Abstract
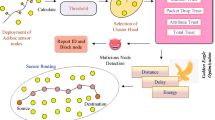
In Wireless Sensor Network (WSN) applications, nodes are deployed in public domains that are prone to be attacked by various types of attacks wherein the data confidentiality, integrity and authentication are compromised. In this paper, we propose Agent based SEcured Routing using Trusted neighbors (ASERT) in WSN. ASERT selects trustworthy neighbors and establishes secured routes using software agents. ASERT operates in following phases. (1) Defining Safeguard Agency (SA) and Routing Agency (RA), both consisting of static and mobile agents and a knowledge base. (2) Identification of trustworthy neighbor nodes by SA with trust model that consists of probability and Message Authentication Codes (MAC) model. (3) Probability model estimates the trustworthy channel and trustworthy nodes whereas MAC model ensures them. (4) MAC’s are dynamically computed by agents by generating the keys with the help of Random Oracle Extractor (ROE). (5) RA establishes secured routes from source to the sink node using agents. (6) Agents effectively identify possible security threats on wireless channel and node. (7) An improvement in packet delivery ratio, packet delivery latency, route maintenance overhead, memory overhead and energy consumption is achieved in ASERT as compared to two protocols, namely, Bio-inspired Trust and Reputation model in WSN (BTRM-WSN) using ant colony based approach and Ambient Trust Sensor Routing that uses trust combined with location information for routing.













Similar content being viewed by others
Explore related subjects
Discover the latest articles and news from researchers in related subjects, suggested using machine learning.References
Kavitha, T., & Sridharan, D. (2010). Security vulnerabilities in wireless sensor networks: A survey. Journal of Information Assurance and Security, 5, 31–44.
Ozdemir, S., & Xiaa, Y. (2011). Integrity protecting hierarchical concealed data aggregation for wireless sensor networks. Computer Networks, 55, 1735–1746.
Pham, V. A., & Karmouch, A. (1998). Mobile software agents: An Overview. IEEE Communications Magazine, 36(7), 26–37.
Chess, D., Benjamin, G., Harrison, C., Levine, D., & Paris, C. (1995). Itinerant agents in mobile computing. IEEE Personal Communication Magazine, 2, 35–49.
Zhang, Y., Yang, J., Li, W., Wang, L., & Jin, L. (2010). An authentication scheme for locating compromised sensor nodes in WSNs. Journal of Network and Computer Applications, 33, 50–62.
Marmol, F. G., & Perez, G. M. (2011). Providing trust in wireless sensor networks using a bio-inspired technique. Telecommunication System, 46, 163–180.
Yim, S. J., & Choi, Y. H. (2012). Neighbor-based malicious node detection in wireless sensor networks. Wireless Sensor Networks, 4, 219–225.
Karlof, C., & Wagner, D. (2003). Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Networks, 1, 293–315.
Bin, T., Xian, Y. Y., Dong, L., Qi, L., & Xin, Y. (2010). A security framework for wireless sensor networks. The Journal of China Universities of Posts and Telecommunications, 17, 118–122.
Mohd Yussoff, Y., Hashim, H., & Dani Baba, M. (2012). Identity-based trusted authentication in wireless sensor network. International Journal of Computer science, 9(3), 1694–0814.
Leligou, H. C., Trakadas, P., Maniatis, S., Karkazis, P., & Zahariadis, T. (2012). Combining trust with location information for routing in wireless sensor networks. Wireless Communications and Mobile Computing, 12(12), 1091–1103.
Khalil, I., Bagchi, S., Rotaru, C. N., & Shroff, N. B. (2010). UNMASK: utilizing neighbor monitoring for attack mitigation in multihop wireless sensor networks. Ad Hoc Networks, 8(2), 148–164.
Bao, F., Chen, I.-R., Chang, M. J., & Cho, J.-H. (2012). Hierarchical trust management for wireless sensor networks and its applications to trust-based routing and intrusion detection. IEEE Transaction on Network Services Management, 9(2), 169–183.
Zhan, G., Shi, W., & Deng, J. ((2010). TARF: A Trust-aware routing framework for wireless sensor networks. In European Conference on Wireless Sensor Networks (EWSN) (pp. 65–80).
Zhan, G., Shi, W., & Deng, J. (2013). Design and Implementation of TARF: A Trust-aware routing framework for WSNs. IEEE Transactions on Dependable Secure Computing, 9(2), 184–197.
Babu, S. S., Raha, A., & Naskar, M. K. (2011). A Direct trust dependent link state routing protocol using route trusts for WSNs (DTLSRP). Scientific Research, Wireless Sensor Network, 3, 125–134.
Srivastava, A. K., & Goel, A. (2011). Security solution for WSN using mobile agent technology. International Journal of Research and Reviews in Wireless Sensor Networks (IJRRWSN), 1(3), 48–52.
Zdarsky, F. A., Robitzsch, S., & Banchs, A. (2011). Security analysis of wireless mesh back-hauls for mobile networks. Journal of Network and Computer Applications, 34(2), 432–442.
Lange, D. B., & Oshima, M. (1999). Seven good reasons for mobile agents. Communications of the ACM, 42(3), 88–89.
Chen, M., Kwon, T., Yuan, Y., & Leung, V. C. M. (2006). Mobile agent based wireless sensor networks. Journal of Computers, 1(1), 14–21.
Pecho, P., Zboril, F, Jr, Drahansky, M., & Hanacek, P. (2009). Agent platform for wireless sensor network with support for cryptographic Protocols. Journal of Universal Computer Science, 15(5), 992–1006.
Reddy, Y. B. (2012). Trust-based approach in wireless sensor networks using an agent to each cluster. International Journal of Security, Privacy and Trust Management(IJSPTM), 1(1), 19–26.
Sheela, D., Nirmala S., Nath, S., & Mahadevan, G. (2011, July). A Recent technique to detect sink hole attacks in WSN. White paper, Anna University.
Mpitziopoulos, A., Gavalas, D., Konstantopoulos, C., & Pantziou, G. (2009). JAID: An algorithm for data fusion and jamming avoidance on distributed sensor networks. Pervasive and Mobile Computing, 5, 135–147.
Boukerch, A., Xu, L., & EL-Khatib K., (2007). Trust-based security for wireless ad hoc and sensor networks. Computer Communications, 30, 2413–2427.
Geetha, D. D. Nalini, N., & Biradar, R. C. (2013). Trusted neighbor identification in wireless sensor networks: agent based approach. In IEEE international conference on advanced research in engineering and technology (ICARET-2013) (pp. 112–117) Vijayawada, India.
Available at: http://en.wikipedia.org/wiki/Randomness_extractor. Browsed on October 2012.
Dodis, Y., Gennaro, R., Hastad, J., Krawczyk, H., & Rabin, T. (2004). Randomness extraction and key derivation using the CBC, cascade and HMAC Modes. In: Annual international cryptology conference (CRYPTO) (pp. 494–510). Santa Barbara, California, USA.
Available at: http://en.wikipedia.org/wiki/List_of_wireless_sensor_nodes. Accessed on March 2013.
Acknowledgments
The authors wish to thank Visvesvaraya Technological University (VTU), Karnataka, INDIA, for funding the part of the project under VTU Research Scheme (Grant No. VTU/Aca./2011-12/A-9/753, Dated: 5 May 2012.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Devanagavi, G.D., Nalini, N. & Biradar, R.C. Trusted Neighbors Based Secured Routing Scheme in Wireless Sensor Networks Using Agents. Wireless Pers Commun 78, 1–28 (2014). https://doi.org/10.1007/s11277-014-1704-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-014-1704-4