Abstract
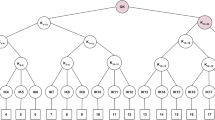
In deep space delay tolerant networks rekeying expend vast amounts of energy and delay time as a reliable end-to-end communication is very difficult to be available between members and key management center. In order to deal with the question, this paper puts forwards an autonomic group key management scheme for deep space DTN, in which a logical key tree based on one-encryption-key multi-decryption-key key protocol is presented. Each leaf node with a secret decryption key corresponds to a network member and each non-leaf node corresponds to a public encryption key generated by all leaf node’s decryption keys that belong to the non-leaf node’s sub tree. In the proposed scheme, each legitimate member has the same capability of modifying public encryption key with himself decryption key as key management center, so rekeying can be fulfilled successfully by a local leaving or joining member in lack of key management center support. In the security aspect, forward security and backward security are guaranteed. In the efficiency aspect, our proposed scheme’s rekeying message cost is half of LKH scheme when a new member joins, furthermore in member leaving event a leaving member makes tradeoff between computation cost and message cost except for rekeying message cost is constant and is not related to network scale. Therefore, our proposed scheme is more suitable for deep space DTN than LKH and the localization of rekeying is realized securely.






Similar content being viewed by others
References
Posner, E. C., & Stevens, R. (1984). Deep space communication—past, present, and future. IEEE Communications Magazine, 22, 8–21.
Williamson, M. (1998). Deep space communications. IEE Review, 44(3), 119–122.
Cesarone, R. J., Abraham, D. S., & Deutsch, L. J. (2007). Prospects for a next-generation deep-space network. Proceedings of the IEEE, 95(10), 1902–1915.
Bhasin, K., Hayden, J., & Agre, J. R. (2001). Advanced communication and networking technologies for Mars exploration. In 19th annual AIAA international communications satellite systems conference, Toulouse, France.
Weber, W. J., Cesarone, R. J., & Abraham, D. S. (2006). Transforming the deep space network into the interplanetary network. Acta Astronautica, 58(8), 411–421.
Bhasin, K., & Hayden, J. L. (2002). Space Internet architecture and technologies for NASA enterprises. International Journal of Satellite Communications, 20(5), 311–332.
Naitong, Z., Hui, L., & Qinyu, Z. (2007). Thought and developing trend in deep space exploration and communication. Journal of Astronautics, 28(4), 786–793.
Jianshe, Y. E., Shijie, S., & Rongjun, S. (2010). Research on DTNfor deep space communications. Journal of Astronautics, 11(4), 941–950.
Yu, C., Xin, M., & Lei, Z. (2012). Analysis of protocol of space information network. Computer Technology and development, 22(6), 1–5.
Burleigh, S., Hooke, A., & Torgerson, L. (2003). Delay tolerant networking: An approach to interplanetary internet. IEEE Communications Magazine, 41(6), 128–136.
Mohanchur, S., Kaushal, K. S., & Kankar, S. D. (2011). Delay resistant transport protocol for deep space communication. International Journal of Communicaitons, Network and System Sciences, 4, 122–132.
Roy, C. A., Baras, J. S., Hadjitheodosiou, M., & Rentz, N. (2005). Hybrid networks with a space segment-topology design and security issues. In Military communications conference, 2005 (vol. 3, pp. 1414–1420). MILCOM 2005. IEEE.
Johann, V. D. M., Dawoud, D., & Tephen, M. (2007). A survey on peer-to-peer key management for mobile ad hoc networks. ACM Computing Surveys, 39(1), 1–46.
Yacine, C., & Hamida, S. (2005). Group key management protocols: A novel taxonomy. International Journal of Information Technology, 2(2), 105–119.
Rani, T. P., & Jaya, K. C. (2012). Survey on key pre distribution for security in wireless sensor networks. Lecture Notes of the Institute for Computer Sciences, 84, 248–252.
Dandan, L., Runtong, Z., & Chuanchen, W. (2012). Efficient group key management scheme with hierarchy structure. Chinese Journal of Electronics, 1(2), 249–253.
Seba, H., Lagraa, S., & Kheddouci, H. (2012). Alliance-based clustering scheme for group key management in mobile ad hoc networks. Journal of Supercomputing, 61(3), 481–501.
Juhyung, S., Junsik, L., & Seungwoo, S. (2010). Topological key hierarchy for energy-efficient group key management in wireless sensor networks. Wireless Personal Communications, 52(2), 359–382.
Elisavet, K. (2011). Efficient cluster-based group key agreement protocols for wireless ad hoc networks. Journal of Network and Computer Applications, 34(1), 384–393.
Klaoudatou, E., & Konstantinou, E. (2011). A survey on cluster-based group key agreement protocols for WSNs. Communications Surveys and Tutorials, IEEE, 13(3), 429–442.
Zhiwen, W., & Shaozi, Li. (2012). A secure and high-efficient dynamic key management scheme for group communication using optimized GDH. ICIC Express Letters, 6(7), 1815–1820.
Pen, X., Jingsha, H., & Yingfang, F. (2012). Distributed group key management in wireless mesh networks. International Journal of Security and its Applications, 6(2), 115–120.
Suganthi, N., Sumathi, V., & Mohanapriyha, R. S. (2011). Secure group key management for dynamic sensor networks. Journal of Computer Sciences, 7(7), 997–1002.
Yingli, S., Cruickshank, H., Moseley, M., & Ashworth, J. (2011). Security architecture for satellite services over cryptographically heterogeneous networks. In Proceedings of the 2011 6th international ICST conference on communications and networking in China (pp. 1093–1098).
Drakakis, K. E., Panagopoulos, A. D., & Cottis, P. G. (2003). Overview of satellite communication networks security: Introduction of EAP. International Journal of Security and Networks, 4(3), 164–170.
EunJ, Y., KeeY, Y., & Jeong, W. H. (2011). An efficient and secure anonymous authentication scheme for mobile satellite communication systems. EURASIP Journal on Wireless Communications and Networking, 86, 1–10.
Howarth, M. P., Iyengar, S., Sun, Z., & Cruickshank, H. (2004). Dynamics of key management in secure satellite multicast. IEEE Journal on Selected Areas in Communications, 2(2), 308–319.
Arslan, M. G., & Alagöz, F. (2006). Security issues and performance study of key management techniques over satellite links. In 11th international workshop on computer-aided modeling, analysis and design of communication links and networks (pp. 122–128).
Ahmad, K., Bakhache, B., El, A.S., & Sindian, S. (2012). A scalable key management scheme for secure IP multicast over DVB-S using chaos. In Proceedings of the Mediterranean electrotechnical conference—MELECON (pp. 736–740).
Chung, K. W., Mohamed, G., & Simon, S. (2000). Secure group communications using key graphs. IEEE/Acm Transactions on Networking, 8(1), 31–37.
Zhen, W., Xuehui, D., & Yi, S. (2011). Group key management scheme based on proxy re-cryptography for near-space network. International Conference on Network Computing and Information Security, 2011, 52–57.
Zhong, Y., & Jian-feng, M. (2011). Identity based group key management scheme for LEO/MEO double-layer space information network. Journal of Astronautics, 32(7), 1551–1557.
Steiner, M., & Waidner, M. (1996). Diffie–Hellman key distribution extended to groups. In Proceedings of the 3rd ACM symposium on computer and communications security (vol. 1, pp. 31–37).
Peoples, C., Parr, G., Scotney, B., Moore, A. (2011). Autonomic context-aware management in interplanetary communications systems. IEEE Aerospace and Electronic Systems Magazine, 26(2), 26–33.
Bokor, E. (2001). Automating operations for NASA’s deep space network (DSN). In Aerospace conference, 2001. IEEE proceedings (vol. 7, pp. 3383–3390).
Wódczak, M., & Wódczak, M. (2010). Future autonomic cooperative networks. In 2nd international ICST conference on mobile networks and management. MONAMI (pp. 71–78).
Coronado, G.L.C., & PérezL, C. (2011). An autonomous decentralized public key infrastructure. In Proceedings—2011 10th international symposium on autonomous decentralized systems (pp. 409–414).
Harney, H., & Muckenhirn, C. (1997). Group key management protocol (GKMP) architecture, RFC 2094.
Feng, B., Robert, H. D., & Huafei, Z. (2003). Variations of Diffie–Hellman problem. Lecture Notes in Computer Science, 2836(2003), 301–312.
Jonathan, K., & Yehuda, L. (2007). Introduction to modern cryptography. London: Chapman & Hall/CRC Press.
Acknowledgments
This work is supported by the National Science Foundation Project of P. R. China (No. 60903004, No. 61003250, No. 61170014), the National Science Foundation for the Doctoral Program of Higher Education of China under Grant No. 20090006110014, the Anhui Academic Science Foundation No. KJ2013B001 and the Beijing Municipal Science Foundation under Grant No. 4102042. Jian Zhou et al. are very grateful to the National Science Foundation of China (NNSFC) for the support.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhou, J., Song, M., Song, J. et al. Autonomic Group Key Management in Deep Space DTN. Wireless Pers Commun 77, 269–287 (2014). https://doi.org/10.1007/s11277-013-1505-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-013-1505-1