Abstract
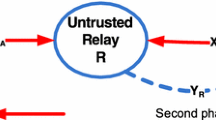
In this paper, a relay based network is considered where the source can transmit confidential data with the help of non-regenerative relay node to the destination. Since the relay is assumed to be untrusted, it is very important to secure confidential data from it while maintaining the reliability of the transmission. A new approach is proposed in which a friendly noise is incorporated with the information bearing signal at the sender such that it does not degrade the integrity of the signal and the quality of the legitimate link. This friendly noise acts as jamming signal for the untrusted relay. The analytical expressions for secrecy outage probability of the proposed technique are derived. The secrecy performance of the proposed approach is compared with the traditional relay transmission and the cooperative jamming schemes. The asymptotic nature of the outage probability is also studied for the different parameters. Numerical results are also presented to verify the derived analytical expressions of the proposed approach.






Similar content being viewed by others
References
Wyner, A. D. (1975). The Wire-tap channel. Bell Systems Technical Journal, 54(8), 1355–1387.
Csiszar, I., & Korner, J. (1978). Broadcast channels with confidential messages. IEEE Transactions on Information Theory, 24(3), 339–348.
Leung-Yan-Cheong, S., & Hellman, M. (1978). The gaussian wire-tap channel. IEEE Transactions on Information Theory, 24(4), 451–456.
Bloch, M., Barros, J., Rodrigues, M. R. D., & McLaughlin, S. (2008). Wireless information-theoretic security. IEEE Transactions on Information Theory, 54(6), 2515–2534.
Krikidis, I., Thompson, J., & McLaughlin, S. (2009). Relay selection for secure cooperative networks with jamming. IEEE Transactions on Wireless Communications, 8(10), 5003–5011.
Krikidis, I. (2010). Opportunistic relay selection for cooperative networks with secrecy constraints. IET Communications, 4(15), 1787–1791.
Ding, Z., Leung, K., Goeckel, D., & Towsley, D. (2011). Opportunistic relaying for secrecy communications: Cooperative jamming vs. relay chatting. IEEE Transactions on Wireless Communications, 10(6), 1725–1729.
Oohama, Y. (2001) “Coding for relay channels with confidential messages”. In IEEE Information Theory Workshop (pp. 87–89).
He, X., & Yener, A. (2008) “Two-hop secure communication using an untrusted relay: A case for cooperative jamming”. In IEEE Global Telecommunications Conference (pp. 1–5).
He, X., & Yener, A. (2010). Cooperation with an untrusted relay: A secrecy perspective. IEEE Transactions on Information Theory, 56(8), 3807–3827.
Goel, S., & Negi, R. (2008). Guaranteeing secrecy using artificial noise. IEEE Transactions on Wireless Communications, 7(6), 2180–2189.
Dong, L., Han, Z., Petropulu, A., & Poor, H. (2009). “Cooperative jamming for wireless physical layer security”. In SSP ’09. IEEE/SP 15th Workshop on Statistical Signal Processing 2009 (pp. 417–420).
Huang, J., & Swindlehurst, A. (2012). Robust secure transmission in miso channels based on worst-case optimization. IEEE Transactions on Signal Processing, 60(4), 1696–1707.
Liu, Y., Li, J., & Petropulu, A. (2013). Destination assisted cooperative jamming for wireless physical-layer security. IEEE Transactions on Information Forensics and Security, 8(4), 682–694.
Huang, J., Mukherjee, A., & Swindlehurst, A. (2013). Secure communication via an untrusted non-regenerative relay in fading channels. IEEE Transactions on Signal Processing, 61(10), 2536–2550.
He, B., Zhou, X., & Abhayapala, T. D. (2013). “Wireless physical layer security with imperfect channel state information: A survey”. CoRR, vol. abs/1307.4146.
Yang, Y., Wang, W., Zhao, H., & Zhao, L. (2012). Transmitter beamforming and artificial noise with delayed feedback: Secrecy rate and power allocation. Journal of Communications and Networks, 14(4), 374–384.
Aggarwal, P., & Trivedi, A. (Sept 2014). “An approach for secure wireless communication using friendly noise”. In International Conference on Advances in Computing, Communications and Informatics (ICACCI) (pp. 1578–1584).
Lai, L., & Poor, H. (2009). “A unified framework for key agreement over wireless fading channels”. In IEEE Information Theory Workshop, 2009. ITW 2009 (pp. 100–104).
Wallace, J., & Sharma, R. (2010). Automatic secret keys from reciprocal mimo wireless channels: Measurement and analysis. IEEE Transactions on Information Forensics and Security, 5(3), 381–392.
Shimizu, T., Iwai, H., & Sasaoka, H. (2011). Physical-layer secret key agreement in two-way wireless relaying systems. IEEE Transactions on Information Forensics and Security, 6(3), 650–660.
Chen, D., Qin, Z., Mao, X., Yang, P., Qin, Z., & Wang, R. (2013). Smokegrenade: An efficient key generation protocol with artificial interference. IEEE Transactions on Information Forensics and Security, 8(11), 1731–1745.
Wang, N., Zhang, N., & Gulliver, T. (2014). Cooperative key agreement for wireless networking: Key rates and practical protocol design. IEEE Transactions on Information Forensics and Security, 9(2), 272–284.
Mathur, S., Trappe, W., Mandayam, N., Ye, C., & Reznik, A. (2008). “Radio-telepathy: Extracting a secret key from an unauthenticated wireless channel”. In Proceedings of the 14th ACM International Conference on Mobile Computing and Networking. New York, NY, USA: ACM, (pp. 128–139).
Zhang, M., Raghunathan, A., & Jha, N. (May 2013). “Towards trustworthy medical devices and body area networks”. In 50th ACM / EDAC / IEEE Design Automation Conference (DAC) (pp. 1–6).
Papoulis, A. (1965). Probability, random variables, and stochastic processes. New York: McGraw-Hill.
Gradshteyn, I. S., & Ryzhik, I. M. (2007). Table of integrals, series, and products (7th ed.). Amsterdam: Elsevier.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Aggarwal, P., Trivedi, A. Secure Wireless Communication Using Friendly Noise Through an Untrusted Relay. Wireless Pers Commun 84, 2927–2941 (2015). https://doi.org/10.1007/s11277-015-2773-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2773-8