Abstract
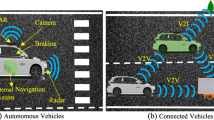
Modern vehicles are proficient in establishing a spontaneous connection over a wireless radio channel, synchronizing actions and information. Security infrastructure is most important in such a sensitive scope of vehicle communication for coordinating actions and avoiding accidents on the road. One of the first security issues that need to be established is authentication via IEEE 1609.2 security infrastructure. According to our preliminary work, vehicle owners are bound to preprocess a certificate from the certificate authority. The certificate carries vehicle static attributes (e.g., licence number, brand and color) certified together with the vehicle public key in a monolithic manner. Nevertheless, a malicious vehicle might clone the static attributes to impersonate a specific vehicle. Therefore, in this paper we consider a resource expensive attack scenario involving multiple malicious vehicles with identical visual static attributes. Apparently, dynamic attributes (e.g., location and direction) can uniquely define a vehicle and can be utilized to resolve the true identity of the vehicle. However, unlike static attributes, dynamic attributes cannot be signed by a trusted authority beforehand. We propose an approach to verify the coupling between non-certified dynamic attributes and certified static attributes on an auxiliary communication channel, for example, a modulated laser beam. Furthermore, we illustrate that the proposed approach can be used to facilitate the usage of existing authentication protocols such as NAXOS, in the new scope of ad-hoc vehicle networks. We use BAN logic to verify the security claims of the protocol against the passive and active interception.








Similar content being viewed by others
References
Dedicated Short Range Communications (DSRC). http://grouper.ieee.org/groups/scc32/Attachments.html.
IEEE Std 1609.2-2013 (Revision of IEEE Std 1609.2-2006). (2013). IEEE standard for wireless access in vehicular environments security services for applications and management messages, pp. 1–289.
Kim, A., Kniss, V., Ritter, G., & Sloan, S. (2011). An approach to communications security for a communications data delivery system for V2V/V2I safety: Technical description and identification of policy and institutional issues. U.S. Department of Transportation, Research and Innovative Technology Admisitration (RITA), FHWA-JPO-11-130.
Kenney, J. B. (2011). Dedicated short-range communications (DSRC) standards in the United States. Proceedings of the IEEE, 99(7), 1162–1182.
Beigl, M. (1999). Point & click-interaction in smart environments. Lecture notes in computer science. Handheld and Ubiquitous Computing, 1707, 311–313.
Burrows, M., Abadi, M., & Needham, R. (1990). A logic of authentication. ACM Transactions on Computer Systems, 8(1), 18–36.
Canetti, R., & Krawczyk, H. (2001). Analysis of key-exchange protocols and their use for building secure channels. Lecture notes in computer science. Advances in Cryptology EUROCRYPT, 2045, 453–474.
Chong, M. K., & Gellersen, H. (2012). Usability classification for spontaneous device association. Personal and Ubiquitous Computing, 16(1), 77–89.
Diffie, W., & Hellman, M. (1976). New directions in cryptography. IEEE Transactions on Information Theory, 22(6), 644–654.
Hartenstein, H., & Laberteaux, K. (2008). A tutorial survey on vehicular ad hoc networks. Communications Magazine, IEEE, 46(6), 164–171.
Hossain, E., Chow, G., Leung, V. C. M., McLeod, R. D., Mišsić, J., Wong, V. W. S., & Yang, O. (2010). Vehicular telematics over heterogeneous wireless networks: A survey. Computer Communications, 33(7), 775–793.
Kindberg, T., & Zhang, K. (2003). Secure spontaneous device association. Ubiquitous Computing, 2862, 124–131.
Koscher, K., Czeskis, A., Roesner, F., Patel, S., Kohno, T., Checkoway, S., McCoy, D., Kantor, B., Anderson, D., Shacham, H., & Savage, S. (2010). Experimental security analysis of a modern automobile. In IEEE symposium on security and privacy (SP), pp. 447–462.
Krawczyk, H. (2003). Sigma: The ’sign-and-mac’ approach to authenticated Diffie–Hellman and its use in the IKE-protocols. Lecture notes in computer science. Advances in Cryptology: CRYPTO, 2729, 400–425.
Kumar, A., Saxena, N., Tsudik, G., & Uzun, E. (2009). A comparative study of secure device pairing methods. Pervasive and Mobile Computing, 5(6), 734–749.
LaMacchia, B., Lauter, K., & Mityagin, A. (2007). Stronger security of authenticated key exchange. Lecture notes in computer science. Provable Security, 4784, 1–16.
Lee, J., & Park, J. H. (2008). Authenticated key exchange secure under the computational Diffie–Hellman assumption. IACR Cryptology ePrint Archive.
Maurer, U. M., & Wolf, S. (1999). The relationship between breaking the Diffie–Hellman protocol and computing discrete logarithms. SIAM Journal on Computing, 28(5), 1689–1721.
Mayrhofer, R., & Welch, M. (2007). A human-verifiable authentication protocol using visible laser light. In The second international conference on availability, reliability and security, pp. 1143–1148.
McCune, J., Perrig, A., & Reiter, M. (2005). Seeing-is-believing: Using camera phones for human-verifiable authentication. In IEEE symposium on security and privacy, pp. 110–124.
Nguyen, L. H., & Roscoe, A. W. (2011). Authentication protocols based on low-bandwidth unspoofable channels: A comparative survey. Journal of Computer Security, 19(1), 139–201.
Papadimitratos, P., Buttyan, L., Holczer, T., Schoch, E., Freudiger, J., Raya, M., et al. (2008). Secure vehicular communication systems: Design and architecture. Communications Magazine, IEEE, 46(11), 100–109.
Patel, S., & Abowd, G. (2003). A 2-way laser-assisted selection scheme for handhelds in a physical environment. Lecture notes in computer science. Ubiquitous Computing, 2864, 200–207.
Ponte Mller, F., Navajas, L., & Strang, T. (2013). Characterization of a laser scanner sensor for the use as a reference system in vehicular relative positioning. Communication Technologies for Vehicles, 7865, 146–158.
Raya, M., & Hubaux, J.-P. (2005). The security of vanets. In Proceedings of the 2nd ACM international workshop on vehicular ad hoc networks, pp. 93–94.
Raya, M., & Hubaux, J.-P. (2007). Securing vehicular ad-hoc networks. Journal of Computer Security, 15(1), 39–68.
Ringwald, M. (2002). Spontaneous interaction with everyday devices using a PDA. In Proceedings on supporting spontaneous interaction in ubiquitous computing settings, a workshop held at Ubicomp.
Tranposrtation Research Board of the National Academies. (2013). Guidelines for the use of mobile LIDAR in transportation applicaions. National Coperative Highway Research Program, Report 748. http://www.trb.org/Main/Blurbs/169111.aspx
Sarr, A., Elbaz-Vincent, P., & Bajard, J.-C. (2010). A new security model for authenticated key agreement. Security and Cryptography for Networks, 6280, 219–234.
Sichitiu, M., & Kihl, M. (2008). Inter-vehicle communication systems: A survey. Communications Surveys Tutorials, IEEE, 10(2), 88–105.
Sufatrio, S., & Yap, R. H. C. (2008). Extending BAN logic for reasoning with modern PKI-based protocols. In IFIP international conference on network and parallel computing, pp. 190–197.
Ulrich, L. (2013). Whiter brights with lasers. IEEE Spectrum, 50(11), 36–56.
Ustaoglu, B. (2008). Obtaining a secure and efficient key agreement protocol from (H)MQV and NAXOS. Designs, Codes and Cryptography, 46(3), 329–342.
Yashiro, T., Kondo, T., Ariyasu, K., & Matsushita, Y. (1994). An inter-vehicle networking method using laser media. In IEEE 44th vehicular technology conference, vol. 1, pp. 443–447.
Fortin, B., Lherbier, R., & Noyer, J. C. (2013). A PHD approach for multiple vehicle tracking based on a polar detection method in laser range data. In IEEE international systems conference (SysCon), pp. 262–268.
Thuy, M., & Leon, F. P. (2009). Non-linear, shape independent object tracking based on 2D lidar data. In IEEE intelligent vehicles symposium, pp. 532–537.
Dolev, S., Krzywiecki, Ł., Panwar, N., & Segal, M. (2015). Vehicle authentication via monolithically certified public key and attributes. Wireless Networks, 1–18. doi:10.1007/s11276-015-1005-1.
Dolev, S., Krzywiecki, Ł., Panwar, N., & Segal, M. (2014). Dynamic attribute based vehicle authentication. In Proceedings of the 13th IEEE international symposium on network computing and applications (NCA), pp. 1–8.
Dolev, S., Krzywiecki, Ł., Panwar, N., & Segal, M. (2015). Optical PUF for vehicles non-forwardable authentication. Technical report TR-1502.
MacLachlan, R. A., & Mertz, C. (2006) Tracking of moving objects from a moving vehicle using a scanning laser rangefinder. In IEEE intelligent transportation systems conference, pp. 301–306.
Abumansoor, O., & Boukerche, A. (2012). Preventing a DoS threat in vehicular ad-hoc networks using adaptive group beaconing. In Proceedings of the 8th ACM symposium on QoS and security for wireless and mobile networks, pp. 63–70.
Capkun, S., Cagalj, M., Rengaswamy, R. K., Tsigkogiannis, I., Hubaux, J. P., & Srivastava, M. B. (2008). Integrity codes: Message integrity protection and authentication over insecure channels. IEEE Transactions on Dependable and Secure Computing, 5(4), 208–223.
Waytz, A., Heafner, J., & Epley, N. (2014). The mind in the machine: Anthropomorphism increases trust in an autonomous vehicle. Journal of Experimental Social Psychology, 52, 113–117.
Thornton, D. A., Redmill, K., & Coifman, B. (2014). Automated parking surveys from a LIDAR equipped vehicle. Transportation Research Part C: Emerging Technologies, 39, 23–35.
Zou, W., & Li, S. (2014). Calibration of nonoverlapping in-vehicle cameraswith laser pointers. IEEE Transactions on Intelligent Transportation Systems, 99, 1–12.
Shikiji, Y., Watari, K., Tsudaka, K., Wada, T., & Okada, H. (2014). Novel vehicle information acquisition method using vehicle code for automotive infrared laser radar. In Telecommunication networks and applications conference (ATNAC), Australasian, pp. 52–57.
Guillory, J., Meyer, S., Sianud, I., Ulmer-moll, A. M., Charbonnier, B., Pizzinat, A., & Algani, C. (2010). Radio-over-fiber architectures. IEEE Vehicular Technology Magazine, 5(3), 30–38.
David, K., Dixit, S., & Jefferies, N. (2010). 2020 Vision. IEEE Vehicular Technology Magazine, 5(3), 22–29.
Larcom, J. A., & Liu, H. (2013). Modeling and characterization of GPS spoofing. In IEEE international conference on technologies for homeland security, pp. 729–734.
Ulrich, L. (2014). Top ten tech cars. IEEE Spectrum, 51(4), 38–47.
He, D., Kumar, N., & Chilamkurti, N. (2015). A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Information Sciences, 321, 263–277.
Chain, K., Chang, K. H., Kuo, W. C., & Yang, J. F. (2015). Enhancement authentication protocol using zero-knowledge proofs and chaotic maps. International Journal of Communication Systems. doi:10.1002/dac.2945.
Amin, R., & Biswas, G. P. (2015). A secure light weight scheme for user authentication and key agreement in multi-gateway based wireless sensor networks. Ad Hoc Networks, 36, 58–80.
Barbeau, M., Hall, J., & Kranakis, E. (2005). Detecting impersonation attacks in future wireless and mobile networks. In Proceedings of the first international conference on secure mobile ad-hoc networks and sensors (MADNES), vol. 4074, pp. 80–95.
Acknowledgments
The work of the first author is partially supported by Orange Labs under external research Contract No. 0050012310-C04021, the Rita Altura Trust Chair in Computer Sciences, Lynne and William Frankel Center for Computer Sciences, and Israel Science Foundation (Grant No. 428/11). The work of the second author is partially supported by fundings from Polish National Science Center (Decision No. DEC-2013/08/M/ST6/00928) project HARMONIA. The work of the last author is partially supported by General Motors.
Author information
Authors and Affiliations
Corresponding author
Additional information
A preliminary version of this paper has appeared in proceedings of the 13th IEEE International Symposium on Network Computing and Applications (IEEE NCA) 2014 [38].
Rights and permissions
About this article
Cite this article
Dolev, S., Krzywiecki, Ł., Panwar, N. et al. Dynamic attribute based vehicle authentication. Wireless Netw 23, 1045–1062 (2017). https://doi.org/10.1007/s11276-016-1203-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-016-1203-5