Abstract
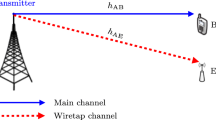
In this article, we compute the Secrecy Outage Probability (SOP) and the Probability of Strictly Positive Secrecy Capacity (SPSC) for Cognitive Radio Networks with Adaptive Transmit Power and energy harvesting using multiple antennas. The secondary source harvests power using multiple antennas using node A signal. Node A is a node transmitting Radio Frequency signals. Then, it adapts its power to generate interference at primary receiver \(P_R\) less than T. Our analysis takes into consideration the interference between primary and secondary nodes. In fact, the Signal to Interference plus Noise Ratio is analyzed at the secondary destination in the presence of interference from the primary transmitter. We derive the SOP and SPSC when the secondary source and destination have multiple antennas. The transmission is made from the best antenna of the secondary source to the best receiving antenna at the secondary destination.











Similar content being viewed by others
References
Fang, D., Qian, Y., & Hu, R. Q. (2018). Security for 5G mobile wireless networks. IEEE Access, 6, 4850–4874.
Bloch, M., & Barros, J. (2011). Physical-layer security: From information theory to security engineering. Cambridge: Cambridge University Press.
Zhang, Y., Wang, H.-M., Yang, Q., et al. (2016). Secrecy sum rate maximization in non-orthogonal multiple access. IEEE Communications Letters, 20(5), 930–933.
Qin, Z., Liu, Y., & Ding, Z., et al. (2016). Physical layer security for 5G non-orthogonal multiple access in large-scale networks. In Communications (ICC), IEEE international conference on. IEEE, 2016, pp. 1–6.
Liu, Y., Qin, Z., Elkashlan, M., et al. (2017). Enhancing the physical layer security of non-orthogonal multiple access in large-scale networks. IEEE Transactions on Wireless Communications, 16(3), 1656–1672.
He, B., Lv, L., Yang, L., Chen, J. (2020). Enhancing secrecy for NOMA untrusted relay networks with user scheduling and jamming. IEEE Communications Letters, Early Access Article.
Thapar, S., Mishra, D., & Saini, R. (2020). Novel outage-aware NOMA protocol for secrecy fairness maximization among untrusted users. IEEE Transactions on Vehicular Technology, Early Access Article.
Webb, H., Yin, C., Nguyen, D. N., Le., T. T. N., Van Do, H., van Hoang, D., & Van Nguyen, N. (2020). Secrecy outage analysis in energy harvesting relay networks with a friendly jammer. In 2020 4th International conference on recent advances in signal processing, telecommunications and computing (SigTelCom).
Dang-Ngoc, H., Ho-Quoc, B., Ho-Van, K. (2020). Key secrecy performance metrics of overlay networks with energy scavenging and artificial noise. In 4th International conference on recent advances in signal processing, telecommunications and computing (SigTelCom).
Trinh, P. V., Carrasco-Casado, A., Pham, A. T., & Toyoshima, M. (2020). Secrecy analysis of FSO systems considering misalignments and eavesdropper’s location. IEEE Transactions on Communications, Early Access Article.
You, B., Lee, I.-H., & Jung, H. (2020). Exact secrecy rate analysis of antenna subset modulation schemes. IEEE Systems Journal.
Kumar, S., Garg, A., & Bhatnagar, M. R. (2020). Physical layer secrecy performance analysis of imperfect feedback based 4\(\times \)1 MISO system. In International conference on signal processing and communications (SPCOM).
Khojastehnia, M., & Loyka, S. (2020). Comments on ‘Precoding for secrecy rate maximisation in cognitive MIMO wiretap channels. Electronics Letters, 56(17).
LLi, C., He, J., Liu, S., Guo, D., Song, L. (2020). On secrecy key of a class of secure asymmetric multilevel diversity coding system. IEEE International symposium on information theory (ISIT).
Shkel, Y. Y., & Poor, H. V. (2020). A compression perspective on secrecy measures. In IEEE international symposium on information theory (ISIT).
Gu, X., Duan, W., Zhang, G., Sun, Q., Wen, M., Ho, P. H. (2022). Physical layer security for RIS-aided wireless communications with uncertain eavesdropper distributions. IEEE Systems Journal.
Tu, L.-T., & Bradai, A. (2021). On the performance of physical layer security of RIS-aided communications. In IEEE conference on antenna measurements and applications (CAMA).
Khalid, W., Yu, H., Do, D. T., Kaleem, Z., Noh, S. (2021). RIS-aided physical layer security with full-duplex jamming in underlay D2D networks. IEEE Access, 9.
Makarfi, A., Rabie, K., Kaiwartya, O., Badarneh, O., Nauryzbayev, G., Kharel, R. (2020). Physical layer security in RIS-assisted networks in Fisher-Snedecor composite fading. In 2020 12th International symposium on communication systems, networks and digital signal processing (CSNDSP).
Tang, Z., Hou, T., Liu, Y., Zhang, J., Zhong, C. (2021). A novel design of RIS for enhancing the physical layer security for RIS-aided NOMA networks. IEEE Wireless Communications Letters, 10(11).
Salh, A., Audah, L., Alhartomi, M. A., Kim, K. S., Alsamhi, S. H., Almalki, F. A., Abdullah, Q., Saif, A., & Algethami, H. (2022). Smart packet transmission scheduling in cognitive IoT systems: DDQN based approach. IEEE Access, 10.
Salh, A., Audah, L., Kim, K. S., Alsamhi, S. H., Alhartomi, M. A., Abdullah, Q., Almalki, F. A., & Algethami, H. (2022). Refiner GAN algorithmically enabled deep-RL for guaranteed traffic packets in real-time URLLC B5G communication systems. IEEE Access, 10.
Saif, A., Dimyati, K., Noordin, K. A., Mohd Shah, N. S., Alsamhi, S. H., & Abdullah, Q. (2021) Energy-efficient tethered UAV deployment in B5G for smart environments and disaster recovery. In 1st International conference on emerging smart technologies and applications (eSmarTA).
Proakis, J. (2007). Digital communications, 5th edition, Mac Graw-Hill.
Hasna, M., & Alouini, M. S. (2003). End-to-end performance of transmission systems with relays over Rayleigh fading channels. IEEE Transactions on Wireless Communications, 2, 1126–1131.
Hussain, S. I., Alouini, M. S., Qarage, K., & Hasna, M. (2012). Reactive relay selection in underlay cognitive networks with fixed gain relays. In IEE International conference on communications, pp. 1784–1788.
Gradshteyn, I. S., & Ryzhik, I. M. (1994). Table of integrals, series and products (5th ed.). Academic: San Diego, CA.
Funding
This publication was supported by the Deanship of Scientific Research at Prince Sattam bin Abdulaziz University, Alkharj, Saudi Arabia.
Author information
Authors and Affiliations
Contributions
Data and material are not available. Software application and custom code are non available. This article is the contribution of Dr. Faisal Alanazi.
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest for this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Alanazi, F. Physical layer security of cognitive radio networks with adaptive transmit power and multi-antenna energy harvesting. Telecommun Syst 83, 91–99 (2023). https://doi.org/10.1007/s11235-023-01011-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-023-01011-7