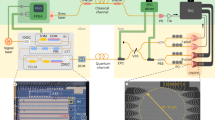
Abstract
Quantum key distribution (QKD) enables provably secure communication between two parties over an optical fiber that arguably withstands any form of attack. Besides the need for a suitable physical signalling scheme and the corresponding devices, QKD also requires a secret key distillation protocol. This protocol and the involved signal processing handle the reliable key agreement process over the fragile quantum channel, as well as the necessary post-processing of key bits to avoid leakage of secret key information to an eavesdropper. In this paper we present in detail an implementation of a key distillation engine for a QKD system based on the coherent one-way (COW) protocol. The processing of key bits by the key distillation engine includes agreement on quantum bit detections (sifting), information reconciliation with forward error correction coding, parameter estimation, and privacy amplification over an authenticated channel. We detail the system architecture combining all these processing steps, and discuss the design trade-offs for each individual system module. We also assess the performance and efficiency of our key distillation implementation in terms of throughput, error correction capabilities, and resource utilization. On a single-FPGA (Xilinx Virtex-6 LX240T) platform, the system supports distilled key rates of up to 4 Mbps.










Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Notes
Note that only a small fraction of the pulses can be detected, strongly depending on the optical fiber length between Alice and Bob. However, these missed detections do not result in bit errors, since these bits are omitted by Alice during the sifting process.
References
IEEE Standard for Information technology– Local and metropolitan area networks– Specific requirements– Part 11: Wireless LAN Medium Access Control (MAC)and Physical Layer (PHY) Specifications Amendment 5: Enhancements for Higher Throughput. IEEE Std 802.11n-2009 (Amendment to IEEE Std 802.11-2007 as amended by IEEE Std 802.11k-2008, IEEE Std 802.11r-2008, IEEE Std 802.11y-2008, and IEEE Std 802.11w-2009) pp. 1–565 (2009).
Bennett, C., Bessette, F., Brassard, G., Salvail, L., & Smolin, J. (1992). Experimental quantum cryptography. Journal of Cryptology, 5, 3–28.
Bennett, C.H., & Brassard, G. (1984). Quantum cryptography: public key distribution and coin tossing. In Proceedings of the IEEE international conference on computers, systems and signal processing (pp. 175–179). New York: IEEE Press.
Canetti, R. (2001). Universally composable security: a new paradigm for cryptographic protocols. In 42nd annual symposium on foundations of computer science, FOCS (pp. 136–145).
Carter, J., & Wegman, M.N. (1979). Universal classes of hash functions. Journal of Computer and System Sciences, 18(2), 143–154.
Cui, K., Wang, J., Zhang, H.F., Luo, C.L., Jin, G., & Chen, T.Y. (2013). A real-time design based on FPGA for expeditious error reconciliation in QKD system. IEEE Transactions on Information Forensics and Security, 8(1), 184–190.
Gisin, N., Ribordy, G., Tittel, W., & Zbinden, H. (2002). Quantum cryptography. Reviews of Modern Physics, 74, 145–195.
ID Quantique: Quantis Random Number Generator (2014). http://idquantique.com/random-number-generators/products.
Jouguet, P., & Kunz-Jacques, S. (2014). High performance error correction for quantum key distribution using polar codes. Journal of Quantum Information and Computation, 14(3–4), 329–338.
Korzh, B., Walenta, N., Lunghi, T., Gisin, N., & Zbinden, H. (2014). Free-running InGaAs single photon detector with 1 dark count per second at 10 % efficiency. Applied Physics Letters, 104(8).
Krawczyk, H. (1994). LFSR-based hashing and authentication. In Y. Desmedt (Ed.), Advances in Cryptology - CRYPTO 94, Lecture Notes in Computer Science, (Vol. 839 pp. 129–139). Berlin Heidelberg: Springer.
Lin, S., & Costello, D. (2004). Error control coding: fundamentals and applications. Pearson-Prentice Hall.
Liveris, A., Xiong, Z., & Georghiades, C. (2002). Compression of binary sources with side information at the decoder using LDPC codes. IEEE Communications Letters, 6(10), 440–442.
Lorunser, T., Querasser, E., Matyus, T., Peev, M., Wolkerstorfer, J., Hutter, M., Szekely, A., Wimberger, I., Pfaffel-Janser, C., & Neppach, A. (2008). Security processor with quantum key distribution. In International conference on application-specific systems, architectures and processors (ASAP) (pp. 37–42).
Muehlberghuber, M., Keller, C., Gürkaynak, F., & Felber, N. (2013). FPGA-based high-speed authenticated encryption system. In VLSI-SoC: from algorithms to circuits and system-on-chip design, IFIP Advances in Information and Communication Technology, (Vol. 418 pp. 1–20). Berlin Heidelberg: Springer.
Pearson, D. (2004). High-speed QKD reconciliation using forward error correction, (pp. 299–302).
Portmann, C. (2014). Key recycling in authentication. IEEE Transactions on Information Theory, 60(7), 4383–4396.
Renner, R., & König, R. (2005). Universally composable privacy amplification against quantum adversaries. In J. Kilian (Ed.), Theory of cryptography, Lecture notes in computer science, (Vol. 3378 pp. 407–425). Berlin Heidelberg: Springer.
Sharon, E., Litsyn, S., & Goldberger, J. (2004). An efficient message-passing schedule for LDPC decoding. In Proceedings of the 23rd IEEE convention of electrical and electronics engineers in Israel. IEEE (pp. 223–226).
Stucki, D., Brunner, N., Gisin, N., Scarani, V., & Zbinden, H. (2005). Fast and simple one-way quantum key distribution. Applied Physics Letters, 87(19), 194, 108.
Studer, C., Preyss, N., Roth, C., & Burg, A. (2008). Configurable high-throughput decoder architecture for quasi-cyclic LDPC codes. In 42nd Asilomar conference on signals, systems and computers. IEEE (pp. 1137–1142).
Takesue, H., Honjo, T., Tamaki, K., & Tokura, Y. (2009). Differential phase shift-quantum key distribution. IEEE Communications Magazine, 47(5), 102–106.
Tanaka, A., Fujiwara, M., Yoshino, K., Takahashi, S., Nambu, Y., Tomita, A., Miki, S., Yamashita, T., Wang, Z., Sasaki, M., & Tajima, A. (2012). High-speed quantum key distribution system for 1-Mbps real-time key generation. IEEE Journal of Quantum Electronics, 48(4), 542–550.
Tomamichel, M., Lim, C.C.W., Gisin, N., & Renner, R. (2012). Tight finite-key analysis for quantum cryptography. Nature Communications, 3, 634.
Walenta, N., Burg, A., Caselunghe, D., Constantin, J., Gisin, N., Guinnard, O., Houlmann, R., Junod, P., Korzh, B., Kulesza, N., Legr, M., Lim, C.W., Lunghi, T., Monat, L., Portmann, C., Soucarros, M., Thew, R.T., Trinkler, P., Trolliet, G., Vannel, F., & Zbinden, H. (2014). A fast and versatile quantum key distribution system with hardware key distillation and wavelength multiplexing. New Journal of Physics, 16(1), 013, 047.
Wegman, M.N., & Carter, J. (1981). New hash functions and their use in authentication and set equality. Journal of Computer and System Sciences, 22(3), 265–279.
Zhang, H.F., Wang, J., Cui, K., Luo, C.L., Lin, S.Z., Zhou, L., Liang, H., Chen, T.Y., Chen, K., & Pan, J.W. (2012). A real-time QKD system based on FPGA. Journal of Lightwave Technology, 30 (20), 3226–3234.
Acknowledgments
The authors greatfully acknowledge Julien-Kenji Izui, Xavier-Christian Paillard, Gregory Trolliet, Fabien Vannel from HEPIA Geneva and Olivier Guinnard from the University of Geneva for their contributions to some key system components that are beyond the scope of this paper. We also acknowledge the financial support of the Swiss Nano-Tera program for the QCRYPT project.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Constantin, J., Houlmann, R., Preyss, N. et al. An FPGA-Based 4 Mbps Secret Key Distillation Engine for Quantum Key Distribution Systems. J Sign Process Syst 86, 1–15 (2017). https://doi.org/10.1007/s11265-015-1086-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11265-015-1086-1