Abstract
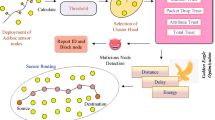
Due to the widespread application of wireless sensor networks in fields such as healthcare, the battlefield, etc., security has become a prime concern for transmitting information without any data manipulation. For this concern, we introduce a Three-Level Weighted Trust evaluation-based Grey Wolf Optimization (3LWT-GWO) approach for the effective detection of misbehaving nodes and provide an optimal secure route through trusted nodes for delivering the data securely to the destination. The proposed model is categorized into three phases: (a) trust-based clustering, (b) cluster head selection, and (c) optimal data routing. Initially, the sensors are deployed randomly in the region in which the nodes have the initial same energy. Then the clustering of nodes is performed in the first phase by computing the Overall Trust Score (OTS) for each node based on the factors like direct trust, indirect trust, energy trust, Long-term neighbor Recommendation Trust, authentication trust, and link quality trust. This OTS helps to identify unsafe nodes. After the identification of unsafe nodes, clustering is performed. In the second stage, the weight of each node is calculated based on the residual energy, node distance, and energy. Then the node that has the highest weight is nominated as Cluster Head. Next, optimal routing is performed based on the GWO algorithm by computing the Trust Satisfactory degree, distance, energy, and delay. Based on the estimated route, the packet is delivered from the source node to the destination. The performance of the 3LWT-GWO method delivers better results when compared with the prevailing techniques in terms of energy consumption, throughput, network lifetime, accuracy, detection rate, and delay.











Similar content being viewed by others
References
Shahbaz, A. N., Barati, H., & Barati, A. (2021). Multipath routing through the firefly algorithm and fuzzy logic in wireless sensor networks. Peer-to-Peer Networking and Applications, 14(2), 541–558.
Desai, R., Patil, B. P., & Sharma, D. P. (2017). Routing protocols for mobile ad hoc network: A survey and analysis. Indonesian Journal of Electrical Engineering and Computer Science, 7(3), 795–801.
Aadil, F., Raza, A., Khan, M. F., Maqsood, M., Mehmood, I., & Rho, S. (2018). Energy aware cluster-based routing in flying ad-hoc networks. Sensors, 18(5), 1413.
Mosavifard, A., & Barati, H. (2020). An energy-aware clustering and two-level routing method in wireless sensor networks. Computing, 102(7), 1653–1671.
Hajipour, Z., & Barati, H. (2021). EELRP: Energy efficient layered routing protocol in wireless sensor networks. Computing, 103, 2789–2809.
Rani, A., & Kumar, S. (2017). A survey of security in wireless sensor networks. In 2017 3rd international conference on computational intelligence and communication technology (CICT) (pp. 1–5). IEEE.
Yadav, K. S., & Tamboli, M. (2017). Defending against path-based denial of service attack in wireless sensor network. In International conference on examination in modern technology and engineering (ICEMTE) (Vol. 5, No. 3, pp. 46–51).
Panda, S. N. (2018). GPS hash table based location identifier algorithm for security and integrity against vampire attacks. In M. U. Bokhari, N. Agrawal, & D. Saini (Eds.), Cyber security (pp. 81–89). Springer.
Isaac Sajan, R., & Jasper, J. (2021). A secure routing scheme to mitigate attack in wireless adhoc sensor network. Computers and Security, 103, 102197.
Kumari, R., & Sharma, P. K. (2018). A silver-coated scheme for detection and prevention against vampire attack in wireless sensor network. In V. Janyani, M. Tiwari, G. Singh, & P. Minzioni (Eds.), Optical and wireless technologies (pp. 547–555). Springer.
Sharma, M. K., & Joshi, B. K. (2017). Detection and prevention of vampire attack in wireless sensor networks. In 2017 International conference on information, communication, instrumentation and control (ICICIC) (pp. 1–5). IEEE.
Mittal, N., Singh, S., Singh, U., & Salgotra, R. (2021). Trust-aware energy-efficient stable clustering approach using fuzzy type-2 Cuckoo search optimization algorithm for wireless sensor networks. Wireless Networks, 27(1), 151–174.
Hamsha, K., & Nagaraja, G. S. (2019). Threshold cryptography based light weight key management technique for hierarchical WSNs. In International conference on ubiquitous communications and network computing (pp. 188–197). Springer.
Labraoui, N., Gueroui, M., & Sekhri, L. (2016). A risk-aware reputation-based trust management in wireless sensor networks. Wireless Personal Communications, 87(3), 1037–1055.
Malik, S. K., Dave, M., Dhurandher, S. K., Woungang, I., & Barolli, L. (2017). An ant-based QoS-aware routing protocol for heterogeneous wireless sensor networks. Soft computing, 21(21), 6225–6236.
Fang, W., Zhang, W., Yang, W., Li, Z., Gao, W., & Yang, Y. (2021). Trust management-based and energy efficient hierarchical routing protocol in wireless sensor networks. Digital Communications and Networks, 7, 470–478.
Khan, T., Singh, K., Abdel-Basset, M., Long, H. V., Singh, S. P., & Manjul, M. (2019). A novel and comprehensive trust estimation clustering based approach for large scale wireless sensor networks. IEEE Access, 7, 58221–58240.
Selvi, M., Thangaramya, K., Ganapathy, S., Kulothungan, K., Nehemiah, H. K., & Kannan, A. (2019). An energy aware trust based secure routing algorithm for effective communication in wireless sensor networks. Wireless Personal Communications, 105(4), 1475–1490.
Shahidinejad, A., & Barshandeh, S. (2020). Sink selection and clustering using fuzzy-based controller for wireless sensor networks. International Journal of Communication Systems, 33(15), e4557.
Gilbert, E. P. K., Baskaran, K., Rajsingh, E. B., Lydia, M., & Selvakumar, A. I. (2019). Trust aware nature inspired optimised routing in clustered wireless sensor networks. International Journal of Bio-Inspired Computation, 14(2), 103–113.
Lyu, C., Zhang, X., Liu, Z., & Chi, C. H. (2019). Selective authentication based geographic opportunistic routing in wireless sensor networks for Internet of Things against DoS attacks. IEEE Access, 7, 31068–31082.
Kumar, N., & Singh, Y. (2017). Trust and packet load balancing based secure opportunistic routing protocol for WSN. In 2017 4th International conference on signal processing, computing and control (ISPCC) (pp. 463–467). IEEE.
Bangotra, D. K., Singh, Y., Selwal, A., Kumar, N., Singh, P. K., & Hong, W. C. (2020). An intelligent opportunistic routing algorithm for wireless sensor networks and its application towards e-healthcare. Sensors, 20(14), 3887.
Habib, M. A., Saha, S., Razzaque, M. A., Mamun-Or-Rashid, M., Hassan, M. M., Pace, P., & Fortino, G. (2020). Lifetime maximization of sensor networks through optimal data collection scheduling of mobile sink. IEEE Access, 8, 163878–163893.
Fang, W., Zhang, W., Chen, W., Pan, T., Ni, Y., & Yang, Y. (2020). Trust-based attack and defense in wireless sensor networks: A survey. Wireless Communications and Mobile Computing, 2020, 1–20.
Mehmood, G., Khan, M. Z., Waheed, A., Zareei, M., & Mohamed, E. M. (2020). A trust-based energy-efficient and reliable communication scheme (trust-based ERCS) for remote patient monitoring in wireless body area networks. IEEE Access, 8, 131397–131413.
Yousefpoor, E., Barati, H., & Barati, A. (2021). A hierarchical secure data aggregation method using the dragonfly algorithm in wireless sensor networks. Peer-to-Peer Networking and Applications, 14, 1–26.
Hasheminejad, E., & Barati, H. (2021). A reliable tree-based data aggregation method in wireless sensor networks. Peer-to-Peer Networking and Applications, 14(2), 873–887.
Naghibi, M., & Barati, H. (2021). SHSDA: Secure hybrid structure data aggregation method in wireless sensor networks. Journal of Ambient Intelligence and Humanized Computing, 12, 1–20.
Sharifi, S. S., & Barati, H. (2021). A method for routing and data aggregating in cluster-based wireless sensor networks. International Journal of Communication Systems, 34(7), e4754.
AlFarraj, O., AlZubi, A., & Tolba, A. (2018). Trust-based neighbor selection using activation function for secure routing in wireless sensor networks. Journal of Ambient Intelligence and Humanized Computing, 2018, 1–11.
Terence, J. S., & Purushothaman, G. (2019). A novel technique to detect malicious packet dropping attacks in wireless sensor networks. Journal of Information Processing Systems, 15(1), 203–216.
Gomathy, V., Padhy, N., Samanta, D., Sivaram, M., Jain, V., & Amiri, I. S. (2020). Malicious node detection using heterogeneous cluster based secure routing protocol (HCBS) in wireless adhoc sensor networks. Journal of Ambient Intelligence and Humanized Computing, 11(11), 4995–5001.
Isaac Sajan, R., & Jasper, J. (2020). Trust-based secure routing and the prevention of vampire attack in wireless ad hoc sensor network. International Journal of Communication Systems, 33(8), e4341.
Elmahdi, E., Yoo, S. M., & Sharshembiev, K. (2020). Secure and reliable data forwarding using homomorphic encryption against blackhole attacks in mobile ad hoc networks. Journal of Information Security and Applications, 51, 102425.
Kumar, K. V., Jayasankar, T., Eswaramoorthy, V., & Nivedhitha, V. (2020). SDARP: Security based Data Aware Routing Protocol for ad hoc sensor networks. International Journal of Intelligent Networks, 1, 36–42.
Acknowledgements
Not applicable.
Funding
There is no funding for this study.
Author information
Authors and Affiliations
Contributions
All the authors have participated in writing the manuscript and have revised the final version. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
Authors declares that they have no conflict of interest.
Ethical standards
This article does not contain any studies with human participants and/or animals performed by any of the authors.
Consent to participate
There is no informed consent for this study.
Consent for publication
Not applicable.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sajan, R.I., Christopher, V.B., Kavitha, M.J. et al. An energy aware secure three-level weighted trust evaluation and grey wolf optimization based routing in wireless ad hoc sensor network. Wireless Netw 28, 1439–1455 (2022). https://doi.org/10.1007/s11276-022-02917-x
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-022-02917-x