Abstract
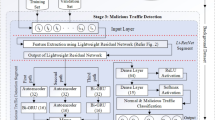
The implementation of IoT in industrial management is referred as Industrial IoT (IIoT). It is used to increase the overall operational efficiency. IIoT is considered as the backbone of the contemporary industries. For this purpose, strong security foundations have to be deployed with IIoT. This accelerates the industrial automation process by enrolling thousands of IoT devices and thus befitting the scattered connection and constrained functionalities of the IoT devices. In the Industrial Internet of Things, abnormal traffic detection is an emerging dilemma in network security. It can be ensured by monitoring the traffic flow in large-scale networks. In this connection, the deep learning paradigm has been accepted as the mainstream phenomenon in the field of abnormal traffic detection. It has achieved optimal results due to the constant improvement of computer performance with the help of Artificial Intelligence. Majority of the existing methods are based on supervised learning. As a result, due to numerous constraints, obtaining and marking abnormal traffic data samples in real life is extremely difficult. In addition, due to the diversity and complexity of the abnormal network data, the adaptability of various detection methods is low as well as difficult to judge the new abnormal traffic. Based on the above problems, this paper has proposed a semi-supervised abnormal flow detection framework in the IIoT based network scenario. The proposed model is named Memory Augment Based on Generative Adversarial Network (MeAEG-Net). It detects anomalies by training only normal flow of sample data and comparing the reconstruction errors of the underlying characteristics of input flow of generator module. To improve the generator's training, generative adversarial network has been deployed to tackle the problem of the autoencoder which is susceptible to noise. The generator uses an autoencoder and decoder structure. In addition, the memory augments module is introduced to the autoencoder's sub-network to reduce the generator module's generalization ability and raise the abnormal traffic reconstruction error. Our experimental results show that the method proposed in this paper can achieve a good effect of abnormal traffic detection in IIoT based networks under the premise of learning normal traffic data samples and improving the overall performance in all sectors of the industry.


















Similar content being viewed by others
References
Phua, C., Lee, V., Smith, K. and Gayler, R., (2010). A comprehensive survey of data mining-based fraud detection research. arXiv preprint arXiv:1009.6119.
Schlegl, T., Seeböck, P., Waldstein, S. M., Schmidt-Erfurth, U., & Langs, G. (2017). Unsupervised anomaly detection with generative adversarial networks to guide marker discovery. International conference on information processing in medical imaging (pp. 146–157). Cham: Springer.
Garcia-Teodoro, P., Diaz-Verdejo, J., Maciá-Fernández, G., & Vázquez, E. (2009). Anomaly-based network intrusion detection Techniques systems and challenges. Computers & security, 28(1–2), 18–28.
Ian, G., Jean, P.A., Mehdi, M., Bing, X., David, W.F., Sherjil, O. and Aaron, C., (2014) Generative adversarial nets. In Advances in neural information processing systems.
Erfani, S. M., Rajasegarar, S., Karunasekera, S., & Leckie, C. (2016). High-dimensional and large-scale anomaly detection using a linear one-class SVM with deep learning. Pattern Recognition, 58, 121–134.
Kim, Y., Kim, M. and Kim, G., (2018) Memorization precedes generation: Learning unsupervised gans with memory networks. arXiv preprint arXiv:1803.01500.
Gong, D., Liu, L., Le, V., Saha, B., Mansour, M.R., Venkatesh, S. and Hengel, A.V.D., (2019). Memorizing normality to detect anomaly: Memory-augmented deep autoencoder for unsupervised anomaly detection. In Proceedings of the IEEE/CVF International Conference on Computer Vision (pp. 1705–1714).
Vinayakumar, R., Alazab, M., Soman, K. P., Poornachandran, P., Al-Nemrat, A., & Venkatraman, S. (2019). Deep learning approach for intelligent intrusion detection system. IEEE Access, 7, 41525–41550.
Dong, B. and Wang, X., (2016). Comparison deep learning method to traditional methods using for network intrusion detection. In 2016 8th IEEE international conference on communication software and networks (ICCSN) (pp. 581–585). IEEE.
Rajkumar, N., D’Souza, A., Alex, S., & Kathrine, G. J. W. (2018). Long short-term memory-based recurrent neural network approach for intrusion detection. International Conference on ISMAC in Computational Vision and Bio-Engineering (pp. 837–846). Cham: Springer.
Kwon, D., Kim, H., Kim, J., Suh, S. C., Kim, I., & Kim, K. J. (2019). A survey of deep learning-based network anomaly detection. Cluster Computing, 22(1), 949–961.
Litjens, G., Kooi, T., Bejnordi, B. E., Setio, A. A. A., Ciompi, F., Ghafoorian, M., Van Der Laak, J. A., Van Ginneken, B., & Sánchez, C. I. (2017). A survey on deep learning in medical image analysis. Medical image analysis, 42, 60–88.
Akcay, S., Atapour-Abarghouei, A. and Breckon, T.P., (2018). Ganomaly: Semi-supervised anomaly detection via adversarial training. In Asian conference on computer vision (pp. 622–637). Springer, Cham.
Zhang, Y. Z., Xiao, J., Yun, X. C., & Wang, F. Y. (2012). DDoS attacks detection and control mechanisms. Ruanjian Xuebao/Journal of Software, 23(8), 2058–2072.
Chun-Qiong, W. U. (2012). Network Intrusion Detection Model Based on Feature Selection [J]. Computer Simulation, 29(6), 136–139.
Da Xu, L., He, W., & Li, S. (2014). Internet of things in industries: A survey. IEEE Transactions on industrial informatics, 10(4), 2233–2243.
Fu, L., Zhang, W., Tan, X., & Zhu, H. (2021). An algorithm for detection of traffic attribute exceptions based on cluster algorithm in industrial internet of things. IEEE Access, 9, 53370–53378.
Kim, D.S. and Park, J.S., (2003). Network-based intrusion detection with support vector machines. In International conference on information networking (pp. 747–756). Springer, Berlin, Heidelberg.
Moore, A.W. and Zuev, D., (2005). Internet traffic classification using bayesian analysis techniques. In Proceedings of the 2005 ACM SIGMETRICS international conference on Measurement and modeling of computer systems (pp. 50–60).
Williams, N., Zander, S., & Armitage, G. (2006). A preliminary performance comparison of five machine learning algorithms for practical IP traffic flow classification. ACM SIGCOMM Computer Communication Review, 36(5), 5–16.
Javaid, A., Niyaz, Q., Sun, W., & Alam, M. (2016). A deep learning approach for network intrusion detection system. Eai Endorsed Transactions on Security and Safety, 3(9), e2.
An, J., & Cho, S. (2015). Variational autoencoder based anomaly detection using reconstruction probability. Special Lecture on IE, 2(1), 1–18.
Gao, N., Gao, L., HE, Y. Y., & Wang, H. (2017). A lightweight intrusion detection model based on autoencoder network with feature reduction. ACTA Electonica Sinica, 45(3), 730.
Wang, W., Zhu, M., Wang, J., Zeng, X. and Yang, Z., (2017). End-to-end encrypted traffic classification with one-dimensional convolution neural networks. In 2017 IEEE international conference on intelligence and security informatics (ISI) (pp. 43–48). IEEE.
Goodfellow, I., Pouget-Abadie, J., Mirza, M., Xu, B., Warde-Farley, D., Ozair, S., Courville, A. and Bengio, Y., (2014). Generative adversarial nets. Advances in neural information processing systems, 27.
Liu, H., Wu, T., Shen, J., & Shi, C. (2020). Advanced persistent threat detection based on generative adversarial networks and long short-term memory. Comput. Sci, 47(1), 281–286.
Yin, C., Zhu, Y., Liu, S., Fei, J. and Zhang, H., (2018). An enhancing framework for botnet detection using generative adversarial networks. In 2018 International Conference on Artificial Intelligence and Big Data (ICAIBD) (pp. 228–234). IEEE.
Buczak, A. L., & Guven, E. (2015). A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Communications surveys & tutorials, 18(2), 1153–1176.
Liu, Z., Thapa, N., Shaver, A., Roy, K., Yuan, X. and Khorsandroo, S., (2020). Anomaly detection on iot network intrusion using machine learning. In 2020 International Conference on Artificial Intelligence, Big Data, Computing and Data Communication Systems (icABCD) (pp. 1–5). IEEE.
Berman, D. S., Buczak, A. L., Chavis, J. S., & Corbett, C. L. (2019). A survey of deep learning methods for cyber security. Information, 10(4), 122.
Acknowledgements
This research project is funded by the Research Foundation of Education, Bureau of Hunan Province (No.19B109), and the Research Foundation of Education Bureau of Hunan Province (No.20A088), and the Special Funds for Construction of Innovative Provinces in Hunan Province of China (No.2020GK2006, No.2020GK2007)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wang, T., Li, W., Rong, H. et al. Abnormal traffic detection-based on memory augmented generative adversarial IIoT-assisted network. Wireless Netw 28, 2579–2595 (2022). https://doi.org/10.1007/s11276-022-02992-0
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-022-02992-0