Abstract
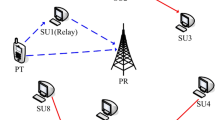
In this paper, we propose secondary relaying schemes in cognitive spectrum leasing. In the proposed protocols, a primary transmitter uses rateless code to transmit its data to a primary receiver. In the secondary network, \(M\) secondary transmitters are ready to help the primary transmitter forward the data to a primary receiver so that they can find opportunities to transmit their data. For performance evaluation, we derive the average outage probability, the average number of encoded packets transmitted by the primary transmitter, the average number of remaining time slots for secondary network and the average capacity of the secondary network over Rayleigh fading channels. Various Monte-Carlo simulations are presented to verify the derivations.





Similar content being viewed by others
References
Mitola, J., & Maguire, G. Q. (1999). Cognitive radio: Making software radios more personal. IEEE Personal Communications, 6(4), 13–18.
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220.
Qing, Z., & Sadler, B. M. (2007). A survey of dynamic spectrum access. IEEE Signal Processing Magazine, 24(3), 79–89.
Khuong, H. V. (2013). Performance evaluation of underlay cognitive multi-hop networks over Nakagami-m fading channels. Wireless Personal Communications, 70(1), 227–238.
Duy, T. T., & Kong, H. Y. (2013). Performance analysis of incremental amplify-and-forward relaying protocols with Nth best partial relay selection under Interference constraint. Wireless Personal Communications, 71(4), 2741–2757.
Laneman, J. N., & Wornell, G. W. (2003). Distributed space-time coded protocols for exploiting cooperative diversity in wireless networks. IEEE Transactions on Information Theory, 49, 2415–2425.
Laneman, J. N., Tse, D. N. C., & Wornell, G. W. (2004). Cooperative diversity in wireless networks: Efficient protocols and outage behavior. IEEE Transactions on Information Theory, 50, 3062–3080.
Han, Y., & Ting, S. H. (2009). Cooperative decode-and-forward relaying for secondary spectrum access. IEEE Transactions on Wireless Communications, 8(10), 4945–4950.
Chen, Z., & Zhang, X.-D. (2012). Cooperative spectrum sharing based on amplify and forward relaying in cognitive radio networks. Wireless Personal Communications, 67(3), 585–598.
Mackay, D. J. C. (2005). Fountain codes. Proceedings of IEEE Communication, 152, 1062–1068.
Liu, X., & Lim, T. J. (2009). Fountain codes over fading relay channels. IEEE Transactions on Wireless Communications, 8(6), 3278–3287.
Molisch, A. F., Mehta, N. B., Yedidia, J. S., & Zhang, J. (2007). Performance of fountain codes in collaborative relay networks. IEEE Transactions on Wireless Communications, 6(11), 4108–4119.
Nikjah, R., & Beaulieu, N. C. (2008). Achievable rates and fairness in rateless coded relaying schemes. IEEE Transactions on Wireless Communications, 7(11), 4439–4444.
Qin, S., Feng, G., & Zhang, Y. (2010). Capacity bounds of cooperative communications with fountain codes. In Proceedings of IEEE WCNC, pp. 1–4.
Chen, Y., Huang, H., Zhang, Z., Qiu, P., & Lau, V. (2008). Cooperative spectrum access for cognitive radio network employing rateless code. In Proceedings of IEEE ICC workshop, pp. 326–331.
Wang, X., Chen, W., & Cao, Z. (2009). A rateless coding based multi-relay cooperative transmission scheme for cognitive radio networks. In Proceedings of IEEE GLOBECOM, pp.1–6.
Gradshteyn, I. S., & Ryzhik, I. M. (2000). Table of integrals, series, and products (6th ed.). New York: Academic Press.
Acknowledgments
This work was supported by 2014 Special Research Fund of Electrical Engineering at University of Ulsan.
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
Derivation of (12)
First, we set the random variable \(X\) as \(X=\sum _{j=1,j\ne i}^M {\gamma _{4ij}}\). Next, we use the moment generating function (MGF) to find the CDF of \(X\). In addition, the MGF of \(\gamma _{4ij}\) is \(\lambda _{4ij}/\left( {\lambda _{4ij}+s}\right) \). Hence, due to the independence of \(\gamma _{4ij}\), the MGF of \(X\) is given by
Using partial fraction expansion and under the condition that the \(\gamma _{4ij}\) are different from each other, (46) can be decomposed into
where \(\alpha _j =\lambda _{ST_j ,SR_i } \prod _{k=1,k\ne j}^M {\frac{\lambda _{ST_k ,SR_i } }{\lambda _{ST_k ,SR_i } -\lambda _{ST_j ,SR_i } }} \).
Applying the inverse Laplace transform for (47), we can get the PDF of \(X\) as follows:
Now, considering the random variable \(Y=1+X\), it is easy to obtain the PDF of \(Y\) as
Since \(\gamma _{SR_i } =\gamma _{4i} /Y\), the CDF of \(\gamma _{SR_i} \) is given as
Substituting (49) into (50) and after some manipulation, we get
Differentiating (51) with respect to \(z\), we obtain (12).
Rights and permissions
About this article
Cite this article
Duy, T.T., Kong, H.Y. Secondary Spectrum Access in Cognitive Radio Networks Using Rateless Codes over Rayleigh Fading Channels. Wireless Pers Commun 77, 963–978 (2014). https://doi.org/10.1007/s11277-013-1546-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-013-1546-5