Abstract
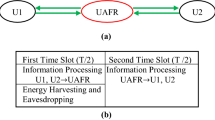
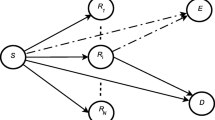
Two cooperative communication protocols, two-way and one-way half-duplex relayings, are investigated and then compared in the amplify-and-forward (AF) mode. The relay is assumed to play the roles of eavesdropper and relay (i.e., an untrusted relay). With a fair power constraint at each node, the secrecy rate of the one-way relaying protocol is proved to be zero strictly. For the two-way relaying protocol, the signal-to-noise ratio (SNR) threshold is derived, above which the secrecy rate is non-zero. Defining a parameter, namely mistrust level, and non-zero secrecy rate can be achieved for the one-way relaying protocol in certain range of the mistrust level at high SNR. With a fair total power constraint, no matter how unreliable the relay is, the two-way AF half-duplex relaying protocol is proved to be a better choice under high SNR.




Similar content being viewed by others
References
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54(8), 1355–1387.
Csiszár, I., & Körner, J. (1978). Broadcast channels with confidential messages. IEEE Transactions on Information Theory, 24, 339–348.
Leung-Yan-Cheong, S. K., & Hellman, M. E. (1978). The Gaussian wiretap channel. IEEE Transactions on Information Theory, 24, 451–456.
Dong, L., et al. (2010). Improving wireless physical layer security via cooperating relays. IEEE Transactions on Signal Processing, 58(3), 1875–1888.
Zhu, J., Mo, J., & Tao, M. (2010). Cooperative secret communication with artificial noise in symmetric interference channel. IEEE Communications Letters, 14(10), 885–887.
Zhang, R., et al. (2010). Physical layer security for two way relay communications with friendly jammers. In IEEE GLOBECOM 10, Miami, FL, 2010.
Jeong, C., Kim, I. M., & Kim, D. I. (2012). Joint secure beamforming design at the source and the relay for an amplify-and-forward MIMO untrusted relay system. IEEE Transactions on Signal Processing, 60(1), 310–325.
Wang, H. M., Yin, Q., & Xia, X. G. (2012). Distributed beamforming for physical-layer security of two-way relay networks. IEEE Transactions on Signal Processing, 60(7), 3532–3545.
Krikidis, I. (2010). Opportunistic relay selection for cooperative networks with secrecy constraints. IET Communications, 4(15), 1787–1791.
Han, Y., et al. (2009). Performance bounds for two-way amplify-and-forward relaying. IEEE Transactions on Wireless Communications, 8(1), 432–439.
Ping, J., & Ting, S. H. (2009). Rate performance of AF two-way relaying in low SNR region. IEEE Communications Letters, 13(4), 233–235.
He, X., & Yener, A. (2008). Two-hop secure communication using an untrusted relay: A case for cooperative jamming. In IEEE GLOBECOM 08, New Orleans, LA, 2008.
Gómez Mármol, F., Martínez Pérez, G., & Gómez Skarmeta, A. F. (2009). TACS, a trust model for P2P networks. Wireless Personal Communications, 51(1), 153–164.
Acknowledgments
The authors thank the anonymous reviewers for the valuable comments and suggestions. The work is supported by the National Natural Science Foundation of China (Grant Nos. 61262084 and 61141007), the Natural Science Foundation of Jiangxi Province, China (Grant Nos. 20132BAB201019 and 20114BAB201018), the Foundation for Young Scientists of Jiangxi Province (Jinggang Star) (Grant No. 20122BCB23002), and the Opening Project of Shanghai Key Laboratory of Integrate Administration Technologies for Information Security (No. AGK2012005).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhou, N., Chen, X., Li, C. et al. Secrecy Rate of Two-Hop AF Relaying Networks with an Untrusted Relay. Wireless Pers Commun 75, 119–129 (2014). https://doi.org/10.1007/s11277-013-1351-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-013-1351-1