Abstract
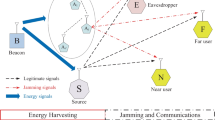
Friendly spectrum jamming is a flexible scheme to establish secure communications among heterogeneous wireless devices without the need of encryption. Previous works have indicated that this scheme however has weak security strength against multiple antenna eavesdropper in today’s wireless communication systems, which limits its wide applicability. To tackle this challenge, we propose a novel modulation method, called energy modulation. The basic idea of our method is to keep the secrecy of the channel state information in modulation, so as to bring high uncertainty to the MIMO’s separation and the eavesdropper’s decoding. As a result, the security strength of friendly jamming notably increases facing multiple antenna eavesdropper. To demonstrate the effectiveness of our method, we perform independent component analysis to decouple the components of the measured signals with maximum likelihood separation. We find that our solution dramatically decreases the eavesdropper’s partial information and has much less bits being compromised comparing with common amplitude and phase modulation.










Similar content being viewed by others
Notes
Encryption is not applied because of the resource constraint problem in Alice for example.
because of the distance advantage that Carol is closer to Eve than Alice and Bob for example.
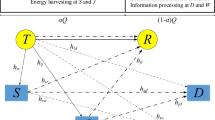
Because of the changing of environment, the channel coefficients evolve continuously in time. However, as we consider a short period of time within a data frame, which is much smaller than the coherence time, the channel states keep invariant.
In wireless communications, the most notable effects caused by physical phenomena are fading and path-loss. Fading is a self-interference phenomenon that results from the multi-path propagation of radio frequency waves while path-loss is simply the attenuation of wave amplitude with distance. As a consequence of these effects, the wireless channel coefficients are normally unpredictable since the exact knowledge of the wave paths and their lengths are unavailable.
It is assumed that the channels over which it receives these N signals are sufficiently different, i.e. the antennas are not located significantly smaller than half of a wavelength.
For example, Zhou et al. [49] proposed a subspace based blind channel estimation method for space-time coded MIMO-OFDM systems using properly designed redundant linear precoding and the noise subspace method. Bolcskei et al. [50] proposed an algorithm for blind channel estimation and equalization for MIMO-OFDM systems using second-order cyclostationary statistics induced by employing a periodic nonconstant-modulus antenna precoding. Muquet et al. [51] developed a subspace method by utilizing the redundancy introduced by the cyclic prefix (CP) insertion.
For multi-path Rayleigh fading channels, the two wireless channels can be considered uncorrelated, \(\rho _{ij} = 0\), if the distance between the ith and the jth receiving antennas is greater than half wavelength; the two wireless channels are partially correlated, \(0< \rho _{ij} <1\), if the distance between the ith and the jth receiving antennas is less than half wavelength.
The problem of how to set the jamming power has been studied in [5, 11, 24, 25]. Generally, as jamming power increases, in the early stage when the jamming power is not significant, jamming is beneficial as the secrecy outage probability becomes lower; while at the later stage when the jamming signal becomes much stronger, the harmful effect of jamming signal to legitimate decoding becomes dominant. So there is normally an optimal jamming power leading to the highest jamming efficiency. Our jamming-to-signal-ratio is set based on these previous works.
References
Chaudhary, S., & Garg, N. (2014). Internet of things: A revolution. Compusoft International Journal of Advanced Computer Technology, 3(4), 714.
Tippenhauer, N. O., Malisa, L., Ranganathan, A., & Capkun, S. (2013). On limitations of friendly jamming for confidentiality. In Security and privacy, pp. 160–173.
Vilela, J. P., Bloch, M., Barros, J., & Mclaughlin, S. W. (2011). Wireless secrecy regions with friendly jamming. IEEE Transactions on Information Forensics and Security, 6(2), 256–266.
Vilela, J. P., Bloch, M., Barros, J., & Mclaughlin, S. W. (2010). Friendly jamming for wireless secrecy. In IEEE International Conference on Communications, pp. 1–6
Chen, L., Zhu, Q., Meng, W., & Hua, Y. (2017). Fast power allocation for secure communication with full-duplex radio. IEEE Transactions on Signal Processing, 65(14), 3846–3861.
Pelechrinis, K., Iliofotou, M., & Krishnamurthy, S. V. (2011). Denial of service attacks in wireless networks: The case of jammers. IEEE Communications Surveys and Tutorials, 13(2), 245–257.
Lin, P. H., Gabry, F., Thobaben, R., Jorswieck, E. A., & Skoglund, M. (2016). Multi-phase smart relaying and cooperative jamming in secure cognitive radio networks. IEEE Transactions on Cognitive Communications & Networking, 2(1), 38–52.
Dong, L., Han, Z., Petropulu, A. P., & Vincent Poor, H. (2009). Cooperative jamming for wireless physical layer security. IEEE Workshop on Statistical Signal Processing, 8(4), 417–420.
Gan, Z., Choo, L. C., & Wong, K. K. (2011). Optimal cooperative jamming to enhance physical layer security using relays. IEEE Transactions on Signal Processing, 59(3), 1317–1322.
Liu, Y., Li, J., & Petropulu, A. P. (2013). Destination assisted cooperative jamming for wireless physical-layer security. IEEE Transactions on Information Forensics and Security, 8(4), 682–694.
Yang, J., Kim, I. M., & Dong, I. K. (2014). Joint design of optimal cooperative jamming and power allocation for linear precoding. IEEE Transactions on Communications, 62(9), 3285–3298.
Gollakota, S., Hassanieh, H., Ransford, B., Katabi, D., & Fu, K. (2011). They can hear your heartbeats: Non-invasive security for implantable medical devices. In ACM SIGCOMM 2011 Conference, pp. 2–13.
Siyari, P., Krunz, M., & Nguyen, D. N. (2017). Friendly jamming in a mimo wiretap interference network: A nonconvex game approach. IEEE Journal on Selected Areas in Communications, PP(99), 1–1.
Cao, X.-R., & Liu, R.-W. (1996). General approach to blind source separation. IEEE Transactions on Signal Processing, 44(3), 562–571.
Oggier, F., & Hassibi, B. (2011). The secrecy capacity of the mimo wiretap channel. IEEE Transactions on Information Theory, 57(8), 4961–4972.
Comon, P. (1994). Independent component analysis, a new concept? Signal Processing, 36(3), 287–314.
Goel, S., & Negi, R. (2008). Guaranteeing secrecy using artificial noise. IEEE Transactions on Wireless Communications, 7(6), 2180–2189.
Tang, X., Liu, R., Spasojevic, P., & Poor, H. V. (2008). The gaussian wiretap channel with a helping interferer. In 2008 IEEE International Symposium on Information Theory, pp. 389–393.
Jin, R., Zeng, K., & Zhang, K. (2021). A reassessment on friendly jamming efficiency. IEEE Transactions on Mobile Computing, 20(1), 32–47.
Wolf, A., & Jorswieck, E. A. (2010). On the zero forcing optimality for friendly jamming in miso wiretap channels. In IEEE Eleventh International Workshop on Signal Processing Advances in Wireless Communications, pp. 1–5.
Akgun, B., Koyluoglu, O. O., & Krunz, M. (2015). Receiver-based friendly jamming with single-antenna full-duplex receivers in a multiuser broadcast channel. In IEEE Global Communications Conference, pp. 1–6.
Xiao, L., Zhang, T., Shen, X., Yang, D., & Cuthbert, L. (2017). Secrecy in wireless information and power transfer for one-way and two-way untrusted relaying with friendly jamming. In Mobile Information Systems, 2017, (2017-8-10), 2017, pp. 1–10.
Ali, B., Zamir, N., Fasih, M., Butt, U., & Ng, S. X. (2016). Physical layer security: Friendly jamming in an untrusted relay scenario. In Signal Processing Conference, pp. 958–962.
Ara, M., Reboredo, H., Renna, F., & Rodrigues, M. R. D. (2013). Power allocation strategies for OFDM gaussian wiretap channels with a friendly jammer. In IEEE International Conference on Communications, pp. 3413–3417.
Sarma, S., & Kuri, J. (2015). Optimal power allocation for protective jamming in wireless networks. Elsevier North-Holland Inc.
Mobini, Z., Mohammadi, M., & Tellambura, C. (2019). Wireless-powered full-duplex relay and friendly jamming for secure cooperative communications. IEEE Transactions on Information Forensics and Security, 14(3), 621–634.
Qi, N., Wang, W., Xiao, M., Jia, L., & Tsiftsis, T. (2021). A learning-based spectrum access Stackelberg game: Friendly jammer-assisted communication confrontation. IEEE Transactions on Vehicular Technology, PP(99), 1.
Berger, D. S., Gringoli, F., Martinovic, I., & Schmitt, J. (2014). Gaining insight on friendly jamming in a real-world IEEE 802.11 network. In ACM Conference on Security and Privacy in Wireless and Mobile Networks, pp. 105–116.
Berger, D. S., Gringoli, F., Facchi, N., Martinovic, I., & Schmitt, J. B. (2016). Friendly jamming on access points: Analysis and real-world measurements. IEEE Transactions on Wireless Communications, 15(9), 6189–6202.
Kim, Y. S., Tague, P., Lee, H., & Kim, H. (2015). A jamming approach to enhance enterprise wi-fi secrecy through spatial access control. Wireless Networks, 21(8), 2631–2647.
Eletreby, R., Rahbari, H., & Krunz, M. (2015). Supporting phy-layer security in multi-link wireless networks using friendly jamming. In IEEE Global Communications Conference, pp. 1–6.
Adams, M., & Bhargava, V. K. (2017). Using friendly jamming to improve route security and quality in ad hoc networks. In Electrical and computer engineering.
Mostafa, A., & Lampe, L. (2014). Securing visible light communications via friendly jamming. In GLOBECOM Workshops, pp. 524–529.
Pham, T. V., & Pham, A. T. (2021). Energy-efficient friendly jamming for physical layer security in visible light communication. In 2021 IEEE International Conference on Communications Workshops (ICC Workshops).
Li, X., Dai, H. N., Wang, H., & Xiao, H. (2016). On performance analysis of protective jamming schemes in wireless sensor networks. Sensors, 16(12), 1987.
Dang-Ngoc, H., Nguyen, D. N., Ho-Van, K., Hoang, D. T., Dutkiewicz, E., Pham, Q. V., & Hwang, W. J. (2021). Secure swarm UAV-assisted communications with cooperative friendly jamming.
Li, X., Dai, H. N., Shukla, M. K., Li, D., & Imran, M. (2021). Friendly-jamming schemes to secure ultra-reliable and low-latency communications in 5g and beyond communications. Computer Standards and Interfaces, 78(2), 103540.
Jin, R., & Zeng, K. (2018). Secure inductive-coupled near field communication at physical layer. IEEE Transactions on Information Forensics and Security, 13(12), 3078–3093.
Hassanieh, H., Wang, J., Katabi, D., Kohno, T. (2015). Securing RFIDs by randomizing the modulation and channel. In Usenix Conference on Networked Systems Design and Implementation, pp. 235–249.
Bharadia, D., Mcmilin, E., & Katti, S. (2013). Full duplex radios. Computer Communication Review, 43(4), 375–386.
Sabharwal, A., Schniter, P., Guo, D., & Bliss, D. W. (2014). In-band full-duplex wireless: Challenges and opportunities. IEEE Journal on Selected Areas in Communications, 32(9), 1637–1652.
Shen, D., & Li, V. O. K. (2006). Fundamentals of wireless communications.
Kashyap, A., Basar, T., & Srikant, R. (2004). Correlated jamming on mimo gaussian fading channels. IEEE Transactions on Information Theory, 50(9), 2119–2123.
Telatar, E. (1999). Capacity of multi-antenna gaussian channels. European Transactions on Telecommunications, 10(6), 585–595.
Rao, C., & Hassibi, B. (2004). Analysis of multiple-antenna wireless links at low snr. IEEE Transactions on Information Theory, 50(9), 2123–2130.
Pollock, T., Abhayapala, T., & Kennedy, R. (2003). Antenna saturation effects on mimo capacity. In IEEE International Conference on Communications.
Biguesh, M., & Gershman, A. B. (2006). Training-based mimo channel estimation: A study of estimator tradeoffs and optimal training signals. IEEE Transactions on Signal Processing, 54(3), 884–893.
Shin, C., Heath, R. W., & Powers, E. J. (2007). Blind channel estimation for mimo-ofdm systems. IEEE Transactions on Vehicular Technology, 56(2), 670–685.
Zhou, S., Muquet, B., & Giannakis, G. B. (2002). Subspace-based (semi-) blind channel estimation for block precoded space-time ofdm. IEEE Transactions on Signal Processing, 50(5), 1215–1228.
Bolcskei, H., Heath, R. W., & Paulraj, A. J. (2002). Blind channel identification and equalization in ofdm-based multiantenna systems. IEEE Transactions on Signal Processing, 50(1), 96–109.
Muquet, B., de Courville, M., & Duhamel, P. (2002). Subspace-based blind and semi-blind channel estimation for ofdm systems. IEEE Transactions on Signal Processing, 50(7), 1699–1712.
Stewart, G. W. (1990). Matrix perturbation theory. Academic Press.
Hyvarinen, A., & Oja, E. (2000). Independent component analysis: Algorithms and applications. Neural Networks, 13(4), 411–430.
Tropp, J. A., & Gilbert, A. C. (2007). Signal recovery from partial information via orthogonal matching pursuit. IEEE Transactions on Information Theory, 53(12), 4655–4666.
Cardoso, J. (1997). Infomax and maximum likelihood for blind source separation. IEEE Signal Processing Letters, 4(4), 112–114.
Giannakis, G. B., & Tsatsanis, M. K. (1992). A unifying maximum-likelihood view of cumulant and polyspectral measures for non-gaussian signal classification and estimation. IEEE Transactions on Information Theory, 38(2), 386–406.
Marquardt, D. W. (1963). An algorithm for least-squares estimation of nonlinear parameters. Journal of the Society for Industrial and Applied Mathematics, 11(2), 431–441.
Mor, J. J. (1978). The Levenberg-Marquardt algorithm: Implementation and theory. Lecture Notes in Mathematics, 630, 105–116.
Duncan, T. E. (1970). On the calculation of mutual information. Siam Journal on Applied Mathematics, 19(1), 215–220.
Brown, G., Pocock, A., Zhao, M. J., & Lujan, M. (2012). Conditional likelihood maximisation: A unifying framework for information theoretic feature selection. Journal of Machine Learning Research, 13(1), 27–66.
Thomas, R. D., Moses, N. C., Semple, E. A., & Strang, A. J. (2014). An efficient algorithm for the computation of average mutual information: Validation and implementation in Matlab. Journal of Mathematical Psychology, 61, 45–59.
Belouchrani, A., Abed-Meraim, K., Cardoso, J. F., & Moulines, E. (2002). A blind source separation technique using second-order statistics. IEEE Transactions on Signal Processing, 45(2), 434–444.
Gopala, P. K., Lai, L., & El Gamal, H. (2006). On the secrecy capacity of fading channels. IEEE Transactions on Information Theory, 54(10), 4687–4698.
Acknowledgements
This work was supported in part by the National Science Foundation of China (NSFC) under grant 61801187 and in part by the U.S. National Science Foundation (NSF) under grants CNS-1619073 and CNS-1464487.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Jin, R., Zeng, K. & Jiang, C. Friendly spectrum jamming against MIMO eavesdropping. Wireless Netw 28, 2437–2453 (2022). https://doi.org/10.1007/s11276-022-02967-1
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-022-02967-1