Abstract
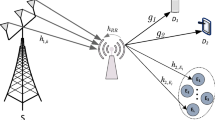
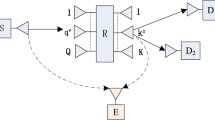
This paper investigates the physical layer security (PLS) performance of full-duplex cooperative non-orthogonal multiple access (FD-CNOMA) network in the presence of an external passive eavesdropper. Firstly, we derive approximate analytical expressions for the secrecy outage probabilities (SOPs) of the downlink users and the system SOP (SSOP) of a single-cell FD-CNOMA network, considering the presence/absence of direct link from the base station (BS) to the far user, under imperfect successive interference cancellation conditions. We consider both perfect channel state information and imperfect CSI conditions. To enhance the PLS performance, we propose an artificial noise (AN)-aided framework and derive approximate analytical expressions for the SOPs of the downlink users and the SSOP of the AN-aided FD-CNOMA network. The asymptotic SOP and SSOP expressions are also derived, which are used to determine the secrecy diversity orders. The proposed AN-aided framework significantly reduces the SOPs of the users and the SSOP of the network compared to that without AN. To further enhance the PLS performance, we use the Polak-Ribiere conjugate gradient method to determine the optimal power allocation coefficient (OPAC) for the users at the BS that minimizes the SSOP of the AN-aided FD-CNOMA network. The proposed OPAC significantly reduces the SOPs of the users and the SSOP, compared to random selection/equal setting of the PACs. Finally, we extend the performance evaluations to a multi-cell scenario and demonstrate that the PLS performance of the FD-CNOMA network significantly deteriorates in the presence of co-channel interference.





















Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Data availability
Material and data are not available.
Notes
The evaluation is extended for a multi-cell scenario in Sect. 4 of this paper.
Even though the BS can serve several downlink NOMA users, it leads to highly complex SIC procedure at the receivers. Hence, a two user scenario is considered in this paper.
Here the SOP evaluation is carried out considering two users per cluster. Evaluation for a multi-user scenario will be considered as a future extension.
References
Tariq, F., Khandaker, M. R., Wong, K.-K., Imran, M. A., Bennis, M., & Debbah, M. (2020). A speculative study on 6G. IEEE Wireless Communications, 27(4), 118–125. https://doi.org/10.1109/MWC.001.1900488
David, K., & Berndt, H. (2018). 6G vision and requirements: Is there any need for beyond 5G? IEEE Vehicular Technology Magazine, 13(3), 72–80. https://doi.org/10.1109/MVT.2018.2848498
Alsabah, M., Naser, M. A., Mahmmod, B. M., Abdulhussain, S. H., Eissa, M. R., Al-Baidhani, A., Noordin, N. K., Sait, S. M., Al-Utaibi, K. A., & Hashim, F. (2021). 6G wireless communications networks: A comprehensive survey. IEEE Access, 9, 148191–148243. https://doi.org/10.1109/ACCESS.2021.3124812
Chen, S., Liang, Y.-C., Sun, S., Kang, S., Cheng, W., & Peng, M. (2020). Vision, requirements, and technology trend of 6G: How to tackle the challenges of system coverage, capacity, user data-rate and movement speed. IEEE Wireless Communications, 27(2), 218–228. https://doi.org/10.1109/MWC.001.1900333
Ding, Z., Liu, Y., Choi, J., Sun, Q., Elkashlan, M., Chih-Lin, I., & Poor, H. V. (2017). Application of non-orthogonal multiple access in LTE and 5G networks. EEE Communications Magazi, 55(2), 185–191. https://doi.org/10.1109/MCOM.2017.1500657CM
Vaezi, M., Schober, R., Ding, Z., & Poor, H. V. (2019). Non-orthogonal multiple access: Common myths and critical questions. IEEE Wireless Communications, 26(5), 174–180. https://doi.org/10.1109/MWC.2019.1800598
Chen, Y., Bayesteh, A., Wu, Y., Ren, B., Kang, S., Sun, S., Xiong, Q., Qian, C., Yu, B., Ding, Z., et al. (2018). Toward the standardization of non-orthogonal multiple access for next generation wireless networks. IEEE Communications Magazine, 56(3), 19–27. https://doi.org/10.1109/MCOM.2018.1700845
Yue, X., Liu, Y., Kang, S., Nallanathan, A., & Ding, Z. (2017). Exploiting full/half-duplex user relaying in NOMA systems. IEEE Transactions on Communications, 66(2), 560–575. https://doi.org/10.1109/TCOMM.2017.2749400
Ding, Z., Dai, H., & Poor, H. V. (2016). Relay selection for cooperative NOMA. IEEE Wireless Communications Letters, 5(4), 416–419. https://doi.org/10.1109/LWC.2016.2574709
Vaezi, M., Baduge, G. A. A., Liu, Y., Arafa, A., Fang, F., & Ding, Z. (2019). Interplay between NOMA and other emerging technologies: A survey. IEEE Transactions on Cognitive Communications and Networking, 5(4), 900–919. https://doi.org/10.1109/TCCN.2019.2933835
Sharma, S. K., Bogale, T. E., Le, L. B., Chatzinotas, S., Wang, X., & Ottersten, B. (2017). Dynamic spectrum sharing in 5g wireless networks with full-duplex technology: Recent advances and research challenges. IEEE Communications Surveys & Tutorials, 20(1), 674–707. https://doi.org/10.1109/COMST.2017.2773628
Duarte, M., Dick, C., & Sabharwal, A. (2012). Experiment-driven characterization of full-duplex wireless systems. IEEE Transactions on Wireless Communications, 11(12), 4296–4307. https://doi.org/10.1109/TWC.2012.102612.111278
Mohammadi, M., Shi, X., Chalise, B. K., Ding, Z., Suraweera, H. A., Zhong, C., & Thompson, J. S. (2019). Full-duplex non-orthogonal multiple access for next generation wireless systems. IEEE Communications Magazine, 57(5), 110–116. https://doi.org/10.1109/MCOM.2019.1800578
Chu, T. M. C., & Zepernick, H.-J. (2018). Performance of a non-orthogonal multiple access system with full-duplex relaying. IEEE Communications Letters, 22(10), 2084–2087. https://doi.org/10.1109/LCOMM.2018.2852308
Nwankwo, C. D., Zhang, L., Quddus, A., Imran, M. A., & Tafazolli, R. (2017). A survey of self-interference management techniques for single frequency full duplex systems. IEEE Access, 6, 30242–30268. https://doi.org/10.1109/ACCESS.2017.2774143
Zou, Y., Zhu, J., Wang, X., & Hanzo, L. (2016). A survey on wireless security: Technical challenges, recent advances, and future trends. Proceedings of the IEEE, 104(9), 1727–1765. https://doi.org/10.1109/JPROC.2016.2558521
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54(8), 1355–1387. https://doi.org/10.1002/j.1538-7305.1975.tb02040.x
Wu, Y., Khisti, A., Xiao, C., Caire, G., Wong, K.-K., & Gao, X. (2018). A survey of physical layer security techniques for 5G wireless networks and challenges ahead. IEEE Journal on Selected Areas in Communications, 36(4), 679–695. https://doi.org/10.1109/JSAC.2018.2825560
Chen, J., Yang, L., & Alouini, M.-S. (2018). Physical layer security for cooperative NOMA systems. IEEE Transactions on Vehicular Technology, 67(5), 4645–4649. https://doi.org/10.1109/TVT.2017.2789223
Yu, C., Ko, H.-L., Peng, X., Xie, W., & Zhu, P. (2019). Jammer-aided secure communications for cooperative NOMA systems. IEEE Communications Letters, 23(11), 1935–1939. https://doi.org/10.1109/LCOMM.2019.2934410
Lei, H., Yang, Z., Park, K.-H., Ansari, I. S., Guo, Y., Pan, G., & Alouini, M.-S. (2019). Secrecy outage analysis for cooperative NOMA systems with relay selection schemes. IEEE Transactions on Communications, 67(9), 6282–6298. https://doi.org/10.1109/TCOMM.2019.2916070
Feng, Y., Yan, S., Liu, C., Yang, Z., & Yang, N. (2018). Two-stage relay selection for enhancing physical layer security in non-orthogonal multiple access. IEEE Transactions on Information Forensics and Security, 14(6), 1670–1683. https://doi.org/10.1109/TIFS.2018.2883273
Salem, A., Musavian, L., Jorswieck, E. A., & Aïssa, S. (2020). Secrecy outage probability of energy-harvesting cooperative NOMA transmissions with relay selection. IEEE Transactions on Green Communications and Networking, 4(4), 1130–1148. https://doi.org/10.1109/TGCN.2020.2999815
Lei, R., Xu, D., & Ahmad, I. (2021). Secrecy outage performance analysis of cooperative NOMA networks with SWIPT. IEEE Wireless Communications Letters, 10(7), 1474–1478. https://doi.org/10.1109/LWC.2021.3070429
Lv, L., Jiang, H., Ding, Z., Yang, L., & Chen, J. (2019). Secrecy-enhancing design for cooperative downlink and uplink NOMA with an untrusted relay. IEEE Transactions on Communications, 68(3), 1698–1715. https://doi.org/10.1109/TCOMM.2019.2960345
Jameel, F., Khan, W.U., Chang, Z., Ristaniemi, T., & Liu, J. (2019). Secrecy analysis and learning-based optimization of cooperative NOMA SWIPT systems. In 2019 IEEE International Conference on Communications Workshops (ICC Workshops) (pp. 1–6). IEEE. https://doi.org/10.1109/ICCW.2019.8756894
Nayak, V. N., & Gurrala, K. K. (2021). Power allocation-assisted secrecy analysis for NOMA enabled cooperative network under multiple eavesdroppers. ETRI Journal, 43(4), 758–768. https://doi.org/10.4218/etrij.2020-0084
Jin, Y., Hu, Z., Xie, D., Wu, G., & Zhou, L. (2021). Physical layer security transmission scheme based on artificial noise in cooperative SWIPT NOMA system. EURASIP Journal on Wireless Communications and Networking, 2021(1), 1–17. https://doi.org/10.1186/s13638-021-02020-3
Cao, K., Wang, B., Ding, H., Li, T., & Gong, F. (2019). Optimal relay selection for secure NOMA systems under untrusted users. IEEE Transactions on Vehicular Technology, 69(2), 1942–1955. https://doi.org/10.1109/TVT.2019.2962860
Arafa, A., Shin, W., Vaezi, M., & Poor, H. V. (2019). Secure relaying in non-orthogonal multiple access: Trusted and untrusted scenarios. IEEE Transactions on Information Forensics and Security, 15, 210–222. https://doi.org/10.1109/TIFS.2019.2911162
Xu, S., Liu, C., Qian, M., Wang, H., & Sun, W. (2021). Secure transmission for cooperative NOMA systems with source-relay selection. IET Communication, 15(20), 2537–2551. https://doi.org/10.1049/cmu2.12293
Zaghdoud, N., Mnaouer, A., Boujemaa, H., & Touati, F. (2020). Secrecy performance analysis of cooperative NOMA system with multiple DF relays. In 2020 international wireless communications and mobile computing (pp. 2160–2163.)
Ruby, R., Pham, Q.-V., Wu, K., Heidari, A. A., Chen, H., & ElHalawany, B. M. (2021). Enhancing secrecy performance of cooperative NOMA-based IoT networks via multiantenna-aided artificial noise. IEEE Internet of Things Journal, 9(7), 5108–5127. https://doi.org/10.1109/JIOT.2021.3109943
Zaghdoud, N., Mnaouer, A. B., Boujemaa, H., & Touati, F. (2022). Secrecy performance analysis of half/full duplex AF/DF relaying in NOMA systems over \(\kappa \)-\(\mu \) fading channels. Telecommunication Systems, 79(2), 213–231. https://doi.org/10.1007/s11235-021-00851-5
Su, B., Yu, W., Liu, H., Chorti, A., & Poor, H. V. (2022). Secure transmission design for cooperative NOMA in the presence of internal eavesdropping. IEEE Wireless Communications Letters, 11(5), 878–882. https://doi.org/10.1109/LWC.2021.3098935
Li, H., Chen, Y., Zhu, M., Sun, J., Do, D.-T., Menon, V. G., & Shynu, P. (2020). Secrecy outage probability of relay selection based cooperative NOMA for IoT networks. IEEE Access, 9, 1655–1665. https://doi.org/10.1109/ACCESS.2020.3047136
Guo, C., Zhao, L., Feng, C., Ding, Z., & Wang, H.-M. (2020). Secrecy performance of NOMA systems with energy harvesting and full-duplex relaying. IEEE Transactions on Vehicular Technology, 69(10), 12301–12305. https://doi.org/10.1109/TVT.2020.3008715
Lv, L., Ding, Z., Chen, J., & Al-Dhahir, N. (2019). Design of secure NOMA against full-duplex proactive eavesdropping. IEEE Wireless Communications Letters, 8(4), 1090–1094. https://doi.org/10.1109/LWC.2019.2907852
Ren, Y., Tan, Y., Makhanbet, M., & Zhang, X. (2021). Improving physical layer security of cooperative NOMA system with wireless-powered full-duplex relaying. Information, 12(7), 279. https://doi.org/10.3390/info12070279
Shim, K., Do, T. N., Nguyen, T.-V., Costa, D. B., & An, B. (2021). Enhancing phy-security of FD-enabled NOMA systems using jamming and user selection: Performance analysis and DNN evaluation. IEEE Internet of Things Journal, 8(24), 17476–17494. https://doi.org/10.1109/JIOT.2021.3080425
Feng, Y., Yang, Z., & Yan, S. (2017). Non-orthogonal multiple access and artificial-noise aided secure transmission in FD relay networks. In 2017 IEEE globecom workshops (GC Wkshps) (pp. 1–6). IEEE. https://doi.org/10.1109/GLOCOMW.2017.8269229
Cao, Z., Ji, X., Wang, J., Wang, W., Cumanan, K., Ding, Z., & Dobre, O. A. (2021). Artificial noise aided secure communications for cooperative NOMA networks. IEEE Transactions on Cognitive Communications and Networking, 8(2), 946–963. https://doi.org/10.1109/TCCN.2021.3130979
Cao, Y., Zhao, N., Pan, G., Chen, Y., Fan, L., Jin, M., & Alouini, M.-S. (2019). Secrecy analysis for cooperative NOMA networks with multi-antenna full-duplex relay. IEEE Transactions on Communications, 67(8), 5574–5587. https://doi.org/10.1109/TCOMM.2019.2914210
Guo, W., & Liu, Y. (2021). On the performance of physical layer security in virtual full-duplex non-orthogonal multiple access system. EURASIP Journal on Wireless Communications and Networking, 2021(1), 1–14. https://doi.org/10.1186/s13638-021-02009-y
Zheng, B., Wen, M., Wang, C.-X., Wang, X., Chen, F., Tang, J., & Ji, F. (2018). Secure NOMA based two-way relay networks using artificial noise and full duplex. IEEE Journal on Selected Areas in Communications, 36(7), 1426–1440. https://doi.org/10.1109/JSAC.2018.2824624
Sun, Y., Ng, D. W. K., Zhu, J., & Schober, R. (2018). Robust and secure resource allocation for full-duplex miso multicarrier NOMA systems. IEEE Transactions on Communications, 66(9), 4119–4137. https://doi.org/10.1109/TCOMM.2018.2830325
Gong, C., Yue, X., Zhang, Z., Wang, X., & Dai, X. (2021). Enhancing physical layer security with artificial noise in large-scale NOMA networks. IEEE Transactions on Vehicular Technology, 70(3), 2349–2361. https://doi.org/10.1109/TVT.2021.3057661
Zaghdoud, N., Mnaouer, A.B., Alouane, W.H., Boujemaa, H., & Touati, F. (2020). Secure performance analysis for full-duplex cooperative NOMA system in the presence of multiple eavesdroppers. In 2020 international wireless communications and mobile computing (IWCMC) (pp. 1719–1725). https://doi.org/10.1109/IWCMC48107.2020.9148456
Liu, C., Zhang, L., Xiao, M., Chen, Z., & Li, S. (2018). Secrecy performance analysis in downlink NOMA systems with cooperative full-duplex relaying. In 2018 IEEE international conference on communications workshops (ICC workshops) (pp. 1–6). IEEE. https://doi.org/10.1109/ICCW.2018.8403764
Abbasi, O., & Ebrahimi, A. (2017). Secrecy analysis of a NOMA system with full duplex and half duplex relay. In 2017 Iran workshop on communication and information theory (IWCIT) (pp. 1–6). IEEE. https://doi.org/10.1109/IWCIT.2017.7947676
Wang, C., Liu, T.C.-K., & Dong, X. (2012). Impact of channel estimation error on the performance of amplify-and-forward two-way relaying. IEEE Transactions on Vehicular Technology, 61(3), 1197–1207. https://doi.org/10.1109/TVT.2012.2185964
Do, D.-T., Le, T. A., Nguyen, T. N., Li, X., & Rabie, K. M. (2020). joint impacts of imperfect CSI and imperfect SIC in cognitive radio-assisted NOMA-v2x communications. IEEE Access, 8, 128629–128645. https://doi.org/10.1109/ACCESS.2020.3008788
Liang, X., Wu, Y., Ng, D. W. K., Jin, S., Yao, Y., & Hong, T. (2020). Outage probability of cooperative NOMA networks under imperfect CSI with user selection. IEEE Access, 8, 117921–117931. https://doi.org/10.1109/ACCESS.2020.2995875
Bertsekas, D. P. (2014). Constrained optimization and Lagrange multiplier methods. Academic Press.
Shin, W., Vaezi, M., Lee, B., Love, D. J., Lee, J., & Poor, H. V. (2017). Non-orthogonal multiple access in multi-cell networks: Theory, performance, and practical challenges. IEEE Communications Magazine, 55(10), 176–183. https://doi.org/10.1109/MCOM.2017.1601065
Wang, K., Liu, Y., Ding, Z., Nallanathan, A., & Peng, M. (2019). User association and power allocation for multi-cell non-orthogonal multiple access networks. IEEE Transactions on Wireless Communications, 18(11), 5284–5298. https://doi.org/10.1109/TWC.2019.2935433
Goldsmith, A. (2005). Wireless communications. Cambridge University Press.
Sesia, S., Toufik, I., & Baker, M. (2011). LTE-the UMTS long term evolution: From theory to practice. Wiley.
Gradshteyn, I. S., & Ryzhik, I. M. (2014). Table of integrals, series, and products. Academic Press.
Abramowitz, M., & Stegun, I. A. (1948). Handbook of mathematical functions with formulas, graphs, and mathematical tables (p. 55). US Government Printing Office.
Acknowledgements
The authors would like to thank the Department of Science and Technology, Government of India for supporting their research under the FIST scheme No. SR/FST/ETI/2017/68.
Funding
No funding was received for this research work.
Author information
Authors and Affiliations
Contributions
Both authors contributed equally to this work.
Corresponding author
Ethics declarations
Conflict of interest
The authors state that there is no conflict of interest for this paper.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix
Derivation of (19)
Recall the following expression for \(P_1^{AN}\) given by (18b):
Let \(X= |h_{b1}|^2\), \(Y= |h_{11}|^2\), \(Z=|h_{be}|^2\), \(U= |h_{1e}|^2\), \(V= |h_{12}|^2\) and \(W= |h_{b2}|^2\). Utilizing \(\Gamma _{1,x_2}^{AN}\), \(\Gamma _{1,x_1}^{AN}\) and \(\Gamma _{e,x_1}^{AN}\) given by (4a), (4b) and (8a) respectively, \(J_1\) can be written as:
where \(\xi _o= \frac{\gamma _2}{\rho _b (\alpha _2-\alpha _1\gamma _2)}\), \(Q= \frac{2^{R_{s,1}}\alpha _1\rho _b Z}{\theta _2 \rho _1U +1}\) and \(\mu _1= 2^{R_{s,1}}-1\). Now (A.2) can be further written using probability rule, i.e., \(\text {Pr}(a< x< b) = \text {Pr}(X< b) -\text {Pr}(X < a)\) as:
Since \(X\sim \text {exp} (\lambda _{b1})\), \(J_{11}\) is determined as:
where \(\vartheta _1 =\frac{\alpha _1}{\beta \alpha _2}-\mu _1\); \(f_Y(y)\) and \(f_Q(q)\) are the PDFs of Y and Q respectively. Since \(Y\sim \text {exp}(\lambda _{11})\), the inner integral can be simplified. As a result, \(J_{11}\) becomes:
To evaluate (A.5), the PDF \(f_Q(q)\) must be known. The CDF of Q, i.e., \(F_Q(q)\) is determined as:
Since \(Z \sim \text {exp}(\lambda _{be})\), \(U \sim \text {exp}(\lambda _{1e})\) and Z and U are assumed as independent, the pdf \(f_Q(q)\) can be obtained as:
where \( p_1= 2^{R_{s,1}}\alpha _1\rho _b\lambda _{be}\) and \(p_2 = \theta _2\rho _1\lambda _{1e}\). Finally, \(J_{11}\) can be determined by substituting (A.7) in (A.5). However, we can observe that a tractable closed form expression cannot be obtained for \(J_{11}\). Utilizing Gaussian- Chebyshev Quadrature formula [59, Eq. (25.4.38)], \(J_{11}\) can be approximated as in (A.8), where \(\frac{\mu _1\beta }{1+\mu _1\beta }<\alpha _1<0.5\), \(S_n= \text {cos}(\frac{(2n-1)}{2N}\pi )\), N is the complexity accuracy trade-off parameter in the above approximation and \(a_n =\frac{\vartheta _1}{2}\left( 1+S_n\right) \).
Since X and Y are assumed as independent, \(J_{12}\) can be obtained as:
where \(0<\alpha _1<\frac{1}{1+\gamma _2}\). Now substituting for \(\Gamma _{1,x_2}^{AN}\), \(J_{2}\) in (A.1) becomes \(J_2=\text {Pr}\bigl [X<\xi _0(\rho _1Y+1)\bigr ]\). Thus \(J_2=J_{12}\), which is given by (A.9). Accordingly, \(P_1^{AN}\triangleq J_{11}-J_{12}+J_{2}=J_{11}\), which is given by (19). It can be observed that if \(\alpha _1< \frac{\mu _1\beta }{1+\mu _1\beta }\), \(J_{11}\) becomes unity, so that \(P_1^{AN}\rightarrow 1\).
Derivation of (20)
Recall the following expression for \(P_1^{nAN}\) given by (18c):
Utilizing the expressions for \(\Gamma _{1,x_1}^{nAN}\), \(\Gamma _{1,x_2}^{nAN}\) and \(\Gamma _{e,x_1}^{nAN}\) in (B.1) and on utilizing \(\text {Pr}(a<X<b)=\text {Pr}(X<b)- \text {Pr}(X<a)\), \(J_3\) becomes:
where \(k_0= 2^{R_{s,1}}\alpha _1\rho _b\). Now \(J_{31}\) is determined as:
Notice that \(J_{31}\) is similar to \(J_{11}\) given in (A.4). Further, it is difficult to get a tractable closed form expression for \(J_{34}\). By utilizing the Gaussian-Chebyshev quadrature formula [59, Eq. (25.4.38)], \(J_{31}\) can be approximated as in (B.4),
where \(\frac{\mu _1\beta }{1+\mu _1\beta }< \alpha _1<0.5\), \(b_n =\frac{\vartheta _1}{2k_0}(1+S_n)\). Notice that \(J_{32}\) in (B.2) is equivalent to \(J_{12}\) given in Appendix A, which is given by (A.9). Further, \(J_4\)=\(J_{32}\). Hence, \(P_1^{nAN} \triangleq J_{31}-J_{32}+J_{4}= J_{31}\) and is given by (20). Notice that (B.4) is valid if and only if \(\alpha _1>\frac{\mu _1\beta }{1+\mu _1\beta }\). Otherwise, \(J_{31}\) \(\rightarrow 1\) which makes \(P_1^{nAN}\rightarrow 1\).
Derivation of (21a) and (21b)
1.1 Derivation of (21a)
From Appendix A, it can be seen that \(P_1^{AN} \triangleq J_{11}\). To determine \(P_{1,asy}^{AN}\), we set \(\rho _b=\rho _1=\rho \rightarrow \infty \) and \( \underset{\rho \rightarrow \infty }{\text {lim}}\) \(e^{\frac{-x}{\rho }}\simeq 1\) in \(J_{11}\) given by (A.5). Accordingly, \(P_{1,asy}^{AN}\) becomes:
By applying partial fraction decomposition method and solving the resulting integrals, \(P_{1,asy}^{AN}\) of (21a) can be obtained.
1.2 Derivation of (21b)
In Appendix B, it was proved that \(P_1^{nAN}\)=\(J_{31}\). To determine \(P_{1,asy}^{nAN}\), we use the integral expression for \(J_{31}\) given by (B.3). By setting \(\rho _b=\rho _1=\rho \rightarrow \infty \) and \(\underset{\rho \rightarrow \infty }{\text {lim}}\) \(e^{\frac{-x}{\rho }}\simeq 1\), \(P_{1,asy}^{nAN}\) can be obtained as given in (21b).
Derivation of (23a)
Substituting (16b) for \(C_{s,2}^{AN}\) in (22b) and rearranging, we get (D.1),
where \(\mu _2=2^{R_{s,2}}-1\). Substituting for \(\Gamma _{1,x_2}^{AN}\), \(\Gamma _{2,x_2}^{AN}\) and \(\Gamma _{e,x_2}^{AN}\), and using \(\text {Pr}(a< x< b) = \text {Pr}(X<b) -\text {Pr}(X<a)\), \(H_1\) can be written as:
where \(T=\frac{2^{R_{s,2}}\alpha _2\rho _b Z}{\theta _2 \rho _1U +1}\). Notice that \(H_{11}\) and \(H_{12}\) are similar to the terms \(J_{11}\) and \(J_{12}\) respectively, given by (A.3) of Appendix A. Accordingly, we write the following approximation for \(H_{11}\) using Gaussian- Chebyshev quadrature formula [59, Eq. (25.4.38)] as given in (D.3),
where \(\vartheta _2=\frac{\alpha _2}{\alpha _1}-\mu _2\), \(\alpha _1<\frac{1}{1+\mu _2}\), \(p_3= 2^{R_{s,2}}\alpha _2\rho _b\lambda _{be}\) and \(c_n= \frac{\vartheta _2}{2}(1+S_n)\). Further, \(H_{12}=J_{12}\) given by (A.9) of Appendix A. Since \(V\sim \text {exp}(\lambda _{12})\), \(W\sim \text {exp}(\lambda _{b2})\) and V and W are assumed as independent, \(H_{13}\) can be obtained as:
Utilizing (4a), (6) and (8b) in (D.1) and simplifying, \(H_2\) becomes as in (D.5),
where \(M= \frac{\theta _1\rho _1V}{\rho _bW+1}\). Since X and U are independent exponential random variables, \(H_{21}\) can be obtained as:
Now \(H_{22}\) can be determined as:
where the pdf \(f_M(m)\) can be written similar to (A.7) of Appendix A as:
here \(p_4=\theta _1\rho _1\lambda _{12}\) and \(p_5=\rho _b\lambda _{b2}\). On substituting (D.8) in (D.7) and after integrating w.r.t. y, (D.7) becomes:
where \(g_0=\frac{p_3+p_4}{p_3p_4}\); \(g_1= \frac{p_4+p_4p_5}{p_5}\); \(g_2=\frac{p_3}{\theta _2\rho _1\lambda _{1e}}-\frac{\mu _2}{\lambda _{1e}}\) and \(g_3= \frac{p_4}{p_5}\). We now apply the product rule of integration and then use partial fraction decomposition. Thereafter, we use (3.353.2) and (3.352.3) given in [60] to get \(H_{22}\) as in (D.10), where \(\psi _1= -\frac{g_1-g_2}{\left( g_2 -g_3 \right) \left( g_3-1 \right) }\); \(\psi _2 =\frac{g_3-1-g_1+g_2}{g_3-1}\) and Ei(.) is the exponential integral function.
Further, it can be seen that \(H_{23}= 1-H_{13}\) where \(H_{13}\) is given by (D.4) and \(H_{24}=1-H_{21}\). Furthermore, \(H_3=1- H_{25}= J_{12}\), where \(J_{12}\) is given by (A.9) of Appendix A. Thus, \(P_2^{AN,IDL} \triangleq \) = \((H_{11}-H_{12})H_{13}+[(H_{21}-H_{22})+(H_{23}\times H_{24})]H_{25}+H_3\). Thus \(P_1^{AN,IDL}\) given by (23a) can be obtained. Notice that (23a) is valid if and only if \(0<\alpha _1<\frac{1}{1+\mu _2}\) and \(0<\alpha _1<\frac{1}{1+\gamma _2}\), i.e., \(0<\alpha _1<\text {min}\bigl (\frac{1}{1+\mu _2},\frac{1}{1+\gamma _2}\bigr )\). If \(\alpha _1>\frac{1}{1+\mu _2}\), \(H_{11}\rightarrow 1\); on the other hand, if \(\alpha _1>\frac{1}{1+\gamma _2}\), \(H_{12}\rightarrow 1\), \(H_{25}\rightarrow 0\) and \(H_{3}\rightarrow 1\). So that \(P_2^{AN,IDL}\rightarrow 1\).
Derivation of (24a)
Substituting (17b) in (22c) and rearranging, we get (E.1).
Now, utilizing the expressions for \(\Gamma _{1,x_2}^{nAN}\), \(\Gamma _{2,x_2}^{nAN}\) and \(\Gamma _{e,x_2}^{nAN}\) and rearranging, \(H_4\) becomes:
where \(k_1= 2^{R_{s,2}}\alpha _2\rho _b\). Notice that \(H_{41}\) is similar to the terms \(J_{31}\) given by (B.2). On similar lines, \(H_{41}\) can be approximated as:
where \(d_n = \frac{\vartheta _2}{2k_1}( 1+S_n)\). Further \(H_{42} = J_{12}\) given by (A.9) of Appendix A. Similarly, \(H_{43}\) can be determined similar to \(H_{13}\) as:
Substituting for \(\Gamma _{1,x_2}^{nAN}\), \(\Gamma _{2,x_2}^{nAN}\) and \(\Gamma _{e,x_2}^{nAN}\) in (E.1), \(H_5\) can be simplified as in (E.5).
Notice that \(H_{51}= 1- e^{\frac{-(\gamma _2-\mu _2)}{k_1\lambda _{be}}}\) and \(H_{52}\) is similar to \(H_{22}\) given in (D.5) of Appendix D. Thus, \(H_{52}\) can be written as:
where \(R= \frac{\rho _1V}{\rho _bW+1}\) and \(p_6= \rho _1\lambda _{12}\). By adopting a similar approach, the following expression can be obtained for \(H_{52}\) as in (E.7),
where \(g_4{=}\frac{k_1+p_6}{k_1p_6}\); \(g_5{=} \frac{p_6+p_6p_5}{p_5}\) and \(g_6= \frac{p_6}{p_5}\). Further, we can observe that \(H_{53}= 1-H_{43}\) where \(H_{43}\) is given by (E.4) and \(H_{54}=1-H_{51}\). Furthermore, \(H_6=1- H_{55}= J_{12}\), where \(J_{12}\) is given by (A.9) of Appendix A. Thus, \(P_2^{nAN,IDL} \triangleq \) \((H_{41}-H_{42})H_{43}+[(H_{51}-H_{52})+(H_{53}\times H_{54})]H_{55}+H_6\). Accordingly, \(P_2^{nAN,IDL}\) given by (24a) can be obtained. Notice that (24a) is valid if and only if \(0{<}\alpha _1{<}\frac{1}{1+\mu _2}\) and \(0{<}\alpha _1{<}\frac{1}{1+\gamma _2}\), i.e., \(0{<}\alpha _1{<}\text {min}\bigl (\frac{1}{1+\mu _2},\frac{1}{1+\gamma _2}\bigr )\). If \(\alpha _1{>}\frac{1}{1+\mu _2}\), \(H_{41}\rightarrow 1\); on the other hand, if \(\alpha _1{>}\frac{1}{1+\gamma _2}\), \(H_{42}\rightarrow 1\),\(H_{55}\rightarrow 0\) and \(H_{6}\rightarrow 1\). So that \(P_2^{nAN,IDL}\rightarrow 1\).
Derivation of (25a) and (25b)
1.1 Derivation of (25a)
From Appendix D, \(P_2^{AN,IDL} \triangleq \) \((H_{11}-H_{12})H_{13}+[(H_{21}-H_{22})+(H_{23}\times H_{24})]H_{25}+H_3\). Now \(P_{2,asy}^{AN,IDL}=\underset{\rho \rightarrow \infty }{\text {lim}}\bigl [(H_{11}-H_{12})H_{13}+[(H_{21}-H_{22})+(H_{23}\times H_{24})]H_{25}+H_3\bigr ] \). By setting \(\rho _b=\rho _1=\rho \rightarrow \infty \) and let \(\underset{\rho \rightarrow \infty }{\text {lim}}e^{\frac{-x}{\rho }}\simeq 1\) in (D.2), the asymptotic expression for \(H_{11}\) is determined as:
By applying partial fraction decomposition method and on solving the resulting integrals, we get(F.2),
where \(\phi _3= \frac{2^{R_{s,2}}\alpha _2\lambda _{be}}{\theta _2\lambda _{1e}}\); \(\phi _4 = \frac{\mu _{2}\lambda _{b2}+\lambda _{12}\theta _1}{\lambda _{b2}}\) and \(\phi _5= \frac{\lambda _{11}\mu _2+\lambda _{b1}(\alpha _2-\alpha _1\mu _2)}{\lambda _{11}-\lambda _{b1}\alpha _1}\). The asymptotic expression for \(H_{12}\) can be obtained from (A.9) in Appendix A, by setting \(\rho _b=\rho _1=\rho \rightarrow \infty \) and \(\underset{\rho \rightarrow \infty }{\text {lim}}e^{\frac{-x}{\rho }}\simeq 1\) and is given by \( \underset{\rho \rightarrow \infty }{H_{12}}\simeq 1-\Bigl [\frac{\lambda _{b1}(\alpha _2-\alpha _1\gamma _{2})}{\lambda _{b1}(\alpha _2-\alpha _1\gamma _{2})+\lambda _{11}\gamma _{2}}\Bigr ]\). From (D.4), the asymptotic expression for \(H_{13}\) can be determined as: \(\underset{\rho \rightarrow \infty }{H_{13}}\simeq \frac{\theta _1\lambda _{12}}{\lambda _{b2}\gamma _2+\theta _1\lambda _{12}}\). From (D.6), the asymptotic expression for \(H_{21}\) can be obtained as:
The asymptotic expression for \(H_{22}\) can be determined by setting \(\rho \rightarrow \infty \) and \(e^{\frac{-x}{\rho }}\simeq 1\) in (D.9) and by applying partial fraction decomposition method and after solving the resulting integral expressions, we get:
where \(\phi _6=\frac{\theta _1\lambda _{12}}{\lambda _{b2}}\) and \(\phi _7= \frac{2^{R_{s,2}}\alpha _2\lambda _{be}}{\theta _1}-\mu _2\). Also, \(\underset{\rho \rightarrow \infty }{H_{23}}= 1-\underset{\rho \rightarrow \infty }{H_{13}} \) and \(\underset{\rho \rightarrow \infty }{H_{24}}= 1-\underset{\rho \rightarrow \infty }{H_{21}}\). Further, \(\underset{\rho \rightarrow \infty }{H_{3}}= 1-\underset{\rho \rightarrow \infty }{H_{25}}=\underset{\rho \rightarrow \infty }{H_{12}} \). Combining these expressions, \(P_{2,asy}^{AN,IDL}\) can be determined as in (25a).
1.2 Derivation of (25b)
In Appendix E, it was shown that \(P_2^{nAN,IDL}\) \(\triangleq \) \((H_{41}-H_{42})H_{43}\)+ \([(H_{51}-H_{52})+(H_{53}\times H_{54})]H_{55}\) + \(H_6\). Now, \(P_{2,asy}^{nAN,IDL}=\underset{\rho \rightarrow \infty }{\text {lim}} P_{2,asy}^{nAN,IDL}\), which is determined by finding the asymptotic expressions for various terms given above. Firstly, \(\underset{\rho \rightarrow \infty }{H_{41}}\) is determined by setting \(\rho _b=\rho _1=\rho \rightarrow \infty \), \( \underset{\rho \rightarrow \infty }{\text {lim}}e^{\frac{-x}{\rho }}{\simeq } 1\) in (E.3) and it can be seen that \(\underset{\rho \rightarrow \infty }{H_{41}}\cong 1\). Now, \(\underset{\rho \rightarrow \infty }{H_{42}}{=} \underset{\rho \rightarrow \infty }{H_{12}}\). Further, asymptotic expression for \(H_{43}\) is obtained from (E.4) as \(\underset{\rho \rightarrow \infty }{H_{43}} {=} \frac{\lambda _{12}}{\lambda _{b2}\gamma _2+\lambda _{12}}\). The asymptotic expression for \(H_{51}\) and \(H_{52}\), \(\underset{\rho \rightarrow \infty }{H_{51}}{=}\underset{\rho \rightarrow \infty }{H_{52}}{=}0\). Furthermore, it can be seen that, \(\underset{\rho \rightarrow \infty }{H_{53}}{=} 1-\underset{\rho \rightarrow \infty }{H_{43}}\) and \(\underset{\rho \rightarrow \infty }{H_{54}}{=}1-\underset{\rho \rightarrow \infty }{H_{51}}\). Moreover, \(\underset{\rho \rightarrow \infty }{H_{6}}{=} 1-\underset{\rho \rightarrow \infty }{H_{55}} {=}\underset{\rho \rightarrow \infty }{H_{12}}\). Combining these expressions, \(P_{2,asy}^{nAN,IDL}\) can be obtained as in (25b).
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Nimi, T., Babu, A.V. Power allocation for enhancing the physical layer secrecy performance of artificial noise-aided full-duplex cooperative NOMA system. Telecommun Syst 85, 41–66 (2024). https://doi.org/10.1007/s11235-023-01067-5
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-023-01067-5