Abstract
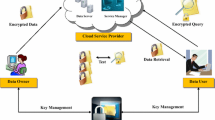
Data owners are used to transmit the data using cloud computing in a low cost. The cloud computing is a popular technology to transmit the data through internet and will also act as third party users. Data owners outsource the data through the cloud server, which have to encrypt the data before outsourcing due to the security and privacy issues. After encrypting the data, users have to find out the respective data using the private key. All information has to be stored in the cloud storage unit. To optimize the cloud storage unit, safety transmission, minimize the cost and searching time, here we have proposed a new scheme as searchable encrypted data file sharing technique. This technique will allocate a keyword for every data during the encryption based on which the keyword matching will accept the data of respective users. The multi keyword search is been proposed for keyword searching. Experimental results analyze the overall performance and the proposed scheme has not only increased the efficiency but also decreased the searching time.







Similar content being viewed by others
References
Abolfazli, S., Sanaei, Z., Tabassi, A., Rosen, S., Gani, A., & Khan, S. U. (2015). Cloud adoption in Malaysia: Trends, opportunities, and challenges. Cloud Computing, IEEE, 2(1), 60–68.
Akgün, M., Bayrak, A. O., Ozer, B., & Sağıroğlu, M. Ş. (2015). Privacy preserving processing of genomic data: A survey. Journal of Biomedical Informatics, 56, 103–111.
Gajra, N., Khan, S. S., & Rane, P. (2015). Private cloud security: Secured user authentication by using enhanced hybrid algorithm. In 2015 IEEE Electrical insulation conference (EIC) (pp. 1–6). IEEE, 2015.
Guo, C., Song, Q., Zhuang, R., & Feng, B. (2015). RSAE: Ranked keyword search over asymmetric encrypted cloud data. In 2015 IEEE fifth international conference on big data and cloud computing (BDCloud) (pp. 82–86). IEEE, 2015.
Hasan, R., & Zawoad, S. (2015). Privacy in the cloud. In S. Zeadally, B. Mohamad (Eds.), Privacy in a digital, networked world, USA: Springer.
Hu, Y., Peng, C., & Bai, G. (2015). Sharing health data through hybrid cloud for self-management. In 2015 IEEE international conference on multimedia and expo workshops (ICMEW) (pp. 1–6). IEEE, 2015.
Li, J., Liu, Z., Chen, X., Xhafa, F., Tan, X., & Wong, D. S. (2015). L-EncDB: A lightweight framework for privacy-preserving data queries in cloud computing. Knowledge-Based Systems, 79, 18–26.
Liu, Z., Weng, J., Li, J., Yang, J., Fu, C., & Jia, C. (2015). Cloud-based electronic health record system supporting fuzzy keyword search. Soft Computing, 1–13.
Magalhães, D., Calheiros, R. N., Buyya, R., & Gomes, D. G. (2015). Workload modeling for resource usage analysis and simulation in cloud computing. Computers & Electrical Engineering, 47, 69–81.
Ohmann, C., Canham, S., Danielyan, E., Robertshaw, S., Legré, Y., Clivio, L., & Demotes, J. (2015). ‘Cloud computing’ and clinical trials: report from an ECRIN workshop. Trials, 16(1), 1–4.
Popescu, C. (2015). Autonomous systems for telemedicine. In 2015 Ninth international conference on complex, intelligent, and software intensive systems (CISIS) (pp. 297–301). IEEE, 2015.
Preethi, B., Shahin, M., & RamaDevi, K. (2015). Synonym query using multi-keyword search using cloud computing. International Journal of Advanced Engineering, 1(3), 192–195.
Ranjan, R., Buyya, R., Nepal, S., & Georgakopulos, D. (2015). A note on resource orchestration for cloud computing. Concurrency and Computation: Practice and Experience, 27(9), 2370–2372.
Raghavendra, S., Geeta, C. M., Shaila, K., Buyya, R., Venugopal, K. R., Iyengar, S. S., & Patnaik, L. M. (2015). MSSS: Most significant single-keyword search over encrypted cloud data. In 6th annual international conference on ICT: Big data, cloud and security (ICT-BDCS 2015) (pp. 43–48).
Samad, J., Loke, S.W., Reed. K. (2015) Mobile Cloud Computing. In da Fonseca N. L. S. & Boutaba. R (Eds.), Cloud Services, Networking, and Management, John Wiley & Sons: Hoboken, NJ.
Shankarwar, M. U. & Pawar, A. V. (2015). Security and privacy in cloud computing: A survey. In Proceedings of the 3rd international conference on frontiers of intelligent computing: Theory and applications (FICTA) 2014 (pp. 1–11). Springer.
Xia, Q., Ni, J., Kanpogninge, A. J. B. A., & Gee, J. C. (2015). Searchable public-key encryption with data sharing in dynamic groups for mobile cloud storage. Journal of Universal Computer Science, 21(3), 440–453.
Xu, Y., Li, M., Hu, X., Wang, Y., & Zhang, H. (2016) Survey on privacy preserving for intelligent business recommendation in cloud In Q.-A. Zeng (Ed.,) Wireless communications, networking and applications, India: Springer.
Xue, H., Inati, S., Sørensen, T. S., Kellman, P., & Hansen, M. S. (2015). Distributed MRI reconstruction using gadgetron-based cloud computing. Magnetic Resonance in Medicine, 73(3), 1015–1025.
Zickau, S., Beierle, F., & Denisow, I. (2015). Securing mobile cloud data with personalized attribute-based meta information. In 2015 3rd IEEE international conference on mobile cloud computing, services, and engineering (MobileCloud) (pp. 205–210). IEEE, 2015.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Pitchai, R., Jayashri, S. & Raja, J. Searchable Encrypted Data File Sharing Method Using Public Cloud Service for Secure Storage in Cloud Computing. Wireless Pers Commun 90, 947–960 (2016). https://doi.org/10.1007/s11277-016-3273-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-016-3273-1