Abstract
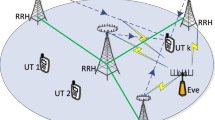
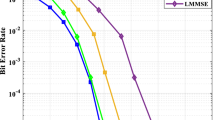
This paper investigates the secrecy performance of the Cell-Free massive multiple-input multiple-output network with finite resolution analog-to-digital converters at the access points (APs) and users in presence of an active eavesdropper. Using the additive quantization noise model, the uplink minimum mean squared error channel estimation and downlink data precoding are respectively operated. Specifically, the lower bound on the achievable ergodic rate and upper bound for the information leakage to the eavesdropper are theoretically derived in details. Thereby, the closed-form expression for the achievable ergodic secrecy rate is accordingly obtained with respect to the number of APs, number of each APs antenna, number of users, pilot and data transmission power and quantization bits, etc. In addition, the asymptotic approximation for the ergodic secrecy rate has been presented. Moreover, the path-following power control algorithm has been proposed aiming at maximizing the secrecy rate subject to both power and achievable rate constraints. Finally, extensive simulations are provided to corroborate the theoretical analytical results and the validity of the proposed power allocation scheme.






Similar content being viewed by others
References
Marzetta, T.L., . (2015). Massive MIMO: an introduction. Bell Labs Tech. J., 20, 11–22.
Larsson, E. G., Edfors, O., Tufvesson, F., et al. (2014). Massive MIMO for next generation wireless systems. IEEE Commun. Mag., 52(2), 186–195.
Marzetta, T. L. (2010). Noncooperative cellular wireless with unlimited numbers of base station antennas. IEEE Trans. Wireless Commun., 9(11), 3590–3600.
Bjornson, E., Larsson, E., & G., Marzetta, T, L. . (2016). Massive MIMO: ten myths and one critical question. IEEE Commun. Mag., 54(2), 114–123.
Bogale, T. E., & Le, L. B. (2016). Massive MIMO and mmWave for 5G Wireless HetNet: potential benefits and challenges. IEEE Veh. Technol. Mag., 11(1), 64–75.
Zhang, J., Wen, C., K., Jin, S., , et al. (2013). On capacity of large-scale MIMO multiple access channels with distributed sets of correlated antennas. IEEE J. Selected Areas Commun., 31(2), 133–148.
Hosseini, K., Yu, W., & Adve, R. S. (2014). Large-scale MIMO versus network MIMO for multicell interference mitigation. IEEE J. Selected Top. Signal Process., 8(5), 930–941.
Ngo, H. Q., Ashikhmin, A., Yang, H., et al. (2017). Cell-free massive MIMO versus small cells. IEEE Trans. Wireless Commun., 16(3), 1834–1850.
Ngo, H. Q., Tran, L., Duong, T. Q., et al. (2018). On the total energy efficiency of cell-free massive MIMO. IEEE Trans. Green Commun. Netw., 2(1), 25–39.
Interdonato, G., Ngo, H. Q., Frenger, P., et al. (2019). Downlink training in cell-free massive MIMO: a blessing in disguise. IEEE Trans. Wireless Commun., 18(11), 5153–5169.
Nguyen, T. K., Nguyen, H. H., & Tuan, H. D. (2020). Max–min QoS power control in generalized cell-free massive MIMO–NOMA with optimal backhaul combining. IEEE Trans. Veh. Technol., 69(10), 10949–10964.
Nguyen, L. D., Duong, T. Q., Ngo, H. Q., et al. (2017). Energy efficiency in cell-free massive MIMO with zero-forcing precoding design. IEEE Commun. Lett., 21(8), 1871–1874.
Björnson, E., Sanguinetti, L. (2020). Making cell-free massive MIMO competitive with MMSE processing and centralized implementation. IEEE Trans. Wireless Commun., 19(1), 77–90.
Doan, T. X., Ngo, H. Q., Duong, T. Q., et al. (2017). On the performance of multigroup multicast cell-free massive MIMO. IEEE Commun. Lett., 21(12), 2642–2645.
Papazafeiropoulos, A., Kourtessis, P., Renzo, M. D., et al. (2020). Performance analysis of cell-free massive MIMO systems: a stochastic geometry approach. IEEE Trans. Veh. Technol., 69(4), 3523–3537.
Zhang, Z.; & Dai, L.: (2020). Capacity improvement in wideband reconfigurable intelligent surface-aided cell-free network. In IEEE 21st International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), pp. 1–5.
Vu, T. T., Ngo, D. T., Tran, N. H., et al. (2020). Cell-free massive MIMO for wireless federated learning. IEEE Trans. Wireless Commun., 19(10), 6377–6392.
Yang, N., Wang, L., Geraci, G., et al. (2015). Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag., 53(4), 20–27.
Bloch, M., Barros, J., Rodrigues, M. R. D., et al. (2008). Wireless information-theoretic security. IEEE Trans. Inf. Theory, 54(6), 2515–2534.
Yener, A., & Ulukus, S. (2015). Wireless physical-layer security: lessons learned from information theory. Proc. IEEE, 103(10), 1814–1825.
Mukherjee, A., Fakoorian, S. A. A., Huang, J., et al. (2014). Principles of physical layer security in multiuser wireless networks: a survey. IEEE Commun. Surv. Tutorials, 16(3), 1550–1573.
Hong, Y. P., Lan, P., & Kuo, C. J. (2013). Enhancing physical-layer secrecy in multiantenna wireless systems: an overview of signal processing approaches. IEEE Signal Process. Mag., 30(5), 29–40.
Trappe, W. (2015). The challenges facing physical layer security. IEEE Commun. Mag., 53(6), 16–20.
Wu, Y., Khisti, A., Xiao, C., et al. (2018). A survey of physical layer security techniques for 5G wireless networks and challenges ahead. IEEE J. Selected Areas Commun., 36(4), 679–695.
Zhu, J., Schober, R., Bhargava, V.K. (2014). Secure transmission in multicell massive MIMO systems. IEEE Trans. Wireless Commun., 13(9), 4766–4781.
Zhu, J., Schober, R., Bhargava, V.K. (2016). Linear precoding of data and artificial noise in secure massive MIMO systems. IEEE Trans. Wireless Commun., 15(3), 2245–2261.
Wu, Y., Schober, R., Ng, D.W.K. et al. (2016). Secure massive MIMO transmission with an active eavesdropper. IEEE Trans. Inf. Theory, 62(7), 3880–3900.
Kapetanovic, D., Zheng, G., & Rusek, F. (2015). Physical layer security for massive MIMO: an overview on passive eavesdropping and active attacks. IEEE Commun. Mag., 53(6), 21–27.
Zhang, X., Guo, D., Guo, K., et al. (2018). Secure performance analysis and detection of pilot attack in massive multiple-input multiple-output system. Int. J. Distrib. Sensor Netw., 5, 1–12.
Zhang, X., Guo, D., Yang, K., et al. (2018). Secure downlink transmission with finite resolution analog beamforming in massive multiple-input multiple-output system. Int. J. Distrib. Sensor Netw., 9, 1–13.
Zhu, J., Xu, W., & Wang, N. (2017). Secure massive MIMO systems with limited RF chains. IEEE Trans. Veh. Technol., 66(6), 5455–5460.
Guo, K.; Guo, Y.; & Ascheid, G. (2015). Distributed antennas aided secure communication in MU-massive-MIMO with QoS guarantee. In Proceeding of 2015 IEEE 82nd Vehicular Technology Conference, pp. 1–7.
Zhang, X., Guo, D., An, K., et al. (2020). Secure transmission and power allocation in multiuser distributed massive MIMO systems. Wireless Netw., 26, 941–954.
Guo, K., Guo, Y., & Ascheid, G. (2016). Security-constrained power allocation in MU-massive-MIMO with distributed antennas. IEEE Trans. Wireless Commun., 15(12), 8139–8153.
Hoang, T. M., Ngo, H. Q., Duong, T. Q., et al. (2018). Cell-free massive MIMO networks: optimal power control against active eavesdropping. IEEE Trans. Commun., 66(10), 4724–4737.
Zhang, X., Guo, D., An, K., et al. (2019). Secrecy analysis and active pilot spoofing attack detection for multigroup multicasting cell-free massive MIMO systems. IEEE Access, 7, 57332–57340.
Zhang, X., Guo, D., An, K., et al. (2020). Secure communications over cell-free massive MIMO networks with hardware impairments. IEEE Syst. J., 14(2), 1909–1920.
Li, Y., Tao, C., Swindlehurst, A. L., et al. (2017). Downlink achievable rate analysis in massive MIMO systems with one-bit DACs. IEEE Commun. Lett., 21(7), 1669–1672.
Hu, X., Zhong, C., Chen, X., et al. (2019). Cell-free massive MIMO systems with low resolution ADCs. IEEE Trans. Commun., 67(10), 6844–6857.
Hu, X.; Zhong, C.; Chen, X., et al.: (2018) Rate analysis and ADC bits allocation for cell-free massive MIMO systems with low resolution ADCs. IEEE Global Communications Conference (GLOBECOM), pp. 1–6.
Xu, Q., & Ren, P. (2020). Secure massive MIMO downlink with low-resolution ADCs/DACs in the presence of active eavesdropping. IEEE Access, 8, 140981–140997.
Zhang, Y., Zhou, M., Cao, H., et al. (2020). Joint resource optimisation in Cell-free massive MIMO with low-resolution ADCs. IET Commun., 14(12), 1894–1901.
Zhang, Y., Zhou, M., Qiao, X., et al. (2019). On the performance of cell-free massive mimo with low-resolution ADCs. IEEE Access, 7, 117968–117977.
Teeti, M. A. (2020). Downlink secrecy rate of one-bit massive MIMO system with active eavesdropping. IEEE Access, 8, 37821–37842.
Gersho, A., & Gray, R. M. (1992). Vector Quantization and Signal Compression. Norwell: Springer.
Tuy, H. (2016). Convex Analysis and Global Optimization (2nd ed., p. 2016). Cham: Springer.
Timilsina, S.; Kudathanthirige, D.; & Amarasuriya, G.: (2018). Physical layer security in cell-free massive MIMO. IEEE Global Communications Conference (GLOBECOM), pp. 1–7.
Acknowledgements
The authors would like to thank the anonymous reviewers and the editors for helping to improve this paper. This work was supported by the National Natural Science Foundation of China under Grant 61901502 and Grant U19B214.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A
To derive the closed-form expression of (24), we should analyze the different components seperately. Firstly, we focus on the term \({\mathbb E}\left\{ {\sum \limits _{m = 1}^M {\sqrt{{\eta _{mk}}} {\varvec{g}}_{mk}^T{\hat{\varvec{g}}}_{mk}^*} } \right\} \) as
Due to the independence between the channel estimation \({{\hat{\varvec{g}}}_{mk}}\) and estimation error \({{\varvec{\tilde{g}}}_{mk}}\), it is easy to obtain that
Then, we calculate
According to some existing literature[35]-[36], we can get that
Substituting (56) and (57) into (55), we can get that
Then, we compute
Now we can focus on the last term as
where
Substituting (54), (58), (59) and (60) into (24) yields the results given by (27), which completes the proof.
Appendix B
For analytical tractability, we can analyze the numerator (desired signal) and denominator (the effective noise) of the Eve’s SINR. Hence, we start with the desired signal component that
According to the property of the MMSE algorithm used in this paper, we know that
Due to mutual independence between the channel estimation and estimation error, it is not hard to achieve that
Next, we calculate the multi-user interference component using the independence of different terms as
Plugging (62) and (65) into (28), we finally achieve the result as (29). This finishes the proof.
Appendix C
From (27) and (29), it is easy to see that \({R_k}\) and \({R_E}\) are increasing with M. Then, by relaxing M to be a continuous real number, after some simple algebraic manipulations, we know that \(\frac{{\partial R_{\sec }^k}}{{\partial M}} > 0\) which indicates that system can obtain more secrecy capacity by equipping more APs.
Note that the expression (27) can be rewritten as
where
Then, defining that \({\mathrm{\Gamma } _k} = \min \left\{ {\sqrt{{\eta _{mk}}} {\lambda _{mk}}} \right\} , 1 \le m \le M\) and \({\mathrm{\Theta } _k} = \max \left\{ {\sum \limits _{i = 1}^K {{\eta _{mi}}{\lambda _{mi}}{\beta _{mk}}} } \right\} , 1 \le m \le M\), we can get that
Obviously, we can derive that \(\mathop {\lim }\limits _{M \rightarrow + \infty } L_k^{\left( 1 \right) } = 0\) and \(\mathop {\lim }\limits _{M \rightarrow + \infty } L_k^{\left( 2 \right) } = 0\).
Consequently, it can be derived that
Similarly, with the definition of \({A_k}\), \({B_k}\), \({C_k}\) and \({D_k}\), we can get that
Evidently, we note that \({A_k}\), \({B_k}\), \({C_k}\) and \({D_k}\) are all positive terms, and don’t scale with M. Hence, we can further get that
Plugging (71) and (72) into (36) can complete the proof.
Rights and permissions
About this article
Cite this article
Zhang, X., Liang, T. & An, K. Secrecy performance analysis of cell-free massive MIMO in the presence of active eavesdropper with low resolution ADCs. Wireless Netw 27, 4839–4852 (2021). https://doi.org/10.1007/s11276-021-02766-0
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-021-02766-0