Abstract
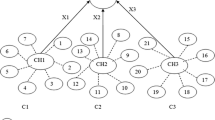
In this paper we propose an approach for key management in sensor networks which takes the location of sensor nodes into consideration while deciding the keys to be deployed on each node. As a result, this approach not only reduces the number of keys that have to be stored on each sensor node but also provides for the containment of node compromise. Thus compromise of a node in a location affects the communications only around that location. This approach which we call as location dependent key management does not require any knowledge about the deployment of sensor nodes. The proposed scheme starts off with loading a single key on each sensor node prior to deployment. The actual keys are then derived from this single key once the sensor nodes are deployed. The proposed scheme allows for additions of sensor nodes to the network at any point in time. We study the proposed scheme using both analysis and simulations and point out the advantages.










Similar content being viewed by others
Notes
The circle corresponding to the highest power level is not shown.
We assume reliable communication of messages here.
References
Basagni, S., Herrin, K., Bruschi, D., & Rosti, E. (2001). Secure pebblenet. In Proceedings of the 2001 ACM International Symposium on Mobile Ad Hoc Networking and Computing, MobiHoc 2001, October 2001.
Chan, H., Perrig, A., & Song, D. (2003). Random key predistribution schemes for sensor networks. In IEEE Symposium on Security and Privacy, pp. 197–213, May 2003.
Du, W., Deng, J., Han, Y., & Varshney, P. (2003). A pairwise key pre distribution scheme for wireless sensor networks. In Proceedings of the Tenth ACM Conference on Computer and Communications Security (CCS 2003), pp. 42–51, October 2003.
Du, W., Deng, J., Han, Y. S., Chen, S., & Varshney, P. K. (2004). A key management scheme for wireless sensor networks using deployment knowledge. In INFOCOM, 2004, April 2004.
Du, W., Deng, J., Han, Y. S., Varshney, P., Katz, J., & Khalili, A. (2005). A pairwise key pre-distribution scheme for wireless sensor networks. In ACM Transactions on Information and System Security (TISSEC), 2005.
Eschenauer, L., & Gligor, V. (2002). A key-management scheme for distributed sensor networks. In Proceedings of the 9th ACM Conference on Computer and Communications Security, pp. 41–47, November 2002.
Liu, D., & Ning, P. (2003). Establishing pairwise keys in distributed sensor networks. In Proceedings of the Tenth ACM Conference on Computer and Communications Security (CCS 2003), pp. 52–61, October 2003.
Liu, D., Ning, P., & Li, R. (2005). Establishing pairwise keys in distributed sensor networks. In ACM Transactions in Information Systems Security (Vol. 8, pp. 41–77), October 2005.
Perrig, A., Szewczyk, R., Wen, V., Culler, D., & Tygar, J. D. (2002). Spins: Security protocols for sensor networks. In Wireless Networks Journal (WINE), September 2002.
Zhu, S., Setia, S., & Jajodia, S. (2003). Leap: Efficient security mechanisms for large-scale distributed sensor networks. In Proceedings of the 10th ACM Conference on Computer and Communications Security (CCS ’03), October 2003.
Capkun, S., & Hubaux, J. P. (2005). Secure positioning of wireless devices with application to sensor networks. In IEEE Infocom, March 2005.
Lazos, L., & Poovendran, R. (2004). Serloc: Secure range-independent localization for wireless sensor networks. In Proceedings of WISE, pp. 21–30, October 2004.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Anjum, F. Location dependent key management in sensor networks without using deployment knowledge. Wireless Netw 16, 1587–1600 (2010). https://doi.org/10.1007/s11276-008-0145-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-008-0145-y