Abstract
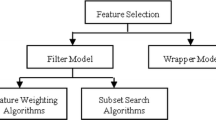
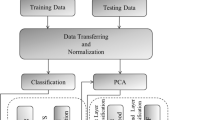
Wireless Networks (WNs) is a widely used technology that has found application in many fields due to their mobile and flexible nature. Many attempts have been made to secure the standard of WNs by utilizing useful security features. But due to the absence of an external robust defense mechanism such as Intrusion Detection Scheme (IDS), most of the time, the network fails to provide proper security to the application. To design an effective defense mechanism, the use of appropriate features is a must for any network. This article proposes an Optimized Maximum Correlation based Feature Reduction (OMCFR) technique for data networks. The proposed scheme utilizes maximum correlation as a major factor depending upon which individual rank is allocated to the features. The useful features are extracted using OMCFR for efficient detection. The selected features are utilized with multiclass classifier to classify the data into normal against intrusive activities. A Random Forest based multiclass classifier technique is utilized in the study. The standard dataset of Wireless Networks from the AWID family (2015), CICIDS2017 and NSL-KDD family is utilized to evaluate the proposed IDS. The results show promising performance with reduced False Positive Rate (FPR) (for NSL-KDD: 0.10, for AWID: 0.27), achieves high detection accuracy (for NSL-KDD: 99.95\(\%\), for AWID: 99.2\(\%\)) and overall time complexity (for NSL-KDD: 182.5 s, for AWID: 812.45 s).











Similar content being viewed by others
References
Denko, M. K. (2005). Detection and prevention of denial of service (dos) attacks in mobile ad hoc networks using reputation-based incentive scheme. Journal of Systemics, Cybernetics and Informatics, 3(4), 1–9.
Di Pietro, R., Guarino, S., Verde, N. V., & Domingo-Ferrer, J. (2014). Security in wireless ad-hoc networks—A survey. Computer Communications, 51, 1–20.
Kannhavong, B., Nakayama, H., Nemoto, Y., Kato, N., & Jamalipour, A. (2007). A survey of routing attacks in mobile ad hoc networks. IEEE Wireless Communications, 14(5), 85–91.
Zargar, S. T., Joshi, J., & Tipper, D. (2013). A survey of defense mechanisms against distributed denial of service (ddos) flooding attacks. IEEE Communications Surveys & Tutorials, 15(4), 2046–2069.
Gavel, S., Raghuvanshi, A. S., & Tiwari, S. (2021). Maximum correlation based mutual information scheme for intrusion detection in the data networks. Expert Systems with Applications, 189, 116089.
Li, Y., Xu, Y., Liu, Z., Hou, H., Zheng, Y., Xin, Y., Zhao, Y., & Cui, L. (2020). Robust detection for network intrusion of industrial iot based on multi-cnn fusion. Measurement, 154, 107450.
Schweitzer, N., Stulman, A., Margalit, R. D., & Shabtai, A. (2016). Contradiction based gray-hole attack minimization for ad-hoc networks. IEEE Transactions on Mobile Computing, 16(8), 2174–2183.
Gavel, S., Raghuvanshi, A. S., & Tiwari, S .(2020a). A multilevel hybrid anomaly detection scheme for industrial wireless sensor networks. International Journal of Network Management. 10.1002/nem.2144
Poongodi, M., & Bose, S. (2015). A novel intrusion detection system based on trust evaluation to defend against ddos attack in manet. Arabian Journal for Science and Engineering, 40(12), 3583–3594.
Eid, H. F., Salama, M. A., Hassanien, A. E., & Kim, T. (2011). Bi-layer behavioral-based feature selection approach for network intrusion classification. In International Conference on Security Technology. Springer (pp. 195–203)
Gavel, S., Raghuvanshi, A. S., & Tiwari, S. (2020). A novel density estimation based intrusion detection technique with Pearson’s divergence for wireless sensor networks. ISA Transactions, 111, 180–191.
Sundararajan, T., Ramesh, S., Maheswar, R., & Deepak, K. (2014). Biologically inspired artificial intrusion detection system for detecting wormhole attack in manet. Wireless Networks, 20(4), 563–578.
Bostani, H., & Sheikhan, M. (2017). Hybrid of binary gravitational search algorithm and mutual information for feature selection in intrusion detection systems. Soft Computing, 21(9), 2307–2324.
Aljawarneh, S., Aldwairi, M., & Yassein, M. B. (2018). Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. Journal of Computational Science, 25, 152–160.
Aljawarneh, S., Yassein, M. B., & Aljundi, M. (2019). An enhanced j48 classification algorithm for the anomaly intrusion detection systems. Cluster Computing, 22(5), 10549–10565.
Maza, S., & Touahria, M. (2019). Feature selection for intrusion detection using new multi-objective estimation of distribution algorithms. Applied Intelligence, 49(12), 4237–4257.
Vijayanand, R., Devaraj, D., & Kannapiran, B. (2018). Intrusion detection system for wireless mesh network using multiple support vector machine classifiers with genetic-algorithm-based feature selection. Computers & Security, 77, 304–314.
Ghazy, R. A., El-Rabaie, E. S. M., Dessouky, M. I., El-Fishawy, N. A., & Abd El-Samie, F. E. (2020). Feature selection ranking and subset-based techniques with different classifiers for intrusion detection. Wireless Personal Communications, 111(1), 375–393.
Gavel, S., Raghuvanshi, A. S., & Tiwari, S. (2021). Distributed intrusion detection scheme using dual-axis dimensionality reduction for internet of things (iot). The Journal of Supercomputing, 77, 10488–10511.
Zhou, Y., Cheng, G., Jiang, S., & Dai, M .(2020) . Building an efficient intrusion detection system based on feature selection and ensemble classifier. Computer Networks p 107247
Amiri, F., Yousefi, M. R., Lucas, C., Shakery, A., & Yazdani, N. (2011). Mutual information-based feature selection for intrusion detection systems. Journal of Network and Computer Applications, 34(4), 1184–1199.
Abraham, A., Jain, R., Thomas, J., & Han, S. Y. (2007). D-scids: Distributed soft computing intrusion detection system. Journal of Network and Computer Applications, 30(1), 81–98.
Chebrolu, S., Abraham, A., & Thomas, J. P. (2005). Feature deduction and ensemble design of intrusion detection systems. Computers & Security, 24(4), 295–307.
Mukkamala, S., & Sung, AH .(2005) . Significant feature selection using computational intelligent techniques for intrusion detection. In Advanced Methods for Knowledge Discovery from Complex Data. Springer (pp. 285–306)
Chen, Y., Abraham, A., & Yang, B. (2006). Feature selection and classification using flexible neural tree. Neurocomputing, 70(1–3), 305–313.
Kim, G., Lee, S., & Kim, S. (2014). A novel hybrid intrusion detection method integrating anomaly detection with misuse detection. Expert Systems with Applications, 41(4), 1690–1700.
Gogoi, P., Bhuyan, M. H., Bhattacharyya, D., & Kalita, J. K. (2012). Packet and flow based network intrusion dataset. In International Conference on Contemporary Computing. Springer (pp. 322–334)
Chitrakar, R., & Huang, C. (2014). Selection of candidate support vectors in incremental svm for network intrusion detection. Computers & Security, 45, 231–241.
Aburomman, A. A., & Reaz, M. B. I. (2016). A novel svm-knn-pso ensemble method for intrusion detection system. Applied Soft Computing, 38, 360–372.
Kuang, F., Xu, W., & Zhang, S. (2014). A novel hybrid kpca and svm with ga model for intrusion detection. Applied Soft Computing, 18, 178–184.
Sindhu, S. S. S., Geetha, S., & Kannan, A. (2012). Decision tree based light weight intrusion detection using a wrapper approach. Expert Systems with Applications, 39(1), 129–141.
Xiang, C., Yong, P. C., & Meng, L. S. (2008). Design of multiple-level hybrid classifier for intrusion detection system using bayesian clustering and decision trees. Pattern Recognition Letters, 29(7), 918–924.
Belgiu, M., & Drăguţ, L. (2016). Random forest in remote sensing: A review of applications and future directions. ISPRS Journal of Photogrammetry and Remote Sensing, 114, 24–31.
Chen, X., & Ishwaran, H. (2012). Random forests for genomic data analysis. Genomics, 99(6), 323–329.
Rodriguez-Galiano, V. F., Ghimire, B., Rogan, J., Chica-Olmo, M., & Rigol-Sanchez, J. P. (2012). An assessment of the effectiveness of a random forest classifier for land-cover classification. ISPRS Journal of Photogrammetry and Remote Sensing, 67, 93–104.
Ali, E., Elazim, S. A., & Abdelaziz, A. (2017). Ant lion optimization algorithm for optimal location and sizing of renewable distributed generations. Renewable Energy, 101, 1311–1324.
Mirjalili, S., Jangir, P., & Saremi, S. (2017). Multi-objective ant lion optimizer: A multi-objective optimization algorithm for solving engineering problems. Applied Intelligence, 46(1), 79–95.
Pal, M. (2005). Random forest classifier for remote sensing classification. International Journal of Remote Sensing, 26(1), 217–222.
Tavallaee, M., Bagheri, E., Lu, W., & Ghorbani, A. A. (2009). A detailed analysis of the kdd cup 99 data set. In 2009 IEEE symposium on computational intelligence for security and defense applications. IEEE (pp. 1–6)
Kolias, C., Kambourakis, G., Stavrou, A., & Gritzalis, S. (2015). Intrusion detection in 802.11 networks: Empirical evaluation of threats and a public dataset. IEEE Communications Surveys & Tutorials, 18(1), 184–208.
Sharafaldin, I., Lashkari, A. H., & Ghorbani, A. A. (2018). Toward generating a new intrusion detection dataset and intrusion traffic characterization. In ICISSP (pp. 108–116)
Ambusaidi, M. A., He, X., Nanda, P., & Tan, Z. (2016). Building an intrusion detection system using a filter-based feature selection algorithm. IEEE Transactions on Computers, 65(10), 2986–2998.
Usha, M., & Kavitha, P. (2017). Anomaly based intrusion detection for 802.11 networks with optimal features using svm classifier. Wireless Networks, 23(8), 2431–2446.
Levin, I. (2000). Kdd-99 classifier learning contest llsoft’s results overview. ACM SIGKDD Explorations Newsletter, 1(2), 67–75.
Agarwal, R., & Joshi, M. V. (2001) . Pnrule: a new framework for learning classifier models in data mining (a case-study in network intrusion detection). In Proceedings of the 2001 SIAM International Conference on Data Mining SIAM, pp. 1–17
Kim, D. S., & Park, J. S. (2003) . Network-based intrusion detection with support vector machines. In International Conference on Information Networking (pp. 747–756). Springer
Xuren, W., Famei, H., & Rongsheng, X. (2006). Modeling intrusion detection system by discovering association rule in rough set theory framework. In 2006 International Conference on Computational Inteligence for Modelling Control and Automation and International Conference on Intelligent Agents Web Technologies and International Commerce (CIMCA’06). IEEE (pp. 24–24)
Toosi, A. N., & Kahani, M. (2007). A new approach to intrusion detection based on an evolutionary soft computing model using neuro-fuzzy classifiers. Computer Communications, 30(10), 2201–2212.
Ashfaq, R. A. R., Wang, X. Z., Huang, J. Z., Abbas, H., & He, Y. L. (2017). Fuzziness based semi-supervised learning approach for intrusion detection system. Information Sciences, 378, 484–497.
Tama, B. A., Comuzzi, M., & Rhee, K. H. (2019). Tse-ids: A two-stage classifier ensemble for intelligent anomaly-based intrusion detection system. IEEE Access, 7, 94497–94507.
Attak, H., Combalia, M., Gardikis, G., Gastón, B., Jacquin, L., Katsianis, D., Litke, A., Papadakis, N., Papadopoulos, D., Pastor, A., et al. (2018). Application of distributed computing and machine learning technologies to cybersecurity. Space, 2, I2CAT.
Bansal, A., & Kaur, S .(2018) . Extreme gradient boosting based tuning for classification in intrusion detection systems. In International Conference on Advances in Computing and Data Sciences. Springer (pp. 372–380)
Catillo, M., Rak, M., & Villano, U .(2019) .Discovery of dos attacks by the zed-ids anomaly detector. Journal of High Speed Networks(Preprint):1–17
Zhong, Y., Chen, W., Wang, Z., Chen, Y., Wang, K., Li, Y., Yin, X., Shi, X., Yang, J., & Li, K. (2020). Helad: A novel network anomaly detection model based on heterogeneous ensemble learning. Computer Networks, 169, 107049.
Asad, M., Asim, M., Javed, T., Beg, M. O., Mujtaba, H., & Abbas, S .(2019). Deepdetect: Detection of distributed denial of service attacks using deep learning. The Computer Journal, 63(7), 983–994
Kim, T., & Pak, W. (2022). Real-time network intrusion detection using deferred decision and hybrid classifier. Future Generation Computer Systems, 132, 51–66.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Gavel, S., Raghuvanshi, A.S. & Tiwari, S. An optimized maximum correlation based feature reduction scheme for intrusion detection in data networks. Wireless Netw 28, 2609–2624 (2022). https://doi.org/10.1007/s11276-022-02988-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-022-02988-w