Abstract
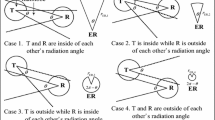
In this paper, we propose a game theoretic framework to analyze a passive eavesdropping attack in millimeter-wave-based wireless personal area networks. As the interaction between defenders and attackers in network security issues can be considered as a game, devices can be considered as players. Usually a player has insufficient information of other players such as strategies and payoffs especially in static situation. We assume that each player selects its strategy based on its belief about the information on opponents and the belief is known as a prior probability. The Bayesian game model is a relevant framework for this situation. It is assumed that each device is equipped with a directional antenna and knows the channel state. In the analysis, the exposure region (ER) that is determined by the antennas directions of players is considered and the ratio of ER for the total area of a network is calculated by using the probability density function of distance between players. The optimal strategies of two players, a transmitter and an eavesdropper, are derived in terms of Bayesian Nash equilibriums and payoffs for the players are computed for pure and mixed strategies in static situation. The analysis shows how the effects of using a directional antenna and the prior probability of transmitters belief are involved in the Nash equilibriums. Numerical results show the equilibriums and two players payoffs. Those values depend on several parameters such as beamwidth and prior probability of belief as well as its opponents strategies. It also shows the effect of directional antennas in the eavesdropping attack; the use of directional antenna seems to increase the transmitters payoff, while it seems to decrease the eavesdroppers payoff. The obtained results will provide the criteria for selecting appropriate strategy to transmitters when an eavesdropper exists in the network.









Similar content being viewed by others
References
Liang, X., & Xiao, Y. (2013). Game theory for network security. IEEE Communications Survey and Tutorials, 15(1), 472–486.
Roy, S., Ellis, C., Shiva, S., Dasgupta, D., Shandilya, V., & Qishi Wu, Q. (2010). A survey of game theory as applied to network security. In Proceedings of the 43rd Hawaii international conference on system sciences (pp. 1–10).
Manshaei, M. H., Zhu, Q., Alpcan, T., Basar, T., & Hubaux, J.-P. (2013). Game theory meets network security and privacy. Journal of ACM Computing Surveys, 45(3), 25.
Rao, N. S., Poole, S. W., Ma, C. Y., He, F., Zhuang, J., & Yau, D. K. (2016). Defense of cyber infrastructures against cyber-physical attacks using game-theoretic models. Risk Analysis, 36(4), 694–710.
Abdalzaher, M. S., Seddik, K., Elsabrouty, M., Muta, O., Furukawa, H., & Abdel-Rahman, A. (2016). Game theory meets wireless sensor networks security requirements and threats mitigation: A survey. Sensors, 16(7), 1003.
Mao, Y., Zhu, P., & Wei, G. (2013). A game theoretic model for wireless sensor networks with hidden-action attacks. International Journal of Distributed Sensor Networks, 9(8), 836056.
Shen, S., Huang, L., Fan, E., Hu, K., Liu, J., & Cao, Q. (2016). Trust dynamics in WSNs: An evolutionary game-theoretic approach. Journal of Sensors, 2016, 1–11.
Abdalzaher, M. S., Seddik, K., Muta, O., & Abdelrahman, A. (2016). Using Stackelberg game to enhance node protection in WSNs. In Proceedings of CCNC (pp. 853–856).
Shan, X., & Zhuang, J. (2013). Hybrid defensive resource allocations in the face of partially strategic attackers in a sequential defender–attacker game. European Journal of Operational Research, 228(1), 262–272.
Xu, J., & Zhuang, J. (2016). Modeling costly learning and counter-learning in a defender–attacker game with private defender information. Annals of Operations Research, 236(1), 271–289.
Ralescu, A. L. (1989). Concept learning from examples and counter examples. International Journal of Man-Machine Studies, 30, 329–354.
Korzhyk, D., Yin, Z., Kiekintveld, C., Conitzer, V., & Tambe, M. (2011). Stackelberg vs. Nash in security games: An extended investigation of interchangeability, equivalence, and uniqueness. Journal of Artificial Intelligence Research, 41, 297–327.
Saad, W., Han, Z., Basar, T., Debbah, M., & Hjorungnes, A. (2009). Coalitional games for distributed eavesdroppers cooperation in wireless networks. In Proceedings of valuetools (p. 66).
Dong, R., Liu, L., Liu, J., & Xu, X. (2009). Intrusion detection system based on payoff matrix for wireless sensor networks. In Proceedings of WGEC (pp. 3–6).
Shiva, S., Roy, S., Bedi, H., Dasgupta, D., & Wu, Q. (2010). A stochastic game model with imperfect information in cyber security. In Proceedings of ICIW (pp. 308–318).
Beckery, S., Jeff Seibert, J., David Zage, D., Cristina Nita-Rotaru C., & Radu Statey, R. (2011). Applying game theory to analyze attacks and defenses in virtual coordinate systems. In Proceedings of DSN (pp. 133–144).
Garnaev, A., Baykal-Gursoy, M., & Poor, H. V. (2014). Incorporating attack type uncertainty into network protection. IEEE Transactions on Information Forensics and Security, 9, 1278–1287.
Yuksel, M., Liu, X., & Erkip, E. (2011). A secure communication game with a relay helping the eavesdropper. IEEE Transactions on Information Forensics and Security, 6(3), 818–830.
Mukherjee, A., & Swindlehurst, A. L. (2013). Jamming games in the MIMO wiretap channel with an active eavesdropper. IEEE Transactions on Signal Processing, 61(1), 82–91.
Niu, H., Sun, L., Ito, M., & Sezaki, K. (2014). User cooperation analysis under eavesdropping attack: A game theory perspective. In Proceedings of PIMRC (pp. 139–144).
Zhu, Q., Saad, W., Han, Z., Poor, H. V. , & Basar, T. Q. (2011). Eavesdropping and jamming in next-generation wireless networks: A game-theoretic approach. In Proceedings of MILCOM (pp. 119–124).
Garnaev, A., & Trappe, W. (2017). Bargaining over the fair trade-off between secrecy and throughput in OFDM communications. IEEE Transactions on Information Forensics and Security, 12(1), 242–251.
Cao, B., Sun, X., Li, Y., Wang, C., & Mei, H. (2016). Understanding the impact of employing relay node on wireless networks. IEEE Transactions on Vehicular Technology, 66, 4287–4299.
Adu-Gyamf, D., Wang, Y., Zhang, F., Kamenyi, D. M., Memon, I., & Gustav, Y. H. (2013). Modeling the spreading behavior of passive worms in mobile social networks. In Proceedings of ICIMIMIE (pp. 380–383).
Khan, S., & Pathan, A.-S. K. (2013). Wireless networks and security issues, challenges and research trends. Heidelberg: Springer.
Garnaev A., & Trappe, W. (2014). Secret communication when the eavesdropper might be an active adversary. In Proceedings of MACOM, Lecture notes of computer science (Vol. 8715 , pp. 121–136).
Boonyakarn, P., Komolkiti, P., & Aswakul, C. (2011). Game-based analysis of eavesdropping defense strategy in WMN with directional antenna. In Proceedings of JCSSE (pp. 29–33).
Goel, V., Aggarwal, V., Yener, A., & Calderbank, A. R. (2010). Modeling location uncertainty for eavesdroppers: A secrecy graph approach. In Proceedings of ISIT (pp. 2627–2631).
Li, X., Xu, J., Dai, H.-N., Zhao, Q., Cheang, C. F., & Wang, Q. (2015). On modeling eavesdropping attacks in wireless networks. Journal of Computational Science, 11, 196–204.
Fan, L., Lei, X., Duong, T. Q., Elkashlan, M., & Karaglannidis, T. Q. (2014). Secure multiuser communications in multiple amplify-and-forward relay networks. IEEE Transactions on Communications, 62(9), 3299–3310.
Dai, H.-N., Wang, Q., Li, D., & Wong, R. C.-W. (2013). On eavesdropping attacks in wireless sensor networks with directional antennas. International Journal of Distributed Sensor Networks, 9, 760834.
Curiac, D.-I. (2016). Wireless sensor network security enhancement using directional antennas: State of the art and research challenges. Sensors, 16(488), 1–15.
Wang, Q., Hong-Ning Dai, H.-N., & Zhao, Q. (2013). Eavesdropping security in wireless ad hoc networks with directional antennas. In Proceedings of WOCC (pp. 687–692).
Zhou, X., Ganti, R. K., & Andrews, J. G. (2011). Secure wireless network connectivity with multi-antenna transmission. IEEE Transactions on Wireless Communications, 10(2), 425–430.
Zhu, J., Zou, Y., Wang, G., Yao, Y.-D., & Karagiannidis, G. K. (2016). On secrecy performance of antenna-selection-aided MIMO systems against eavesdropping. IEEE Transactions on Vehicular Technology, 65(1), 214–225.
Li, X., Wang, H., Dai, H.-N., Wang, Y., & Zhaol, Q. (2016). An analytical study on eavesdropping attacks in wireless nets of things. Mobile Information Systems, 2016, 1–10.
Valliappan, N. (2012). Antenna subset modulation for secure millimeter-wave wireless communication. M.S. dissertation, Chap 4, Science in Engineering, University of Texas, Austin, TX, USA.
Kim, M., Hwang, E., & Kim, J.-N. (2015). Analysis of eavesdropping attack in mmWave-based WPANs with directional antennas. Wireless Networks, 23(2), 355–369.
Kim, M., Kim, Y., & Lee, W. (2012). Performance analysis of directional CSMA/CA for IEEE 802.15.3c under saturation environments. ETRI Journal, 34(1), 24–34.
Kim, M., Kim, Y. S., & Lee, W. (2013). Analysis of directional neighbour discovery process in millimetre wave wireless personal area networks. IET Networks, 2(2), 92–101.
Kim, M., Kim, Y., & Lee, W. (2014). Resource allocation scheme for millimeter wave-based WPANs using directional antennas. ETRI Journal, 36(3), 385–395.
Kim, M. (2016). Multi-hop communications in directional CSMA/CA over mmWave WPANs. Wireless Communications and Mobile Computing, 16, 765–777.
Kim, M. (2017). Optimal packet length for throughput maximization in mmWave WPANs. International Journal of Electronics, 104, 1700–1714.
Fudenberg, D., & Tirole, J. (1991). Game theory. Cambridge: The MIT Press.
Mathworld. (2005). Square line picking. http://mathworld.wolfram.com/SquareLinePicking.html. Accessed October 1, 2017.
Acknowledgements
The author would like to thank the editor and the anonymous reviewers for their constructive and valuable comments. This work was supported by the Basic Science Research Program and Mid-career Research Program through NRF grant funded by the MEST (NRF-2016R1D1A1B03931037, NRF-2013R1A2A2A01067452) and supported by the Korea University Grant.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: Derivation of \(P_{\mathrm{ER}}\)
Let X be a random variable of the distance between two DEVs in the \(L \times L\) room. Then, it is known that the probability density function (PDF) of X, f(x), is given as follows [45]:
The value of \(P_{\mathrm{ER}}\) depends on antenna equipment of a DEV. We differentiate \(P_{\mathrm{ER}}\) either \(P_\mathrm{{{ER,d}}}\) or \(P_\mathrm{{{ER,o}}},\) when the DEV is equipped with a directional and an omni-directional antenna, respectively. Then, they are given by
respectively, where \(r_i\) in Eq. (17) is ER radius given by \(r_i=\mathrm{{min}}(r_{{\mathrm{ER}},i},\sqrt{2}L).\) The ER of a DEV depends on the antenna directions of the DEV and other DEV that emits the signal and there are four different ER radii \(\{ r_{{\mathrm{ER}},i}\}_{i=1}^{4}\) which are given by
where \(G_\mathrm{{{TM}}}(G_\mathrm{{{TS}}})\) and \(G_\mathrm{{{RM}}}(G_\mathrm{{{RS}}})\) are the antenna gains of the main lobe (side lobe) of a transmitter and a receiver, respectively. \(P_\mathrm{{{R}}}\) is the receiver sensitivity corresponding to the base data rate of 25.8 Mbps, which is \(-70\) dB in this case. Equation (18) is the radius of ER when an omni-directional antenna is equipped on a DEV, which is given by
where \(G_\mathrm{{{0}}}\) is the main lobe antenna gain obtained for \(\theta =2 \pi .\) During the derivation of Eqs. (19)–(20), the path loss model of IEEE 802.15.3c were used. For the detailed derivation of the ER radii, see [39].
Appendix 2: Proof of Theorem 2
-
(a)
For the strategies, the expected payoffs of tx and ev are given as follows:
$$\begin{aligned} \left\{ \begin{array}{ll} E_{\mathrm{e}}(s_{\mathrm{e,1}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}) = P_{\mathrm{ER}}p_{\mathrm{e}}( w_{\mathrm{e}} p_{\mathrm{ch}} p_{\mathrm{tx}}- c_{\mathrm{e}}), \\ E_{\mathrm{e}}(s_\mathrm{{{e,2}}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}) = w_{\mathrm{e}}p_{\mathrm{ch}}p_{\mathrm{tx}} P_{\mathrm{ER}} p_{\mathrm{e}}- c_{\mathrm{e}}, \\ E_{\mathrm{e}}(s_{\mathrm{e,1}}^{\mathrm{m}},s_\mathrm{{{t,2}}}^{\mathrm{m}}) = -c_{\mathrm{e}}(1-p_{\mathrm{ch}} p_{\mathrm{tx}}) P_{\mathrm{ER}} p_{\mathrm{e}}, \\ E_{\mathrm{e}}(s_\mathrm{{{e,2}}}^{\mathrm{m}},s_\mathrm{{{t,2}}}^{\mathrm{m}}) = -c_{\mathrm{e}}, {\hbox { }} E_{\mathrm{e}}(s_{\mathrm{e,3}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}) = E_{\mathrm{e}}(s_{\mathrm{e,3}}^{\mathrm{m}},s_\mathrm{{{t,2}}}^{\mathrm{m}}) = 0, \end{array} \right. \end{aligned}$$and
$$\begin{aligned} \left\{ \begin{array}{l l} E_{\mathrm{t}}(s_{\mathrm{e,1}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}) = p_{\mathrm{ch}}(w_{\mathrm{t}}-c_{\mathrm{t}}-2 w_{\mathrm{t}}p_{\mathrm{on}}P_{\mathrm{ER}} p_{\mathrm{e}}), \\ E_{\mathrm{t}}(s_\mathrm{{{e,2}}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}) = p_{\mathrm{ch}}(w_{\mathrm{t}}- c_{\mathrm{t}}-2 w_{\mathrm{t}}P_{\mathrm{ER}} p_{\mathrm{e}}), \\ E_{\mathrm{t}}(s_{\mathrm{e,3}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}) = p_{\mathrm{ch}} (w_{\mathrm{t}}- c_{\mathrm{t}}), \\ E_{\mathrm{t}}(s_{\mathrm{e,1}}^{\mathrm{m}},s_\mathrm{{{t,2}}}^{\mathrm{m}}) = E_{\mathrm{t}}(s_\mathrm{{{e,2}}}^{\mathrm{m}},s_\mathrm{{{t,2}}}^{\mathrm{m}}) = E_{\mathrm{t}}(s_{\mathrm{e,3}}^{\mathrm{m}},s_\mathrm{{{t,2}}}^{\mathrm{m}})=0, \end{array} \right. \end{aligned}$$(21)respectively. To find BNEs, we consider the following cases:
-
(i)
For tx, if tx selects \(s_{\mathrm{t,1}}^{\mathrm{m}},\)ev must select the strategy which gives maximum the expected payoff. \(E_{\mathrm{e}}(s_{\mathrm{e,1}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}) \ge E_{\mathrm{e}}(s_\mathrm{{{e,2}}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}})\) holds always, while
$$\begin{aligned} \left\{ \begin{array}{l l} E_{\mathrm{e}}(s_{\mathrm{e,1}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}) \ge E_{\mathrm{e}}(s_{\mathrm{e,3}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}), {\hbox { if }} w_{\mathrm{e}} \ge c_{\mathrm{e}}/p_{\mathrm{ch}} p_{\mathrm{tx}} \\ E_{\mathrm{e}}(s_{\mathrm{e,1}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}})< E_{\mathrm{e}}(s_{\mathrm{e,3}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}}), {\hbox { if }} w_{\mathrm{e}} < c_{\mathrm{e}}/p_{\mathrm{ch}} p_{\mathrm{tx}} \end{array} \right. \end{aligned}$$(22)holds. Therefore, ev selects \(s_{\mathrm{e,1}}^{\mathrm{m}}\) if \(w_{\mathrm{e}} \ge c_{\mathrm{e}}/p_{\mathrm{ch}} p_{\mathrm{tx}},\) while it selects \(s_{\mathrm{e,3}}^{\mathrm{m}}\) if \(w_{\mathrm{e}} < c_{\mathrm{e}}/p_{\mathrm{ch}} p_{\mathrm{tx}}.\) If tx selects \(s_\mathrm{{{t,2}}}^{\mathrm{p}},\)ev must select \(s_{\mathrm{e,3}}^{\mathrm{p}}.\) Therefore, if \(w_{\mathrm{e}} < c_{\mathrm{e}}/p_{\mathrm{ch}} p_{\mathrm{tx}},\)\(s_{\mathrm{e,3}}^{\mathrm{m}}\) is the dominant strategy, while if \(w_{\mathrm{e}} \ge c_{\mathrm{e}}/p_{\mathrm{ch}} p_{\mathrm{tx}},\) there is no dominant strategy for ev.
-
(ii)
For ev, if ev selects \(s_{\mathrm{e,1}}^{\mathrm{m}},\)tx selects \(s_{\mathrm{t,1}}^{\mathrm{m}}\) if \(w_{\mathrm{t}} \ge c_{\mathrm{t}}/(1-2p_{\mathrm{on}}P_{\mathrm{ER}} p_{\mathrm{e}}).\) Otherwise, it selects \(s_\mathrm{{{t,2}}}^{\mathrm{m}}.\) If ev selects \(s_\mathrm{{{e,2}}}^{\mathrm{m}},\)tx selects \(s_\mathrm{{{t,2}}}^{\mathrm{m}}\) since \(w_{\mathrm{t}} < c_{\mathrm{t}}/(1-2P_{\mathrm{ER}} p_{\mathrm{e}}).\) Finally, if ev selects \(s_{\mathrm{e,3}}^{\mathrm{m}},\)tx selects \(s_{\mathrm{t,1}}^{\mathrm{m}}\) always since \(w_{\mathrm{t}} > c_{\mathrm{t}}.\) Therefore, there is no dominant strategy for tx if \(c_{\mathrm{t}}/(1-2p_{\mathrm{on}}P_{\mathrm{ER}}p_{\mathrm{e}}) \le w_{\mathrm{t}} < c_{\mathrm{t}}/(1-2P_{\mathrm{ER}} p_{\mathrm{e}}).\)\(s_{\mathrm{t,1}}^{\mathrm{p}}\) is the dominant strategy if \(w_{\mathrm{t}} \ge c_{\mathrm{t}}/(1-2P_{\mathrm{ER}} p_{\mathrm{e}}).\)
By (i)-(ii), we conclude that \([s_{\mathrm{e,1}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}} ]\) is a BNE if \(c_{\mathrm{t}}/(1-2p_{\mathrm{on}}P_{\mathrm{ER}}p_{\mathrm{e}}) \le w_{\mathrm{t}} < c_{\mathrm{t}}/(1-2P_{\mathrm{ER}} p_{\mathrm{e}})\) and \(w_{\mathrm{e}} \ge c_{\mathrm{e}}/p_{\mathrm{ch}}p_{\mathrm{tx}},\)\([s_{\mathrm{e,3}}^{\mathrm{m}},s_{\mathrm{t,1}}^{\mathrm{m}} ]\) is a BNE if \(w_{\mathrm{t}} < c_{\mathrm{t}}/(1-2P_{\mathrm{ER}} p_{\mathrm{e}})\) and \(w_{\mathrm{e}} < c_{\mathrm{e}}/p_{\mathrm{ch}}p_{\mathrm{tx}}.\)
-
(b)
Therefore, no BNE exists if \(w_{\mathrm{t}} < c_{\mathrm{t}}/(1-2p_{\mathrm{on}}P_{\mathrm{ER}}p_{\mathrm{e}})\) and \(w_{\mathrm{e}} \ge c_{\mathrm{e}}/p_{\mathrm{ch}}p_{\mathrm{tx}}.\)
-
(i)
Appendix 3: Proof of Theorem 3
Since \(E_{\mathrm{t}}\) and \(E_{\mathrm{e}}\) are computed as
and
respectively, the results follow. Here A is the set of environments of a tx-ev pair where the players’ payoffs can be considered, which is given as Eq. (4) in Sect. 3.
Rights and permissions
About this article
Cite this article
Kim, M. Game theoretic approach of eavesdropping attack in millimeter-wave-based WPANs with directional antennas. Wireless Netw 25, 3205–3222 (2019). https://doi.org/10.1007/s11276-018-1713-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-018-1713-4