Abstract
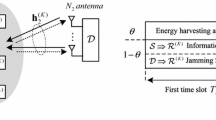
This paper studies the secrecy performance of a wireless energy harvesting system in which a source connected to wireless backhaul links sends information to a destination via an untrusted relay that not only helps the overall commutation but also overhears the sources confidential information. The secrecy capacity is created by using destination-assisted jamming signals. The jamming provides additional energy to the relay. To analyze the secrecy performance of the proposed system, we derived analytical expressions for the secrecy outage probability (SOP) and the average secrecy capacity, and the high-power approximations for the SOP. The accuracy of the calculations is verified by Monte Carlo simulations. Numerical results provide useful insight into the effects of the system parameters, such as the failure probability of unreliable backhaul links, the transmit powers, the power-splitting ratio, and the locations of the relay, on the secrecy performance.






Similar content being viewed by others
References
Truong, T., Nguyen, M., Kundu, C., & Nguyen, L. D. (2018). Secure cognitive radio networks with source selection and unreliable backhaul connections. IET Communications, 12, 1771–1777.
Nguyen, H. T., Zhang, J., Yang, N., Duong, T. Q., & Hwang, W. (2017). Secure cooperative single carrier systems under unreliable backhaul and dense networks impact. IEEE Access, 5, 18310–18324.
Kim, K. J., Yeoh, P. L., Orlik, P. V., & Poor, H. V. (2016). Secrecy performance of finite-sized cooperative single carrier systems with unreliable backhaul connections. IEEE Transaction on Signal Processing, 64(17), 4403–4416.
Ding, Z., Perlaza, S. M., Esnaola, I., & Poor, H. V. (2014). Power allocation strategies in energy harvesting wireless cooperative networks. IEEE Transaction on Wireless Commun., 13(2), 846–860.
Nasir, A., Zhou, X., Durrani, S., & Kennedy, R. (2015). Wireless-powered relays in cooperative communications: Time-switching relaying protocols and throughput analysis. IEEE Transactions on Communications, 63(5), 1607–1622.
Hu, L., et al. (2018). Cooperative jamming for physical layer security enhancement in internet of things. IEEE Internet of Things Journal, 5(1), 219–228.
Liu, Y., Chen, H. H., & Wang, L. (2017). Physical layer security for next generation wireless networks: Theories, technologies, and challenges. IEEE Communications Surveys and Tutorials, 19(1), 347–376.
Liu, L., Zhang, R., & Chua, K. C. (2014). Secrecy wireless information and power transfer with MISO beamforming. IEEE Transactions on Signal Processing, 62, 1850–1863.
Zhang, H., Li, C., Huang, Y., & Yang, L. (2015). Secure beamforming for SWIPT in multiuser MISO broadcast channel with confidential messages. IEEE Communications Letters, 19, 1347–1350.
Hoang, T. M., Duong, T. Q., Vo, N. S., & Kundu, C. (2017). Physical layer security in cooperative energy harvesting networks with a Friendly Jammer. IEEE Wireless Communications Letters, 6, 174–177.
Kalamkar, S. S., & Banerjee, A. (2017). Secure communication via a wireless energy harvesting untrusted relay. IEEE Transactions on Vehicular Technology, 66(3), 2199–2213.
Guo, J., Zhao, N., Yu, F. R., Liu, X., & Leung, V. C. M. (2017). Exploiting adversarial jamming signals for energy harvesting in interference networks. IEEE Transactions on Wireless Communications, 16, 1267–1280.
Zhao, N., Cao, Y., Yu, F. R., Chen, Y., Jin, M., & Leung, V. C. M. (2018). Artificial noise assisted secure interference networks with wireless power transfer. IEEE Transactions on Vehicular Technology, 67, 1087–1098.
Yin, C., Nguyen, H. T., Kundu, C., Kaleem, Z., Garcia-Palacios, E., & Duong, T. Q. (2018). Secure energy harvesting relay networks with unreliable Backhaul connections. IEEE Access, 6, 12074–12084.
Zhou, X., Zhang, R., & Ho, C. K. (2013). Wireless information and power transfer: Architecture design and rate-energy tradeoff. IEEE Transactions on Communications, 61, 4754–4767.
Gradshteyn, I. S., & Ryzhik, I. M. (2007). Table of integrals, series, and products (7th ed.). New York: Academic Press.
Cao, Y., et al. (2018). Optimization or alignment: Secure primary transmission assisted by secondary networks. IEEE Journal on Selected Areas in Communications, 36, 905–917.
Khafagy, M. G., Ismail, A., Alouini, M. S., & Assa, S. (2015). Efficient cooperative protocols for full duplex relaying over Nakagami-m fading channels. IEEE Transactions on Wireless Communications, 14(6), 3456–3470.
Olver, F. W. J., Lozier, D. W., Boisvert, R. F., & Clark, C. W. (2010). NIST handbook of mathematical functions. Cambridge: Cambridge University Press.
Zhu, G., Zhong, C., Suraweera, H. A., Zhang, Z., Yuen, C., & Yin, R. (2014). Ergodic capacity comparison of different relay precoding schemes in dual-hop AF systems with co-Channel interferer. IEEE Transactions on Communications, 62(7), 2314–2328.
Mathai, A. M., & Saxena, R. K. (1978). The H-function with applications in statistics and other disciplines. New York: Wiley.
Acknowledgments
This work was supported by the 2019 Research Fund of University of Ulsan.
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
1.1 Appendix 1
The value of the function \(\varXi (y)\) can be described as
Using (49), we can rewrite the SOP in (19) as
Substituting the CDF of X given by (16) and PDF of Y given by \(f(m_2,\lambda _2;t)\), we can derive the analytical expression for the SOP as in (20).
1.2 Appendix 2
We first study the trend of the element g(Y) in \({\mathcal {J}}_2\). It can be seen that \(\mathop {\lim }\nolimits _{\begin{array}{c} (P_T,P_D) \rightarrow (\infty ,\infty ) \\ {\bar{y}}_p< Y < \infty \end{array}} g\left( Y \right) \rightarrow 0\), hence, we can use the approximating function of the CDF of X, \(F_X^ \approx ( t )\) instead of using the CDF of X to simplify the calculation of \({\mathcal {J}}_2\). Using the fact \(e^t=\sum _{n=0}^{+\infty }\frac{t^n}{n!}\) and (14), \(F_X ( t )\) as \(t \rightarrow 0\) can be approximated by \(F_X^ \approx ( t )\) as follows.
1.2.1 The expression for \({\mathcal {J}}_2\) in the case of \(p=1\)
Substituting the PDF of Y given by \(f(m_2,\lambda _2;t)\) and \(F_X^\approx (t)\) given by (51), \({{\mathcal {J}}}_2^{p = 1}\) can be calculated as
With the help of [16, Eqs. (3.351.3) and (3.351.4)], \({\mathcal {J}}_2^{p = 1}\) can be expressed as in (24).
1.2.2 The expression for \({\mathcal {J}}_2\) in the case of \(p<1\)
Substituting the PDF of Y given by \(f(m_2,\lambda _2;t)\) and \(F_X^\approx (t)\) given by (51), \({\mathcal {J}}_2^{p < 1}\) can be calculated as
1.3 Appendix 3
The CDF of \(\gamma _D\) can be calculated as
Substituting the CDF of Y given by \(F(m_2,\lambda _2;t)\) and CDF of X given by (15), we have
With the help of [16, Eq. (3.471.9)], we can obtain (35).
1.4 Appendix 4
Substituting the CDF of \(\gamma _D\) into (36), \(C_D\) can be obtained as in (37) where \({\mathcal {I}}_1 \left( \alpha ,\beta , v,\mu \right)\) is calculated by
Using the fact that \(\frac{{d{K_v}\left( x \right) }}{{dx}} = - \frac{1}{2}\left( {{K_{v - 1}}\left( x \right) + {K_{v + 1}}\left( x \right) } \right)\), \({{\mathcal {I}}_2}\left( {\gamma ;\alpha ,\beta ,v,\mu } \right)\) can be calculated as
By expressing \(\ln \left( {1 + \gamma } \right)\) in (58) by \(H_{2,2}^{1,2}\left[ {\gamma | \begin{array}{c} (1,1),(1,1)\\ (1,1),(0,1) \end{array}} \right]\) and \({K_v}\left( {2\sqrt{\mu \gamma } } \right)\) in (58) by \(\frac{1}{2}H_{2,0}^{0,2}\left( \mu \gamma |{(v/2,1),(v/2,1)} \right)\), and using [21, Eq. (2.6.2)], we can obtain (38). Then, Proposition 4 can be proved.
1.5 Appendix 5
Substituting (40) in to (39), \(C_R\) can be expressed as in (43) where \({\mathcal {I}}_3 (\mu _2)\) is calculated by
For the case of \(\mu _2 \ne 1\), we can decompose \({{\mathcal {I}}_4}\left( {{\mu _2};\gamma } \right)\) as
For the case of \(\mu _2=1\), we can decompose \({{\mathcal {I}}_4}\left( {{\mu _2};\gamma } \right)\) as
Substituting (60) and (61) into (59), and after some manipulation, we can prove Proposition 7.
Rights and permissions
About this article
Cite this article
Tuan, V., Kong, H.Y. Secure communication via an untrusted relay with unreliable backhaul connections. Wireless Netw 25, 3453–3465 (2019). https://doi.org/10.1007/s11276-019-01940-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-019-01940-9