Abstract
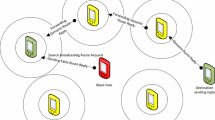
Mobile ad-hoc network is an infrastructure less type of network which does not require any kind of fixed infrastructure. It provides multi-hop communication between the source and destination nodes which are not within the direct range of each other through the intermediate nodes. These intermediate nodes cooperate with other nodes in finding an optimum and shortest route toward the destination. However, in holistic environments, some nodes do not cooperate with other nodes in finding the optimal route towards the destination and intentionally give the false route information of having the shortest path toward the destination with a high destination sequence number in order to attract the traffic toward itself and start dropping of the data packets instead of forwarding it. This type of routing misbehaviour is generally called as black hole attack or full packet dropping attack which is one of the most severe destructive attacks that lead to the network degradation. In this paper, we have proposed a protocol called as Mitigating Black Hole effects through Detection and Prevention (MBDP-AODV) based on a dynamic threshold value of the destination sequence number. In order to validate the efficiency of proposed protocol, the NS-2.35 simulator is used. The simulation results show that proposed protocol performs better as compared with existing one under black hole attack.






















Similar content being viewed by others
References
Balaji, S., & Rajaram, M. (2016). SIPTAN: Securing inimitable and plundering track for ad hoc network. Wireless Personal Communications. doi:10.1007/s11277-016-3187-y.
Hwang, R. J., & Hsiao, Y. K. (2013). An anonymous distributed routing protocol in mobile ad-hoc networks. Journal Supercomputing, 66, 888–906. doi:10.1007/s11227-013-0920-0.
Singh, T., Singh, J., & Sharma, S. (2016). Energy efficient secured routing protocol for MANETs. Wireless Networks. doi:10.1007/s11276-015-1176-9.
Poongodi, T., & Karthikeyan, M. (2016). Localized secure routing architecture against cooperative black hole attack in mobile ad hoc networks. Wireless Personal Communications. doi:10.1007/s11277-016-3318-5.
Perkins, C. E., Beliding-Royer, E., & Das, S. (2004). Ad hoc on-demand distance vector (AODV) routing. IETF Internet Draft, MANET working group.
Johnson, D. B., Maltz, D. A., & Hu, Y.-C. (2004). The dynamic source routing protocol for mobile ad-hoc network (DSR). IETF Internet Draft.
Dorri, A. (2016). An EDRI-based approach for detecting and eliminating cooperative black hole nodes in MANET. Wireless Networks. doi:10.1007/s11276-016-1251-x.
Jhaveri, R. H., Patel, S. J., & Jinwala, D. C. (2012). DoS attacks in mobile ad hoc networks: A survey. In IEEE 2nd international conference on advanced computing and communication technologies.
Verma, K., Hasbullah, H., & Kumar, A. (2013). Prevention of DoS attacks in VANET. Wireless Personal Communications, 73, 95–126. doi:10.1007/s11277-013-1161-5.
Laxmi, V., Lal, C., Gaur, M. S., & Mehta, D. (2015). JellyFish attack: Analysis, detection and countermeasure in TCP-based MANET. Journal of Information Security and Applications, 22, 99–112.
Faghihniya, M. J., Hosseini, S. M., & Tahmasebi, M. (2016). Security upgrade against RREQ flooding attack by using balance index on vehicular adhoc network. Wireless Networks. doi:10.1007/s11276-016-1259-2.
Djahel, S., Abdesselam, F. N., & Zhang, Z. (2011). Mitigating packet dropping problem in mobile ad hoc networks: Proposals and challenges. In IEEE communications survey and tutorial (pp. 658–672).
Dabideen, S., & Aceves, J. J. G. L. (2012). Secure routing in MANETs using local times. Wireless Networks, 18, 811–826. doi:10.1007/s11276-012-0435-2.
Gurung, S., & Chauhan, S. (2016). A novel approach for mitigating grayhole attack in MANET. Wireless Networks. doi:10.1007/s11276-016-1353-5.
Jhaveri, R. H., & Patel, N. M. (2015). A sequence number based bait detection scheme to thwart grayhole attack in mobile ad hoc networks. Wireless Networks, 21, 2781–2798. doi:10.1007/s11276-015-0945-9.
Gurung, S., & Saluja, K. K. (2014). Mitigating impact of black hole attack in MANET. In Proceedings of the 5th international conference on recent trends in information, telecommunication and computing.
Shahabi, S., Ghazvini, M., & Bakhtiarian, M. (2015). A modified algorithm to improve security and performance of AODV protocol against black hole attack. Wireless Networks. doi:10.1007/s11276-015-1032-y.
Gurung, S., & Siddhartha, S. (2017). A review of black-hole attack mitigation techniques and its drawbacks in mobile ad-hoc network. In Proceedings of the 2nd IEEE international conference on WiSPNET, (pp. 2409–2415).
Shi, F., Liu, W., Jin, D., & Song, J. (2014). A cluster-based countermeasure against blackhole attacks in MANETs. Telecommunication Systems, 57(2), 119–136.
Chang, J. M., Tsou, P. C., Woungang, I., Chao, H. C., & Lai, C. F. (2015). Defending against collaborative attacks by malicious nodes in MANETs: A cooperative bait detection approach. IEEE System Journal, 9(1), 65–75. doi:10.1109/JSYST.2013.2296197.
Katal, A., Wazid, M., Goudar, R. H., & Singh, D. P. (2013). A cluster based detection and prevention mechanism against novel datagram chunk dropping attack in MANET multimedia transmission. In Proceedings of IEEE conference on information and communication technologies (pp. 479–484).
Su, M. Y. (2011). Prevention of selective black hole attacks on mobile ad hoc networks through intrusion detection systems. Computer Communications, 34(1), 107–117. doi:10.1016/j.comcom.2010.08.007.
Mohanapriya, M., & Krishnamurthi, I. (2014). Modified DSR protocol for detection and removal of selective black hole attack in MANET. Computers and Electrical Engineering, 40, 530–538.
Lacey, T. H., Mills, R. F., Mullins, B. E., Raines, R. A., Oxley, M. E., & Rogers, S. K. (2012). RIPsec: Using reputation-based multilayer security to protect MANETs. Computer and Security, 31, 122–136.
Dokurer, S., Erten, Y. M., & Acar, C. E. (2007). Performance analysis of ad-hoc networks under black hole attacks. In Proceedings of the IEEE SoutheastCon.
The network simulator-ns-2. (2016). http://www.isi.edu/nsnam/ns/.
Acknowledgements
The first author would like to thank Department of Electronics and Information Technology (DEITY), Government of India, for supporting Ph.D. research scholar under Visvesvaraya Scheme. The authors would also like to thank the editor and anonymous reviewers for providing helpful comments in improving this manuscript.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Gurung, S., Chauhan, S. A dynamic threshold based approach for mitigating black-hole attack in MANET. Wireless Netw 24, 2957–2971 (2018). https://doi.org/10.1007/s11276-017-1514-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-017-1514-1