Abstract
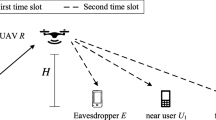
This article addresses the problem of secure communication in an unmanned aerial vehicle (UAV)-aided wireless communication system in which a source sends confidential messages to a destination via an untrusted UAV mounted with a miniaturized energy-harvesting transceiver. The UAV can overhear the source’s confidential messages. To create a positive secrecy rate, the destination sends jamming signals during the communication. We aim to maximize the achievable secrecy rate for two scenarios: security-on-demand UAV (SoD-UAV), where the UAV can modify its trajectory and power-splitting (PS) ratio to serve the secure communication, and non-security-on-demand UAV (nSoD-UAV), where the UAV only forwards the source’s messages. For the nSoD-UAV, we optimize the transmit powers at the source and the destination for a given UAV’s trajectory and given PS ratios. For the SoD-UAV, the UAV’s trajectory, the PS ratios and the transmit powers are jointly optimized. Due to the non-convex optimization problems, we use successive convex optimization and block coordinate descent methods to find efficient approximate solutions. Numerical results verify that the achievable secrecy rate is significantly improved using the proposed algorithms.













Similar content being viewed by others
References
Xu, J., Zeng, Y., & Zhang, R. (2018). UAV-enabled wireless power transfer: Trajectory design and energy optimization. IEEE Transactions on Wireless Communications, 17(8), 5092–5106.
Sun, J., Wang, Z., & Huang, Q. (2019). Cyclical NOMA based UAV-enabled wireless network. IEEE Access, 7, 4248–4259.
Cho, S., Lee, K., Kang, B., Koo, K., & Joe, I. (2018). Weighted harvest-then-transmit: UAV-enabled wireless powered communication networks. IEEE Access, 6, 72212–72224.
Feng, Y., Yan, S., Yang, Z., Yang, N., & Yuan, J. (2018). User and relay selection with artificial noise to enhance physical layer security. IEEE Transactions on Vehicular Technology, 67(11), 10906–10920.
Liu, W., Zhou, X., Durrani, S., & Popovski, P. (2016). Secure communication with a wireless-powered friendly Jammer. IEEE Transactions on Wireless Communications, 15(1), 401–415.
Zhu, F., & Yao, M. (2016). Improving physical-layer security for CRNs Using SINR-based cooperative beamforming. IEEE Transactions on Vehicular Technology, 65(3), 1835–1841.
Zhang, W., Chen, J., Kuo, Y., & Zhou, Y. (2019). Artificial-noise-aided optimal beamforming in layered physical layer security. IEEE Communications Letters, 23(1), 72–75.
Zhong, C., Yao, J. & Xu, J. (2019). Secure UAV communication with cooperative jamming and trajectory control. IEEE Communications Letters (accepted).
Cai, Y., Cui, F., Shi, Q., Zhao, M., & Li, G. Y. (2018). Dual-UAV-enabled secure communications: Joint trajectory design and user scheduling. IEEE Journal on Selected Areas in Communication, 36(9), 1972–1985.
Cui, M., Zhang, G., Wu, Q., & Ng, D. W. K. (2018). Robust trajectory and transmit power design for secure UAV communications. IEEE Transactions on Vehicular Technology, 67(9), 9042–9046.
Liu, L., Zhang, R., & Chua, K. C. (2014). Secrecy wireless information and power transfer With MISO beamforming. IEEE Transactions on Signal Processing, 62(7), 1850–1863.
Zhang, H., Li, C., Huang, Y., & Yang, L. (2016). Secure beamforming for SWIPT in multiuser MISO broadcast channel with confidential messages. IEEE Communications Letters, 19(8), 1347–1350.
Kalamkar, S. S., & Banerjee, A. (2017). Secure communication via a wireless energy harvesting untrusted relay. IEEE Transactions on Vehicular Technology, 66(3), 2199–2213.
Boyd, S., & Vandenberghe, L. (2004). Convex optimization. Cambridge: Cambridge Univ. Press.
Chong, E. K. P., & Zak, S. H. (2004). An introduction to optimization (2nd ed.). Hoboken: Wiley.
Acknowledgements
This work was supported by the Priority Research Centers Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (2019R1A6A1A03032988).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendices
1.1 Appendix 1
The convexity of \(f_1(t_1,t_2)\) is confirmed through its Hessian matrix. By defining \(T=(t_1+a_1)(t_2+a_2)\), the first-order derivatives of \(f_1(t_1,t_2)\) are expressed by
where
Next, the second-order derivatives of \(f_1(t_1,t_2)\) are expressed by
Then the Hessian matrix is given by
Let \(\mathbf{u }=\left[ u_1,u_2\right] ,\mathbf{u }\in {\mathbb {R}}^2\), and \(J=\left( \tfrac{1}{T^2}-\tfrac{1}{\left( T+a_0\right) }^2\right) ^{-1}\mathbf{u }H\mathbf{u }^\top \). Substituting (43) into J, we have
Using the fact that \(\tfrac{T}{2}\leqslant \tfrac{T\left( T+a_0\right) }{2T+a_0}\leqslant {T}\) as \(t_1>0\) and \(t_2>0\), and substituting (38) and (39) into (44), we have
Using (45), we show that H is a positive definite matrix; hence, Theorem 1 is proved.
1.2 Appendix 2
1.2.1 Convexity of \(f_2\left( \theta \right) \)
The first-order derivative of \(f_2\left( \theta \right) \) is expressed by
where \(f_4\left( \theta \right) =\left( a_0+\tfrac{a_1}{1-\theta }+\tfrac{a_2}{\theta }\right) ^{-1}-\left( \tfrac{a_1}{1-\theta }+\tfrac{a_2}{\theta }\right) ^{-1}\).
Next, the second-order derivative of \(f_2\left( \theta \right) \) is expressed by
After some manipulation, (47) can be written as
where
Since \(f_4(\theta )<0,f_5(\theta )>0\) and \(f_6(\theta )>0,\forall \theta \in (0,1)\), we can confirm that \(\tfrac{\partial ^2}{\left( \partial \theta \right) ^2}f_2\left( \theta \right) <0,\forall \theta \in \left( 0,1\right) \). Therefore, \(f_2\left( \theta \right) \) is a concave function with respect to \(\theta \in \left( 0,1\right) \).
1.2.2 Convexity of \(f_3\left( \theta \right) \)
It is easy to obtain the second-order derivative of \(f_3\left( \theta \right) \) as
Since \(\tfrac{\partial ^2}{\left( \partial \theta \right) ^2}f_3\left( \theta \right) <0,\forall \theta \in \left( 0,1\right) \); hence, \(f_3\left( \theta \right) \) is a concave function with respect to \(\theta \in \left( 0,1\right) \).
Rights and permissions
About this article
Cite this article
Tuan, V.P., Sang, N.Q. & Kong, H.Y. Secrecy capacity maximization for untrusted UAV-assisted cooperative communications with wireless information and power transfer. Wireless Netw 26, 2999–3010 (2020). https://doi.org/10.1007/s11276-020-02255-w
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-020-02255-w