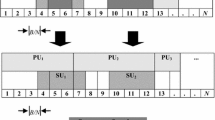
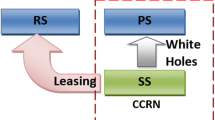
Abstract
The underlay paradigm is an important spectrum sharing model for cognitive-based secondary networks, in which the interference temperature limit (ITL) quantifies the amount of resources that can be shared by a secondary network and power control is known to play a crucial role. Many recent studies have discussed ITL-based underlay spectrum sharing and power control, but issues such as ITL decision-making and the value range for the ITL have not been analyzed. We also know that the presence of secondary network interference may increase the transmission power of primary users (PUs) who have hard traffic quality of service requirements. This additional resource sharing cost (increased transmit power) may discourage the PUs from sharing resources with secondary networks; the motivation in favor of resource sharing has not yet been completely explored. To address these unresolved problems, underlay-based spectrum sharing is reconsidered in this paper, using the scenario in which a cell primary network coexists with a cell secondary network that shares the spectrum resource with the primary network. First, under a fixed interference cap (IC) design, a simple primary network power control scheme is introduced. We then discuss IC design issues from the primary network point of view. Finally, a primary network interference compensation-based dynamic spectrum leasing scheme is proposed, in which the primary network suboptimal price search and SU’s power iteration algorithm are also provided. We use simulation to demonstrate the performance of our proposed schemes.





Similar content being viewed by others
Notes
\(\rho (\mathbf{F}^{(p)})\) is defined as the spectral radius of matrix \(\mathbf{F}^{(p)}\). According to the Perron-Frobenius theorem [43], we know that if we denote eigenvalues of matrix \(\mathbf{F}^{(p)}\) by \(\lambda _{1}, \lambda _{2},\ldots , \lambda _{\mathrm{k}}^{(\mathrm{p})}\), then we have \(\rho ({\mathbf{F}^{(p)}})= \max {\vert }\lambda _{i}{\vert }, i= 1,2, \ldots , k^{(p)}\).
One may argue that the APO may not be the only performance degradation for primary network/PUs or the APO may not be the unique performance loss expression; other performance loss/expressions, such as bit-rate-decease, may also exist. While, for our considered scenario, because we have assumed PUs with hard-QoS (the minimum SINR requirements), that is, their minimum SINR requirements must be satisfied. Then the presence of secondary network interference will surely increase the transmission power of PUs, that is, the APO.
Without considering the secondary network interference, the feasibility of primary network power control with MTPCs has been analyzed in [28].
Herein, we always assume that all PUs in the network will truthfully report their residual power, and the motivation of spending additional power (or APO) to support the coexistence of SUs is that all PUs will receive some compensation.
For the primary network, the immediate effects of the presence of secondary network interference are a reduction in the available SINR for PUs and a bit-rate decrease or bit-error-rate (BER) increase. However, as mentioned earlier, we have restricted that the PUs have hard QoS requirements, so that all PUs have to increase their transmission power to achieve their SINR targets. Thus, we quantify the PUs’ transmit power increase by APO and use it as the cost of resource sharing.
As mentioned earlier, the unit APO price \(\rho \) reflects how PUs care for their power consumption. For our interference compensation-based DSL, it can be seen as a power trading between the primary and secondary networks in which the PUs use more transmission power to support the coexistence of SUs to earn rewards, while the SUs obtain IC resources but with interference-compensated payment.
In this setting, the optimal and suboptimal prices are the same, as can be noted in Fig. 2(b). Therefore, we did not discriminate them in the following discussion.
Because the SUs have a co-located receiver SUBS and the same primary and secondary network signal correlation coefficient \(1/G_{p}^{(s)}\), all SUs suffer from same primary network interference.
As mentioned earlier, the case \(\lambda _{0}=0\) is for interweave-based spectrum sharing. As the motivation of underlay-based spectrum sharing for the primary network is to obtain external revenue, we always have \(\lambda _{0}>0\).
The cases \(\lambda _0 =\max _{i\in \mathrm{A}(\lambda _0)} \left( {2\omega _i^{(s)} \gamma _{i,tar}^{(s)}}\right) \) and \(\lambda _{0}=0\) are omitted here for lack of sense, as mentioned earlier (please see “Appendix1”).
References
Mitola, J., & Maguire, G. Q. (1999). Cognitive radio: Making software radios more personal. IEEE Personal Communications, 6, 13–18.
Zhao, Q., & Sadler, B. M. (2007). A survey of dynamic spectrum access. IEEE Signal Processing Magazine, 24(3), 79–89.
Federal Communications Commission (2002). Spectrum policy task force report. ET Docket No. 02–135, Nov 2002.
Huang, J., Berry, R., & Honig, M. L. (2006). Auction-based spectrum sharing. ACM/Springer Mobile Networks and Applications (MONET), 11(3), 405–418.
Al Daoud, A., Alpcan, T., Agarwal, S., & Alanyali, M. (2008). A stackelberg game for pricing uplink power in wide-band cognitive radio networks. In Proceedings of 47th IEEE conference on decision and control, Mexico, Dec 2008.
Li, Z., Gao, L., Wang, X., Gao, X., & Hossain, E. (2010). Pricing for uplink power control in cognitive radio networks. IEEE Transactions on Vehicular Technology, 59(4), 1769–1778.
Xing, Y., Mathur, C. N., Haleem, M. A., Chandramouli, R., & Subbalakshmi, K. P. (2007). Dynamic spectrum access with QoS and interference temperature constraints. IEEE Transactions on Mobile Computing, 6(4), 423–433.
Wang, F., Krunz, M., & Cui, S. G. (2008). Price-based spectrum management in cognitive radio networks. IEEE Journal of Selected Topics in Signal Processing, 2(1), 74–87.
Scutari, G., Palomar, D. P., & Barbarossa, S. (2008). Optimal linear precoding strategies for wideband noncooperative systems based on game theory—Part I: Nash equilibria. IEEE Transactions on Signal Processing, 56(3), 1230–1249.
Scutari, G., Palomar, D. P., & Barbarossa, S. (2008). Optimal linear precoding strategies for wideband noncooperative systems based on game theory—Part II: Algorithms. IEEE Transactions on Signal Processing, 56(3), 1250–1267.
Hong, M., & Garcia, A. (2011). Equilibrium pricing of interference in cognitive radio networks. IEEE Transactions on Signal Processing, 59(12), 6058–6072.
Hong, M., Garcia, A., & Wilson, S. G. (2011). Distributed uplink resource allocation in cognitive radio networks—Part I/II: Equilibria and algorithms for power allocation. CoRR abs/1102.1959.
Hong, M., Garcia, A., Barrera, J., & Wilson, S. G. (2013). Joint access point selection and power allocation for uplink wireless networks. IEEE Transactions on Signal Processing, 61(13), 3334–3347.
Shaat, M., & Bader, F. (2012). Asymptotically optimal resource allocation in OFDM-based cognitive networks with multiple relays. IEEE Transactions on Wireless Communications, 11(3), 893–897.
Alsharoa, A., Bader, F., & Alouini, M.-S. (2013). Relay selection and resource allocation for two-way DF-AF cognitive radio networks. IEEE Wireless Communications Letters, 2(4), 427–430.
Wang, T., Song, L., Han, Z., & Jiao, B. (2011). Improve secure communications in cognitive two-way relay networks using sequential second price auction. In Fifth IEEE international symposium on new frontiers in dynamic spectrum access networks 2011 (DySPAN 2011). Aachen, Germany, May 2011.
Li, T., & Jayaweera, S. K. (2008). A novel primary-secondary user power control game for cognitive radios. In The 2008 international symposium on information theory and its applications (ISITA2008). Auckland, NZ, Dec 2008.
Jayaweera, S. K., Vazquez-Vilar, G., & Mosquera, C. (2010). Dynamic spectrum leasing (DSL): A new paradigm for spectrum sharing in cognitive radio networks. IEEE Transactions on Vehicular Technology, 59(5), 2328–2339.
Jayaweera, S. K., & Li, T. (2009). Dynamic spectrum leasing in cognitive radio networks via primary-secondary user power control games. IEEE Transactions on Wireless Communications, 8(6), 3300–3310.
Hakim, K., Jayaweera, S. K., et al. (2010). Efficient dynamic spectrum sharing in cognitive radio networks: Centralized dynamic spectrum leasing (C-DSL). IEEE Transactions on Wireless Communications, 9(9), 2956–2967.
El-howayek, G., & Jayaweera, S. K. (2011). Distributed dynamic spectrum leasing (D-DSL) for spectrum sharing over multiple primary channels. IEEE Transactions on Wireless Communications, 10(1), 55–60.
Vazquez-Vilar, G., Mosquera, C., & Jayaweera, S. K. (2010). Primary user enters the game: Performance of dynamic spectrum leasing in cognitive radio networks. IEEE Transactions on Wireless Communications, 10(12), 3625–3629.
Foschini, G. J., & Miljanic, Z. (1993). A simple distributed autonomous power control algorithm and its convergence. IEEE Transactions on Vehicular Technology, 42(4), 641–646.
Bambos, N., Chen, C., & Pottie, G. J. (2000). Channel access algorithms with active link protection for wireless communication networks with powercontrol. IEEE/ACM Transactions on Networking, 8(5), 583–597.
Tan, C. W., Palomar, D. P., & Chiang, M. (2009). Energy–Robustness tradeoff in cellular network power control. IEEE/ACM Transactions on Networking, 17(3), 912–925.
Buzzi, S., & Saturnino, D. (2011). A game-theoretic approach to energy-efficient power control and receiver design in cognitive CDMA wireless networks. IEEE Journal of Selected Topics in Signal Processing, 5(1), 137–150.
Sorooshyari, S., Tan, C. W., & Chiang, M. (2012). Power control for cognitive radio networks: Axioms, algorithms, and analysis. IEEE/ACM Transactions on Networking, 20(3), 878–891.
Grandhi, S. A., Zander, J., & Yates, R. (1995). Constrained power control. Wireless Personal Communications, 1(4), 257–270.
Yates, R. D. (1995). A framework for up link power control in cellular radio systems. IEEE JSAC, 13(7), 1341–1347.
Meshkati, F., Chiang, M., Poor, H. V., & Schwartz, S. (2006). A non-cooperative power control game for multi-carrier CDMA systems. IEEE Journal of Selected Areas in Communications, 24(6), 1115–1129.
Alpcan, T., Basar, T., Srikant, R., & Altman, E. (2002). CDMA uplink power control as a noncooperative game. Wireless Networks, 8, 659–670.
Le Treust, M., & Lasaulce, S. (2010). A repeated game formulation of energy-efficient decentralized power control. IEEE Transactions on Wireless Communications, 9(9), 2860–2868.
Kakhbod, A., & Teneketzis, D. (2012). Power allocation and spectrum sharing in multi-user, multi-channel systems with strategic users. IEEE Transactions on Automatic Control, AC–57(9), 2338–2342.
Ren, S., & van der Schaar, M. (2011). Pricing and distributed power control in wireless relay networks. IEEE Transactions on Signal Processing, 59(6), 2913–2926.
Saraydar, C. U., Mandayam, N. B., & Goodman, D. J. (2002). Efficient power control via pricing in wireless data networks. IEEE Transactions on Communications, 50, 291–303.
Jain, R., Chiu, D., & Hawe, W. (1984). A quantitative measure of fairness and discrimination for resource allocation in shared systems. Digital Equipment Corporation, DEC-TR-301, Tech. Rep. http://www1.cse.wustl.edu/jain/papers/ftp/fairness.pdf.
Sediq, A. B., et al. (2013). Optimal tradeoff between sum-rate efficiency and Jain’s fairness index in resource allocation. IEEE Transactions on Wireless Communications, 12(7), 3496–3509.
Chiang, M., Hande, P., Lan, T., & Tan, C. W. (2008). Power control in wireless cellular networks. Foundations and Trends in Networking, 2(4), 381–533.
Osborne, M. J., & Rubinstein, A. (1994). A Course in Game Theory. Cambridge, MA: MIT Press.
Varian, H. R. (1992). Microeconomic Analysis. New York: W.W. Norton & Company.
Tse, D. N. C., & Viswanath, P. (2005). Fundamentals of Wireless Communication (1st ed.). Cambridge, UK: Cambridge University Press.
Debreu, G. (1952). A social equilibrium existence theorem. Proceedings of the National Academy of Sciences of the USA, 38, 886–893.
Horn, R. A., & Johnson, C. R. (1985). Matrix Analysis. Cambridge: Cambridge University Press.
Acknowledgments
This work was supported by Fundamental Research Funds for the Central Universities (CDJXS11162236). The authors would like to thank the anonymous reviewers improved the content and presentation of this paper considerably.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendices
1.1 Appendix 1: Proof of (20)
Using the results obtained in Sect. 3, we first simplify the SUs’ SINR defined in (2), and then we derive (20).
Let us define \(I_p^{(s)} ={\sum _{i=1}^{K^{(p)}} {p_i^{(p)} g_{i,s}^{(p)}}}\big /{G_p^{(s)}}\) as the total primary network interference experienced by all SUs at the SUBS.Footnote 10 From (8), we know that \(p_i^{(p)} =\frac{G_p^{(p)} \gamma _{0,tar}^{(p)}}{G_p^{(p)} -(K^{(p)}-1)\gamma _{0,tar}^{(p)}}\left( {\eta _0^{(p)} +I_s^{(p)}}\right) \frac{1}{g_{i,p}^{(p)}}\). Because we have \(\eta _i^{(s)} =\eta _0^{(s)},\forall i=1,\ldots ,K^{(s)}\), that is, all SUs’ signals at the SUBS are corrupted by the same noise power, then after some manipulations about the SINR, we ultimately derive the SINR for SU \(i\) as
where \(a=\left( {\frac{1}{G_p^{(s)}}\frac{G_p^{(p)} \gamma _{0,tar}^{(p)}}{G_p^{(p)} -\left( {K^{(p)}-1}\right) \gamma _{0,tar}^{(p)}}\sum _{l=1}^{K^{(p)}} {\frac{g_{l,s}^{(p)}}{g_{l,p}^{(p)}}}}\right) , b=a\eta _0^{(p)} +\eta _0^{(s)}, c_j ={ah_{j,p}^{(s)}}/{G_s^{(p)}}+{h_{j,s}^{(s)}}/{G_s^{(s)}}\). Based on this SINR formula, two properties can be obtained for (23).
Property 1
\((i)\) We have \({\partial \gamma _i^{(s)} \left( {p_i^{(s)},\mathbf{p}_{-i}^{(s)}}\right) }\big /{\partial p_i^{(s)}}>0\), that is, the SINR \(\gamma _i^{(s)} \left( {p_i^{(s)}, \mathbf{p}_{-i}^{(s)}}\right) \) of SU \(i\) is a monotonically increasing function of its transmission power \(p_i^{(s)} \) for any given \(\mathbf{p}_{-i}^{(s)} \); (ii) For SU \(i\), we have \(\gamma _i^{(s)} \in \left[ {0,\gamma _{i,\max }^{(s)}}\right) \), where \(\gamma _{i,\max }^{(s)} ={G_s^{(p)} h_{i,s}^{(s)}}\big /{ah_{i,p}^{(s)}}\).
Proof
\((i)\) can be directly obtained from (23) by derivative. With property \((i)\), we have that \(\gamma _i^{(s)} \left( {p_i^{(s)},\mathbf{p}_{-i}^{(s)}}\right) \) is maximized at \(p_i^{(s)} \rightarrow \infty \); therefore, we have \(\mathop {\lim }\limits _{p_i^{(s)} \rightarrow \infty } \gamma _i^{(s)} \left( {p_i^{(s)},\mathbf{p}_{-i}^{(s)}}\right) =\gamma _{i,\max }^{(s)} \), that is, property (ii).
We can express the first-order partial derivative of \(u_i^{(s)} \left( {p_i^{(s)},\mathbf{p}_{-i}^{(s)}}\right) \) with respect to \(p_i^{(s)} \) as
From Property 1, we know that \({\partial \gamma _i^{(s)} \left( {p_i^{(s)},\mathbf{p}_{-i}^{(s)}}\right) }\big /{\partial p_i^{(s)}}>0\) is always true, and we assume that \(\lambda _{0}>0\).Footnote 11 Therefore, the best response of the SUs should consider two cases:
Case I: \(\lambda _0 \ge 2\omega _i^{(s)} \gamma _{i,tar}^{(s)} \). It is clear that the term \(\lambda _0 -2\omega _i^{(s)} \left( {\gamma _{i,tar}^{(s)} -\gamma _i^{(s)} \left( {p_i^{(s)}, \mathbf{p}_{-i}^{(s)}}\right) }\right) \) is positive for any feasible value of \(\gamma _i^{(s)} \left( {p_i^{(s)}, \mathbf{p}_{-i}^{(s)}}\right) \), which also means that \({\partial \gamma _i^{(s)} \left( {p_i^{(s)}, \mathbf{p}_{-i}^{(s)}}\right) }\big /{\partial p_i^{(s)}}\) is positive and SU \(i\)’s utility function is monotonically increasing in \(p_i^{(s)} \). Because the SUs aim to minimize their utility functions, the best response of SU \(i\) is to transmit at zero power.
Case II: \(0<\lambda _0 <2\omega _i^{(s)} \gamma _{i,tar}^{(s)} \). In this case, there exists a unique \(p_i^{(*s)} \in P_i^{(s)} \) such that \({\partial \gamma _i^{(s)} \left( {p_i^{(s)},\mathbf{p}_{-i}^{(s)}}\right) }\big /{\partial p_i^{(s)}}=0\) and \(\gamma _i^{(s)} \left( {p_i^{(s)},\mathbf{p}_{-i}^{(s)}}\right) =\gamma _{i,tar}^{(s)} -{\lambda _0}\big /{2\omega _i^2}\). With the secondary user SINR definition given in (23), we then have
To sum up, we have the SUs’ best response (20). \(\square \)
1.2 Appendix 2: Proof of Theorem 1
We first prove the existence of the NE. From the well-known result due to Debreu et al. [42], an NE exists in game \(\Xi ^{(s)}=\left\{ {\Omega ,\left\{ {P_i^{(s)}}\right\} _{i\in \Omega } ,\left\{ {u_i^{(s)} \left( {p_i^{(s)},\mathbf{p}_{-i}^{(s)}}\right) }\right\} _{i\in \Omega }}\right\} \) if for all \(i\in \Omega , P_i^{(s)} \) is a nonempty, convex, and compact subset of some Euclidean space \(\mathfrak {R}\), and \(u_i^{(s)} \left( {p_i^{(s)}, \mathbf{p}_{-i}^{(s)}}\right) \) is continuous in \(\left( {p_i^{(s)}, \mathbf{p}_{-i}^{(s)}}\right) \) and quasi-convex in \(p_i^{(s)} \). We can note that for game \(\Xi ^{(s)}\), the strategy set for SU \(i \)is characterized by \(P_i^{(s)} =\left\{ {p_i^{(s)} :0\le p_i^{(s)} <\infty }\right\} \), that is, it is not a compact set. However, we can take \(p_{i,\max }^{(s)} \rightarrow \infty \) for SU \(i\) as its available MTPC, which will not affect the analysis of the paper. Thus, the strategy set for each SU can be observed as compact. Following the proof of (20), we know that the utility function is continuous in \(\left( {p_i^{(s)},\mathbf{p}_{-i}^{(s)}}\right) \) and quasi-convex in \(p_i^{(s)} \). Therefore, the secondary user power control game \(\Xi ^{(s)}\) has at least one NE.
To prove the uniqueness of the NE and also the convergence of the SUs’ power iteration, using the best response-based NE definition, we just need to demonstrate that each SU’s best response can converge to a unique point [4]. From (25), we know that for a given primary network price \(\lambda _{0}\), not all SUs will be active to share the primary network resource. Let \({\mathcal {A}}(\lambda _0)=\left\{ {i|i\in \Omega ,f_i^{(s)} \left( {\gamma _{i,tar}^{(s)},\lambda _0}\right) >0}\right\} \) denote the active SU sets, and define
SU \(i\)’s power iteration is then
We rewrite the above power iteration in a linear matrix below, so that if the game has a unique NE, then it is the unique component-wise non-negative solution to
where \(\left( {\mathbf{F}^{(s)}}\right) _{i,j\in {\mathcal {A}}\left( {\lambda _0}\right) } =\delta _i^{(s)} c_j \) if \(i \ne j\) and \(\left( {\mathbf{F}^{(s)}}\right) _{i,j\in {\mathcal {A}}\left( {\lambda _0}\right) } =0\) if \(i=j\), and \(\mathbf{v}^{(s)}=b\cdot \left( {\delta _1^{(s)},\delta _2^{(s)} ,\ldots ,\delta _{K^{(s)}}^{(s)}}\right) ^{T}\). For \(0<\lambda _0 <\max _{i\in {\mathcal {A}}\left( {\lambda _0}\right) } \left( {2\omega _i^{(s)} \gamma _{i,tar}^{(s)}}\right) \) Footnote 12, \(\mathbf{F}^{(s)}\) is a non-negative matrix (i.e., all entries are non-negative) and is also non-negative component-wise. As [4], let \(\rho (\mathbf{F}^{(p)})\) be the spectral radius of matrix \(\mathbf{F}^{(s)}\). If \(\rho (\mathbf{F}^{(p)})<1\), then \(\left( {\mathbf{I}-\mathbf{F}^{(s)}}\right) ^{-1}=\sum _{n=0}^\infty {\left( {\mathbf{F}^{(s)}}\right) }^{n}\) exists and is non-negative. In that case, there is a unique component-wise non-negative solution to \(\left( {\mathbf{I}-\mathbf{F}^{(s)}}\right) \mathbf{p}^{(s)}=\mathbf{v}^{(s)}\) given by
which represents the unique NE of the secondary network power game. On the other hand, if \(\rho (\mathbf{F}^{(p)})>1\), then \(\sum _{n=0}^\infty {\left( {\mathbf{F}^{(s)}}\right) }^{n}\rightarrow \infty \) and the game \(\Xi ^{(s)}\) has no NE. Therefore, to prove the uniqueness of the NE and also the convergence of the algorithm is equivalent to proving \(\rho (\mathbf{F}^{(p)})<1\) under the condition \(\lambda _{0} \ge \lambda _{0,ne}\). Because each eigenvalue of a square matrix depends continuously upon its entries (as [43]), that is, \(\rho (\mathbf{F}^{(p)})\) is continuous and non-increasing in primary network price \(\lambda _{0}\). Then, following the proof of Theorem 1 in [4], we know that there exists a threshold \(\lambda _{0,ne;}\) if \(\lambda _{0} \ge \lambda _{0,ne}\), the algorithm converges to the unique NE. To sum up, we have Theorem 1. \(\square \)
1.3 Appendix 3: Proof of Theorem 2
First, from Theorem 1, we know that if \(\lambda _{0,opt}<\lambda _{0,ne}\), then the secondary user power iteration algorithm will not converge to a fixed power level and \(\lim _{n\rightarrow \infty } p_i^{(s)} (n)=p_{i,\max }^{(s)} \rightarrow \infty , \forall i\in {\mathcal {A}}\left( {\lambda _{0,opt}}\right) \). Thus, \(\lim _{n\rightarrow \infty } \rho \omega ^{(p)}\left( {\sum _{i\in {\mathcal {A}}\left( {\lambda _{0,opt}}\right) } {p_i^{(s)} (n)} h_{i,p}^{(s)}}\right) \rightarrow \infty \). However, we know that the term \(-\lambda _0^2 \sum _{i\in {\mathcal {A}}\left( {\lambda _{0,opt}}\right) } {1/{2\omega _i^2}} +\lambda _0 \sum _{i\in {\mathcal {A}}\left( {\lambda _{0,opt}}\right) } {\gamma _{i,tar}^{(s)}} \) is bounded above, then we will have \(u^{(p)}(\lambda _{0})<0\), which violates the law of primary network resource sharing, thus, \(\lambda _{0,opt}\ge \lambda _{0,ne}\).
For the primary network, its amount of resources shared is limited by constraint (18). From (20), we know that the secondary transmission power is a continuously and non-increasing function of primary network price; thus, there is always a price \(\lambda _{0,th}(\le \lambda _{0,max})\) such that the secondary network interference is less than \(I_{th}\) if \(\lambda _{0}\ge \lambda _{0,th}\).
With the proof above, the constrained optimization problem defined in (22) can be transformed to an unconstrained optimization problem as \(\max _{\max \left\{ {\lambda _{0,th} ,\lambda _{0,ne}}\right\} \le \lambda _0 \le \lambda _{0,\max }} u^{(p)}\left( {\lambda _0}\right) =\sum _{i\in {\mathcal {A}}\left( {\lambda _0}\right) } {\left( {-\frac{\lambda _0^2}{2\omega _i^2}+\gamma _{i,tar}^{(s)} \lambda _0}\right) } -\rho \omega ^{(p)}\left( {\sum _{i\in {\mathcal {A}}\left( {\lambda _0}\right) } {p_i^{(s)} \left( {\lambda _0}\right) } h_{i,p}^{(s)}}\right) \) in which, though the objective function \(u^{(p)}(\lambda _{0})\) is non-concave, we have the knowledge that the primary network utility function is monotonically increasing in the interval \(\left[ {0,\omega _{[1]}^{(s)} \gamma _{[1],tar}^{(s)}} \right] \), and how it will be if \(\lambda _0 >\omega _{[1]}^{(s)} \gamma _{[1],tar}^{(s)} \) is unclear. Thus, \(\lambda _{0,opt}\) is not less than \(\omega _{[1]}^{(s)} \gamma _{[1],tar}^{(s)} \). To sum up, we have the conclusion. \(\square \)
1.4 Appendix 4: Proof of Proposition 3
From the proof of Theorem 1, we know that if \(\lambda _{0} \ge \lambda _{0,th}\), then the SUs’ power control algorithm can always converge to a unique solution. Because the primary network suboptimal price search is from the maximum price, i.e., \(\lambda _{0}=\lambda _{0,max}\), to price zero and based on the suboptimal price search stop condition, we know that this procedure will surely converge and can also guarantee the convergence of the SUs’ power iteration to the unique solution, that is, the Proposition 3. \(\square \)
Rights and permissions
About this article
Cite this article
Feng, Wj., Jiang, W. Primary Network Interference Compensation-Based Dynamic Spectrum Leasing and Secondary Network Power Control. Wireless Pers Commun 82, 965–992 (2015). https://doi.org/10.1007/s11277-014-2261-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-014-2261-6