Abstract
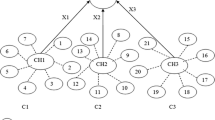
Today, key management is widely recognized as an important aspect of security in wireless sensor networks. In these networks, sensor nodes can be either mobile or static. Therefore, supporting the mobility of the nodes can be regarded as a purpose of key management schemes. In our previous work, we presented a key management scheme that was more efficient with respect to security and connectivity compared to the other ones. In that scheme, it is assumed that the nodes are static. In this paper we are going to present a scheme that supports the mobility of the nodes and makes the initial scheme more flexible. The basic criterion for the evaluation of the scheme is the communication overhead. First, the nodes establish a secure link with the cluster heads and then establish a secure link among themselves with the help of the cluster heads. We have analyzed this scheme with regards to the communication overhead and we will compare it with the other schemes.
Similar content being viewed by others
References
Eschenauer, L., & Gligor, V. D. (2002). A key management scheme for distributed sensor networks. In Proceedings of the 9th ACM conference on computer and communications security (pp. 41–47).
Du X., Xiao Y., Guizani M., Chen H.-H. (2007) An effective key management scheme for heterogeneous sensor networks. Ad Hoc Networks 5(1): 24–34
Chan, H., Perrig, A., & Song, D. (2003). Random key pre distribution schemes for sensor networks. In IEEE symposium on research in security and privacy.
Lu, K., Qian, Y., & Hu, J. (2006). A framework for distributed key management schemes in heterogeneous wireless sensor networks. In IEEE international performance computing and communications conference (pp. 513–519).
Traynor, P., Kumar, P., Bin Saad, H., Cao, G. & La Porta, T. (2006). Establishing pair-wise keys in heterogeneous sensor networks. In Proceedings of the 25th IEEE international conference on computer communications. doi:10.1109/INFOCOM.2006.260.
Traynor P., Kumar R., Bin Saad H., Cao G., La Porta T. (2007) Efficient hybrid security mechanisms for heterogeneous sensor networks. IEEE Transactions Mobile Computing 6(6): 663–677
Price, A., Kosaka, K., & Chatterjee, S. (2004). A secure key management scheme for sensor networks. In Proceedings of the 10th Americas conference on information systems.
Liu, D.D., & Ning, P. (2003). Location-based pairwise key establishments for static sensor networks. In Proceedings of the 1st ACM workshop on security of ad hoc and sensor networks (pp. 72–82).
Liu D., Ning P., Li R. (2005) Establishing pairwise keys in distributed sensor networks. ACM Transactions on Information and System Security 8(1): 41–77
Du W., Deng J., Han Y. S., Varshney P. K., Katz J., Khalili A. (2005) A pairwise key pre-distribution scheme for wireless sensor networks. ACM Transactions on Information and System Security 8(2): 228–258
Banihashemian, S., & Ghaemi Bafghi, A. (2010). A new key management scheme in heterogeneous wireless sensor networks. In 12th international conference on advanced communication technology (pp. 141–146).
Banihashemian, S., & Ghaemi Bafghi, A. (2010). Performance study of RKPH key management protocol and analysis of effective parameters on it. In Proceeding national csicc2010 (in pesinan).
Banihashemian, S., & Ghaemi Bafghi, A. (2010). Alternative shared key replacement in heterogeneous wireless sensor networks. In 8th annual communication networks and services research conference (pp. 174–178).
Zhu, S., Setia, S., & Jajodia, S. (2003). LEAP: Efficient security mechanisms for large-scale distributed sensor networks. In Proceedings of the 10th ACM conference on computer and communications security (pp. 62–72).
Chan, H., & Perrig, A., (2005). PIKE: Peer intermediaries for key establishment in sensor networks. In Proceedings of INFOCOM 2005 (pp. 524–535).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Banihashemian, S., Ghaemi Bafghi, A. & Yaghmaee Moghaddam, M.H. Centralized Key Management Scheme in Wireless Sensor Networks. Wireless Pers Commun 60, 463–474 (2011). https://doi.org/10.1007/s11277-011-0302-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-011-0302-y