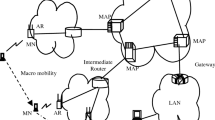
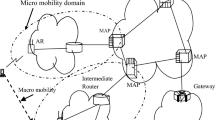
Abstract
By introducing a mobility anchor point (MAP), Hierarchical Mobile IPv6 (HMIPv6) reduces the signaling overhead and handoff latency associated with Mobile IPv6. In this paper, we propose a mobility-based load control (MLC) scheme, which mitigates the burden of the MAP in fully distributed and adaptive manners. The MLC scheme combines two algorithms: a threshold-based admission control algorithm and a session-to-mobility ratio (SMR)-based replacement algorithm. The threshold-based admission control algorithm gives higher priority to ongoing mobile nodes (MNs) than new MNs, by blocking new MNs when the number of MNs being serviced by the MAP is greater than a predetermined threshold. On the other hand, the SMR-based replacement algorithm achieves efficient MAP load distribution by considering MNs’ traffic and mobility patterns. We analyze the MLC scheme using the continuous time Markov chain in terms of the new MN blocking probability, ongoing MN dropping probability, and binding update cost. Also, the MAP processing latency is evaluated based on the M/G/1 queueing model. Analytical and simulation results demonstrate that the MLC scheme outperforms other schemes and thus it is a viable solution for scalable HMIPv6 networks.













Similar content being viewed by others
Notes
That is, load balancing among HAs and security issues are beyond scope of this paper.
References
Akyildiz, I., Mcnair, J., Ho, J., Uzunalioglu, H., & Wang, W. (1999). Mobility management in next-generation wireless systems. Proceedings of the IEEE, 87(8), 1347–1384.
Akyildiz, I., Xie, J., & Mohanty, S. (2004). A survey of mobility management in next-generation all IP-based wireless systems. IEEE Wireless Communications, 11(4), 16–28.
Johnson, D., Perkins, C., & Arkko, J. (2003). Mobility support in IPv6. IETF RFC 3775, June 2003.
Soliman, H., Castelluccia, C., Malki, K. E., & Bellier, L. (2005). Hierarchical Mobile IPv6 mobility management (HMIPv6). IETF RFC 4140, August 2005.
Pack, S., Nam, M., Kwon, T., & Choi, Y. (2006). An adaptive mobility anchor point selection scheme in Hierarchical Mobile IPv6 networks. Elsevier Computer Communications, 29(16), 3066–3078.
Hong, D., & Rappaport, S. (1986). Traffic model and performance analysis for cellular mobile radio telephone systems with prioritized and nonprioritized handoff procedures. IEEE Transactions on Vehicular Technology, 35(3), 77–92.
Pack, S., Lee, B., & Choi, Y. (2004). Load control scheme at local mobility agent in mobile IPv6 networks. In Proceedings of World Wireless Congress (WWC) 2004, May 2004.
Fang, Y., & Zhang, Y. (2002). Call admission control schemes and performance analysis in wireless mobile networks. IEEE Transactions on Vehicular Technology, 51(2), 371–382.
Pack, S., & Choi, Y. (2004). A study on performance of Hierarchical Mobile IPv6 in IP-based cellular networks. IEICE Transactions on Communications, E87-B(3), 462–469.
Hwang, S., Lee, B., Han, Y., & Hwang, C. (2004). An adaptive Hierarchical Mobile IPv6 using mobility profile. Wiley Wireless Communication and Mobile Computing, 4(2), 233–245.
Ma, W., & Fang, Y. (2004). Dynamic hierarchical mobility management strategy for mobile IP networks. IEEE Journal on Selected Areas in Communications, 22(4), 664–676.
Ortigoza-Guerrero, L., & Aghvami, A. H. (1999). A prioritized handoff dynamic channel allocation strategy for PCS. IEEE Transactions on Vehicular Technology, 48(4), 1203–1215.
Zhuang, W., Bensaou, B., & Chua, K. (2000). Adaptive quality of service handoff priority scheme for mobile multimedia networks. IEEE Transactions on Vehicular Technology, 49(2), 494–505.
Haung, Y. (2002). Determining the optimal buffer size for short message transfer in a heterogeneous GPRS/UMTS Network. IEEE Transactions on Vehicular Technology, 52(1), 216–225.
Lin, P., Lai, W., & Gan, C. (2004). Modeling oppotunaity driven multiple access in UMTS. IEEE Transactions on Wireless Communications, 3(5), 1669–1677.
Xiao, Y., Pan, Y., & Li, J. (2004). Design and Analysis of Location Management for 3G Cellular Networks. IEEE Transactions on Parallel and Distributed Systems, 15(4), 339–349.
Kleinrock, L. (1975). Queuing systems, Volume 1: Theory. New York: Wiley.
Wang, W., & Akyilidiz, I. (2001). A cost-efficient signaling protocol for Mobility Application Part (MAP) in IMT-2000 systems. In Proceedings of ACM Mobicom, 2001, October 2001.
Zeng, H., Fang, Y., & Chlamtac, I. (2002). Call blocking performance study for PCS networks under more realistic mobility assumptions. Telecommunication Systems, 19(2), 125–146.
Lin, Y. (2000). Overflow control for cellular mobility database. IEEE Transactions on Vehicular Technology, 49(2), 520–530.
Lin, Y. (2001). Eliminating overflow for large-scale mobility databases in cellular telephone networks. IEEE Transactions on Computers, 50(4), 356–370.
Hung, H., Lin, Y., Peng, N., & Yang, S. (2001). Resolving mobile database overflow with most idle replacement. IEEE Jounal on Selected Areas in Communications, 19(10), 1953–1961.
Luo, Y., Pan, Y., Li, J., Xiao, Y., & Lin, X. (2003). A new overflow replacement policy for efficient location management in mobile networks. In Proceedings of IEEE ISDCS 2003, May 2003.
Jue, J., & Ghosal, D. (1998). Design and analysis of a replicated server architecture for supporting IP-host mobility. Cluster Computing, 1(2), 249–260.
Deng, H., Huang, X., Zhang, K., Niu, Z., & Ojima, M. (2003). A hybrid load balance mechanism for distributed home agents in mobile IPv6. In Proc. IEEE PIMRC 2003, September 2003.
Vasilache, A., Li, J., & Kameda, H. (2003). Threshold-based load balancing for multiple home agents in mobile IP networks. Telecommunication Systems, 22(1-4), 11–31.
Fritsche, W., & Guardini, I. (2006). Deploying home agent load sharing in operational mobile IPv6 networks. In Proceedings of ACM MobiArch 2006, December 2006.
Bandai, M., & Sasase, I. (2003). A load balancing mobility management for multilevel Hierarchical Mobile IPv6 networks. In Proceedings of IEEE PIMRC 2003, September 2003.
Taleb, T., Suzuki, T., Kato, N., & Nemoto, Y. (2005). A dynamic & efficient MAP selection scheme for mobile IPv6 networks. In Proceedings of IEEE Globecom 2005, December 2005.
Pack, S., Nam, M., & Choi, Y. (2006). Design and analysis of optimal multi-level hierarchical mobile IPv6 networks. Wireless Personal Communications, 36(2), 95–112.
Acknowledgments
This work was supported by the Korea Research Foundation Grant funded by the Korean Government (KRF-2008-314-D00354).
Author information
Authors and Affiliations
Corresponding author
Additional information
The preliminary version of this paper was presented at IEEE Global Telecommunications Conference (GLOBECOM) 2004, Dallas, USA, November 2004.
Appendix 1
Appendix 1
1.1 Derivation of π(i, j) in the TLC/MLC schemes
As shown in Fig. 7, the Markov chain for the TLC scheme (and the MLC scheme) has a state space, \(S=\{(i,\,j)| 0 \leq i \leq K, 0 \leq i+j \leq C\}\), and the following balance equations are established:
-
(1)
i = 0 and j = 0:
$$ (\lambda_O+\lambda_N)\cdot \pi(0,0)=\mu_N \cdot \pi(1,0)+\mu_O \cdot \pi(0,1); $$ -
(2)
i = 0 and 0 < j < K:
$$ (\lambda_O+\lambda_N+j \mu_O)\cdot \pi(0,j)=\lambda_O \cdot \pi(0,j-1) +\mu_N \cdot \pi(1,j)+(j+1)\mu_O \cdot \pi(0,j+1); $$ -
(3)
i = 0 and K≤j < C:
$$ (\lambda_O+j \mu_O) \cdot \pi(0,j)=\lambda_O \cdot \pi (0,j-1)+\mu_N \cdot \pi(1,j)+(j+1)\mu_O \cdot \pi(0,j+1); $$ -
(4)
i = 0 and j = C:
$$ C \mu_O \cdot \pi(0,C)=\lambda_O \cdot \pi(0,C-1); $$ -
(5)
0 < i < K and j = 0:
$$ (\lambda_O+\lambda_N+i\mu_N)\cdot \pi(i,0)=\lambda_N \cdot \pi(i-1,0) +(i+1)\mu_N \cdot \pi(i+1,0)+\mu_O \cdot \pi(i,1); $$ -
(6)
0 < i < K and 0 < j < K−i:
$$ \begin{aligned} (\lambda_O+\lambda_N+i \mu_N+j \mu_O) \cdot \pi(i,j)&=\lambda_N \cdot \pi(i-1,j)+\lambda_O \cdot \pi(i,j-1)\\ &+(i+1)\mu_N \cdot \pi(i+1,j)+(j+1)\mu_O \cdot \pi(i,j+1); \end{aligned} $$ -
(7)
0 < i < K and j = K−i:
$$ \begin{aligned} (\lambda_O+i\mu_N+j \mu_O) \cdot \pi(i,j)&=\lambda_N \cdot \pi(i-1,j) +\lambda_O \cdot \pi(i,j-1)\\ &+(i+1)\mu_N\cdot \pi(i+1,j)+(j+1)\mu_O \cdot \pi(i,j+1); \end{aligned} $$ -
(8)
0 < i < K and K−i < j < C−i:
$$ \begin{aligned} (\lambda_O+i \mu_N+j \mu_O)\cdot \pi(i,j)&=\lambda_O \cdot \pi(i,j-1)+(i+1)\mu_N \cdot \pi(i+1,j)\\ &+(j+1) \mu_O\cdot \pi(i,j+1); \end{aligned} $$ -
(9)
0 < i < K and j = C−i:
$$ (i\mu_N+j\mu_O)\cdot \pi(i,j)=\lambda_O \cdot \pi(i,j-1); $$ -
(10)
i = K and j = 0:
$$ (\lambda_O+K \mu_N)\cdot \pi(K,0)=\lambda_N \cdot\pi(K-1,0) +\mu_O \cdot \pi(K,1); $$ -
(11)
i = K and 0 < j < C−K:
$$ (\lambda_O+K\mu_N+j \mu_O)\cdot \pi(K,j)=\lambda_O \cdot \pi(K,j-1)+ (j+1)\mu_O \cdot \pi(K,j+1); $$ -
(12)
i = K and j = C−K:
$$ (K \mu_N+(C-K)\mu_O)\cdot \pi(K,C-K)=\lambda_O \cdot \pi(K,C-K-1). $$
Each balance equation can be represented as a form of \(\pi(i,\,j)=A\pi(i-1,\,j)+B\pi(i+1,\,j)+C\pi(i,\,j-1)+D\pi(i,\,j+1)\), where A, B, C, and D are constants. Then, the steady state probability can be computed using an iterative algorithm and the normalization condition, \(\sum\nolimits_{i=0}^{K} \sum\nolimits_{j=0}^{C-i} {\pi(i,j)}=1\). In the iterative algorithm, ɛ is a sufficiently small value and |S| represents the cardinality of S.
Iterative algorithm
-
Step 1: t is set to 0.
-
Step 2: For all (i, j) ∈S, πt(i, j) is initialized as 1/|S|.
-
Step 3: For all (i, j) ∈ S, \(\pi^{t+1}(i,j) \leftarrow \pi^{t}(i,j)\).
-
Step 4: For all \((i,j) \in S\), compute πt+1(i,j) by balance equations, \(\pi^{t+1}(i,\,j)=A \pi^{t}(i-1,\,j)+B \pi^{t}(i+1,\,j)+C\pi^{t}(i,\,j-1)+D\pi^{t}(i,\,j+1)\).
-
Step 5: For all (i, j) ∈ S, if |πt+1(i, j)−πt(i, j)| < ɛ, the iteration is terminated. Otherwise, \(t \leftarrow t+1\) and go to Step 3.
Rights and permissions
About this article
Cite this article
Pack, S., Kwon, T. & Choi, Y. A mobility-based load control scheme in Hierarchical Mobile IPv6 networks. Wireless Netw 16, 545–558 (2010). https://doi.org/10.1007/s11276-008-0152-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-008-0152-z