Abstract
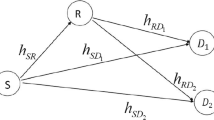
This paper derives the outage and packet error probabilities of Non Orthogonal Multiple Access (NOMA) systems. In the first time slot, the Base Station transmits a combination of two symbols \(s_w\) and \(s_s\) dedicated for weak and strong users. This signal is received by the two users and a relay. In the second time slot, the relay amplifies the received signal to the two users. Both users use the signal with the highest Signal to Interference plus Noise Ratio among direct and relayed signals. The weak user detects only its signal. Strong user first detects symbol \(s_w\) of weak user. After removing the contribution of weak user, strong user detects its own symbol \(s_s\). In this article, expressions for outage probability, Packet Error Probability and the throughput of cooperative NOMA are derived. We also optimize the power allocated to weak and strong users to maximize the system throughput.










Similar content being viewed by others
References
Li, Q. C., Niu, H., Papathanassiou, A. T., & Wu, G. (2014). 5G network capacity: Key elements and technologies. IEEE Vehicular Technology Magazine, 9(1), 71–78.
Saito, Y., Benjebbour, A., Kishiyama, Y., & Nakamura, T. (2013). System- level performance evaluation of downlink non-orthogonal multiple access (NOMA). In Proceedings of the IEEE international symposium on personal, indoor and mobile radio communications (PIMRC) (pp. 611–615).
Ding, Z., Peng, M., & Poor, H. V. (2015). Cooperative non-orthogonal multiple access in 5G systems. IEEE Communication Letters, 19(8), 1462–1465.
Ding, Z., Dai, H., & Poor, H. V. (2016). Relay selection for cooperative NOMA. IEEE Communications Letters, 5(4), 416–419.
Men, J., & Ge, J. (2015). Non-orthogonal multiple access for multiple-antenna relaying networks. IEEE Communications Letters, 19(10), 1686–1689.
Niu, Y., Gao, C., Li, Y., Su, L., & Jin, D. (2016). Exploiting multi-hop relaying to overcome blockage in directional mmwave small cells. Journal of Communications and Networks, 18(3), 364–374.
Kim, J. B., & Lee, I. H. (2015). Non-orthogonal multiple access in coordinated direct and relay transmission. IEEE Communication Letters, 19(11), 2037–2040.
Zhong, C., & Zhang, Z. (2016). Non-orthogonal multiple access with co-operative full-duplex relaying. IEEE Communication Letters, 20(12), 2478–2481.
Liu, Y. I., Ding, Z., Elkashlan, M., & Vincent Poor, H. (2016). Cooperative non-orthogonal multiple access with simultaneous wireless information and power transfer. IEEE Journal on Selected Areas in Communications, 34(4), 938–953.
Varshney, L. (2008). Transporting information and energy simultaneously. In Proceedings of the IEEE international symposium on information theory (ISIT), Toronto, ON, Canada (pp. 1612–1616).
Sun, H., Zhou, F., Hu, R. Q., & Hanzo, L. (2019). Robust beamforming design in a NOMA cognitive radio network relying on SWIPT. IEEE Journal on Selected Areas in Communications, 37(1), 142–155. (To appear in 2019).
Liu, Y., Ding, Z., Elkashlan, M., & Yuan, J. (2016). Non-orthogonal multiple access in large-scale underlay cognitive radio networks. IEEE Transactions on Vehicular Technology, 65(12), 10152–10157.
Bhattacharjee, S., Acharya, T., & Bhattacharya, U. (2018). NOMA inspired multicasting in cognitive radio networks. IET Communications, 12(15), 1845–1853.
Zhou, F., Chu, Z., Sun, H., & Leung, V. C. M. (2018). Resource allocation for secure MISO-NOMA cognitive radios relying on SWIPT. In 2018 IEEE International Conference on Communications (ICC) (pp. 1–6).
Liu, M., Song, T., & Gui, G. (2018). Deep cognitive perspective: Resource allocation for NOMA based heterogeneous IoT with imperfect SIC. IEEE Internet of Things Journal, 6, 2885–2894. (Early Access).
Xu, L., Zhou, Y., Wang, P., & Liu, W. (2018). Max-min resource allocation for video transmission in NOMA-based cognitive wireless networks. IEEE Transactions on Communications, 66(11), 5804–5813.
Li, B., Qi, X., Huang, K., Fei, Z., Zhou, F., & Hu, R. Q. (2018). Security-reliability tradeoff analysis for cooperative NOMA in cognitive radio networks. IEEE Transactions on Communications, 67, 83–96. (Early Access).
Wang, D., & Men, S. (2018). Secure energy efficiency for NOMA based cognitive radio networks with nonlinear energy harvesting. IEEE Access, 6, 62707–62716.
Wei, L., Jing, T., Fan, X., Wen, Y., & Huo, Y. (2018). The secrecy analysis over physical layer in NOMA-enabled cognitive radio networks. In 2018 IEEE international conference on communications (ICC) (pp 1– 6).
Yue, X., Liu, Y., Kang, S., & Nallanathan, A. (2017). Performance analysis of NOMA with fixed gain relaying over Nakagami-m fading channels. IEEE Access, 5, 5445–5454.
Men, J., & Ge, J. (2015). Performance analysis of non-orthogonal multiple access in downlink cooperative network. IET Communications, 9(18), 2267–2273.
Xi, Y., Burr, A., Wei, J. B., & Grace, D. (2011). A general upper bound to evaluate packet error rate over quasi-static fading channels. IEEE Transactions on Wireless Communications, 10(5), 1373–1377.
Abramowitz, M., & Stegun, I. A. (1948). Handbook of mathematical functions: With formulas, graphs, and mathematical tables (1st ed., p. 196). North Chelmsford: Courier Corporation.
Vaughan, R. J., & Venables, W. N. (1972). Permanent expressions for order statistics densities. Journal of the Royal Statistical Society: Series B (Methodological), 34, 308–310.
Acknowledgements
This work was supported by King Abdulaziz University (Grant No. This project was funded by the Deanship of Scientific Research (DSR) at King Abdulaziz University, Jeddah, Saudi Arabia, under grant TBD. The authors, therefore, acknowledge with thanks the DSR for technical and financial support.)
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A
The channel gain of weak user is lower than that of strong user i.e.
Therefore, we have
We deduce
If \(h_{BSu_1}\) and \(h_{BSu_2}\) are independent random variables (r.v.), we deduce
For Rayleigh fading channels \(|h_{BSu_1}|^2\) and \(|h_{BSu_2}|^2\) are exponentially distributed with mean
for \(i=1,2\).
Therefore, we can write
We have
We deduce
If \(h_{BSu_1}\) and \(h_{BSu_2}\) are independent random variables (r.v.), we deduce
Appendix B
Using (6), we have
Using the results of “Appendix A”, we deduce
Using (13), the outage probability of relayed link of weak user is expressed as
We deduce
Let
Therefore, we can write
We deduce
The first term of (33) is equal to
The second term of (33) is equal to
Let \(u=y-\epsilon \), we have
We have [23]
where \(K_1(.)\) is the modified Bessel function of second kind and first order.
Therefore, we obtain
Finally, (33), (34) and (38) give the outage probability of weak user is written as
Appendix C
The first term of (17) is expressed as
where
Using the results of “Appendix A” (26), we deduce
The second term of (17) is expressed as
where
Therefore, last equation gives
Let \(z=y-b\), we deduce
Using (42) and (48), the outage probability of strong user is written as
Appendix D
User \(u_i\) has the i-th largest channel gain. Its PDF is given by [24]
where \(p_1\), \(p_2\), ..., \(p_N\) are relay indexes different from q, \(p_1\ne p_2 \ne p_{N-1}\), \(p_1<p_2<\cdots <p_{N-i}\) and \(p_{N-i+1}<p_{N-i+2}<\cdots <p_{N-1}\).
We have
where
The CDF of the channel gain of i-th user is deduced by a primitive of the PDF
Rights and permissions
About this article
Cite this article
Alnwaimi, G., Boujemaa, H. & Arshad, K. Throughput optimization of cooperative non orthogonal multiple access. Telecommun Syst 76, 359–370 (2021). https://doi.org/10.1007/s11235-020-00726-1
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-020-00726-1