Abstract
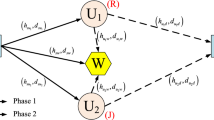
A distributed zero-beamforming-based cooperative jamming technique is useless when an eavesdropper detects the sharing seed. Further, currently alternatives are very limited when the eavesdropper is located near a source for wiretapping. This paper presents some solutions for this extreme case. The jammer node, which can be a relay or destination node, randomly generates and transmits a binary jamming message to both source and destination or to both source and relay node in the first phase. When these two receivers securely and correctly decode the message, the source creates and transmits another message based on the decoded message and the use of exclusive-or for its information message. Consequently, the next transmission can avoid the eavesdropping. We present a comparison between the proposed protocols and conventional protocols that do not send a binary jamming message. The system performance is analyzed and evaluated in terms of the exact closed-form outage probability over Reyleigh fading channels. The simulation results using a Monte-Carlo simulation are in complete agreement with the theoretical results.





Similar content being viewed by others
References
Wyner, A. D. (1975). The wire-tap channel. Bell System Technical Journal, 54, 1355–1387.
Leung-Yan-Cheong, S., & Hellman, M. E. (1978). The Gaussian wire-tap channel. IEEE Transaction on Information Theory, 24, 451–456.
Csiszar, I., & Korner, J. (1978). Broadcast channels with confidential messages. IEEE Transactions on Information Theory, 24, 339–348.
Liang, Y., Poor, H. V., & Shamai (Shitz), S. (2008). Secure communication over fading channels. IEEE Transactions on Information Theory, 54, 2470–2492.
Khodakarami, H., & Lahouti, F. (2012). Link adaptation for physical layer security over wireless fading channel. IET Communications, 6, 353–362.
Sakran, H., Shokair, M., Nasr, O., et al. (2012). Proposed relay selection scheme for physical layer security in cognitive radio networks. IET Communications, 6, 2676–2687.
Romeru-Zurita, N., McLernon, D., & Ghogho, M. (2014). Physical layer security by robust masked beamforming and protected zone optimisation. IET Communications, 8, 1248–1257.
Krikidis, I., Thompson, J. S., & Mclaughlin, S. (2009). Relay selection for secure cooperative networks with jamming. IEEE Transactions on Wireless Communications, 8, 5003–5011.
Ibrahim, Doaa H., Hassan, Emad S., & El-Dolil, Sami A. (2014). A new relay and jammer selection schemes for secure one-way cooperative networks. Wireless Personal Communications, 75, 665–685.
Chen, J., Song, L., Han, Z., & Jiao, B. (2011). Joint relay and jammer selection for secure decode-and-forward two-way relay communications. In IEEE global telecommunications conference (pp. 1–5).
Wang, H.-M., Luo, M., & Yin, Q. (2012). Hybrid cooperative relaying and jamming for secure two-way relay networks. In IEEE global communications conference (pp. 4846–4850).
Wang, H.-M., Luo, M., Xia, X.-G., & Yin, Q. (2013). Joint cooperative beamforming and jamming to secure AF relay systems with individual power constraint and no eavesdropper’s CSI. IEEE Signal Processing Letters, 20, 39–42.
Yupeng, L., Jiangyuan, L., & Petropulu, A. P. (2013). Destination assisted cooperative jamming for wireless physical-layer security. IEEE Transactions on Information Forensics and Security, 8, 682–694.
Krikidis, I., Thompson, J. S., & McLaughlin, S. (2009). Relay selection for secure cooperative networks with jamming. IEEE Transactions on Wireless Communications, 8, 5003–5011.
Sun, X., Xu, W., Jiang, M., & Zhao, C. (2013). Opportunistic selection for decode-and-forward cooperative networks with secure probabilistic constraints. Wireless Personal Communications, 70, 1633–1652.
Truc, T. T., & Kong, H. Y. (2014). An application of network-coding technique into cooperative jamming. In 27th Biennia Symposium on Communications (pp. 218–222).
Son, P. N., & Kong, H. Y. (2014). Exact outage probability of two-way decode-and-forward scheme with opportunistic relay selection under physical layer security. Wireless Personal Communication, 77, 2889–2917.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Nguyen, S.Q., Kong, H.Y. Binary Jamming Message Solutions for Source-Wiretapping Under Physical-Layer Security: Analysis and Design. Wireless Pers Commun 84, 2493–2512 (2015). https://doi.org/10.1007/s11277-015-2716-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2716-4