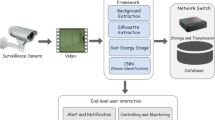
Abstract
In today's digital realm, global safety concerns have given rise to intelligent surveillance technologies. Currently, Gait-based surveillance systems have lately got increasing attention and are widely used because they employed human distinctive and behavioral characteristics as well as recognize them without their cooperation. They play a vital role in smart video monitoring systems and have a broad array of applications, especially in public security applications. Gait recognition is the process of validating a person looking at the way they walk. Behind these surveillance systems, superior computer vision-based deep learning algorithms are deployed for the effective identification of individuals. On the other hand, the vulnerable nature of these algorithms is the main factor for potential security threats in these surveillance systems. Different researchers design several kinds of adversarial attacks for different computer vision domains to exploit their vulnerabilities. In most of these attacks, the resulting adversarial noise in form of either patches or pixels is apparent and clearly identifiable by the human naked eye. From this line of research, this study presents a new variant of the attack, to highlight the vulnerability of gait recognition systems. The adversarial noise in the form of one pixel is added to that location of Gait energy images (GEI) which are less imperceptible by humans. More specifically, this can be accomplished using the Grey wolf optimization (GWO) method, which takes a GEI image and a calculated perturbation as input and starts working to find the optimum location on a given GEI image. This optimum candidate/location is the one where the texture is not excessively affected when it is disrupted by computed perturbation, and as a result, the attack is less perceptible. Moreover, the study investigates that CNN’s based gait recognition systems encountered severe potential threats even when the noise is less imperceptible by the human naked eye.













Similar content being viewed by others
Data Availability
Dataset can be requested through the corresponding author.
Code Availability
The code access can be requested through the corresponding author.
References
Krizhevsky, A., Sutskever, I., & Hinton, G. E. (2017). Imagenet classification with deep convolutional neural networks. Communications of the ACM, 60(6), 84–90.
Maqsood, M., Yasmin, S., Mehmood, I., Bukhari, M., & Kim, M. (2021). An Efficient DA-Net Architecture for Lung Nodule Segmentation. Mathematics, 9(13), 1457.
Maqsood, M., Bukhari, M., Ali, Z., Gillani, S., Mehmood, I., Rho, S., & Jung, Y. (2021). A Residual-Learning-Based Multi-Scale Parallel-Convolutions-Assisted Efficient CAD System for Liver Tumor Detection. Mathematics, 9(10), 1133.
Galvez, R. L., Bandala, A. A., Dadios, E. P., Vicerra, R. R. P., & Maningo, J. M. Z. (2018). Object detection using convolutional neural networks. In: TENCON 2018–2018 IEEE Region 10 Conference, IEEE, (pp. 2023–2027).
He, Z., Cao, Y., Du, L., Xu, B., Yang, J., Cao, Y., Tang, S., & Zhuang, Y. (2019). Mrfn: Multi-receptive-field network for fast and accurate single image super-resolution. IEEE Transactions on Multimedia, 22(4), 1042–1054.
Liu, F., Shen, C., & Lin, G. (2015). Deep convolutional neural fields for depth estimation from a single image. In: Proceedings of the IEEE conference on computer vision and pattern recognition, (pp. 5162–5170).
Ilyas, W., Noor, M., & Bukhari, M. (2021). An Efficient Emotion Recognition Frameworks for Affective Computing. The Journal of Contents Computing, 3(1), 251–267.
Mehmood, A., Maqsood, M., Bashir, M., & Shuyuan, Y. (2020). A deep siamese convolution neural network for multi-class classification of alzheimer disease. Brain Sciences, 10(2), 84.
Ali, Z., Irtaza, A., & Maqsood, M. (2021). An efficient U-Net framework for lung nodule detection using densely connected dilated convolutions. The Journal of Supercomputing, 1–22
Ashraf, R., Afzal, S., Rehman, A. U., Gul, S., Baber, J., Bakhtyar, M., Mehmood, I., Song, O.-Y., & Maqsood, M. (2020). Region-of-Interest based transfer learning assisted framework for skin cancer detection. IEEE Access, 8, 147858–147871.
Uliyan, D. M., Sadeghi, S., & Jalab, H. A. (2020). Anti-spoofing method for fingerprint recognition using patch based deep learning machine. Engineering Science and Technology, an International Journal, 23(2), 264–273.
Collobert. R., & Weston. J. (2008). A unified architecture for natural language processing: Deep neural networks with multitask learning. In: Proceedings of the 25th international conference on Machine learning, (pp. 160–167).
Neves, J., Narducci, F., Barra, S., & Proença, H. (2016). Biometric recognition in surveillance scenarios: A survey. Artificial Intelligence Review, 46(4), 515–541.
Yang, S. X., Larsen, P. K., Alkjær, T., Simonsen, E. B., & Lynnerup, N. (2014). Variability and similarity of gait as evaluated by joint angles: Implications for forensic gait analysis. Journal of Forensic Sciences, 59(2), 494–504.
BenAbdelkader, C., Cutler, R., & Davis, L. (2002). Stride and cadence as a biometric in automatic person identification and verification. In: Proceedings of Fifth IEEE international conference on automatic face gesture recognition, IEEE, (pp. 372–377).
Alotaibi, M., & Mahmood, A. (2017). Improved gait recognition based on specialized deep convolutional neural network. Computer Vision and Image Understanding, 164, 103–110.
Hawas, A. R., El-Khobby, H. A., Abd-Elnaby, M., & Abd El-Samie, F. E. (2019). Gait identification by convolutional neural networks and optical flow. Multimedia Tools and Applications, 78(18), 25873–25888.
Linda, G. M., Themozhi, G., & Bandi, S. R. (2020). Color-mapped contour gait image for cross-view gait recognition using deep convolutional neural network. International Journal of Wavelets, Multiresolution and Information Processing, 18(01), 1941012.
Han, J., & Bhanu, B. (2005). Individual recognition using gait energy image. IEEE Transactions on Pattern Analysis and Machine Intelligence, 28(2), 316–322.
Bashir, K., Xiang, T., & Gong, S. (2010). Gait recognition without subject cooperation. Pattern Recognition Letters, 31(13), 2052–2060.
Lam, T. H., & Lee, R. S. A. (2006). new representation for human gait recognition: Motion silhouettes image (MSI). International conference on biometrics (pp. 612–618). Springer.
Bashir, K., Xiang, T., & Gong, S. (2010). Cross view gait recognition using correlation strength. In: Bmvc, (pp. 1–11).
Liu, N., Lu, J., Tan, Y-P., & Chen, Z. (2009). Enhanced gait recognition based on weighted dynamic feature. In: 2009 16th IEEE International Conference on Image Processing (ICIP), IEEE, (pp. 3581–3584).
Gupta, S. K., Sultaniya, G. M., & Chattopadhyay, P. (2020). An efficient descriptor for gait recognition using spatio-temporal cues. In: Emerging Technology in Modelling and Graphics, (pp. 85–97). Springer.
Arora, P., Hanmandlu, M., & Srivastava, S. (2015). Gait based authentication using gait information image features. Pattern Recognition Letters, 68, 336–342.
Yang, X., Zhou, Y., Zhang, T., Shu, G., & Yang, J. (2008). Gait recognition based on dynamic region analysis. Signal Processing, 88(9), 2350–2356.
Arshad, H., Khan, M. A., Sharif, M. I, Yasmin, M., Tavares, J. M. R., Zhang, Y. D., & Satapathy. S. C. (2020). A multilevel paradigm for deep convolutional neural network features selection with an application to human gait recognition. Expert Systems, e12541
Wu, X., Yang, T., & Xia, Z. (2020). Gait recognition based on densenet transfer learning. International Journal of Environmental Science, 9(1), 1–14.
Goodfellow, I. J., Shlens, J., & Szegedy, C. (2014). Explaining and harnessing adversarial examples. https://arxiv.org/abs/14126572
Szegedy, C., Zaremba, W., Sutskever, I., Bruna, J., Erhan, D., Goodfellow, I., & Fergus, R. (2013). Intriguing properties of neural networks. https://arxiv.org/abs/13126199
Zhu Z-A., Lu. Y-Z., & Chiang, C-K. (2019). Generating adversarial examples by makeup attacks on face recognition. In: 2019 IEEE International Conference on Image Processing (ICIP), IEEE, (pp. 2516–2520).
Goswami, G., Ratha, N., Agarwal, A., Singh, R., & Vatsa, M. (2018). Unravelling robustness of deep learning based face recognition against adversarial attacks. In: Proceedings of the AAAI Conference on Artificial Intelligence, 1.
Dahl, G. E., Stokes, J. W., Deng, L., & Yu, D. (2013). Large-scale malware classification using random projections and neural networks. In: 2013 IEEE International Conference on Acoustics, Speech and Signal Processing, IEEE, (pp. 3422–3426).
Brown, T. B., Mané, D., Roy, A., Abadi, M., & Gilmer, J. (2017). Adversarial patch. https://arxiv.org/abs/171209665
Su, J., Vargas, D. V., & Sakurai, K. (2019). One pixel attack for fooling deep neural networks. IEEE Transactions on Evolutionary Computation, 23(5), 828–841.
Mirjalili, S., Mirjalili, S. M., & Lewis, A. (2014). Grey wolf optimizer. Advances in Engineering Software, 69, 46–61.
Wan, C., Wang, L., & Phoha, V. V. (2018). A survey on gait recognition. ACM Computing Surveys (CSUR), 51(5), 1–35.
Singh, J. P., Jain, S., Arora, S., & Singh, U. P. (2018). Vision-based gait recognition: A survey. IEEE Access, 6, 70497–70527.
He, Z., Wang, W., Dong, J., & Tan, T. (2020). Temporal sparse adversarial attack on gait recognition. https://arxiv.org/abs/2002.09674
Jia, M., Yang, H., Huang, D., & Wang, Y. (2019). Attacking gait recognition systems via silhouette guided GANs. In: Proceedings of the 27th ACM International Conference on Multimedia, (pp. 638–646).
July, M. C. Vulnerability of deep learning-based gait biometric recognition to adversarial perturbations.
Kurakin, A., Goodfellow, I., & Bengio, S. (2016). Adversarial machine learning at scale. https://arxiv.org/abs/161101236
Papernot, N., McDaniel, P., Jha, S., Fredrikson, M., Celik, Z. B., & Swami, A. (2016). The limitations of deep learning in adversarial settings. In: 2016 IEEE European symposium on security and privacy (EuroS&P), IEEE, (pp. 372–387).
Carlini, N., & Wagner, D. (2017). Towards evaluating the robustness of neural networks. In: 2017 ieee symposium on security and privacy (sp), IEEE, (pp. 39–57).
Sabour, S., Cao, Y., Faghri, F., & Fleet, D. J. (2015). Adversarial manipulation of deep representations. https://arxiv.org/abs/151105122
Liu, Y., Chen, X., Liu, C., & Song, D. (2016). Delving into transferable adversarial examples and black-box attacks. https://arxiv.org/abs/161102770
Rozsa, A., Rudd, E. M., & Boult, T. E. (2016). Adversarial diversity and hard positive generation. In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, (pp. 25–32).
Chen, P-Y., Zhang, H., Sharma, Y., Yi, J., & Hsieh, C-J. (2017). Zoo: Zeroth order optimization based black-box attacks to deep neural networks without training substitute models. In: Proceedings of the 10th ACM workshop on artificial intelligence and security, (pp. 15–26).
Moosavi-Dezfooli, S-M., Fawzi, A., & Frossard, P. (2016). Deepfool: a simple and accurate method to fool deep neural networks. In: Proceedings of the IEEE conference on computer vision and pattern recognition, (pp. 2574–2582).
Moosavi-Dezfooli, S-M., Fawzi, A., Fawzi, O., & Frossard, P. (2017). Universal adversarial perturbations. In: Proceedings of the IEEE conference on computer vision and pattern recognition, (pp. 1765–1773).
Li, Y., Zhang, H., Bermudez, C., Chen, Y., Landman, B. A., & Vorobeychik, Y. (2020). Anatomical context protects deep learning from adversarial perturbations in medical imaging. Neurocomputing, 379, 370–378.
Cheng, G., & Ji, H. (2020). Adversarial Perturbation on MRI Modalities in Brain Tumor Segmentation. IEEE Access, 8, 206009–206015.
Fawaz, H.I., Forestier, G., Weber, J., Idoumghar, L., & Muller, P.A. (2019). Adversarial attacks on deep neural networks for time series classification. In: 2019 International Joint Conference on Neural Networks (IJCNN), IEEE, (pp. 1–8).
Roth, T., Gao, Y., Abuadbba, A., Nepal, S., & Liu, W. (2021). Token-modification adversarial attacks for natural language processing: A survey. https://arxiv.org/abs/210300676
Neekhara, P., Hussain, S., Pandey, P., Dubnov, S., McAuley, J., & Koushanfar, F. (2019). Universal adversarial perturbations for speech recognition systems. https://arxiv.org/abs/190503828
Yuan, X., He, P., Zhu, Q., & Li, X. (2019). Adversarial examples: Attacks and defenses for deep learning. IEEE transactions on neural networks and learning systems, 30(9), 2805–2824.
Papernot, N., McDaniel, P., Wu, X., Jha, S., & Swami, A. (2016). Distillation as a defense to adversarial perturbations against deep neural networks. In: 2016 IEEE symposium on security and privacy (SP), IEEE, (pp. 582–597).
Huang, R., Xu, B., Schuurmans, D., & Szepesvári, C. (2015). Learning with a strong adversary. https://arxiv.org/abs/151103034
Liang, B., Li, H., Su, M., Li, X., Shi, W., & Wang, X. (2018). Detecting adversarial image examples in deep neural networks with adaptive noise reduction. IEEE Transactions on Dependable and Secure Computing.
Carlini, N., & Wagner, D. (2007). Adversarial examples are not easily detected: Bypassing ten detection methods. In: Proceedings of the 10th ACM workshop on artificial intelligence and security, (pp. 3–14).
Carlini, N., & Wagner, D. (2016). Defensive distillation is not robust to adversarial examples. https://arxiv.org/abs/160704311
Wu, Z., Li, G., Shen, S., Lian, X., Chen, E., & Xu, G. (2021). Constructing dummy query sequences to protect location privacy and query privacy in location-based services. World Wide Web, 24(1), 25–49.
Wang, T., Bhuiyan, M. Z. A., Wang, G., Qi, L., Wu, J., & Hayajneh, T. (2019). Preserving balance between privacy and data integrity in edge-assisted Internet of Things. IEEE Internet of Things Journal, 7(4), 2679–2689.
Yu, S., Tan, D., & Tan, T. (2006). A framework for evaluating the effect of view angle, clothing and carrying condition on gait recognition. In: 18th International Conference on Pattern Recognition (ICPR'06). IEEE, (pp. 441–444).
Bukhari, M., Bajwa, K. B., Gillani, S., Maqsood, M., Durrani, M. Y., Mehmood, I., Ugail, H., & Rho, S. (2020). An efficient gait recognition method for known and unknown covariate conditions. IEEE Access, 9, 6465–6477.
Bonabeau, E., Dorigo, M., & Théraulaz, G. (1999). From natural to artificial swarm intelligence. Oxford University Press, Inc.
Dorigo, M., Birattari, M., & Stutzle, T. (2006). Ant colony optimization. IEEE Computational Intelligence Magazine, 1(4), 28–39.
Kennedy, J., & Eberhart, R. (1995). Particle swarm optimization. In: Proceedings of ICNN'95-international conference on neural networks. IEEE, (pp. 1942–1948).
Rashedi, E., Nezamabadi-Pour, H., & Saryazdi, S. (2009). GSA: A gravitational search algorithm. Information Sciences, 179(13), 2232–2248.
Storn, R., & Price, K. (1997). Differential evolution–a simple and efficient heuristic for global optimization over continuous spaces. Journal of Global Optimization, 11(4), 341–359.
Yao, X., Liu, Y., & Lin, G. (1999). Evolutionary programming made faster. IEEE Transactions on Evolutionary Computation, 3(2), 82–102.
Rudolph, G. (2000). Evolution strategies. Evolutionary Computation, 1, 81–88.
Samangouei, P., Kabkab, M., & Chellappa, R. (2018). Defense-gan: Protecting classifiers against adversarial attacks using generative models. https://arxiv.org/abs/180506605
Chen, S., Shi, D., Sadiq, M., & Cheng, X. (2020). Image Denoising With Generative Adversarial Networks and its Application to Cell Image Enhancement. IEEE Access, 8, 82819–82831.
Din, N. U., Javed, K., Bae, S., & Yi, J. (2020). A novel GAN-based network for unmasking of masked face. IEEE Access, 8, 44276–44287.
Yang, G., Yu, S., Dong, H., Slabaugh, G., Dragotti, P. L., Ye, X., Liu, F., Arridge, S., Keegan, J., & Guo, Y. (2017). DAGAN: Deep de-aliasing generative adversarial networks for fast compressed sensing MRI reconstruction. IEEE transactions on medical imaging, 37(6), 1310–1321.
Jiang, L., Qiao, K., Qin, R., Wang, L., Yu, W., Chen, J., Bu, H., & Yan, B. (2020). Cycle-consistent adversarial GAN: The integration of adversarial attack and defense. Security and Communication Networks.
Liu, X., Yang, H., Liu, Z., Song, L., Li, H., & Chen, Y. (2018). Dpatch: An adversarial patch attack on object detectors. https://arxiv.org/abs/180602299
Guo, Y., Wei, X., Wang, G., & Zhang, B. (2021). Meaningful Adversarial Stickers for Face Recognition in Physical World. https://arxiv.org/abs/2104.06728
Chan. P. P., Zheng, J., Liu, H., Tsang, E., & Yeung, D. S. (2021). Robustness analysis of classical and fuzzy decision trees under adversarial evasion attack. Applied Soft Computing 107:107311.
Karim, F., Majumdar, S., & Darabi, H. (2020). Adversarial attacks on time series. IEEE transactions on pattern analysis and machine intelligence.
Dong, Y., Su, H., Wu, B., Li, Z., Liu, W., Zhang, T., & Zhu, J. (2019). Efficient decision-based black-box adversarial attacks on face recognition. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, (pp. 7714–7722).
Zhang, H., Zhou, W., & Li, H. (2020). Contextual adversarial attacks for object detection. In: 2020 IEEE International Conference on Multimedia and Expo (ICME), IEEE, (pp. 1–6).
Di Noia, T., Malitesta, D., & Merra, F.A. (2020). Taamr: Targeted adversarial attack against multimedia recommender systems. In: 2020 50th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W), IEEE, (pp. 1–8).
Acknowledgements
This work was supported by Korea Institute for Advancement of Technology (KIAT) grant funded by the Korea Government (MOTIE) (P0008703, The Competency Development Program for Industry Specialist) and also Korea Environment Industry & Technology Institute (KEITI) through Exotic Invasive Species Management Program, funded by Korea Ministry of Environment (MOE) (2021002280004).
Funding
Not applicable.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Maqsood, M., Ghazanfar, M.A., Mehmood, I. et al. A Meta-Heuristic Optimization Based Less Imperceptible Adversarial Attack on Gait Based Surveillance Systems. J Sign Process Syst 95, 129–151 (2023). https://doi.org/10.1007/s11265-022-01742-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11265-022-01742-x