks with opportunistic scheduling. In 2015 IEEE International Conference on Communications (ICC) (pp. 7370–7375). IEEE.
Jin, H., Jung, B. C., & Leung, V. C. (2014). Fundamental limits of cdf-based scheduling: Throughput, fairness, and feedback overhead. IEEE/ACM Transactions on Networking, 23(3), 894–907.
Milošević, N. D., Anastasov, J. A., Cvetković, A. M., Milović, D. M., & Milić, D. N. (2019). On the intercept probability of DF relaying wireless communication. Wireless Personal Communications, 104(4), 1523–1533.
Bloch, M., Barros, J., Rodrigues, M. R., & McLaughlin, S. W. (2008). Wireless information-theoretic security. IEEE Transactions on Information Theory, 54(6), 2515–2534.
Prudnikov, A., Brychkov, Y., & Marichev, O. (1990). Integrals and series, part 3: More special functions (Vol. 3). Moscow: Nauka Publishers.
Adamchik, V., & Marichev, O. (1990). The algorithm for calculating integrals of hypergeometric type functions and its realization in REDUCE system. In Proceedings of the international symposium on Symbolic and algebraic computation (pp. 212–224). ACM.
Wolfram Research, Inc. The Mathematical Functions Site. http://functions.wolfram.com (1998–2019). Accessed 22 June 2019.
Acknowledgements
This work was supported by Ministry of science and technology development of Republic of Serbia (Grants III-44006, TR-32028 and TR-32051). Also, the paper is in the scope of COST Action CA 16220.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Anastasov, J.A., Cvetković, A.M., Milović, D.M. et al. On physical layer security in WSN over GK fading channels during intercept events. Telecommun Syst 74, 95–102 (2020). https://doi.org/10.1007/s11235-019-00638-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-019-00638-9