Abstract
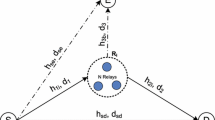
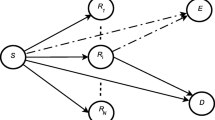
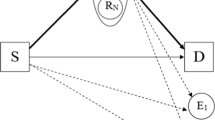
As demand for highly reliable data transmission in wireless networks has increased rapidly, cooperative communication technology has attracted a great deal of attention. In cooperative communication, some nodes, called eavesdroppers, illegally receive information that is intended for other communication links at the physical layer because of the broadcast characteristics of the wireless environment. Hence, Physical Layer Security is proposed to secure the communication link between two nodes against access by the eavesdroppers. In this paper, we propose and analyze the performance of decode-and-forward schemes with the best relay selection under Physical Layer Security with two operation protocols: first, only cooperative communication, and second, a combination of direct transmission and cooperative communication (the incremental protocol). In these schemes, a source transmits data to a destination with the assistance of relays, and the source-destination link is eavesdropped by one other node. The best relay is chosen in these proposals based on the maximum Signal-to-Noise ratio from the relays to the destination, and satisfies the secure communication conditions. The performance of each system is evaluated by the exact outage probability of the data rate over Rayleigh fading channels. Monte-Carlo results are presented to verify the theoretical analysis and are compared with a direct transmission scheme under Physical Layer Security and compared with each other.






Similar content being viewed by others
References
Nosratinia, A., Hunter, T. E., & Hedayat, A. (2004). Cooperative communication in wireless networks. IEEE Communications Magazine, 42, 74–80.
Laneman, J. N., Tse, D. N. C., & Wornell, G. W. (2004). Cooperative diversity in wireles networks: Efficient protocols and outage behavior. IEEE Transactions on Information Theory, 50, 3062–3080.
Krikidis, I., Thompson, J., Mclaughlin, S., & Goertz, N. (2008). Amplify-and-forward with partial relay selection. IEEE Communications Letters, 12, 235–237.
Xia, Minghua, & Aissa, S. (2012). Cooperative AF relaying in spectrum-sharing systems: Outage probability analysis under co-channel interferences and relay selection. IEEE Transactions on Communications, 60, 3252–3262.
Ikki, S. S., & Ahmed, M. H. (2010). Performance analysis of adaptive decode-and-forward cooperative diversity networks with best-relay selection. IEEE Transaction on Communications, 58, 68–72.
Tourki, K., Yang, Hong-Chuan, & Alouini, M.-S. (2011). Accurate outage analysis of incremental decode-and-forward opportunistic relaying. IEEE Transactions on Wireless Communications, 10, 1021–1025.
Ju, Min Chul, Kim, Il-Min, & Kim, Dong In. (2012). Joint relay selection and relay ordering for DF-based cooperative relay networks. IEEE Transaction on Communications, 60, 908–915.
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54, 1355–1367.
Bloch, M., Barros, J., Rodrigues, M. R. D., & McLaughlin, S. W. (2008). Wireless information-theoretic security. IEEE Transactions on Information Theory, 54, 2515–2534.
Goel, S., & Negi, R. (2008). Guaranteeing secrecy using artificial noise. IEEE Transactions on Wireless Communications, 7, 2180–2189.
Dong, Lun, Han, Zhu, Petropulu, A. P., & Poor, H. V. (2010). Improving wireless physical layer security via cooperating relays. IEEE Transactions on Signal Processing, 58, 1875–1888.
Krikidis, I., Thompson, J. S., & McLaughlin, S. (2009). Relay selection for secure cooperative networks with jamming. IEEE Transactions on Wireless Communication, 8, 5003–5011.
Krikidis, I. (2010). Opportunistic relay selection for cooperative networks with secrecy constraints. IET Communications, 4, 1787–1791.
Sun, X., Xu, W., Jiang, M., & Zhao, C. (2012). Opportunistic selection for decode-and-forward cooperative networks with secure probabilistic constraints. Wireless Personal Communications. doi:10.1007/s11277-012-0771-7.
Ikki, S. S., Uysal, M., Ahmed, M. H. (2009). Performance analysis of incremental-relay-selection decode-and-forward technique. Global Telecommunications Conference GLOBECOM, 1–6.
Duy T. T., & Kong, H.-Y. (2012). Performance analysis of two-way hybrid decode-and-amplify relaying scheme with relay selection for secondary spectrum access. Wireless Personal Communications. doi:10.1007/s11277-012-0616-4.
Acknowledgments
This work was supported by 2013 Special Research Fund of Electrical Engineering at University of Ulsan
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix A: Solving the Probability \(\Pr \left[ {D_2 =\left\{ \varnothing \right\} } \right] \) in Formula (19)
Substituting (9) and (10) into (19), we obtain (36) as
The probability \(\Pr \left[ {\gamma _{2i} <\gamma _{3i} } \right] \) is given as
where \(f_{2i} (\cdot ), f_{3i} (\cdot )\) and \(F_{2i} (\cdot )\) are the probability density functions (PDF) of the exponential random variables \(\gamma _{2i} , \gamma _{3i} \) and the CDF of the exponential random variable \(\gamma _{2i}\), respectively, and given as
From (37), the probability \(\Pr \left[ {D_2 =\left\{ \varnothing \right\} } \right] \) in (36) is obtained as
Appendix B: Solving the Probability in (24)
We note that there are \(C_M^{K}\) possible ways for the subset \(D_{2}\). Hence, formula (24) is expressed as
Substituting (17) and (9) into (42), we obtain (43) as
The probability \(\Pr \left[ {\gamma _{3i} <\gamma _{2i} <\theta } \right] \) is derived as
where \(f_{2i} (\cdot ), f_{3i} (\cdot )\)and \(F_{2i} (\cdot )\) are given in (38), (39) and (40) in “Appendix A”, respectively.
Substituting (37) and (44) into (43), we have the probability \(\Delta \) in (24) as
Appendix C: Solving the Probability in (28)
Similar to “Appendix B”, there are \(C_M^K \) possible ways for the subset \(D_{2}\). Hence, formula (28) is expressed as
Substituting (17) and (10) into (46), formula (47) is obtained as
The probability \(\Pr \left[ {\gamma _{2i} >\gamma _{3i} >\theta } \right] \) is derived as
where \(f_{2i} (\cdot )\) and \(f_{3i} (\cdot )\) are given in (38) and (39) in “Appendix A”, respectively; \(F_{3i} (\cdot )\) is the CDF of the exponential random variable \(\gamma _{3i} \), and given as
Substituting (37) and (48) into (47), we have the probability \(\Omega \) in (28) as
Rights and permissions
About this article
Cite this article
Son, P.N., Kong, H.Y. Exact Outage Probability of a Decode-and-Forward Scheme with Best Relay Selection Under Physical Layer Security. Wireless Pers Commun 74, 325–342 (2014). https://doi.org/10.1007/s11277-013-1287-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-013-1287-5