Abstract
This paper addresses the problem of computing end-to-end delay bounds for a traffic flow traversing a tandem of FIFO multiplexing network nodes using Network Calculus. Numerical solution methods are required, as closed-form delay bound expressions are unknown except for few specific cases. For the methodology called the Least Upper Delay Bound, the most accurate among those based on Network Calculus, exact and approximate solution algorithms are presented, and their accuracy and computation cost are discussed. The algorithms are inherently exponential, yet affordable for tandems of up to few tens of nodes, and amenable to online execution in cases of practical significance. This complexity is, however, required to compute accurate bounds. As the LUDB may actually be larger than the worst-case delay, we assess how close the former is to the latter by computing lower bounds on the worst-case delay and measuring the gap between the lower and upper bound.




























Similar content being viewed by others
Notes
Roughly speaking, a service-curve expresses the lower bound on the service that a backlogged node may get over time.
Such closed-form expressions can be generalized to all tandems whose nesting trees are tree-equivalent, i.e. have the same shape, as discussed in Lenzini et al. (2008). For instance, the solution for any fully nested tandem can be computed in a closed form, starting from the one computed for the tree-equivalent sink-tree tandem, via simple variable substitution.
All the graphs report the average of ten randomly generated replicas.
References
Agrawal R, Cruz RL, Okino C, Rajan R (1999) Performance bounds for flow control protocols. IEEE/ACM Trans Netw 7(3):310–323
Bauer H, Scharbarg J-L, Fraboul C (2010) Improving the worst-case delay analysis of an AFDX network using an optimized trajectory approach. IEEE Trans Ind Inform 6(4):521–533
Bisti L, Lenzini L, Mingozzi E, Stea G (2010) DEBORAH: a tool for worst-case analysis of FIFO tandems. In: ISoLA 2010, Crete, Oct 18–20, 2010
Bisti L, Lenzini L, Mingozzi E, Stea G (2008) Estimating the worst-case delay in FIFO tandems using network calculus. In: Proc of VALUETOOLS 2008, Athens, Greece, 21–23 October, 2008
Blake S, Black D, Carlson M, Davies E, Wang Z, Weiss W (1998) An architecture for differentiated services. IETF RFC 2475
Bouillard A, Thierry E (2008) An algorithmic toolbox for Network Calculus. J Discrete Event Dyn Syst 18(1):3–49
Bouillard A, Jouhet L, Thierry E (2010) Tight performance bounds in the worst-case analysis of feed-forward networks. In: Proc of INFOCOM 2010, S. Diego, CA, 14–19 March, 2010
Boyer M, Navet N, Olive X, Thierry E (2010) The Pegase project: precise and scalable analysis for aerospace communication systems with Network Calculus. In: Proc of ISoLA 2010, Crete, October 18–20, 2010
Braden R, Clark D, Shenker S (1994) Integrated services in the Internet architecture: an overview. IETF RFC 1633
Chakraborty S, Künzli S, Thiele L, Herkersdorf A, Sagmeister P (2003) Performance evaluation of network processor architectures: combining simulation with analytical estimation. Comput Netw 42(5):641–665
Chang CS (2000) Performance guarantees in communication networks. Springer, New York
Cruz RL (1991) A calculus for network delay. IEEE Trans Inf Theory 37(1):114–141
Fourer R (2010) A simplex algorithm for piecewise-linear programming I: derivation and proof. Math Program 33(2):204–233. doi:10.1007/BF01582246
Kiefer A, Gollan N, Schmitt JB (2010) Searching for tight performance bounds in feed-forward networks. In: Proc of MMB/DFT, pp 227–241
Koubaa A, Alves M, Tovar E (2006) Modeling and worst-case dimensioning of cluster-tree wireless sensor networks. In: Proc of IEEE RTSS’06, pp 412–421
Le Boudec J-Y, Thiran P (2001) Network Calculus. LNCS, vol 2050. Springer, Berlin
Lenzini L, Martorini L, Mingozzi E, Stea G (2006) Tight end-to-end per-flow delay bounds in FIFO multiplexing sink-tree networks. Perform Eval 63:956–987
Lenzini L, Mingozzi E, Stea G (2008) A methodology for computing end-to-end delay bounds in FIFO-multiplexing tandems. Perform Eval 65:922–943
Lenzini L, Mingozzi E, Stea G (2005) Delay bounds for FIFO aggregates: a case study. Comput Commun 28(3):287–299
Martin S, Minet P (2006) Schedulability analysis of flows scheduled with FIFO: application to the expedited forwarding class. In: Proc of IPDPS 2006, Rhodes Island, 25–29 April, 2006
Martin S, Minet P, George L (2004) Deterministic end-to-end guarantees for real-time applications in a DiffServ-MPLS domain. In: Proc of SERA 2003. LNCS, vol 3026. Springer, Berlin, pp 51–73
Schmitt JB, Roedig U (2005) Sensor Network Calculus—a framework for worst case analysis. In: DCOSS’05, pp 141–154, June 2005
Schmitt JB, Zdarsky FA, Fidler M (2008) Delay bounds under arbitrary multiplexing: when Network Calculus leaves you in the lurch. In: Proc of INFOCOM 2008, pp 1669–1677
Skeie T, Johannessen S, Holmeide O (2006) Timeliness of real-time IP communication in switched industrial Ethernet networks. IEEE Trans Ind Inform 2:25–39
Urvoy-Keller G, Hèbuterne G, Dallery Y (2002) Traffic engineering in a multipoint-to-point network. IEEE J Sel Areas Commun 20(4):834–849
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: Table of symbols
Hereafter we report the symbols most frequently used in the paper, along with a short explanation of their meaning.
Symbol | Description |
|---|---|
A(t) | Cumulative arrival function (CAF) |
D(t) | Cumulative departure function (CDF) |
β(t) | Generic service curve |
δ φ (t) | Delay-element service curve |
β θ,R (t) | Rate-latency service curve |
α(t) | Generic arrival curve |
γ σ,ρ (t) | Affine (leaky-bucket) arrival curve |
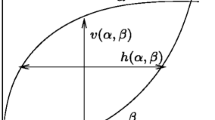
h(α,β) | Maximum horizontal deviation between arrival curve α(t) and service curve β(t) |
β eq(t,τ) | Equivalent service curve |
E(β,α,τ)(t) | Equivalent service curve, obtained by subtracting from service curve β(t) arrival curve α(t−τ) |
π(t) | Pseudoaffine (PA) curve |
D | Offset of a PA curve |
\(\rho_{\pi}^{*}\) | Long-term rate of a PA curve |
\(\overline{E}( \pi,\alpha,s )\) | Expression of an equivalent service curve according to Corollary 2.1 |
N | Number of nodes in the tandem |
R k | Rate of node k |
θ k | Latency of node k |
M | Number of flows in the tandem |
(i,j) | A flow traversing nodes from i to j included |
l(i,j) | Level of nesting of flow (i,j) |
H(i,j) | Height of t-node (i,j), i.e. the length of the longest path from (i,j) to a leaf t-node |
σ (i,j) | Burst size of flow (i,j) |
ρ (i,j) | Sustainable rate of flow (i,j) |
V | The least upper delay bound (LUDB) |
Ω | Number of Recursive Simplex Decompositions (RSDs) |
U | Utilization factor |
Appendix 2: Proof of Property 6.1
Property 6.1: Consider a tandem of N nodes, traversed by the tagged flow (1,N) and by cross-flows (i,i),1≤i<N. All flows have the same leaky-bucket arrival curve. All nodes have the same rate-latency service curve, with R=2ρ/U, U ranging from 20 % to 100 %. In the above settings, a lower bound for the worst-case delay of the tagged flow is:
Proof
We set up a scenario according to the three hypotheses listed at the beginning of this section. At node 1, the tagged flow (1,N) sends its burst at time t=0 (by hypothesis b). The cross flow flows (1,1) is forced to do the same, otherwise its traffic does not impact the tagged flow (hypothesis c). Assume that the burst of flow (1,1) gets to the front of the queue, and that the one from (1,N) gets at the back. Call the tagged bit the σth of the tagged flow. Call a i,b i the times at which the first and last bit of the tagged flow arrive at node i, and t i the time at which the tagged bit exits node i. It is a 1=b 1=0,b j=t j−1,2≤j≤N, and v=t n. The scenario is reported in Fig. 29, for the first two nodes. As nodes are lazy by hypothesis (a), the CDF at node 1 has a slope equal to R, hence t 1=θ+2σ/R. Flow (1,1) leaves after node 1, thus leaving a gap equal to σ/R in the CAF at node 2, hence a 2=θ+σ/R. Assume all cross flows (j,j),2≤j≤N, are greedy. They send their burst σ at time a j, and keep sending traffic at a rate ρ afterwards, until time b j. Then it is easy to prove (by induction) that node j accumulates backlog in [a j,b j], as the slope of the CAF A j(t) is always larger than R. Therefore, node j clears its backlog at a rate R. The backlog to be cleared is equal to σ+[σ+ρ⋅(b j−a j)], where the first addendum is due to the tagged flow and the second one is due to the cross flow. We thus obtain the following:

By instantiating (33) for j=N, and considering that R=2ρ/U, the thesis follows after a few straightforward algebraic manipulations.
□
Appendix 3: Proof of Property 6.2
Property 6.2: Consider an N-node source-tree tandem, where all flows have the same leaky-bucket arrival curve, with σ (1,i)=σ and ρ (1,i)=ρ, and nodes have a rate-latency service curve, with θ i=θ and R i=(N+1−i)⋅ρ/U, U ranging from 20 % to 100 %. In the above settings, it is
Proof
Assume the tagged flow (1,N) sends its burst at time t=0. Since all flows enter at node 1, cross flows (1,i),1≤i≤N−1 must send their burst at t=0 as well, otherwise they do not affect the tagged flow at all. Assume that the bursts are stored in sequence in node 1’s queue, ordered by increasing i, so that the front-most space in the queue is taken by the burst of flow (1,1). The scenario is reported in Fig. 30 for the first three nodes, assuming identically null latencies for ease of reading. The last bit in node 1’s queue at time t=0 is the tagged bit, i.e. the one whose delay we want to measure. Since nodes are lazy, the tagged bit leaves node 1 at:
At node 2, it is a 2=θ+σ/R 1 since flow (1,1) has left the tandem. The tagged bit arrives at b 2=t 1, where it is the (N−1)⋅σ-th of a CAF A 2(t) having a slope equal to R 1=N⋅ρ/U. Since R 2=(N−1)⋅ρ/U<R 1, at node 2 traffic arrives faster than it is transmitted, hence node 2 accumulates an increasing backlog until time b 2. Thus, at node 2 the tagged bit leaves at:
and the CDF D 2(t) will have a slope equal to R 2. By repeating the same argument, it is easy to conclude that, at node j,2≤j≤N, it is:
Hence, by considering that v=t N and substituting R i=(N+1−i)⋅ρ/U, we obtain:
which is the thesis.
□
Rights and permissions
About this article
Cite this article
Bisti, L., Lenzini, L., Mingozzi, E. et al. Numerical analysis of worst-case end-to-end delay bounds in FIFO tandem networks. Real-Time Syst 48, 527–569 (2012). https://doi.org/10.1007/s11241-012-9153-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11241-012-9153-1