Abstract
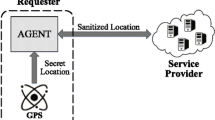
The popularity of mobile devices with positioning capability and Internet accessibility in recent years has led to a revolution in the Location-based services (LBSs) market. Unfortunately, without preserving the user’s location privacy, LBS providers can collect and log the accurate location data of the service users and provide them to third parties. Many mechanisms have been proposed to preserve the LBS user’s location privacy. These mechanisms provide a partial disclosure of the user’s location. While said mechanisms have had demonstrable effectiveness with snapshot queries, the shortcoming of supporting continuous queries is their main drawback. Geo-indistinguishability represents a formal notion of obfuscation-based location privacy which protects the user’s accurate location while allowing an adequate amount of information to be released to get the service with an accepted utility level. Despite its effectiveness and simplicity, geo-indistinguishability does not address the potential correlation of the subsequent locations reported within the continuous queries. In this paper, we investigate the effect of exploiting the correlation of the user’s obfuscated locations on the location privacy level. We propose an adaptive location preserving privacy mechanism that adjusts the amount of noise required to obfuscate the user’s location based on the correlation level with its previous obfuscated locations. The experiments show that adapting the noise based on the correlation level leads to a better performance by applying more noise to increase the location privacy level when required or by reducing the noise to improve the utility level.















Similar content being viewed by others
References
Mobile Location-Based Services Report. (2015). Retrieved 10 10, 2016. http://www.researchandmarkets.com/research/78bk4m/mobile.
Basagni, S., Chlamtac, I., & Syrotiuk, V. R. (2001). Location aware, dependable multicast for mobile ad hoc networks. Computer Networks, 36(5), 659–670.
Ayres, G., Mehmood, R., Mitchell, K., & Race, N. J. (2009). Localization to enhance security and services in Wi-Fi networks under privacy constraints. In International conference on communications infrastructure. Systems and applications in Europe. Springer. Berlin Heidelberg.
Al-Dhubhani, R., & Cazalas, J. (2017). Correlation analysis for geo-indistinguishability based continuous LBS queries. In 2nd international conference on anti-cybercrime (ICACC). IEEE.
Gruteser, M., & Grunwald, D. (2003). Anonymous usage of location-based services through spatial and temporal cloaking. In Proceedings of the 1st international conference on mobile systems, applications and services. San Francisco, CA, USA.
Mokbel, M., Chow, C.-Y., & Aref, W. (2006). The new casper: Query processing for location services without compromising privacy. In Proceedings of the 32nd international conference on very large data bases (VLDB ’06). Seoul, Korea.
Gedik, B., & Liu, L. (2008). Protecting location privacy with personalized k-anonymity: architecture and algorithms. IEEE Transactions on Mobile Computing, 7(1), 1–18.
Nguyen, N., Han, S., & Shin, M. (2015). URALP: Unreachable region aware location privacy against maximum movement boundary attack. International Journal of Distributed Sensor Networks, 11(8), 1–16.
Qiwei, L., Caimei, W., Yan, X., Huihua, X., Wenchao, H., & Xudong, G. (2017). Personalized privacy-preserving trajectory data publishing. Chinese Journal of Electronics, 26(2), 285.
Chow, C.-Y., & Mokbel, M. (2007). Enabling private continuous queries for revealed User locations. Advances in spatial and temporal databases (pp. 258–275). Berlin Heidelberg: Springer.
Bamba, B., Liu, L., Pesti, P., & Wang, T. (2008). Supporting anonymous location queries in mobile environments with privacygrid. In Proceedings of the 17th international conference on World Wide Web (WWW ‘08). New York, NY, USA.
Ma, C., Zhou, C., & Yang, S. (2015). A voronoi-based location privacy-preserving method for continuous query in LBS. International Journal of Distributed Sensor Networks, 11(3), 1–17.
Wang, Y., Xia, Y., Hou, J., Gao, S.-M., Nie, X., & Wang, Q. (2015). A fast privacy-preserving framework for continuous location-based queries in road networks. Journal of Network and Computer Applications, 53, 57–73.
Kido, H., Yanagisawa, Y., & Satoh, T. (2005). An anonymous communication technique using dummies for location-based services. In Proceedings of the international conference on pervasive services (ICPS ‘05).
Shankar, P., Ganapathy, V., & Iftode, L. (2009). Privately querying location-based services. In Proceedings of the 11th international conference on ubiquitous computing (UbiComp ’09). Orlando, Florida, USA.
Gao, S., Ma, J., Shi, W., & Zhan, G. (2015). LTPPM: a location and trajectory privacy protection. Wireless Communications and Mobile Computing, 15(1), 155–169.
Wei, W., Xu, F., & Li, Q. (2012). MobiShare: Flexible privacy-preserving location sharing in mobile online social networks. In Proceedings of IEEE INFOCOM. Orlando, FL.
Sun, Y., Zhang, B., Zhao, B., & Su, X. (2015). Mix-zones optimal deployment for protecting location. Peer-to-Peer Networking and Applications, 8(6), 1108–1121.
Palanisamy, B., & Liu, L. (2015). Attack-resilient mix-zones over road networks: Architecture and algorithms. IEEE Transactions on Mobile Computing, 14(3), 495–508.
Eckhoff, D., German, R., Sommer, C., Dressler, F., & Gansen, T. (2011). SlotSwap: Strong and affordable location privacy in intelligent transportation systems. IEEE Communications Magazine, 49(11), 000.
Chen, Y.-S., Lo, T.-T., Lee, C.-H., & Pang, A.-C. (2013). Efficient pseudonym changing schemes for location privacy protection in VANETs. In International Conference on Connected Vehicles and Expo (ICCVE).
Domenic, M. K., Wang, Y., Zhang, F., Memon, I., & Gustav, Y. H. (2013). Preserving users’ privacy for continuous query services in road networks. In 6th international conference on information management, innovation management and industrial engineering.
Memon, I., Ali, Q., Zubedi, A., & Mangi, F. A. (2016). DPMM: Dynamic pseudonym-based multiple mix-zones generation for mobile traveler. Multimedia Tools and Applications. doi:10.1007/s11042-016-4154-z.
Boualouache, A., & Moussaoui, S. (2017). Urban pseudonym changing strategy for location privacy in VANETs. International Journal of Ad Hoc and Ubiquitous Computing, 24(1–2), 49–64.
Shen, N., Yang, J., Yuan, K., Fu, C., & Jia, C. (2016). An efficient and privacy-preserving location sharing mechanism. Computer Standards and Interfaces, 44, 102–109.
Mascetti, S., Freni, D., Bettini, C., Sean Wang, X., & Jajodia, S. (2011). Privacy in geo-social networks: proximity notification with untrusted service providers and curious buddie. The International Journal on Very Large Data Bases, 20(4), 541–566.
Ghinita, G., Kalnis, P., Khoshgozaran, A., Shahabi, C., & Tan, K.-L. (2008). Private queries in location based services: anonymizers are not necessary. In Proceedings of the 2008 ACM SIGMOD international conference on Management of data (SIGMOD ‘08). New York, NY, USA.
Paulet, R., Golam Kaosar, M., Yi, X., & Bertino, E. (2014). Privacy-preserving and content-protecting location based queries. IEEE Transactions on Knowledge and Data Engineering, 26(5), 1200–1210.
Calderoni, L., Palmieri, P., & Maio, D. (2015). Location privacy without mutual trust: The spatial Bloom filter. Computer Communications, 68, 4–16.
Gutscher, A. (2006). Coordinate transformation-a solution for the privacy problem of location based services. In Proceedings of the 20th international conference on parallel and distributed processing (IPDPS ‘06). Rhodes Island, Greece.
Cheng, W. C., & Aritsugi, M. (2015). A user proprietary obfuscate system for positions sharing in location-aware social networks. Journal of Computer and Communications, 3(5), 7–20.
Yiu, M. L., Jensen, C. S., Møller, J., & Lu, H. (2011). Design and analysis of a ranking approach to private location-based services. ACM Transactions on Database Systems, 36(2), 10.
Kachore, V. A., Lakshmi, J., & Nandy, S. K. (2015). Location Obfuscation for Location Data Privacy. In IEEE world congress on services. New York, USA.
Skvortsov, P., Schembera, B., Dürr, F., & Rothermel, K. (2017). Optimized Secure Position Sharing with Non-trusted Servers. arXiv preprint arXiv, 1702.08377.
Shahid, A. R., Jeukeng, L., Zeng, W., Pissinou, N., Iyengar, S. S., Sahni, S., & Varela-Conover, M. (2017). PPVC: Privacy Preserving Voronoi Cell for location-based services. In International conference on computing, networking and communications (ICNC).
Zurbarán, M., Ávila, K., Wightman, P., & Fernández, M. (2015). Near-rand: Noise-based location obfuscation based on random neighboring points. IEEE Latin America Transactions, 13(11), 3661–3667.
Florian, M., Pieper, F., & Baumgart, I. (2016). Establishing location-privacy in decentralized long-distance geocast services. Ad Hoc Networks, 37, 110–121.
Soma, S. C., Hashem, T., Cheema, M. A., & Samrose, S. (2016). Trip planning queries with location privacy in spatial databases. World Wide Web, 20(2), 205–236.
Ngai, E. C. H., & Rodhe, I. (2013). On providing location privacy for mobile sinks in wireless sensor networks. Wireless Networks, 19(1), 115–130.
Wang, J., Wang, F., Cao, Z., Lin, F., & Wu, J. (2017). Sink location privacy protection under direction attack in wireless sensor networks. Wireless Networks, 23(2), 579–591.
Schlegel, R., Chow, C.-Y., Huang, Q., & Wong, D. S. (2015). User-Defined privacy grid system for continuous location-based services. IEEE Transactions on Mobile Computing, 14(10), 2158–2172.
Shokri, R., Theodorakopoulos, G., Troncoso, C., Hubaux, J.-P., & Boudec, J.-Y. L. (2012). Protecting location privacy: optimal strategy against localization attacks. In Proceedings of the 2012 ACM conference on Computer and communications security. New York, NY, USA.
Dwork, C. (2008). Differential privacy: A survey of results. In 5th International Conference, TAMC 2008. Xi’an, China.
Xiong, P., Zhu, T., Niu, W., & Li, G. (2015). A differentially private algorithm for location data release. Knowledge and Information Systems, 47(3), 647–669.
Andrés, M. E., E., N. B., Chatzikokolakis, K., & Palamidessi, C. (2013). Geo-indistinguishability: Differential privacy for location-based systems. In Proceedings of the 2013 ACM SIGSAC conference on computer & communications security. New York, NY, USA.
Dwork, C. (2006). Differential privacy. Proc. of ICALP. Berlin: Springer.
Theodorakopoulos, G. (2015). The Same-origin attack against location privacy. In Proceedings of the 14th ACM workshop on privacy in the electronic society.
Chatzikokolakis, K., Palamidessi, C., & Stronati, M. (2015). Constructing elastic distinguishability metrics for location privacy. In Proceedings on Privacy Enhancing Technologies.
Ghinita, G., Damiani, M. L., & Silvestri, C. (2009). Preventing velocity-based linkage attacks in location-aware applications. In Proceedings of the 17th ACM SIGSPATIAL international conference on advances in geographic information systems, ACM.
Talukder, N., & Ahamed, S. I. (2010). Preventing multi-query attack in location-based services. In Proceedings of the third ACM conference on Wireless network security.
Troja, E., & Bakiras, S. (2015). Efficient location privacy for moving clients in database-driven dynamic spectrum access. In 24th International Conference on Computer Communication and Networks (ICCCN). IEEE. Las Vegas.
Ying, J. J.-C., Lee, W.-C., Weng, T.-C., & Tseng, V. S. (2011). Semantic trajectory mining for location prediction. Proceedings of the 19th ACM SIGSPATIAL In International conference on advances in geographic information systems. New York.
Ma, Q., Zhang, S., Zhu, T., Liu, K., Zhang, L., He, W., & Liu, Y. (2016). PLP: Protecting location privacy against correlation analyze Attack in crowdsensing. In IEEE transactions on mobile computing, p. (99).
Chatzikokolakis, K., Palamidessi, C., & Stronati, M. (2014). A predictive differentially-private mechanism for mobility traces. In Proceedings of 14th international symposium, PETS 2014. Amsterdam, The Netherlands.
Zheng, Y., Xie, X., & Ma, W.-Y. (2010). Geolife: A collaborative social networking service among user, location and trajectory. IEEE Data Engineering Bulletin, vol. 33(2), pp. 32–40. Retrieved from https://www.microsoft.com/en-us/download/details.aspx?id=52367.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Al-Dhubhani, R., Cazalas, J.M. An adaptive geo-indistinguishability mechanism for continuous LBS queries. Wireless Netw 24, 3221–3239 (2018). https://doi.org/10.1007/s11276-017-1534-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-017-1534-x