Abstract
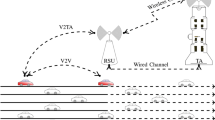
Increasing demand in user-friendly, computationally efficient and sophisticated vehicles led automobile industries to manufacture them with efficient onboard sensors, communication devices, resource rich hardware. Vehicular resources provide infotainment on-the-go. In mere future, every vehicle is a resource full machine. The vehicular resources which include computing power, storage and internet connectivity can be shared among the vehicles or can be lend over the internet to various customers. Vehicles can comprehensively make use of the resources available with road-side units (RSU’s) to communicate with other vehicles and RSU’s. Vehicular communications are useful especially in situations of accidents (or) natural calamities. Vehicles can update the RSU’s with information regarding such events. This information can then be broadcasted to the vehicles in that area or path. The proposed scheme ensures secure and efficient communications among nodes in a hierarchy consisting of vehicles, RSU’s, RSU co-ordinators and Trusted authority. The approach outlined in the paper can be used to decrease the overhead involved in secure transfer of information during communication.









Similar content being viewed by others
Abbreviations
- id :
-
Identifier to the nodes present in hierarachy
- IV:
-
Identification vector to nodes which is in the form of co-ordinates
- x :
-
Dependent variables used for the identifiers of the vehicle itself
- y :
-
Dependent variables used for the identifiers of the vehicles with which communication is being done
- RSU:
-
Road side unit
- RSU-C:
-
Road side unit coordinator
- TA:
-
Trusted authority
References
Gillani, S., et al. (2013). A survey on security in vehicular ad hoc networks. Communication technologies for vehicles. Berlin Heidelberg: Springer.
Yan, G., Wen, D., Olariu, S., & Weigle, M. C. (2013). Security challenges in vehicular cloud computing. IEEE Transactions on Intelligent Transportation Systems, 14(1), 284–294.
Xu, Q., Mak, T., Ko, J., & Sengupta, R. (2004). Vehicle-to-vehicle safety messaging in DSRC. In Proceedings of the rst ACM workshop on Vehicular ad hoc networks, ACM Press, pp. 19–28.
Car-to-Car communication, [Online]. http://www.car-to-car.org [Accessed 15 June, 2010].
Chan, H., Perrig, A., & Song, D. (2003). Random key predistribution schemes for sensor networks. Symposium on security and privacy, 2003. Proceedings. 2003. IEEE.
Eschenauer, L., & Gligor, V. D. (2002). A key-management scheme for distributed sensor networks. In Proceedings of the 9th ACM conference on Computer and communications security, ACM.
Zhou, Jun, et al. (2015). 4S: A secure and privacy-preserving key management scheme for cloud-assisted wireless body area network in m-healthcare social networks. Information Science, 314, 255–276.
Stallings, W. (2005). Cryptography and network security: Principles and practices (4th ed.). Upper Saddle River, NJ: Prentice Hall.
Yang, X., Liu, J., Zhao, F., & Vaidya, N. (2004). A vehicle-to-vehicle communication protocol for cooperative collision warning. In first annual international conference on mobile and ubiquitous systems: Networking and services (MobiQuitous 2004), August 2004.
Han, K. et al. (2013) Algorithm design for data communications in duty-cycled wireless sensor networks: A survey. IEEE Communications Magazine, 51(7), 107–113.
Ali, Mazhar, et al. (2015). Security in cloud computing: Opportunities and challenges. Information Sciences, 305, 357–383.
Wei, Lifei, et al. (2014). Security and privacy for storage and computation in cloud computing. Informatoin Science, 258, 371–386.
Wei, L. et al. (2010). SecCloud: Bridging secure storage and computation in cloud. ICDCS Workshops, pp. 52–61.
Jing, Qi, et al. (2014). Security of the internet of things: Perspectives and challenges. Wireless Networks, 20(8), 2481–2501.
Attar, Alireza, et al. (2012). A survey of security challenges in cognitive radio networks: Solutions and future research directions. Proceedings of the IEEE, 100(12), 3172–3186.
Yang, Haomin, et al. (2014). Provably secure three-party authenticated key agreement protocol using smart cards. Computer Networks, 58, 29–38.
Wan, J., et al. (2014). Context-aware vehicular cyber-physical systems with cloud support: Architecture. Challenges and Solutions, IEEE Communications Magazine, 52(8), 106–113.
Hesham, A., Abdel-Hamid, A., & Abou El-Nasr, M. (2011). A dynamic key distribution protocol for PKI-based VANETs. In IEEE conference publications, Wireless Days (WD), IFIP.
Al-kahtani, M. S. (2012). Survey on security attacks in Vehicular Ad hoc Networks (VANETs). 6th International conference on signal processing and communication systems (ICSPCS), 2012, vol. 1(9), pp. 12–14.
Sumra, I. A., Ahmad, I., Hasbullah, H., & bin Ab Manan, J.-L. (2011). Behaviour of attacker on some new possible attacks in Vehicular Ad hoc Network (VANET), 3rd International congress on ultra modern telecommunications and control systems and workshops (ICUMT), 2011, pp. 1–8, 5–7 October 2011.
Lo, N.-W., Tsai, H.-C. (2007). Illusion attack on vanet applications—A message plausibility problem, Globecom Workshops, 2007 IEEE, pp.1–8.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Raja Sekhar, K., Ravi Chandra, T.S., Pooja, S. et al. Light weight security protocol for communications in vehicular networks. Wireless Netw 22, 1343–1353 (2016). https://doi.org/10.1007/s11276-015-1034-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-015-1034-9