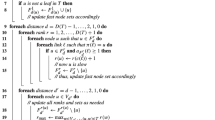Abstract
In this paper, we investigate the fundamental properties of broadcasting in mobile wireless networks. In particular, we characterize broadcast capacity and latency of a mobile network, subject to the condition that the stationary node spatial distribution generated by the mobility model is uniform. We first study the intrinsic properties of broadcasting, and present the RippleCast broadcasting scheme that simultaneously achieves asymptotically optimal broadcast capacity and latency, subject to a weak upper bound on maximum node velocity and under the assumption of static broadcast source. We then extend RippleCast with the novel notion of center-casting, and prove that asymptotically optimal broadcast capacity and latency can be achieved also when the broadcast source is mobile. This study intendedly ignores the burden related to the selection of broadcast relay nodes within the mobile network, and shows that optimal broadcasting in mobile networks is, in principle, possible. We then investigate the broadcasting problem when the relay selection burden is taken into account, and present a combined distributed leader election and broadcasting scheme achieving a broadcast capacity and latency which is within a \(\Uptheta((\log n)^{1+\frac{2}{\alpha}})\) factor from optimal, where n is the number of mobile nodes and α > 2 is the path loss exponent. However, this result holds only under the assumption that the upper bound on node velocity converges to zero (although with a very slow, poly-logarithmic rate) as n grows to infinity.




Similar content being viewed by others
Notes
This is true unless the destination is the vicinity of the sender, which occurs with vanishingly probability in a sufficiently large network with randomly selected source/destination pairs.
This strategy has become the fundamental communication paradigm in delay tolerant networks [4].
A formal definition of sparse and dense mobile networks will be given in Sect. 3.
To simplify notation, in the following we assume that the product of the transmitter and receiver antenna gain is 1.
Given the probabilistic characterization of mobile node positions assumed in this paper, most of the properties proved in this paper hold with high probability (w.h.p.), i.e., with probability at least \(1-\frac{1}{n}\).
The actual rule used to selected leaders in case more than one nodes are present in a mini-cell is irrelevant.
Different non-source nodes are allowed to have different velocity, as long as a common upper bound on node velocity is not impaired.
For the sake of simplicity, we use the intuitive notion of “closed curve” when referring to a ripple, although the ripple is not a curve in standard geometric sense.
References
Brar, G., Blough, D., & Santi, P. (2008). The SCREAM approach for efficient distributed scheduling with physical interference in wireless mesh networks. In Proceedings of IEEE ICDCS, pp. 214–224.
Chen, Y., & Welch, J. L. (2005). Location-based broadcasting for dense mobile ad hoc networks. In Proceedings of ACM MSWiM, pp. 63–70.
Ellis, R. B., Martin, J. L., & Yan, C. (2007). Random geometric graph diameter in the unit ball. Algorithmica, 47(4), 421–438.
Fall, K. (2003). A Delay-Tolerant network architecture for challenged internets. In Proceedings of ACM SIGCOMM, pp. 27–34.
Franceschetti, M., Migliore, M. D., & Minero, P. The capacity of wireless networks: Information-theoretic and physical limits. Available at http://circuit.ucsd.edu/∼massimo/papers.htm.
Grossglauser, M., & Tse, D. N. C. (2001). Mobility increases the capacity of ad-hoc wireless networks. In Proceedings of IEEE Infocom, pp. 1360–1369.
Gupta, P., & Kumar, P. R. (2000). The capacity of wireless networks. IEEE Transactions on Information Theory, 46(2), 388–404.
Jacquet, P., Mans, B., & Rodolakis, G. (2009). Information propagation speed in mobile and delay tolerant networks. In Proceedings of IEEE Infocom, pp. 244–252.
Keshavarz-Haddad, A., & Riedi, R. (2007). On the broadcast capacity of multihop wireless networks: Interplay of power, density and interference. In Proceedings of IEEE SECON, pp. 314–323.
Kolchin, V. F., Sevast’yanov, B. A., & Chistyakov, V. P. (1978). Random allocations. Washington, DC: V.H. Winston and Sons.
Kong, Z., & Yeh, E. (2008). On the latency of information dissemination in mobile wireless networks. In Proceedings of ACM MobiHoc, pp. 139–148.
Kuhn, F., Wattenhofer, R., & Zollinger, A. (2008). Ad hoc networks beyond unit disk graphs. Wireless Networks, 114(5), 715–729.
LeBoudec, J.-Y., & Vojnovic, M. (2005). Perfect simulation and stationarity of a class of mobility models. In Proceedings of IEEE Infocom, pp. 2743–2754.
Li, X. Y., Tang, S .J., & Frieder, O. (2007). Multicast capacity for large scale wireless ad hoc networks. In Proceedings of ACM Mobicom, pp. 266–277.
Liu, B., Towsley, D., & Swami, A. (2008). Data gathering capacity of large scale multihop wireless networks. In Proceedings of IEEE MASS, pp. 124–132.
Marco, D., Duarte-Melo, E. J., Liu, M., & Neuhoff, D. L. (2003). On the many-to-one transport capacity of a dense wireless sensor network and the compressibility of Its data. In Proceedings of the IPSN, LNCS 2634, 1–16.
Nakano, K., & Olariu, S. (2002). A survey on leader election protocols for radio networks. In Proceedings of ISPAN, pp. 71–77.
Neely, M. J., & Modiano, E. (2005). Capacity and delay tradeoffs for ad hoc mobile networks. IEEE Transactions Information Theory, 51(6), 1917–1937.
Ni, S., Tseng, Y., Chen, Y., & Sheu, J. (1999). The broadcast storm problem in a mobile ad hoc network. In Proceedings of ACM Mobicom, pp. 151–162.
Ozgur, A., Leveque, O., & Tse, D. (2007). Hierarchical cooperation achieves linear capacity scaling in ad hoc networks. In Proceedings of IEEE Infocom, pp. 382–390.
Pleisch, S., Balakrishnan, M., Birman, K., & van Renesse, R. (2006). MISTRAL: Efficient flooding in mobile ad-hoc networks. In Proceedings of ACM MobiHoc, pp. 1–12.
Resta, G., & Santi, P. (2009). Latency and capacity optimal broadcasting in wireless multi-Hop networks. In Proceedings of IEEE ICC.
Resta, G., & Santi, P. (2011). Latency and capacity optimal broadcasting in wireless multi-hop networks with arbitrary number of sources. IEEE Transaction on Information Theory, 57(12), 7746–7758.
Scheideler, C., Richa, A., & Santi, P. (2008). An O(log n) dominating set protocol for wireless ad hoc networks under the physical interference model. In Proceedings of ACM MobiHoc, pp. 91–100.
Shakkottai, S., Liu, X., & Srikant, R. (2007). The multicast capacity of large multihop wireless networks. In Proceedings of ACM MobiHoc, pp. 247–255.
Sharma, G., Mazumdar, R., & Shroff, N. (2006). Delay and capacity trade-offs in mobile ad hoc networks: A global perspective. In Proceedings of IEEE Infocom, pp. 1–12.
Wu, Y., & Li, Y. (2008). Construction algorithms for k-connected m-dominating sets in wireless sensor networks. In Proceedings of ACM Mobihoc, pp. 83–90.
Zheng, R. (2006). Information dissemination in power-constrained wireless networks. In Proceedings of IEEE Infocom, pp. 1–10.
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
Proof of Lemma 2.
Let us call the cells at cell distance i from the cell containing the source node the i-th ripple. We start showing that: a) for each cell A in the i-th ripple, the leader node of cell A transmits during round t + i the packet generated by the source node at round t. The proof is by induction on i. Property a) trivially holds when i = 0. Assume now property a) holds for each j < i. In order for a) to hold also for i, we need to show that, for any cell A in the i-th ripple, the node selected as leader for A during round t + i, which is going to transmit during round t + i, has received the packet generated by the source at round t before its transmission opportunity during round t + i. Given that a) is assumed to hold for j < i, we have that the leader node of cell B, where B is any of the cells in the (i − 1)-th ripple adjacent to A (note that at least one such cell always exists), has transmitted during round t + i − 1 the packet generated by source node at round t. Given the rules for selecting leader nodes, we have that the leader node at round t + i − 1 for cell B is selected amongst the nodes located in the central mini-cell of B at the beginning of round t + i − 1. By Proposition 1, we have that at least one such node exists, w.h.p. Furthermore, the upper bound \(\bar{v}\) on node velocity guarantees that a node travels at most \( \bar{v} \bar{k}^2 \tau=\frac{l}{3}\) in the time elapsing between the beginning of round t + i − 1 and the beginning of round t + i. Since the leader node of cell B was within the central mini-cell of cell B at the beginning at round t + i − 1 and given the above observation about the distance traveled by nodes, we have that the leader node of cell B is still within cell B when it is scheduled for transmission during round t + i − 1. Hence, by Proposition 3, we have that the packet transmitted by the leader node of cell B during round t + i − 1, which by induction is the packet generated by the source node at round t, is correctly received by all nodes within cell A at the time of transmission. In particular, the leader node w for cell A at round t + i is within the central mini-cell of A at the beginning of round t + i, which given the above observation about maximum traveled distance, ensures that w was within cell A also during the entire round t + i − 1. Thus, node w can correctly receive the packet sent by the leader node of cell B during round t + i − 1, and can forward it in the network when scheduled for transmission at round t + i, which implies property a).
Let us now define the set of covered cells Cov(p) for a certain packet p as the set of cells such that their respective leader nodes have already transmitted packet p. By property a), and assuming packet p is generated by the source at round t, we have that Cov(p) at round t + i is the union of all the cells in ripples \(0,\dots,i\). Given the assumption on the size L(n) of the deployment region, we have that Cov(p) contains all the cells in the deployment region at round \(t+\frac{L(n)}{2 l}=t+O(\sqrt{\frac{n}{\log n}})\). Let us now consider an arbitrary mobile node u, and assume by contradiction that node u has not received packet p by the end of round \(t+\frac{L(n)}{2 l}\). Since Cov(p) contains all the cells in the deployment region by then, and considering that each of the ripples propagating packet p is a “closed curve”Footnote 8, the only possible way for node u to avoid receiving p is to cut through the ripple propagation front during round j, for some \(0<j<\frac{L(n)}{2 l}\). However, for this to be possible, node u should travel distance at least 2l between two successive rounds (see Fig. 5), which is possible only if node velocity is at least \(v^{\prime}=\frac{2 l}{2 \bar{k}^2 \tau}>\bar{v}\). Thus, the assumption about maximum node velocity is contradicted, and the Lemma is proved. \(\square\)
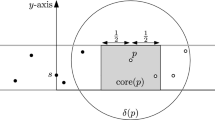
Assume the source s is somewhere south of the diagrams, and the propagation front of packet p moves northward. Stars represents cell leaders active in a certain round, and the checkered region is the region covered by them. The white area has not yet been covered by packet p, while the gray area represents cells in Cov(p) during a certain round. On the left, a circle represents a node lying in the white area which has not yet received p at a certain round t + j − 1. To avoid reception of packet p, the node must cut the propagation front and reach the gray area during round t + j (right), where p is no longer transmitted. Thus, the node should travel distance at least 2l between the two consecutive rounds
Proof of Lemma 3.
Let us consider now the interference experienced by u under the condition that in each cell with the same color there are at most m nodes. Assume w.l.o.g. that cell(u) has coordinates (0,0). Given the coloring scheme, interferers lie in the cells with bottom left corner at \((x\cdot k\cdot l,y\cdot k\cdot l)\) with \(x,y\in\mathbf{Z}\) and (x, y) ≠ (0, 0) (shaded cells in Fig. 2).
The distance d(x, y) between u and an interferer located in cell \((x\cdot k\cdot l,y\cdot k\cdot l),\) with x, y ≠ 0, can be lower bounded as follows:
where the term −l depends on the actual positions of u and I inside their respective cells.
Since \(a^{2}+b^{2}\ge \left(\max\{a,b\}\right)^{2},\) from (3) we obtain the following lower bound on d(x, y):
Note that the last bound is always strictly positive, since we are assuming k ≥ 2 and |x|, |y| are not both 0.
The interference received by u thus satisfies
where the sum is extended over all the pairs (x, y) ≠ (0, 0), with \(x,y\in \mathbf{Z}\).
Counting twice the contributions along x = 0, y = 0, and |x| = |y|, we have
due to the eightfold symmetry of the summation shown in Fig. 7. Collecting the values for which max(x, y) = x we obtain
where \(\zeta(\cdot)\) is the Riemann’s zeta function and summarizing we obtain formula (1). \(\square\)
Proof of Lemma 9.
Let P s denote a minimum-hop cell path connecting cell C(s, i) with C c . In other words, P s is a minimum-length sequence of cells \(C(s,i)=C_0,\dots,C_j = C_c\) such that, for each \(q=0,\dots,j-1,\) cells C q and C q+1 are adjacent. We will prove that the packet generated by s at round i is propagated through P s till it reaches C c , with the packet progressing one cell at each round. The proof is by induction on the cell distance q from C(s, i). More specifically, we want to prove the following property: a) packet p i is correctly received by node L(C q+1,i + q) during round i + q, for any 0 ≤ q ≤ j − 1. Property a) implies the lemma by observing that d(C(s, i), C c ) = d(s, i) implies existence of a cell path of length d(s, i) connecting cells C(s, i) and C c .
To prove the base case q = 0, we observe that Lemma 8 ensures that p i is correctly received by all nodes that are located in cells adjacent to C(s, i)—including cell C 1—at time t i + 2k 2τ. On the other hand, Lemma 7 ensures that node L(C 1,i) remains within cell C 1 during the whole duration of rounds i and i + 1. Thus, node L(C 1,i) is guaranteed to be in cell C 1 at time t i + 2k 2τ, and to correctly receive p i .
Assume now that property a) holds for any \(q^{\prime}<q\). By induction hypothesis, node L(C q ,i + q − 1) has correctly received p i at the end of round i + q − 1. We have to prove that p i will be transmitted by node L(C q ,i + q − 1) during the next broadcast round i + q. We first observe that, in order for a packet to be transmitted by a non-source node, the packet had to be stored in the transmit buffer upon reception. This happens if and only if the following three conditions are fulfilled: (1) the node is the leader of its cell for the current round; (2) the cellID in the packet equals the cell to which the node belongs; and (3) packet ID is larger than that of the last received packet. It is easy to see that condition (1) is fulfilled at node L(C q ,i + q − 1). Condition (2) is fulfilled under the assumption, which holds without loss of generality, that the next cell selected by node L(C q−1,i + q − 2) when transmitting p i was set to C q . As for condition (3), we have to prove that packet ordering is preserved when forwarding packets generated by the source towards cell C c . More specifically, we have to prove that packets p j with j > i cannot be received by L(C q ,i + q − 1) before packet p i . Note that there are two possible ways in which a packet p j with j > i can be propagated “faster” than packet p i :—(i) packet p j is a new packet generated by s, and s has moved along P s in the direction of C c ; and—(ii) packet p j is a packet relayed by a leader node on its route to cell C c . As for case i), we observe that, by Lemma 6, node s can only move to adjacent cells during a broadcast round, hence its speed cannot exceed the speed of packet p i propagation towards C c . Yet, it is possible that, say, node s is located in cell C 1 at round i + 1, possibly leading to impaired packet ordering in case packet p i+1 is transmitted by s before packet p i is forwarded to C 2 by node L(C 1,i). However, the transmission slot reserved for source transmission is located after the 2k 2 slots allocated for forwarding pending packets to the center cell C c , hence packet ordering is preserved in case (i). As for case (ii), we observe that it is possible for a leader node to have two packets in the transmit buffer during a certain round (due to, e.g., mobility of the source in the direction of the center cell as explained above). However, in case multiple packets are present in the transmit buffer, older packets are prioritized over newer ones, thus preserving packet ordering also in this case. We have then proved that packet p i is stored in the buffer of node L(C q ,i + q − 1) during round i + q − 1. We now have to prove that node L(C q ,i + q − 1) will transmit this packet during round i + q, and that node L(C q+1,i + q) correctly receives the packet. As for the first part, observe that nodes in cell C q have two transmission opportunities during round i + q; since node L(C q ,i + q − 1) has at most two packets in its transmit buffer (packet p i , and possibly packet p j with j = i − 1 or j = i + 1), two transmission opportunities are sufficient for node L(C q ,i + q − 1) to transmit all packets in the buffer, including packet p i . To see why at most two packets can be stored in a node’s transmit buffer, it is sufficient to observe that multiple packets are sent by a cell only when the source is traveling, say, from cell C k to cell C k+1 in a round j, in which case two packets will be transmitted by cell C k+1 during round j + 1 (the packet p j sent by the source at round j, and the new packet p j+1 generated by the source at round j + 1). If the source would be allowed to move to cell C k+2 during round j + 2, we would have cell C k+2 transmitting 3 packets at round j + 2 (packets p j , p j+1, and the new packet p j+2 generated by the source at round j + 2). However, Lemma 6 implies that the source cannot move to cell C k+2 during round j + 2, since it can cross at most one cell during the duration of two broadcast rounds. This implies that every cell transmits at most two packets during any center-cast phase of the broadcast round, which in turns implies that at most two packets can be stored in a node’s transmit buffer.
We are now left to show that node L(C q+1,i + q) correctly receives packet p i . By induction hypothesis, by the fact that leader nodes are unique in a cell, and by Lemma 7, we have that the only node in cell C q that has non-empty transmit buffer during round i + q is L(C q , i + q − 1), implying that there is no conflicting transmission from other nodes in C q during node L(C q ,i + q − 1) transmission(s). In order to prove that node L(C q+1,i + q) correctly receives p i , it is sufficient to observe that, by Lemma 7, node L(C q ,i + q − 1) is still within cell C q during round i + q, which implies that packets sent by this node during round i + q are correctly received by all nodes in adjacent cells, including node L(C q+1,i + q). \(\square\)
Rights and permissions
About this article
Cite this article
Resta, G., Santi, P. The fundamental limits of broadcasting in dense wireless mobile networks. Wireless Netw 18, 679–695 (2012). https://doi.org/10.1007/s11276-012-0427-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-012-0427-2